Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Integrate Oracle APEX with Oracle Cloud Infrastructure Identity and Access Management Identity Domains
Introduction
Oracle Cloud Infrastructure Identity and Access Management (OCI IAM) provides identity and access management features such as authentication, single sign-on (SSO), and identity lifecycle management for Oracle Cloud Infrastructure as well as Oracle and non-Oracle applications, whether SaaS, cloud-hosted, or on-premises.
Objective
- Configure SSO on Oracle APEX applications using OCI IAM identity domains as an Identity Provider (IdP) which provides security controls like Multi-Factor Authentication (MFA), Adaptive Security, Reporting, and so on.
Prerequisites
-
OCI IAM administrator access of any identity domain for partner application set up.
-
Oracle APEX 18.1 and above with an application for authentication set up.
Task 1: Install a Sample Application in Oracle APEX
-
Log in to your APEX workspace to create a sample application for which we will use OCI IAM as an IdP for SSO. To create an application on Oracle APEX, click App Builder.
-
Click Create Application.
-
Select From a File.
-
Click Copy and Paste and select Sales as shown in the following images.
Task 2: Register a Confidential Application in OCI IAM
We will register a confidential application in the OCI IAM domain. For this tutorial, we have used the default domain.
-
Log in to the OCI Console, navigate to Identity and Security. Under Identity, click Domains and Applications.
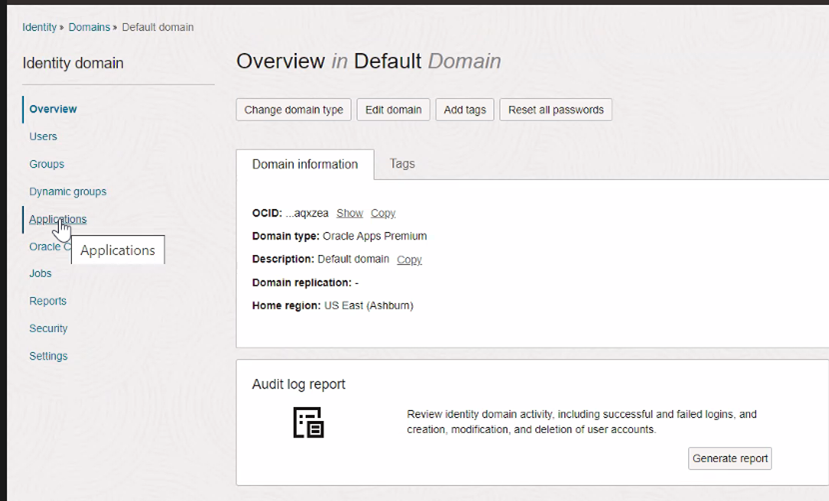
-
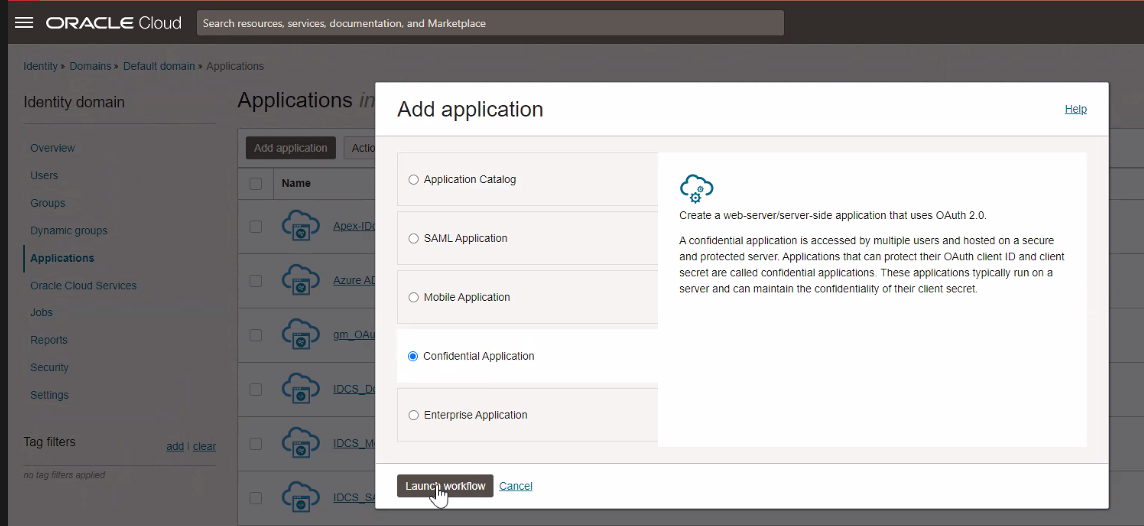
Select Confidential Application and click Launch workflow.
-
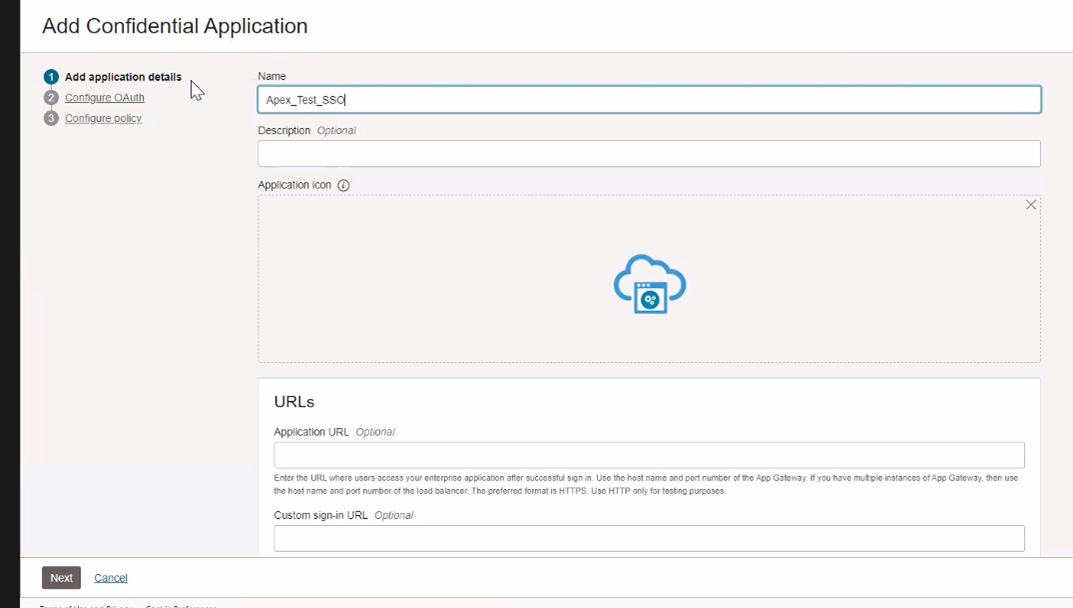
Enter a Name for your application and click Next.
