3 Deploy Containerized Advanced Management Console on Kubernetes Environment
Ensure that all prerequisites are met before you start the deployment.
See Setup the Environment for details.
Create a working directory on your Kubernetes controller machine (on the machine
where helm package and kubectl of your cluster is configured). Place all the required
artifacts such as helm package, custom-values.yaml file,
jks files, and so on in this working directory. You can perform
helm install, update, and uninstall, and kubectl create and delete from this working
directory. See Helm Commands for the complete list of CLI commands for helm.
Configure the Database
Ensure that you have installed and configured MySQL or Oracle database; either on-premise or on DBaaS.
The DB service locator, name, and user credentials must be provided for WebLogic data source setup through AMC helm chart.
Deploy WebLogic Kubernetes Operator
- Verify if the operator’s pod is running. Note that it might take a while for the
operator's pod to be up and running.
kubectl get pods -n <operator-namespace> --watchExample Command:$ kubectl get pods -n wko-ns --watchExpected Output:NAME READY STATUS RESTARTS AGE weblogic-operator-75c85f5649-l6cbx 1/1 Running 0 107s - View the operator's pod log to verify if the operator is up and running:
kubectl logs -n <operator-namespace> -c weblogic-operator deployments/weblogic-operatorExample Command:$ kubectl logs -n wko-ns -c weblogic-operator deployments/weblogic-operator
Create Kubernetes Secrets and ConfigMap
A Secret is an object that contains sensitive data, such as passwords, tokens, or keys. A ConfigMap is an object that stores non-confidential data in key-value pairs.
Create Kubernetes Secrets
You can store and manage confidential information, such as passwords, authentication tokens, and ssh keys in Kubernetes Secret. Storing confidential information in a Secret is safer and more flexible than using them directly in a container image.
You can create Secrets to store user credentials, database connection information, LDAP server credentials, mail server configuration, and so on. Each Secret must have a unique name, which is updated in the custom-values.yaml file. The Secrets are referenced through this file during deployment.
Create Secrets as shown in the following example. The credentials and namespace depicted in the examples are sample values. These values might change based on your requirement.
# Create Secret for WLS Admin Credentials
$ kubectl create secret generic amc-wls-credentials \
--from-literal=username=weblogic \
--from-literal=password='Welcome@123' \
-n amc-ns
##Create Secret for Database Connection
$ kubectl create secret generic amc-ds-credentials \
--from-literal=username=amc2 \
--from-literal=password='amc2' \
-n amc-ns
##Create Secret for mail session in Weblogic
$ kubectl create secret generic amc-mail-credentials \
--from-literal=username=first.last@example.com \
--from-literal=password='mailserverpassword' \
-n amc-ns
##Create Secret for connecting to LDAP server, LDAP Server integration from WLS
$ kubectl create secret generic amc-ldap-credentials \
--from-literal=password='AMC2Admin$' \
-n amc-nsThe Secret names are updated in the custom-values.yaml file. See the sample custom-values.yaml file.
Create a ConfigMap
ConfigMaps are useful for storing and sharing non-sensitive, unencrypted configuration information. It binds configuration files, command-line arguments, environment variables, port numbers, and other configuration artifacts.
You can use a ConfigMap to override any environment-specific configuration.
The WLS for Containerized AMC is configured with default Demo Identity and Demo Trust keystore certificates. During deployment, if you want to overwrite the default configuration, use Custom Identity and Java Standard Trust method. For detailed steps, see Configure Keystores. However, you must have a valid Identity keystore to overwrite the default configuration.
Create a ConfigMap to add a keystore file as shown in the following example. Change the values based on your requirement.
# For Reusing existing JKS or Overriding default JKS Certificate
$ kubectl create configmap amc-keystore --from-file=<path>/amckeystore.jks -n amc-nsProvide the details of the ConfigMap and the file name in custom-values.yaml file. You can also create a Secret for the passwords associated with keystore and alias, and update the secret name in custom-values.yaml file.
$ kubectl create secret generic amc-jks-credentials \
--from-literal=password='keystore_password' \
-n amc-nsConfigure AMC Helm Chart
Ensure to download the AMC Helm Chart from GitHub. The Kubernetes manifest resources including the domain resource file as required by the WKO is packaged as Helm chart.
