RIB-EXT Side of Configuration to Point to External Application
Below are the steps to point rib-ext to the correct injector service.
Table 4-2
| Category | Step | Comment |
|---|---|---|
|
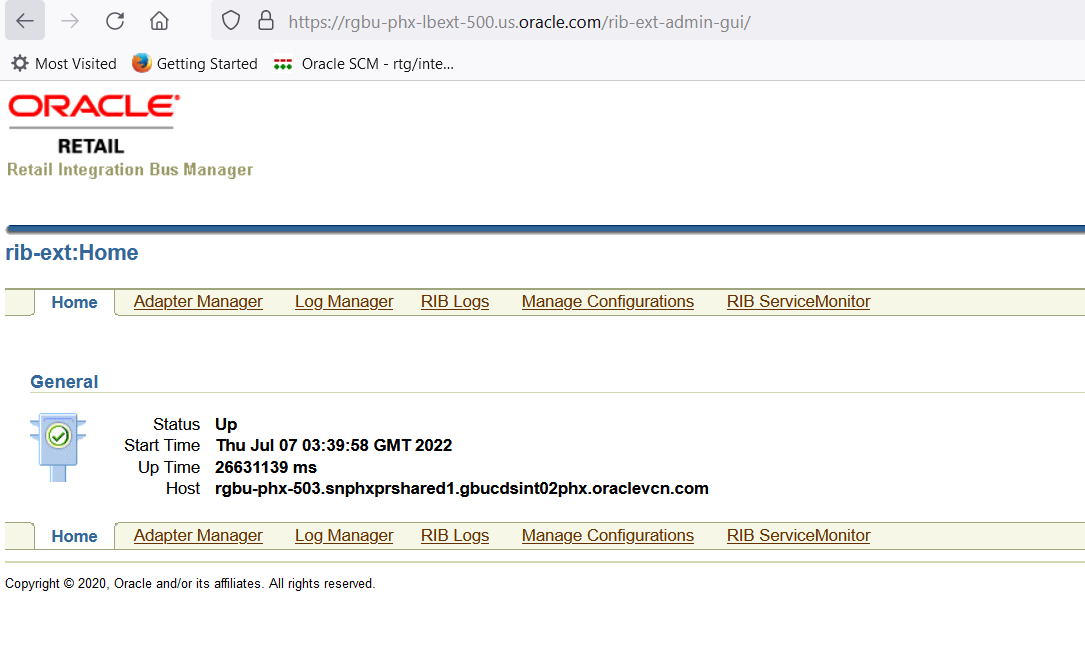
Access RIB Admin GUI |