-
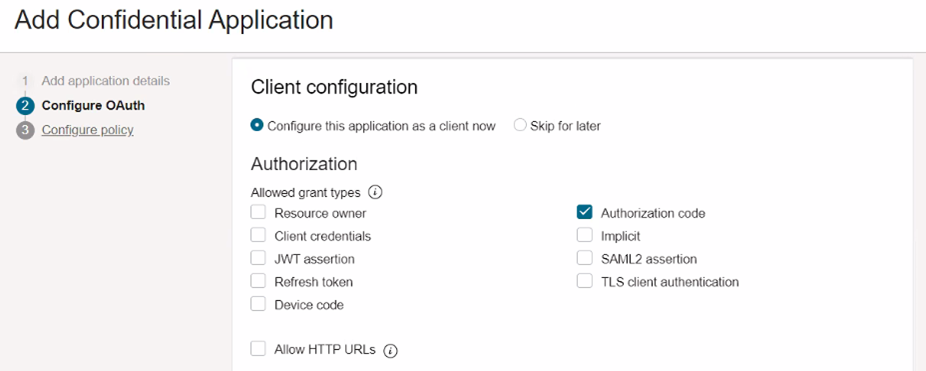
Select Authorization code as the Allowed Grant Type and click Next.
-
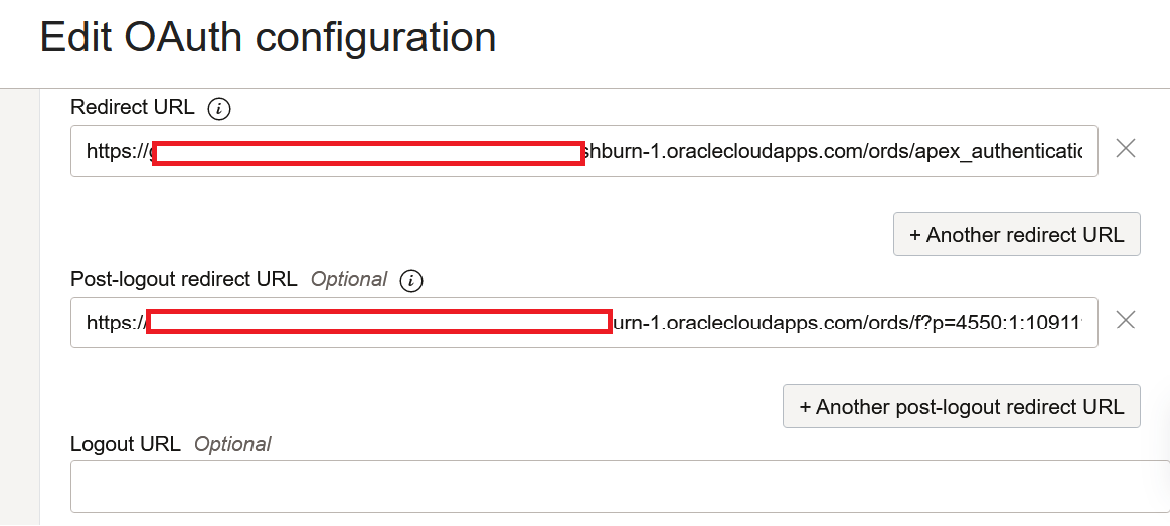
Enter the Redirect URL in this format:
https://guid-demodb.adb.region.oraclecloudapps.com/ords/apex_authentication.callback. For example,https://guid-demodb.adb.us-ashburn-1.oraclecloudapps.com/ords/apex_authentication.callback. -
Enter the Post logout redirect URL in this format:
https://guid-demodb.adb.region.oraclecloudapps.com/ords/f?p=your_apex_number_here. -
Leave the Logout URL blank.
Note: Note down this URL, it must match exactly when added later in the Oracle APEX authentication scheme post-logout URL.
-
Click Finish.
-
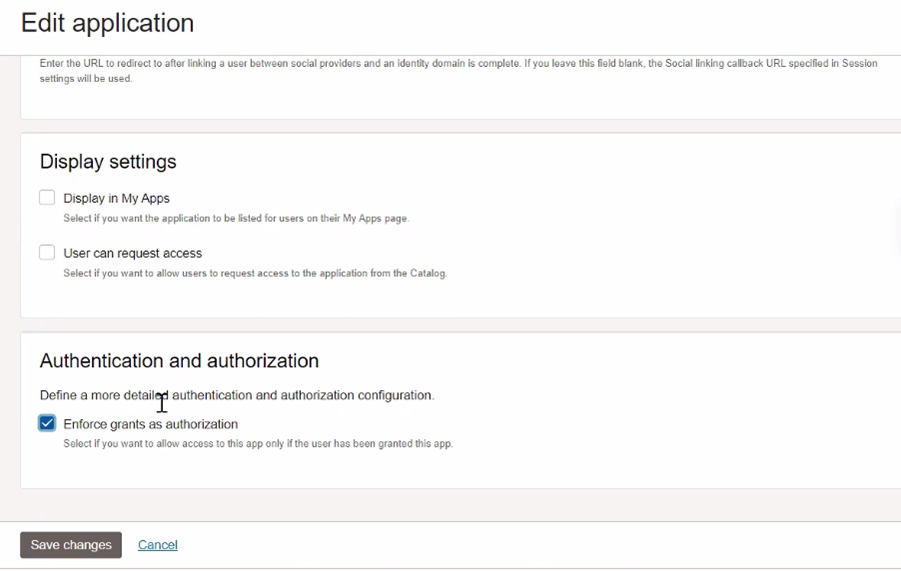
Click Edit application and select Enforce grant as Authorization under Authentication and Authorization (This will be used later to control access to the Oracle APEX application).
