4 Managing User Security
When implementing the Merchandising suite as a cloud service, Merchandising uses Oracle Cloud Infrastructure Identity and Access Management (OCI IAM) as its identity provider:
-
Oracle Cloud Infrastructure Identity and Access Management (OCI IAM):
https://docs.oracle.com/en-us/iaas/Content/Identity/home.htm
For more information about using OCI IAM and Oracle Retail applications, see Oracle Retail Identity Management for OCI IAM.
https://docs.oracle.com/en/industries/retail/retail-identity-management/latest/idmsg/index.html
Managing Users in OCI IAM
OCI IAM is Oracle's cloud native security and identity platforms. It provides a powerful set of hybrid identity features to maintain a single identity for each user across cloud, mobile, and on-premises applications. OCI IAM both enables single sign on (SSO) across all applications in your Oracle Cloud tenancy.
You can also integrate OCI IAM with other on-premise applications to extend the scope of this federated identity management.
All application user maintenance is performed via OCI IAM. It is also where users are assigned to groups, which are the equivalent to roles (or job roles) in Merchandising.
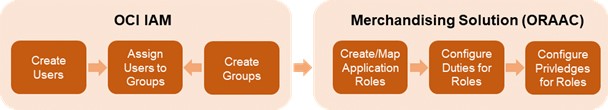
Add Groups in OCI IAM
For Merchandising Cloud Service implementations, all the default roles are created for you in OCI IAM for both production and non-production environments, including the administration roles described below. The non-production version of the roles will include a "_PREPROD" extension.
This is because a single instance of OCI IAM will hold both production and non-production roles for your Merchandising cloud solutions, so the names need to be differentiated. These roles should not be removed. For the full list of groups/roles that are seeded with each of the Merchandising cloud services, see the volume 2 security guides for each service.
If you want to add roles outside the default roles for the Merchandising solutions, you can initiate that process in OCI IAM by creating a new group.
It is recommended you use a similar naming convention as is used for base roles, appending non-production roles with the _PREPROD extension so that if you later choose to migrate the configurations between environments, the role names only need to have the extensions updated. You could also use different extensions if creating roles for different purposes. General steps for adding groups in OCI IAM are shown below, but please see the latest OCI IAM documentation for specifics.
Add Users in OCI IAM
General steps for adding users in OCI IAM are shown below, but please see the latest OCI IAM documentation for specifics.
-
In OCI IAM, click on the Users link in the Navigation Drawer.
-
Select Add to add a new user.
-
In the popup, enter the user's name and ID, then click Next.
-
Assign the new user to one or more groups by ticking the appropriate boxes. Use the search box in the popup to narrow down the list, if needed. Then click Finish.
Additionally, several users will be added in OCI IAM for your Merchandising cloud service implementation that are used for running batch processes, web service calls, and so on. These users (e.g., for example, bdi_admin, jos_admin) will be managed by the Oracle Cloud Operations team and should also not be removed.
Map Groups to Application
When new groups are created in OCI IAM, they must be associated with an appropriate Oracle Retail enterprise role to access the Merchandising suite. This can only be done by users assigned to the administration role in the appropriate solution:
-
Merchandising: RMS_APPLICATION_ADMINISTRATOR_JOB
-
Sales Audit: RESA_APPLICATION_ADMINISTRATOR_JOB
-
Pricing: PRICING_APPLICATION_ADMINSTRATOR_JOB
-
Invoice Matching: REIM_APPLICATION_ADMINSTRATOR_JOB
-
Allocation: ALLOCATION_APPLICATION_ADMINSTRATOR_JOB
-
Fiscal Management: RFM_APPLICATION_ADMINISTRATOR_JOB
The users with application administration roles have permissions that allow them to update the default role to application access mappings based on these two duties:
-
SETTINGS_MENU_DUTY
-
ADMIN_CONSOLE_DUTY
The Settings Menu Duty provides access to all the menu options under the Settings menu in each of the solutions, except the Security folder. The Admin Console Duty provides access to the Security option. This allows you to create a new role that assigns only the non-security related duties, if desired. The administrative roles provided for each solution are the only roles to which the SETTINGS_MENU_DUTY and ADMIN_CONSOLE_DUTY can be assigned. These duties cannot be assigned to any custom roles.