Access the rib admin GUI at https://<external-load-balancer>/rib-ext-admin-gui Log in with the admin user. |
 |
|
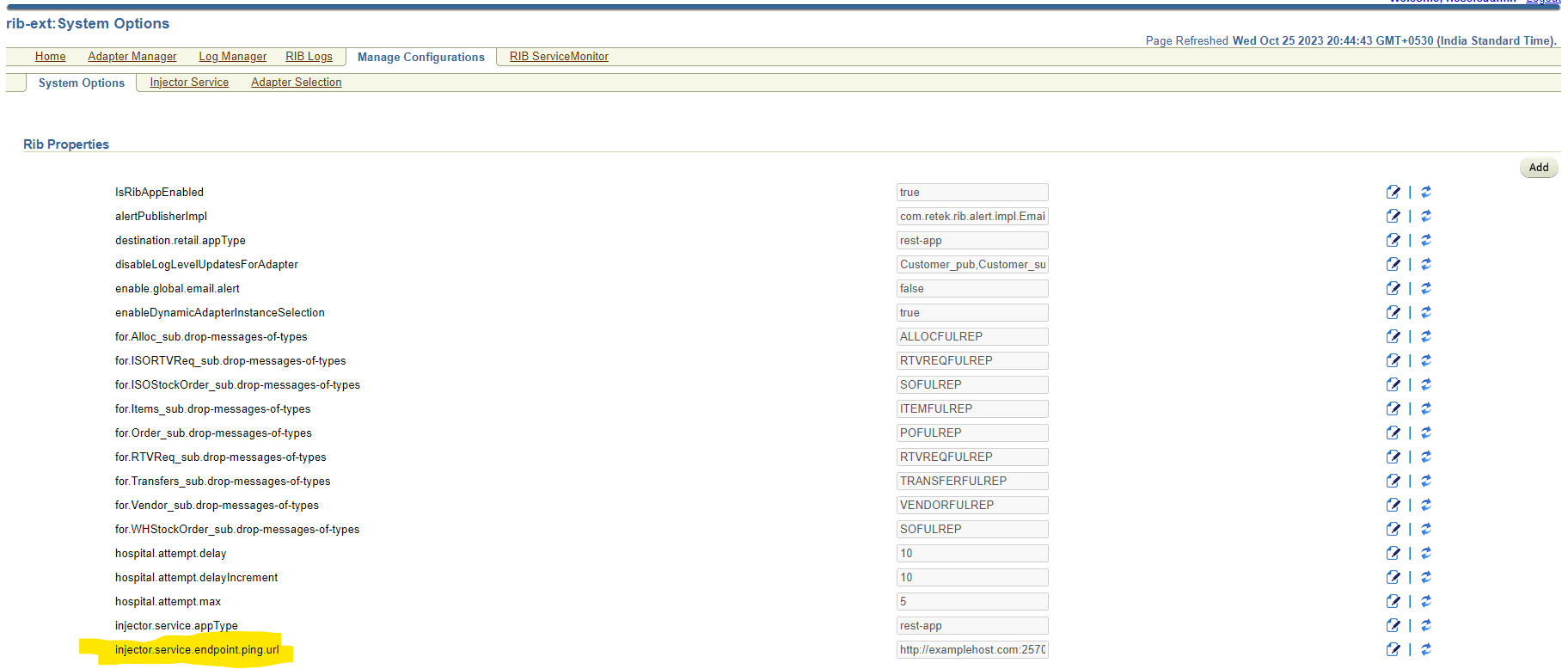
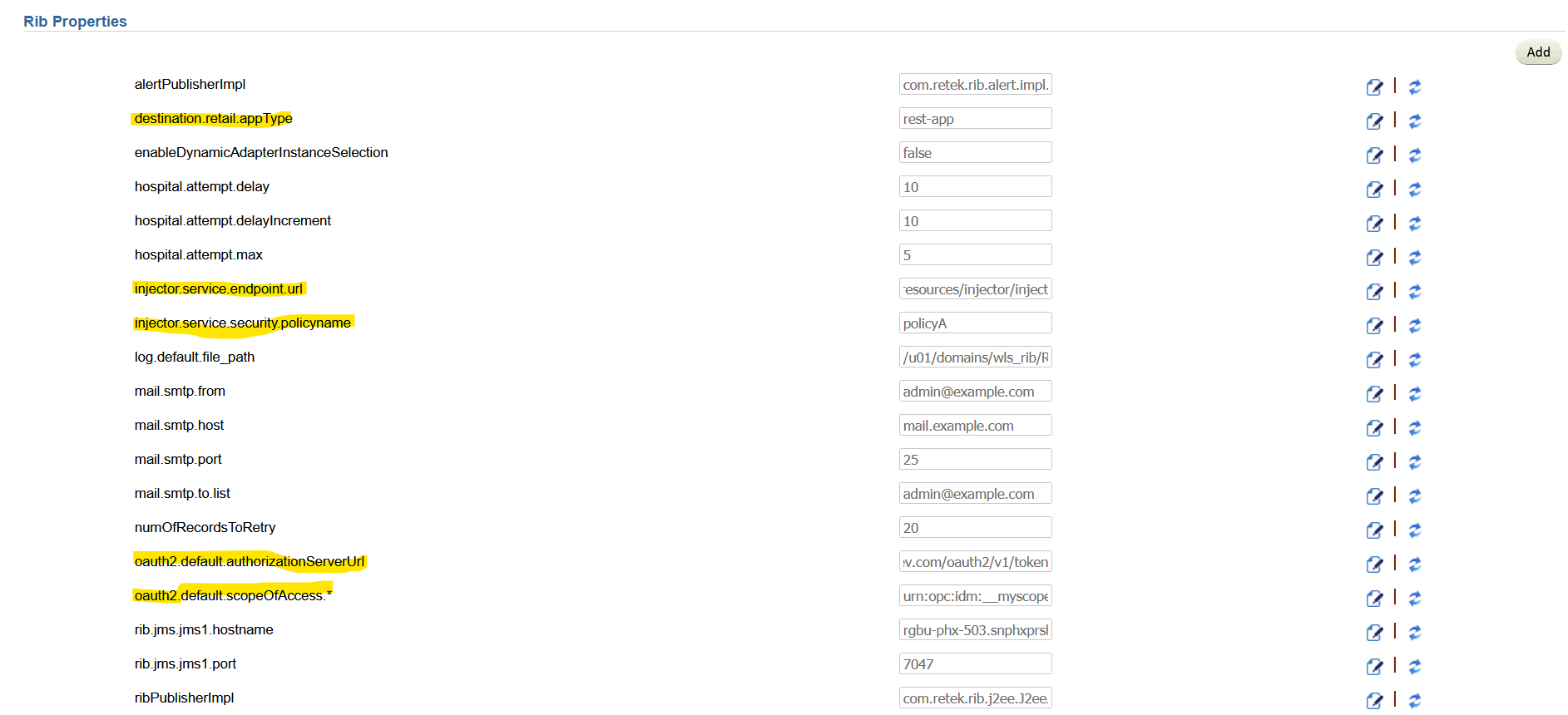
Verify Configuration and update |
Navigate to Manage Configurations -> System options Search for and verify the following:
|
|
|
Supported Grant Types for OAuth2 |
Only client credential grant type is supported. Follow steps below. |
|
|
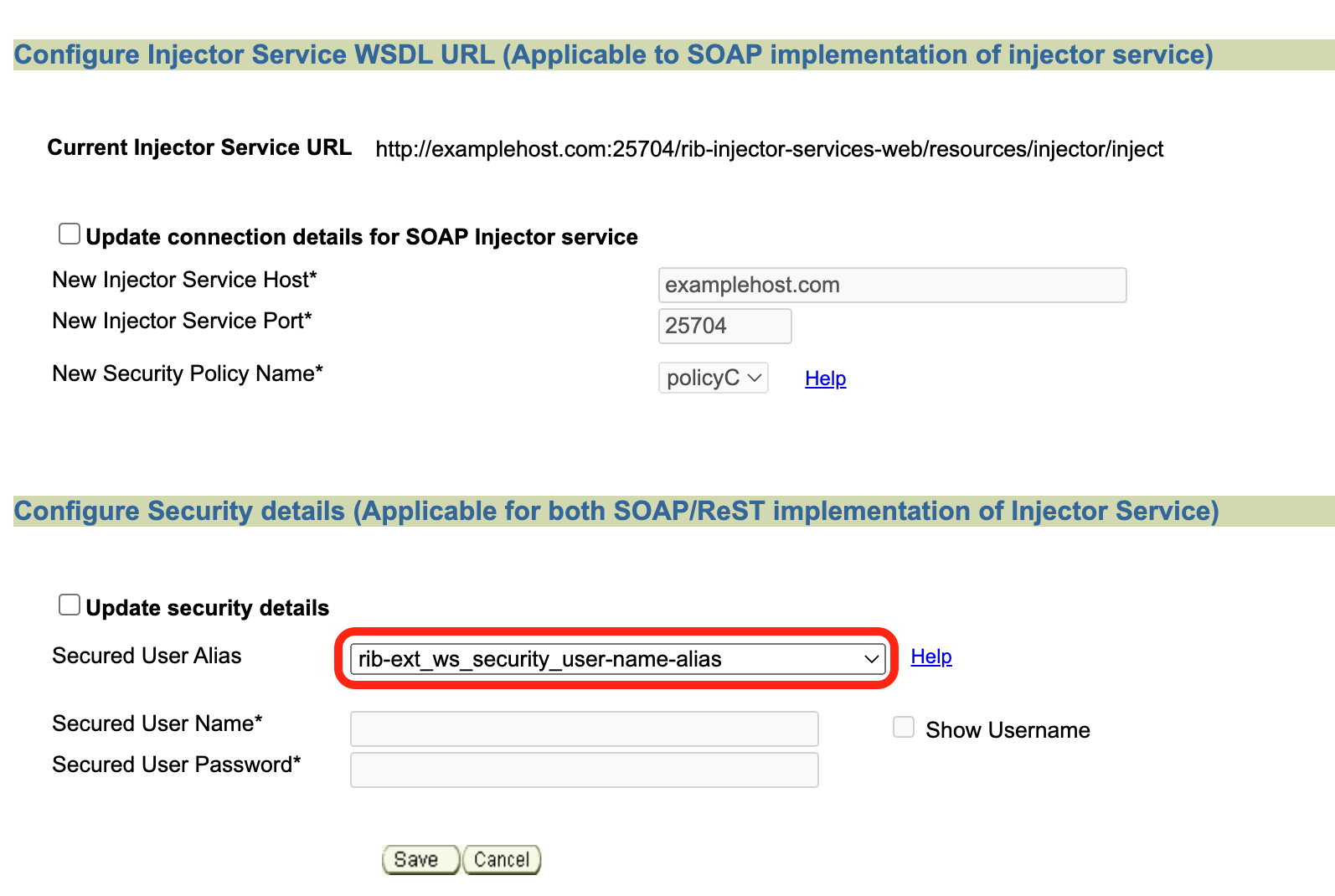
Update username and password to empty |
Navigate to Manage Configurations - > Injector Service Update details.