-
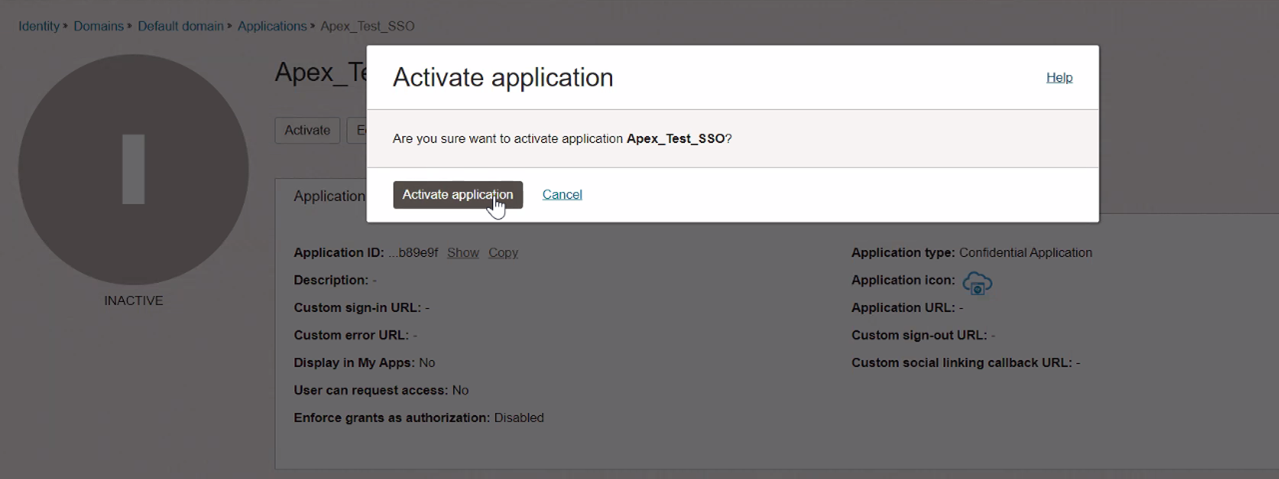
Click Activate Application.
-
Copy the Client ID and Client secret which we will use in the configuration on Oracle APEX side.
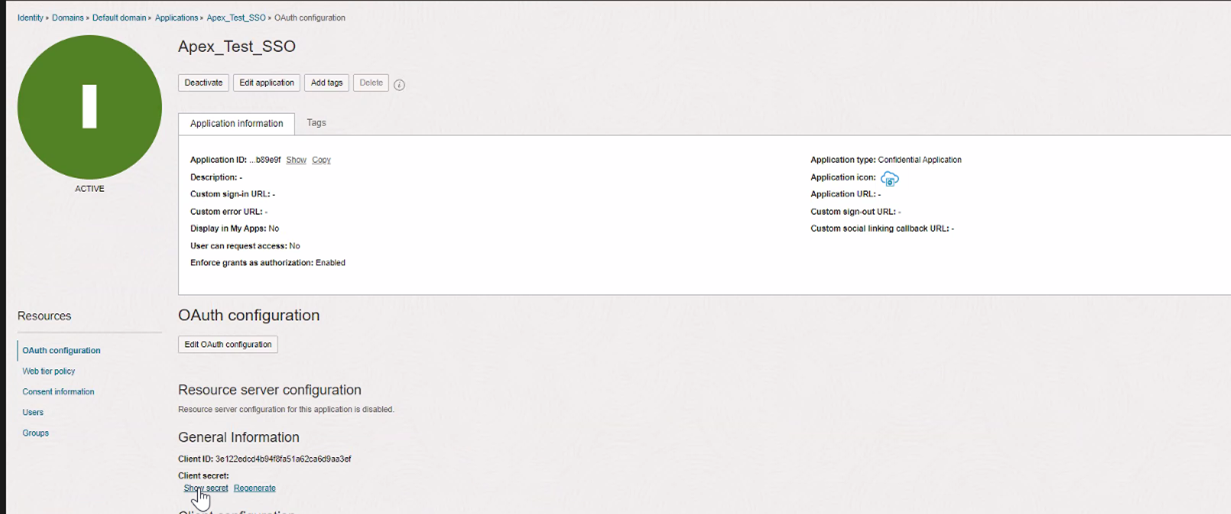
Task 3: Create a new Web Credential in your Oracle APEX Workspace
-
Open Oracle APEX workspace. In your application created in Task 1, click Shared Objects.
-
Click Credentials.
-
Click Create.
-
Enter the following information and click Create.
Note: Use the Client ID and Client Secret from the confidential application in Task 2.
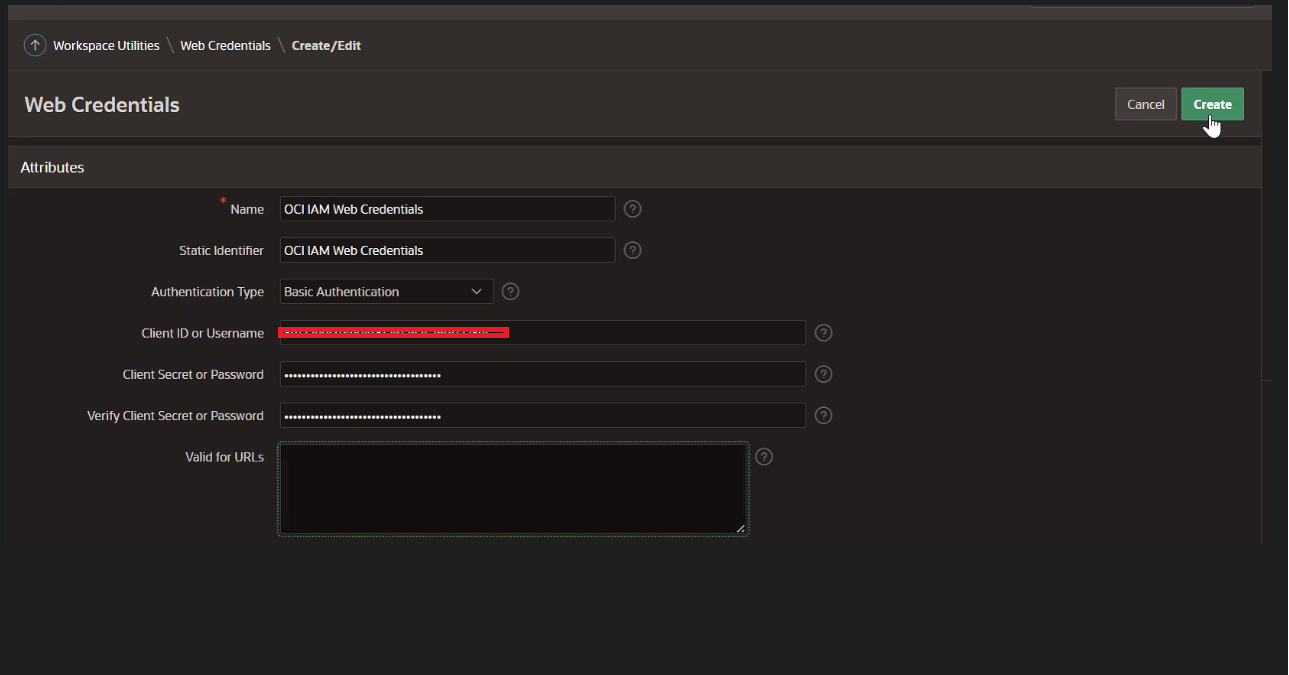
-
Assign a user to this application.