The Kubernetes manifest resources including the domain resource file as required by
the WKO is packaged as a Helm chart. Ensure that you download the AMC Helm
Chart from GitHub and then install it from the local path. The configuration
parameters that are required to deploy the Containerized AMC are part of the
default values.yaml included in the AMC Helm Chart.
Configurable Parameters
Default values are configured in the AMC Helm Chart.
You can download the Helm Chart from GitHub.
The table provides the default values that are configured in the AMC Helm Chart.
Table 3-1 AMC Helm Chart Configurable Values
| Configuration Keys | Sub-Keys (if any) | Description | Default (if any) | Mandatory or Optional | Accepted Range of Values |
|---|---|---|---|---|---|
namespace |
Kubernetes namespace that the AMC domain should be a part of. | amc | Mandatory | ||
domain |
Domain name for the WebLogic Kubernetes Operator to manage. | amc-domain |
Optional | ||
image |
repo |
Repository hosting the AMC container image. | None | Mandatory | |
tag |
Tag for the AMC container image. | None | Mandatory | ||
pullPolicy |
Policy for image pull. | IfNotPresent |
Optional | Always, IfNotPresent,Never | |
pullSecrets |
For image pull authentication with container registry hosting the AMC container image. | None | Optional | ||
weblogicCredentials |
secretsName |
Name of the Kubernetes Secret containing the credentials for WebLogic server. | <domain-name>-weblogic-credentials |
Depends on the option selected |
Either of these scenarios: (a): User creates a Kubernetes secret containing (b): User provides plain text input against |
username |
Username to be used for WebLogic admin server. | None | Depends on the option selected | ||
password |
Password to be used for WebLogic admin server. | None | Depends on the option selected | ||
weblogicSSLCertificateOverride |
enabled |
Enable to override the default SSL certificate used by WebLogic server. | false |
Optional | |
configmapName |
The ConfigMap should be created from the jks file in the AMC namespace beforehand. The name should be updated against this field.
|
Mandatory, if enabled | |||
keystore: filename |
The name of the jks file used to create the configuration map.
|
Mandatory, if enabled | |||
keystore:secretsName |
Name of the Kubernetes Secret containing the keystore password. | <domain-name>-weblogic-keystore-credentials |
Depends on the option selected | Either of these scenarios:
(a): User creates a Kubernetes secret containing (b): User provides plain text input against |
|
keystore:password |
Plain text password for keystore. | Depends on the option selected | |||
keystorealias:alias |
Name of the alias in the jks.
|
Mandatory, if enabled | |||
keystorealias:secretsName |
Name of the Kubernetes Secret containing the keystore alias password. | <domain-name>-weblogic-keystorealias-credentials |
Depends on the option selected | Either of these Scenarios:
(a): User creates a Kubernetes secret containing (b): User provides plain text input against |
|
keystorealias:password |
Depends on the option selected | ||||
replicaCount |
Number of managed server pods to spin up. Note:Automatic scaling of managed servers is not yet supported. |
2 | Mandatory | 2 to 10 | |
restartVersion |
An increment in this value forces domain restart and introspect on upgrade of deployment. | 1 | Optional | ||
extraEnv |
JAVA_OPTIONS |
Java Options(for memory, proxy, and so on) to be applied to WebLogic containers. | -Xmx2g-Xms512m - Dweblogic.StdoutDebugEnabled=false |
Optional | |
USER_MEM_ARGS |
User memory arguments to be supplied to WebLogic containers. | -XX:+UseContainerSupport |
Optional | ||
resources |
limits |
Set the Kubernetes resource limit for CPU or Memory on the WebLogic containers. | 3Gi for admin server memory and 5Gi for managed server memory
|
Optional | |
requests |
Set the Kubernetes resource request for CPU or Memory on the WebLogic containers. | 1Gi for both admin and managed server memory
|
Optional | ||
isVersionUpgrade |
Set to true for AMC version upgrades. | false |
Optional | ||
database |
type |
Type of database. | mysql |
Mandatory | mysql, oracle |
name |
Name of the database. | amc2 |
Mandatory | ||
credentials.secretsName |
Name of Kubernetes Secret containing the credentials for database connection. | <domain-name>-datasource-credentials |
Depends on the option selected | Either of these scenarios:
(a): User creates a Kubernetes secret containing (b): User provides plain text input against |
|
credentials.username |
Username for the database connection. | None | Depends on the option selected | ||
credentials.password |
Password for the database connection. | None | Depends on the option selected | ||
host |
Hostname where the Database instance is running. | None | Mandatory | ||
port |
Port number of the database instance is running on. | 3306 | Mandatory | ||
isOracle11 |
To be enabled if using Oracle 11g as Database for AMC. | false |
Optional | ||
use_cj_driver_mysql8 |
Enables the usage of com.mysql.cj.jdbc.Driver.