|
|
|
Update ClientID/Secret |
Navigate to Manage Configurations - > Injector Service Update details
|
|
|
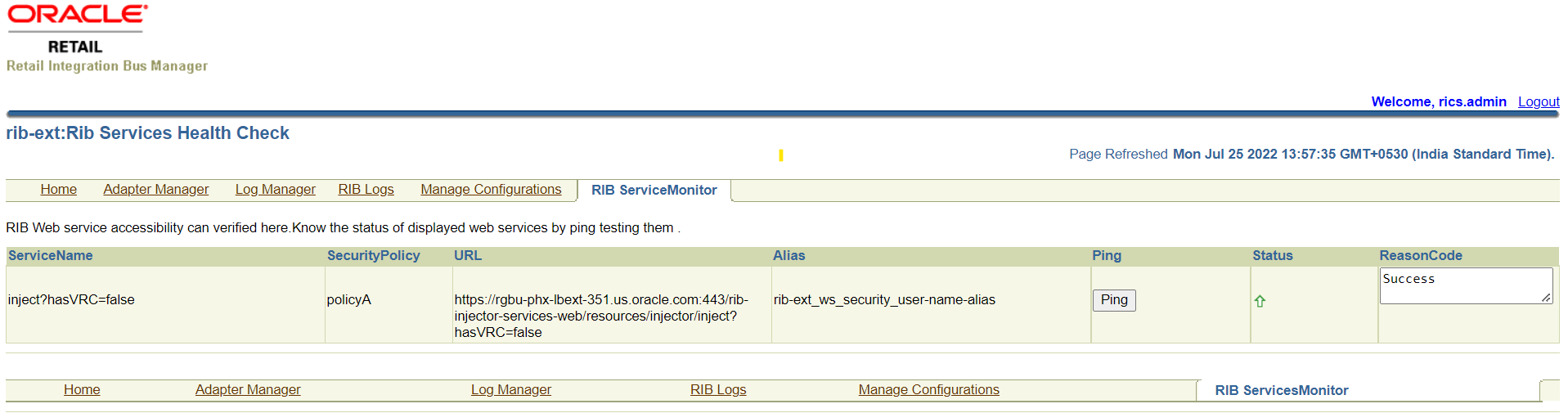
Ping Test |
Navigate to Manage Configurations -> RIB Service Monitor
|
|
|
How to verify provided injector service details are correct |
Verify if the provided injector service URL and credentials are correct. |
Execute the following curl commands ClientId=56c7eb72f11b43bb98bf2570fa2353eb ClientSecret=bb18aa22-4bb4-41d1-9ed4-fea276651e28 IDCSUrl=https://idcs-24e4baae56764e91be371e6a2060d66e.identity.c9dev2.oc9qadev.com AccessToken=$(curl -i -X POST \ --user $ClientId:$ClientSecret \ -H "Content-Type: applica-tion/x-www-form-urlencoded;charset=UTF-8" \ $IDCSUrl/oauth2/v1/token \ -d "grant_type=client_credentials&scope=urn:opc:idm:__myscopes__" | grep -o -P '(?<=access_token":").*(?=","token_type)') ribExtServiceUrl=https://rgbu-phx-lbext-351.us.oracle.com/rib-injector-services-web/resources/injector/ping curl -ivkL --noproxy '*' -H "Authorization: Bearer $AccessToken" -H "Content-Type: applica-tion/xml" -X GET $ribExtServiceUrl |