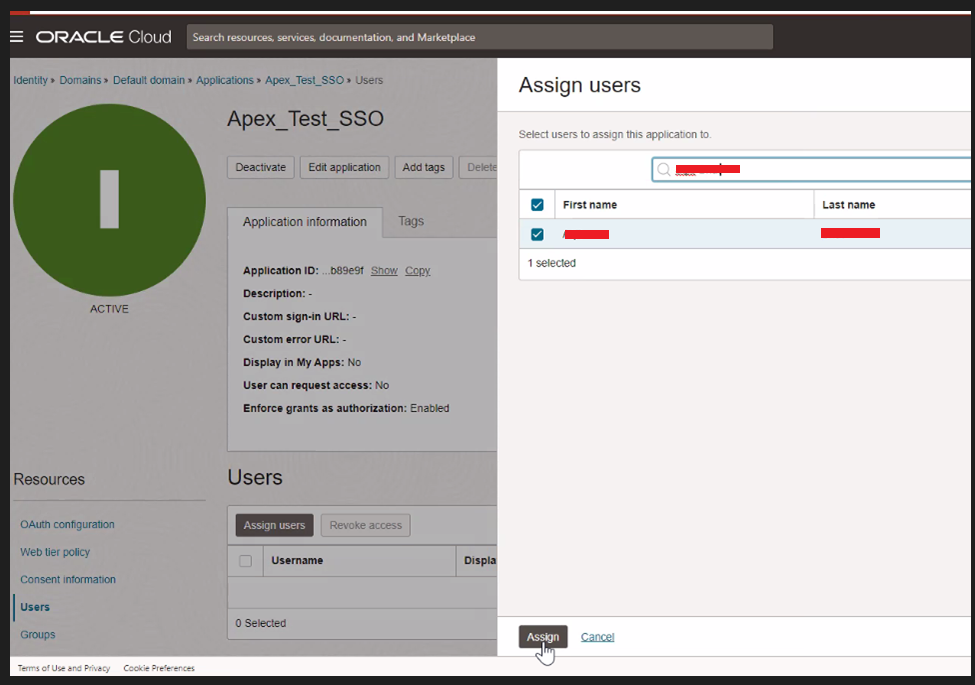
Task 4: Create a new Authentication Scheme in Oracle APEX for the Sample Application
-
Open Oracle APEX workspace and click Shared Objects. Under Security, click Authentication Schemes and Create.
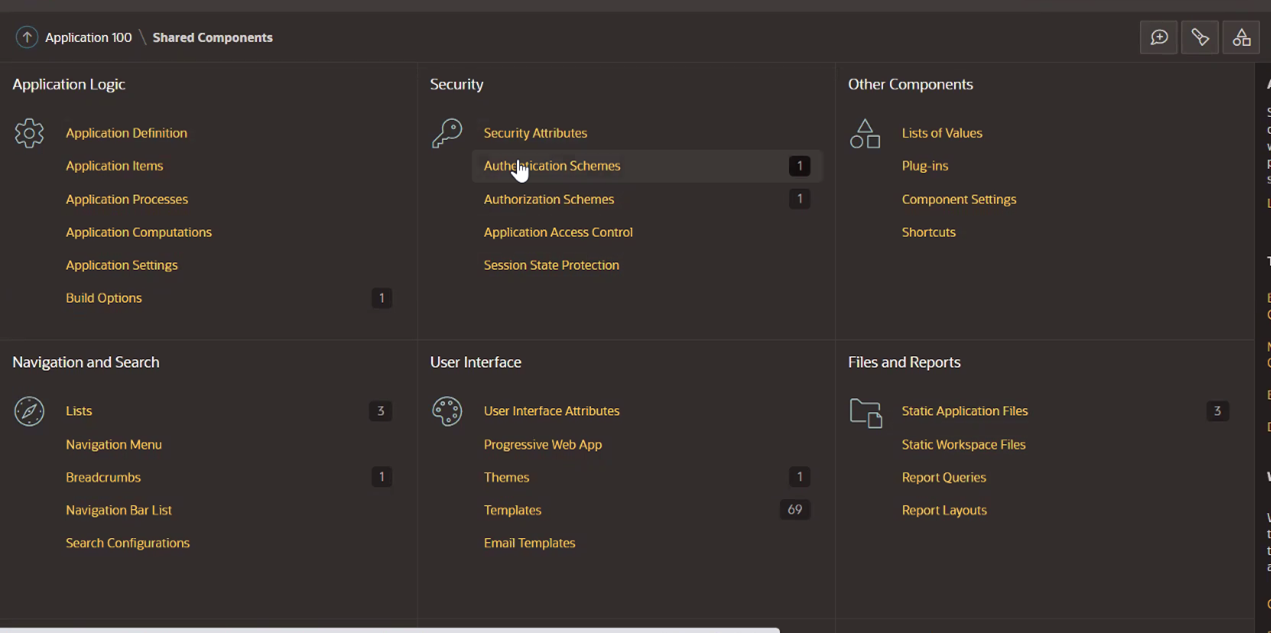
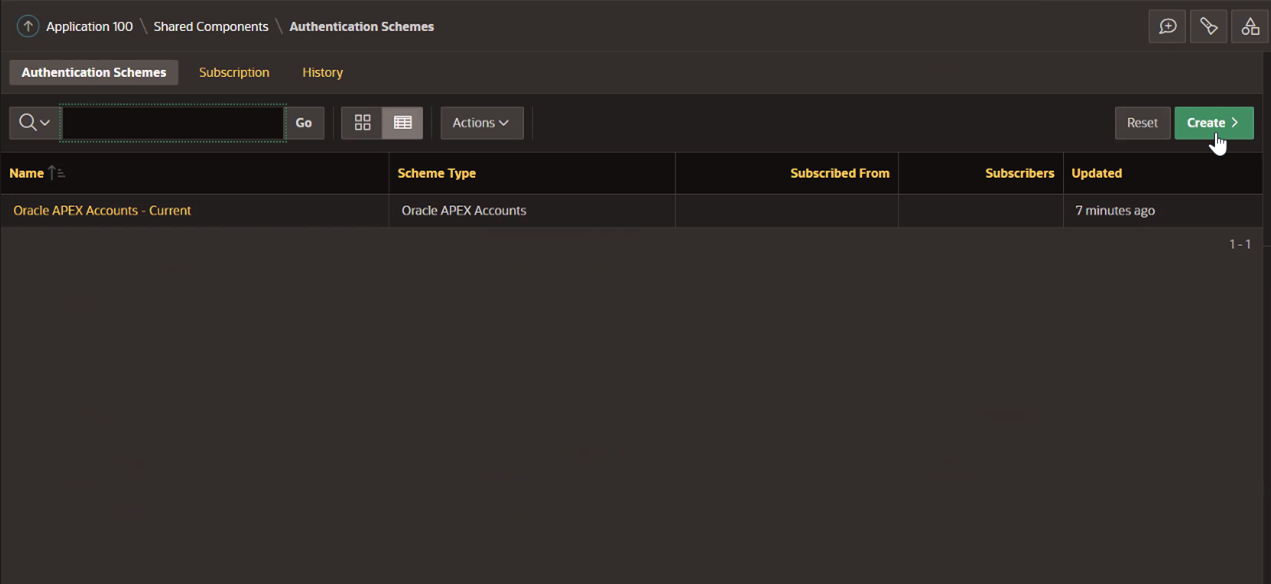
-
Select Based on a pre-configured scheme from the gallery and click Next.