Figure 4-1 Settings
To make sure the users you create and associate with OCI IAM groups can access functions in the Merchandising cloud services, the last step is to map the OCI IAM group to a role in the appropriate Merchandising cloud service. This is done in the application itself using the Duplicate action. The steps for this are covered in more detail in the Managing Roles, Duties, and Privileges in the Merchandising Suite section below.
Managing Roles, Duties, and Privileges in the Merchandising Suite
As part of the Merchandising solutions security set up, default enterprise roles and their mappings to application roles are provided with every application. Additionally, each solution has a default configuration of duties assigned to application roles, and privileges assigned to duties.
The details for each of these are outlined in volume 2 of the specific solution's security guide. If you wish to change the privileges assigned to base duties, create new duties, or remove or add duties to default roles or your custom roles, you will do this by accessing the Security menu options in the Settings menu in each of the Merchandising solutions.
Note:
The roles, duties, and privileges for each solution area are viewed and managed separately. For example, you will not be able to view or update Allocation duties when accessing the security setup from the Merchandising solution.Figure 4-2 Security Roles
Manage Duties
Clicking on the Roles option in the Security menu will launch the Oracle Retail Application Administrator Console. This page allows you to view and edit all the existing duties that exist for the solution, including the description of how a duty is expected to be used. You can also add custom duties or remove duties, as needed.
Figure 4-3 Roles Page
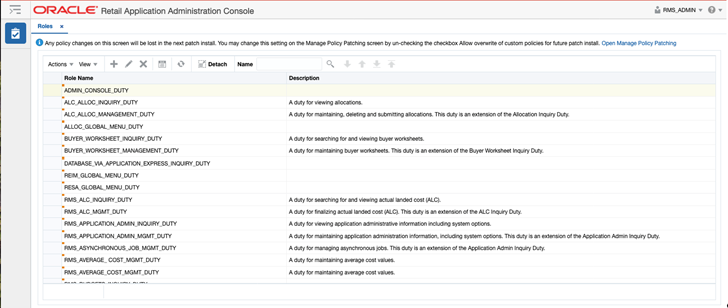
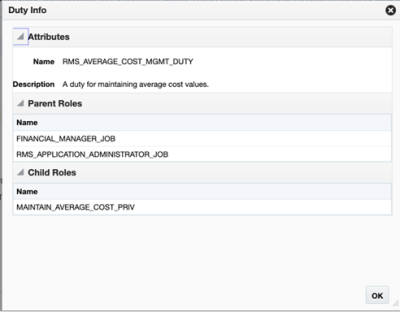
Additionally, hovering over the orange square in the top left of each role name allows you to click on the "carrot" that appears to display additional information about the role, including roles it is assigned to, and which privileges are contained in the duty.
Figure 4-4 Duty Info Pop-up
Manage Role Mappings
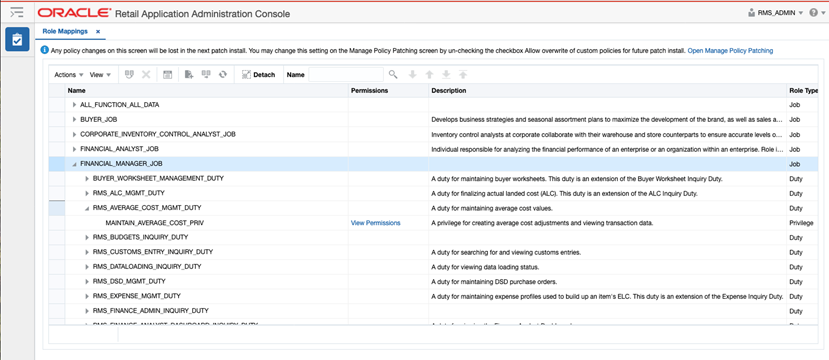
The relationship between roles and duties and/or privileges is managed in the Role Mappings page, which is accessed from the Security menu. Like the Roles screen, this will also launch the Oracle Retail Application Administrator Console. In this screen, you will see all the roles that have had duties and privileges assigned.