|
false |
Optional | To be enabled only if using MySQL8 and WLS 12.2.1.4 | |
nodePort |
enabled |
Set to true to enable NodePort service.
|
false |
Optional | |
adminserver |
Port number exposing WebLogic admin server interface for access outside cluster using Kubernetes NodePort service. | Random port assignment | Optional | ||
managedserver |
Port number exposing AMC interface for access outside cluster using Kubernetes NodePort service. | Random port assignment | Optional | ||
loadBalancer |
enabled |
Set to Note:Once the LoadBalancer service is enabled for the Containerized AMC, it is persisted even on disabling the option. This is done on purpose to retain the assigned external IP address. Ensure that this service is not deleted inadvertently, else this will lead to AMC services being inaccessible. Note:If only LoadBalancer service is enabled in the |
false |
Optional | |
port |
Port number exposing AMC interface for access outside cluster using Kubernetes LoadBalancer service. | 8002 | Mandatory, if enabled | ||
annotations |
Annotations for the LoadBalancer service. | None | Optional | ||
mailServer |
enabled |
Set to true to enable Mail Server configuration.
|
false |
Optional | |
properties |
Settings for the mail server. | None | Mandatory, if enabled | ||
credentials.secretsName |
Name of Kubernetes Secret containing the credentials for mailserver connection. | <domain-name>-mailserver-credentials |
Depends on the option selected | Either of these scenarios:
(a): User creates a Kubernetes secret containing (b): User provides plain text input against |
|
credentials.username |
Username for the Mail Server connection. | None | Depends on the option selected | ||
credentials.password |
Password for the Mail Server connection. | None | Depends on the option selected | ||
ldap |
enabled |
Set to true to enable LDAP Server configuration.
|
false |
Optional | |
credentials.secretsName |
Name of Kubernetes Secret containing the credential for LDAP connection. | <domain-name>-ldap-credentials |
Depends on the option selected | Either of these scenarios:
(a): User creates a Kubernetes secret containing (b): User provides plain text input against |
|
credentials.password |
Password for the LDAP Server connection. | None | Depends on the option selected | ||
host |
Host name of LDAP server. | None | Mandatory, if enabled | ||
port |
Port number for LDAP service. | 389 | Optional | ||
enableSSL |
Set to true to use SSL for LDAP.
|
false |
Optional | ||
principal |
LDAP principal | None | Mandatory, if enabled | ||
userbaseDN |
Base domain name (DN) for user. | None | Mandatory, if enabled | ||
groupbaseDN |
Base domain name (DN) for group. | None | Mandatory, if enabled |
Deploy Containerized Advanced Management Console
Ensure WKO is deployed successfully before proceeding with the AMC deployment.
kubectl get events -n <amc-namespace> --watch
kubectl get all -n <amc-namespace> -o wide$ kubectl get events -n amc-ns --watch
$ kubectl get all -n amc-ns -o wideYou should see the details about Pods and Services, and the server status as
Running after sometime.
Access the Containerized AMC
You can access Containerized AMC using the NodePort service or the LoadBalancer service or both, depending on the configuration in the custom-values.yaml.