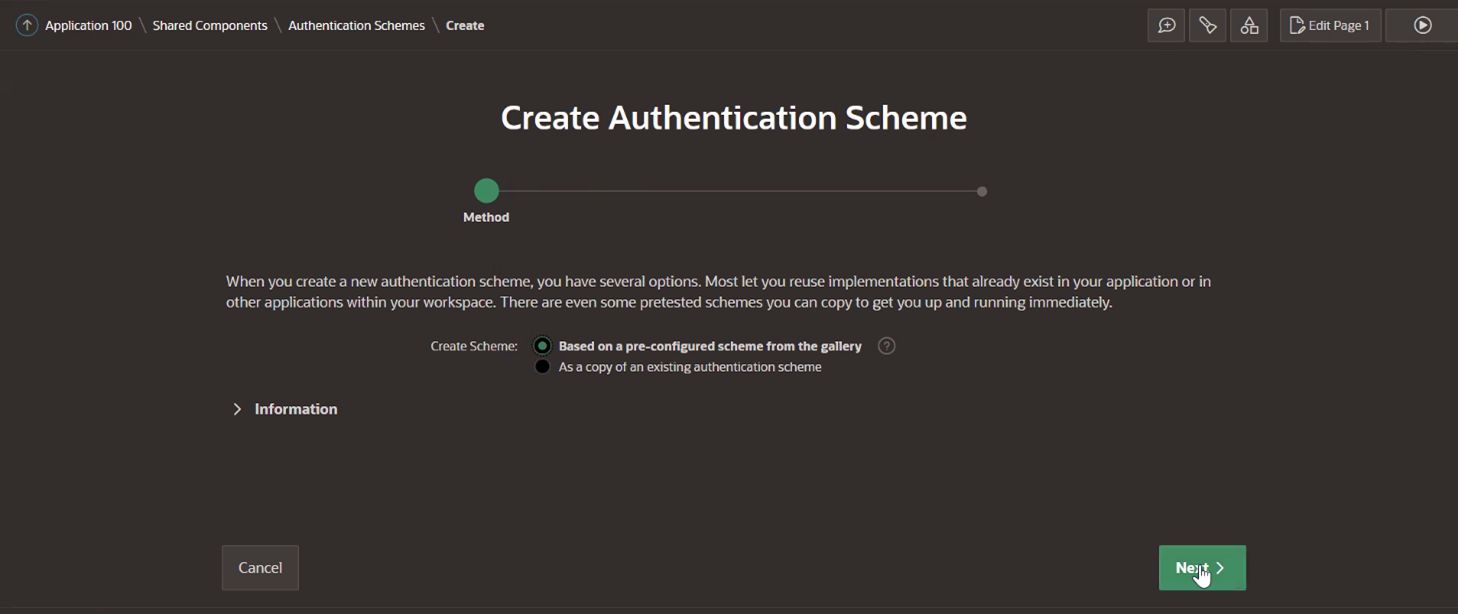
-
Enter the following information and click Create. The Discovery URL will be
https://[idcs-service-url]/.well-known/openid-configuration/.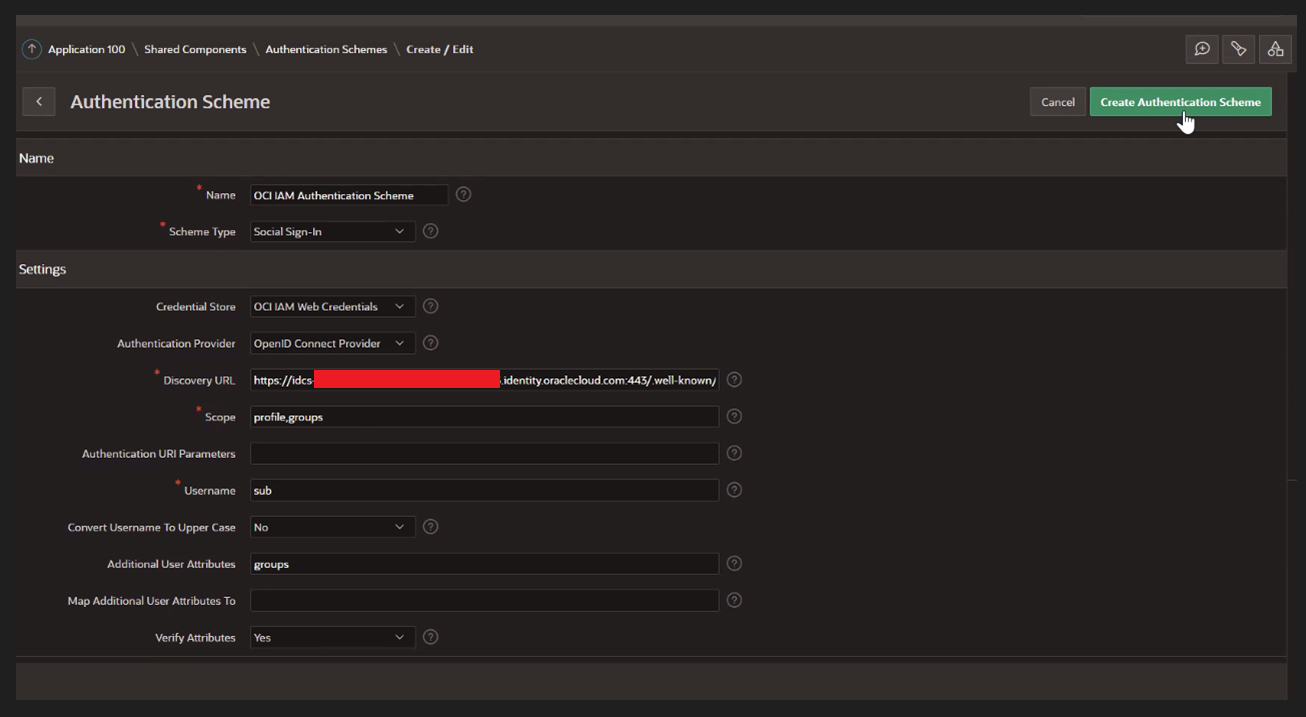
-
Click the created Oracle Identity Cloud Service (IDCS) Authentication Scheme - Current.