Clicking on the arrow next to the role name will show you the list of duties currently assigned to the role. Clicking on the arrow next to the duty name will show you the privileges assigned to that duty. Descriptions are also shown for the duties and privileges to help with understanding of what functions they control in the solution.
You can also click on the View Permissions link for privileges to see the technical details related to the privilege.
There are several actions that you can take in this screen: Duplicate, Delete, Select and Add, and Remap. You also have the option to export this list to Excel.
Figure 4-5 Role Mappings Page
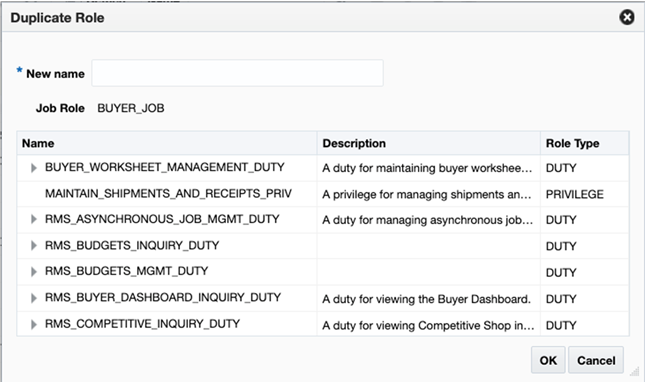
Duplicate
The Duplicate action allows you to copy the duty and privilege configuration of one role to another. This is used to create the role association in the application with the one created in OCI IAM.
To use this function, highlight the role you wish to copy and select
the Duplicate option from the Actions menu or by clicking on the ![]() duplicate icon.
duplicate icon.
It is best to select a role that has similar duties to the role you are adding, when possible. Then, enter the name of the new role where the copied duties and privileges should be added. The application role must not already have duties/privileges assigned in the solution and must have already been created in OCI IAM prior to this step. Once the new role is created in the solution and the duties and privileges are copied to the new role, you can begin configuring the role by removing any duties or privileges that do not apply or adding new.
Figure 4-6 Duplicate Role Page
Delete
The Delete action is enabled when a duty or privilege role is selected.
To delete a duty assigned to a role or a privilege assigned to a duty,
select the Delete option from the Actions menu or click on the ![]() delete
icon
delete
icon
Note:
Any changes to the privileges assigned to duties in this screen will impact all job roles assigned to this duty.Select and Add
The Select and Add option allows you to add new duties to a role
or add new duties or privileges to a duty. To add new duties to a
role, highlight the role in the table and then select the Select and
Add option in the Actions menu or click on the![]() add icon.
add icon.
This will open a popup displaying all the available duties that can be added to the role. Highlight the duties to be added and use the arrows to add to the box on the right. Once all have been added, click OK to save your changes.
