6 Security
Security in the integration layer is a big concern for every retail enterprise. The security system should be open enough to allow trusted remote applications to integrate easily and, at the same time, lock down unauthorized remote access. To address security concerns, RIB utilizes the security modules available in the Oracle middle ware and database systems.
There are two categories of administrators in RIB: RIB System Administrators and RIB Application Administrators. RIB System Administrators are involved in installing, configuring, deploying defect fixes, and making sure that the integration infrastructure is up and running properly. They generally are concerned with the business side of the integration system. Their tasks include bringing up or taking down RIB adapters, and fixing data issues with message payloads using RIHA. There are separate realms, roles, groups, and users defined for each category of RIB administrators.
RIB Application Administrators Security Domain
For each rib-<app>.ear deployed, RIB creates the users belonging to the below groups:
-
RicsAdminGroup
-
RicsOperatorGroup
-
RicsMonitorGroup
The default groups and user that RIB creates must not be deleted or modified.
RIB follows a role-based authorization for allowing valid users to perform a defined set of operations from the rib-admin-gui. The user belonging to each of above groups will be associated with a well defined role and thus able to perform authorized operations only. It is recommended that you have a unique user belonging to each group.
Integration with SIOCS
-
RIB will use IDCS OAuth2 for authentication of ReST calls both inbound and outbound (publisher/injector restful services). The primary authentication mechanism in the cloud is OAuth2 using the IDCS authenticator. Out-of-the-box configuration expects OAuth2 to be used.
-
RICS to EICS integration will be a ReST call with OAuth2.
-
The EICS injector URL will be auto-wired as part of RICS provisioning. URL will look something like:
http://wtss-svc.<SIOCS_SUB-NAMESPACE>.svc.occloud:9999/siocs-int-services/internal/api/inject
-
The RICS IDCS Client ID and Secret are auto-wired with rib-sim_oauth2_application_client_user-name-alias as part of provisioning. These will be used to get the access token for accessing EICS end point.
Note:
rib-sim_ws_security_user-name_alias is for BasicAuth and should be set empty for OAuth2 however auto wiring takes care of setting this alias to empty.
-
IDCS Url is also auto-wired, and is set during RICS provisioning. The URL looks something like:
https://idcs-<TENANT>/oauth2/v1/token
Step Comment Access rib-sim admin GUI at
https://<external-load-balancer>/<sub-namespace>/rib-sim-admin-gui
Navigate to Manage Configurations-> System Options.
Search and verify the following system options:
-
injector.service.appType : rest-app
-
Check the injector.service.endpoint.url. URL should be something like:
http://wtss-svc.<SIOCS_SUB-NAMESPACE>.svc.occloud:9999/siocs-int-services/api/ribinjector/inject
-
Look for injector.service.security.policyname, policy should be policyC for internal calls.
-
oauth2.default.authorizationServerUrl : RICS IDCS Host for making call to get the access to-ken.

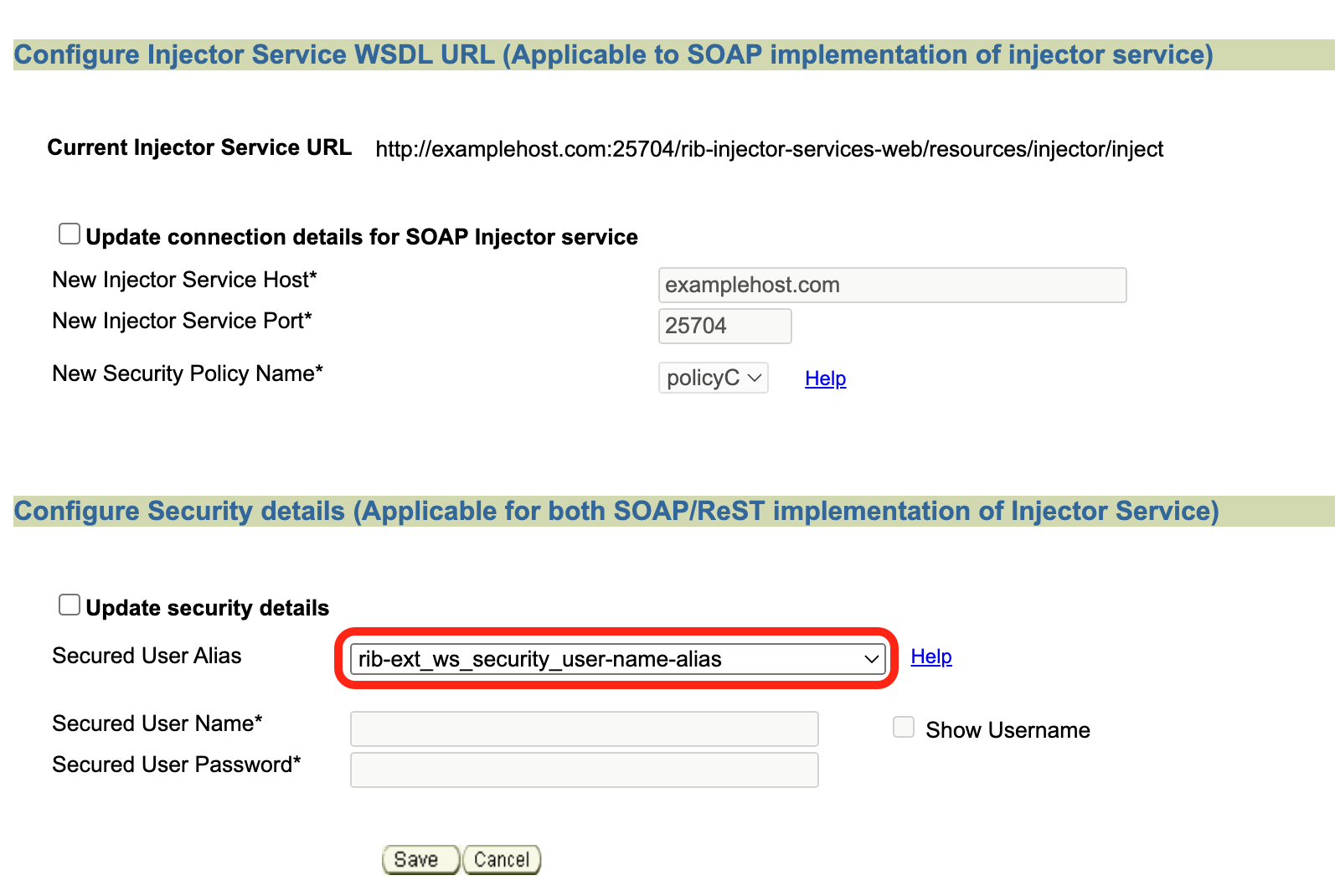
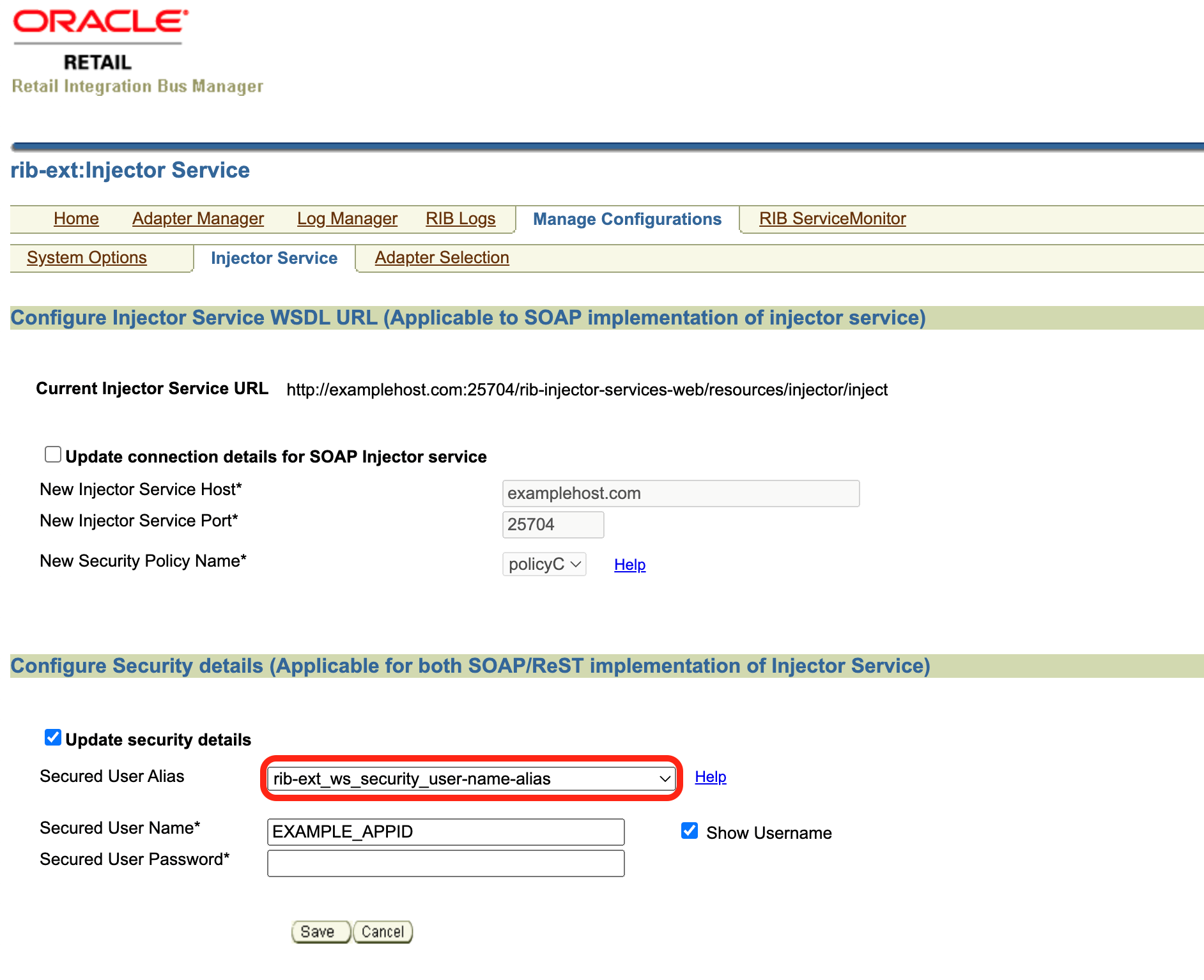
Navigate to Manage Configurations-> Injector Service.
Verify the following:
-
Current Injector Service URL : should point to correct injector service url.
-
rib-sim_ws_security_username_alias credential should be empty.
-
rib-sim_oauth2_application_client_user-name-alias credential must be getting populated with client ID and secret.
How to verify whether the SIM injector URL and credentials are correct.
Navigate to RIB Service Monitor Tab
-
Click ping to test the connectivity.
-
Integration with ROB
-
RICS to ROB integration is Rest call, Oauth2 Authorization.
-
The integration is configured between ROB and RICS via the ReST service (which is HTTPS).
-
ROB injector URL looks something like this:
https://<external-load-balancer>/<rob-sub-namespace>/rib-injector-services-web/orcos/resources/injector/inject
-
The OB IDCS app Client ID and Secret will be used to get the access token for accessing ROB end point.
-
The IDCS Url is set during RICS provisioning. The URL looks something like:
https://idcs-<TENANT>/oauth2/v1/token
Note:
rib-rob_ws_security_user-name_alias is for BasicAuth and should be set empty for OAuth2
Table 6-1 Integrating with ROB
| Category | Steps | Comment |
|---|---|---|
|
Access RIB Admin GUI |
Access the rib admin GUI at https://<external-load-balancer>/rib-rob-admin-gui Log in with the admin user. |
|
|
Verify Configuration and update |
Navigate to Manage Configurations -> System options
|
|
|
Verify username and password |
Navigate to Manage Configurations - > Injector Service
|
|
|
Verify ClientID and Secret |
Navigate to Manage Configurations - > Injector Service Choose rib-rob_oauth2_application_client_user-name-alias from drop down and verify details
|
|
|
Ping test |
Navigate to Manage Configurations -> RIB Service Monitor
|
|
|
Verify provided credentials |
How to verify if the ROB injector URL and credentials are correct. |
ClientId=RGBU_RICS_STG83_APPID ClientSecret=776381f5-88f5-4995-aa57-ecc7b7a1a8d7 IDCSUrl=https://idcs-24e4baae56764e91be371e6a2060d66e.identity.c9dev2.oc9qadev.com AccessToken=$(curl -i -X POST \ --user $ClientId:$ClientSecret \ -H "Content-Type: application/x-www-form-urlencoded;charset=UTF-8" \ $IDCSUrl/oauth2/v1/token \ -d "grant_type=client_credentials&scope=urn:opc:idm:__myscopes__" | grep -o -P '(?<=access_token":").*(?=","token_type)') echo $AccessToken ribExtServiceUrl=https://omni.retail.us-phoenix-1.ocs.oc-test.com/rgbu-omni-rgbu-stg83-obcs/rib-injector-services-web/orcos/resources/injector/ping curl -ivkL --noproxy '*' -H "Authorization: Bearer $AccessToken" -H "Content-Type: application/xml" -X GET $ribExtServiceUrl if you get a 200 response, then the configuration is correct if you get 401 unauthorized, then Client ID and secret are incorrect |