-
Click Post-Logout URL tab, select Go-To and URL. In the URL, paste the Oracle APEX application URL from Task 2.6. This URL must match the IDCS post logout redirect URL.
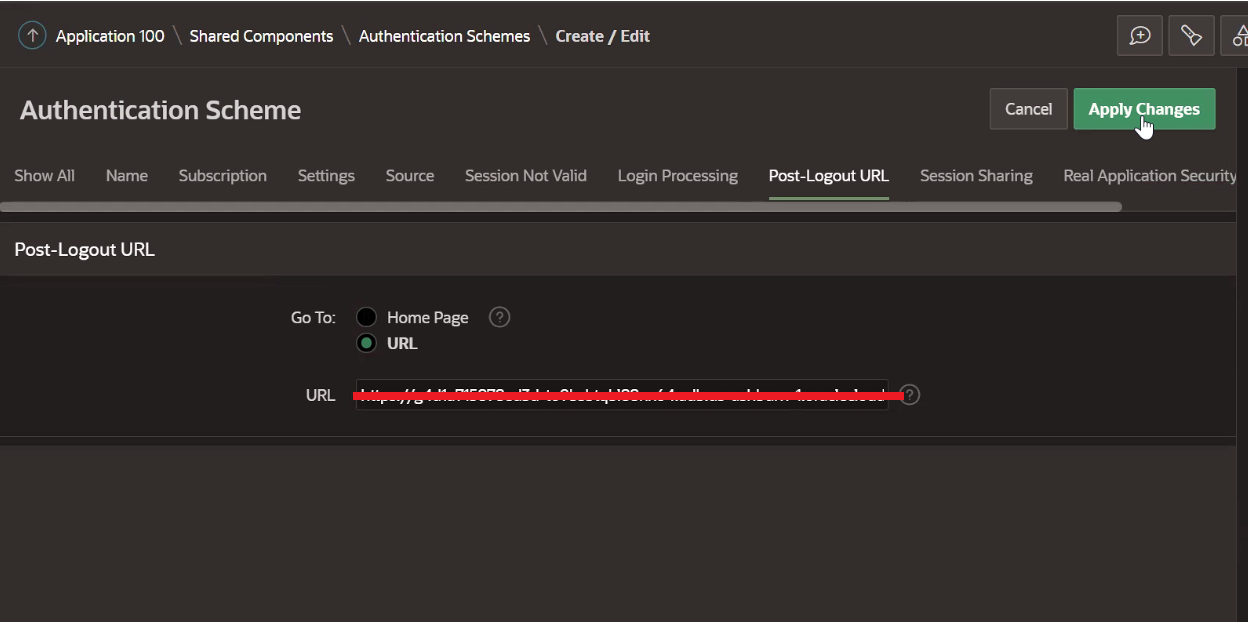
-
Under Security Attributes, update the information and click Apply Changes.
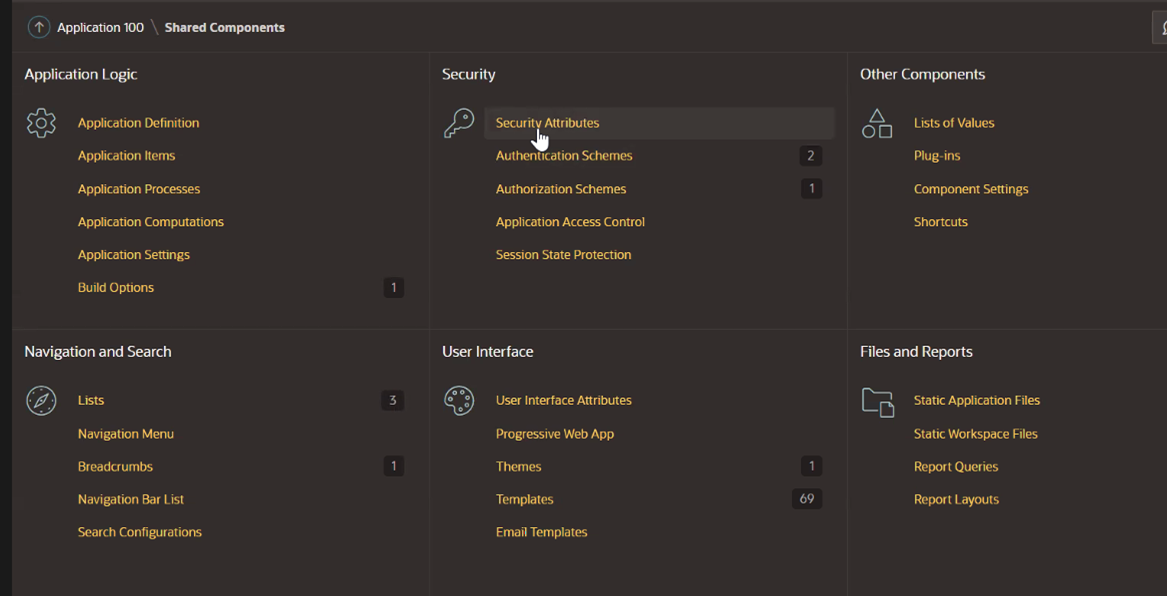
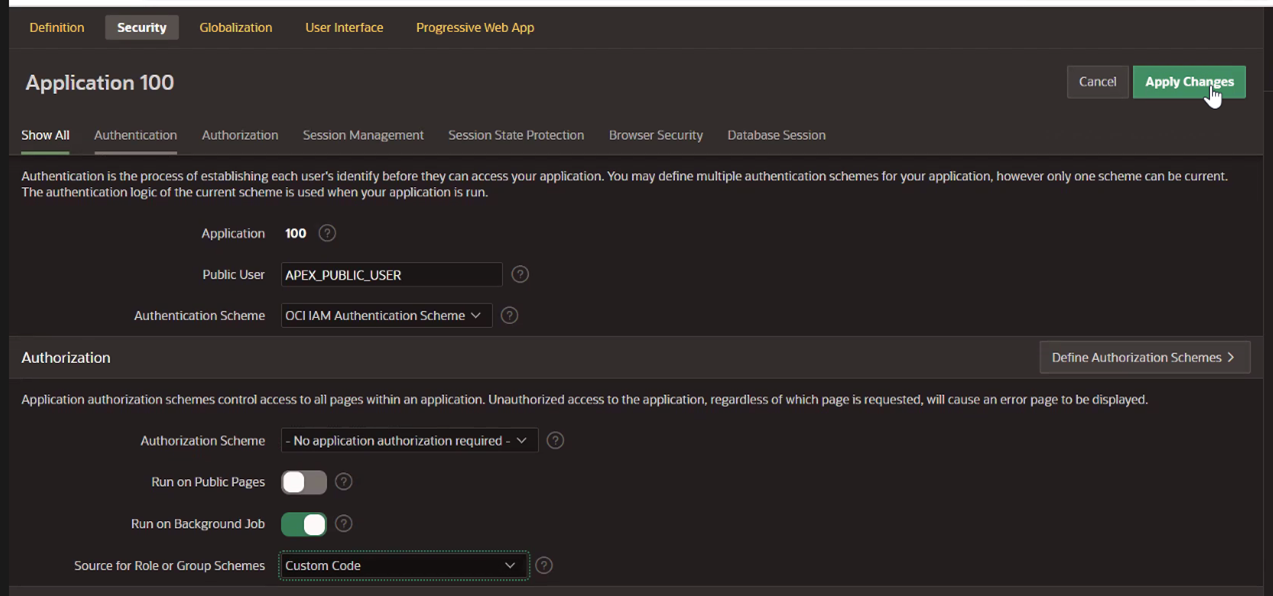
-
(Optional) In the Source section, enter the following PL/SQL code.