Figure 4-7 Select and Add a Page
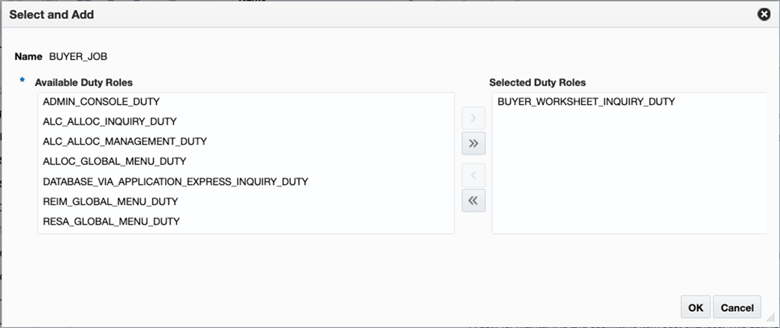
Similarly, to add privileges or child duties to duty, highlight the duty in the table and select the Select and Add option in the Actions menu or click on the add icon button. Select the duties or privileges from the list of available options and click OK to save your changes. It should be noted that any child duties or privileges you add to a duty would be added to all roles that have the parent duty, not just the selected role
Remap
The Remap action and iconic button ![]() is enabled
when a job or duty is selected. The Remap action is used to move mappings
from one role to another role. During this process, a new role is
created and all the associated roles beneath the previous role are
moved into the new role, leaving the old role as an orphan or with
other roles associated with it. It is not recommended that this be
used in Merchandising solutions. Instead, create a new role using
the Duplicate feature.
is enabled
when a job or duty is selected. The Remap action is used to move mappings
from one role to another role. During this process, a new role is
created and all the associated roles beneath the previous role are
moved into the new role, leaving the old role as an orphan or with
other roles associated with it. It is not recommended that this be
used in Merchandising solutions. Instead, create a new role using
the Duplicate feature.
Policy Patching
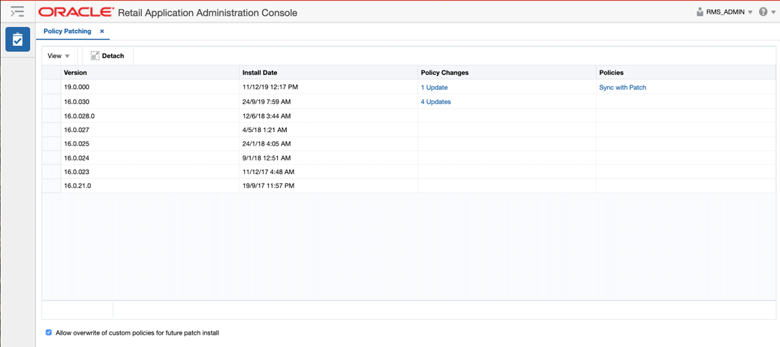
The Policy Patching screen displays two different views. The first view is called the Patch History view. The Patch History view displays the list of patches that have been applied to the solution.
The latest patch provides a link to synchronize the changes introduced in the patch with your role configurations. The Patch History view also has a check box at the bottom of the page to indicate whether to overwrite your configurations when the application is patched in the future.
By default, this should be unchecked to prevent overwriting of your custom policies when patches are applied, so that you can review and apply changes to how your custom policies have been designed.
Figure 4-8 Policy Patching Page
Click the Sync with Patch link to access the second view, which shows you the base policies and your custom policies.
Figure 4-9 Policy Patching – Base Policies
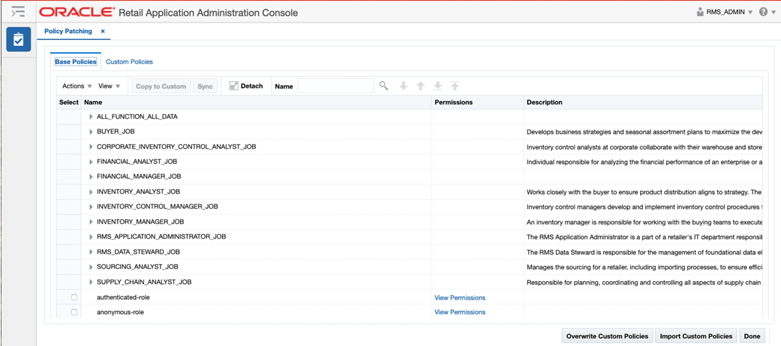
This view provides a way for you to synchronize the changes introduced in a patch with your configuration. The first tab called Base Policies displays the application policies that came in the patched application. The second tab called Custom Policies displays the application policies that you configured. Details on the changes in duties and privileges are provided in the Advanced Release Notes for each patch.