After you deploy the AMC on Kubernetes environment and verify the status of deployment using the command kubectl get all -n amc-ns, the complete node and server information is displayed. The following is an example output:
Figure 3-1 Server Details
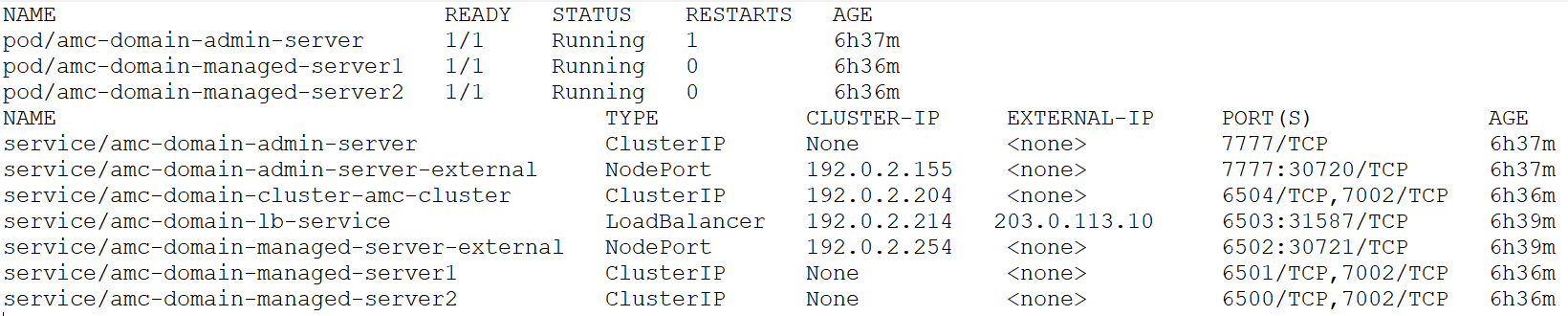
The details of the servers and nodes, including internal and external ports are displayed.
Access Containerized AMC using LoadBalancer Service
In the LoadBalancer service type, note down the external IP and port number. You can use the values to create the URL to access Containerized AMC. Considering the example, the URL to access the Containerized AMC will be https://203.0.113.10:6503/amcwebui/login.html.
Access Containerized AMC using NodePort Service
In the NodePort service type, you can create URLs of the Admin Server and AMC Server using any of the Kubernetes node IP addresses/host name and the external port number mapped against respective NodePort services.
- Admin Server:
http://<kubernetes-node>:30720/console/login/LoginForm.jsp - AMC Server:
https://<kubernetes-node>:30721/amcwebui/login.html
Run the following command to retrieve the Kubernetes node IP addresses:
kubectl get nodes -o wide
You can login using the credentials provided in the custom-values.yaml file.
Note:
- It is recommended to access the Containerized AMC using LoadBalancer service rather than NodePort service.
- If only LoadBalancer service is enabled in the
custom-values.yamlfile, the WebLogic admin server console will not be accessible. If there is a need to access the admin server console, enable the NodePort service as well.
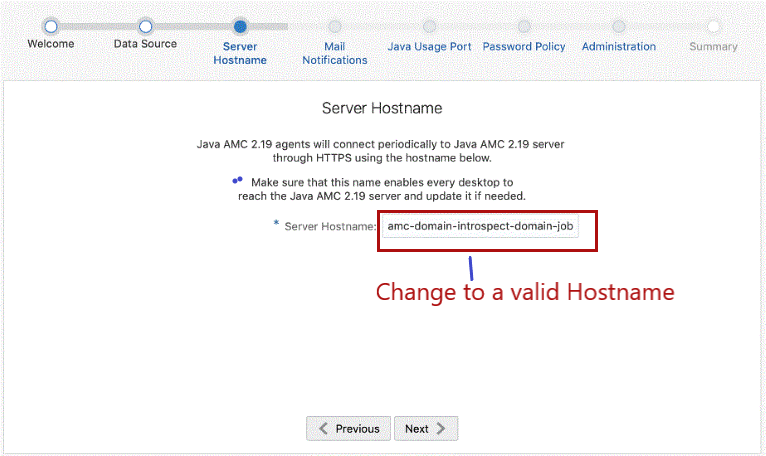
Initialize the Containerized AMC
During initialization, the host name (or host IP) has to be provided. This host name (or host IP) is to be used by all agents to communicate with the server.
By default, the AMC initialization wizard fetches the server host name from the CN (common name) of SSL certificate. However, the CN name might not be the valid server host name for Containerized AMC. Hence, during initialization, provide a valid server host name to access Containerized AMC. Also, ensure that you don't have to change the host name (or host IP) once you specify.
For example, as shown in the following screen shot, the host name is fetched from SSL certificate by default. This is not a valid host name. You need to provide a valid host name or IP for the Containerized AMC to communicate with the server.
Figure 3-2 Initializing Containerized AMC