Note: This is only required if you want to control authorization, in cases where we want to change the features or behavior of an application based on the groups a user belongs to. For more information, see the Controlling Authorization section at the end of this tutorial.
procedure load_dynamic_groups as l_group_names apex_t_varchar2; begin -- -- add all group names to l_group_names -- for i in 1 .. apex_json.get_count('groups') loop apex_string.push ( p_table => l_group_names, p_value => apex_json.get_varchar2 ( p_path => 'groups[%d].name', p0 => i )); end loop; -- -- save group names in session -- apex_authorization.enable_dynamic_groups ( p_group_names => l_group_names ); end;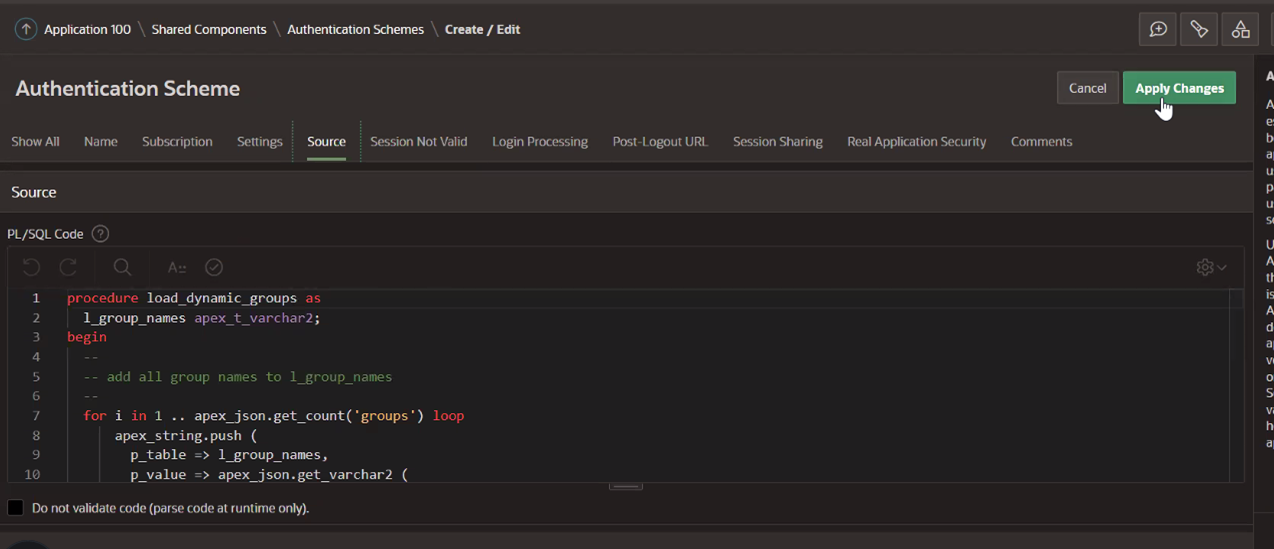
-
(Optional used for step 7) Under Login Processing, enter the following information and save.
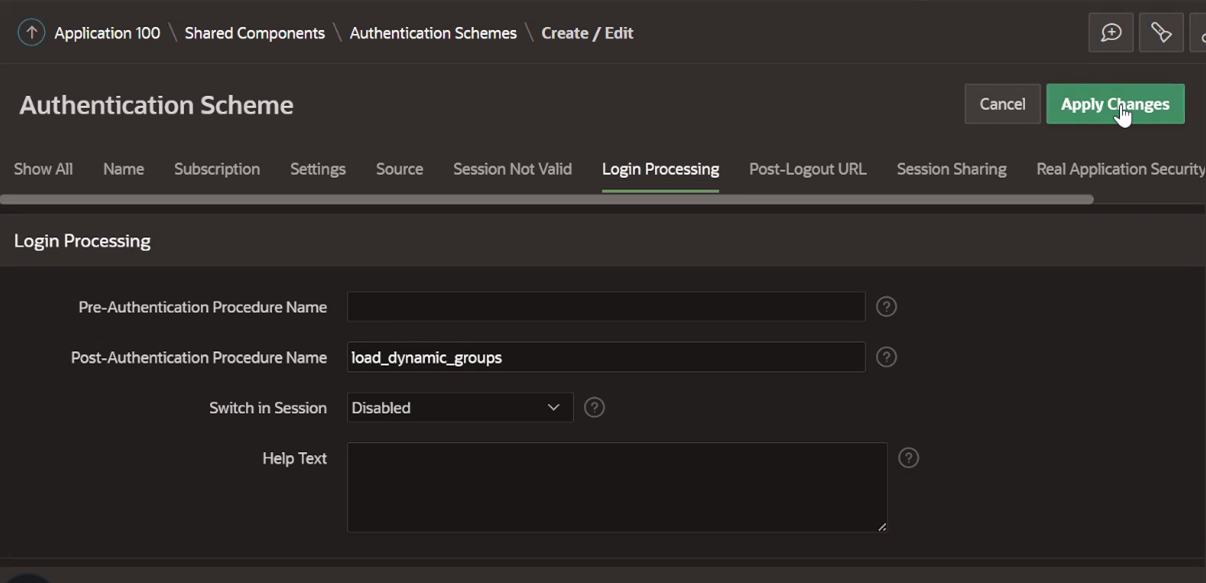
Task 5: Test Login to the Oracle APEX Application
-
Click Run Page.