Copy to Custom
The Copy to Custom action is enabled when a privilege is selected in the Base Policies tab and the privilege does not exist in the custom application policies. The Copy to Custom action copies the privilege to a selected duty in the custom policy setup.
Sync
The Sync action is enabled when a privilege that changed in the patch is selected that exists in the custom policy. The Sync action synchronizes the permissions in the selected privilege with the same privilege in the custom application policy setup.
View Permissions
The View Permissions link is used to display the permissions associated with a privilege. This link opens a popup that displays the Resource Name, Permission Actions and Permission Class.
Overwrite Custom Policies
The Overwrite Custom Policies action overwrites the current custom policy setup with the base policy in the patched application. The action will cause the loss of your configured policy changes. The action backs up the application policies before overwriting and can be retrieved using the Manage Backups screen.
Import Custom Policies
The Import Custom Policies action overwrites the current application policy setup with the application policies available in a jazn-data.xml file. The action opens a pop-up, which provides an option to choose a file from your local machine, such as one that you may have created using the Policy Backup screen. This action is useful when migrating policies from one environment to another.
Refresh
The Refresh action is only available in the Custom Policies tab and may be used to refresh the custom application policies. The action can be used to verify the changes in the custom policies after a successful Sync or Copy to Custom action from the base policies.
Note:
If a new duty has been introduced in a patch then the Roles page should be used to create the duty and Role Mappings should be used to assign it to the appropriate job roles. Once the new duty role has been created and assigned to a job role, the Copy to Custom action can be used to assign privileges to that duty.Policy Backups
If a new duty has been introduced in a patch then the Roles page should be used to create the duty and Role Mappings should be used to assign it to the appropriate job roles. Once the new duty role has been created and assigned to a job role, the Copy to Custom action can be used to assign privileges to that duty.
Figure 4-10 Policy Backup Page
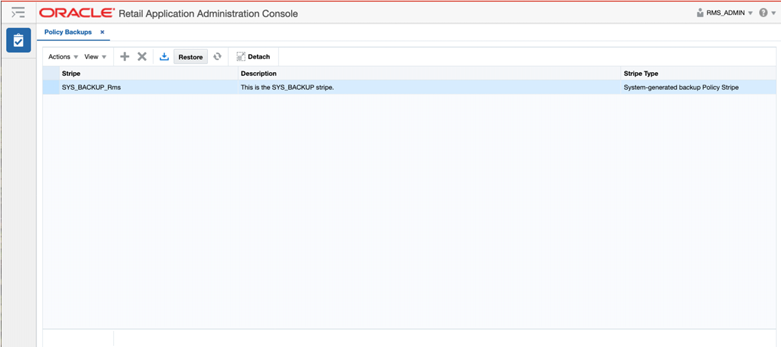
The backups can be created by the following actions:
-
Before overwriting the application polices during a patch install. The installer created backup is prefixed with the name SYS_BACKUP. The installer overwrites the application policies and creates a backup only if the Allow Overwrite of Custom Policies flag is checked in the Policy Patching screen.
-
Selecting the Create action on the Manage Backups screen. The user created backup is prefixed with the name USER_BACKUP.
-
Using the Overwrite Custom Policies action on the Policy Patching screen. The Overwrite Custom Policies action creates a backup before overwriting the custom policies. The backup created by the Overwrite Custom Policies action is prefixed with the name SYS_BACKUP.
Create
This action is used to create a backup of the current policies. The backup stripe name is prefixed with the text USER_BACKUP. The create action opens up a popup where you can enter the comments for why the backup is being taken.
Note:
Only one user-initiated backup is allowed. If a backup already exists, it will be overwritten.Download
The download action is used to download the selected backup stripe in an xml format. It will generate a file called backup.xml which can be stored on the device where the browser is running. The xml file can be opened to look at the changes in the backup.