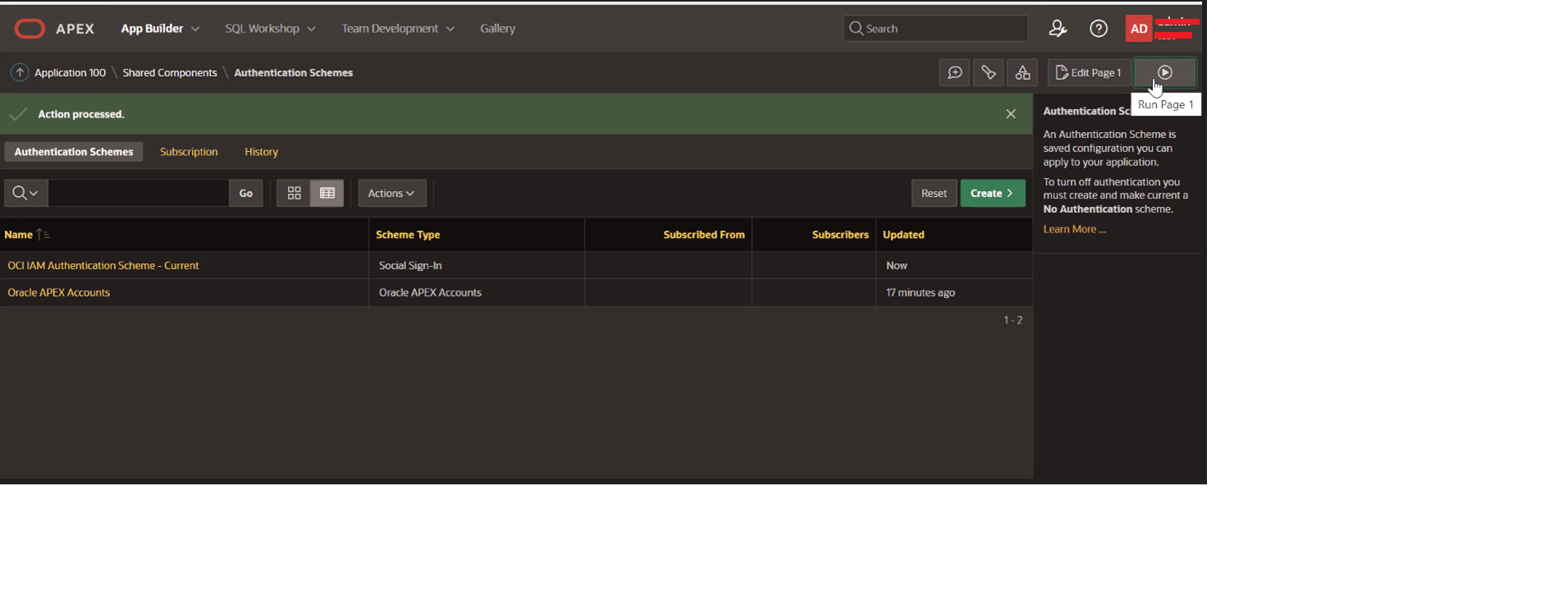
-
Enter the credentials on the prompted login screen. For this tutorial, the account used for authentication is synced from the local active directory and the password resides in the active directory. OCI IAM will collect the username and password and get them validated against active directory.
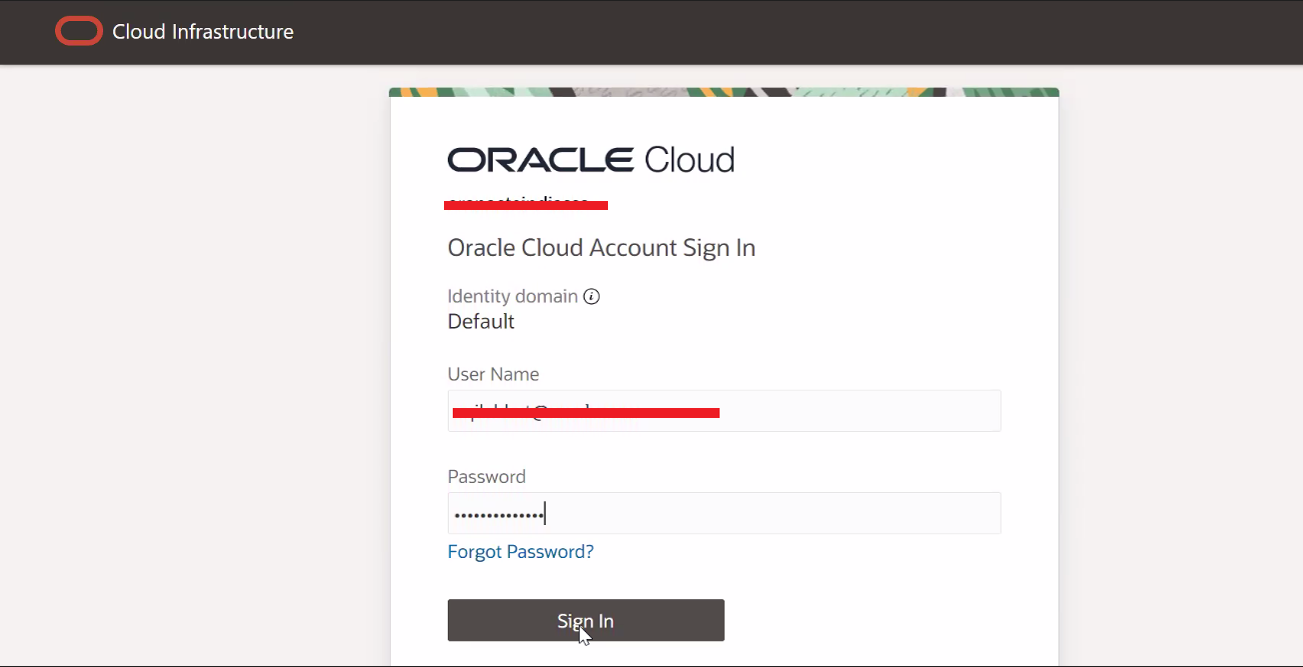
-
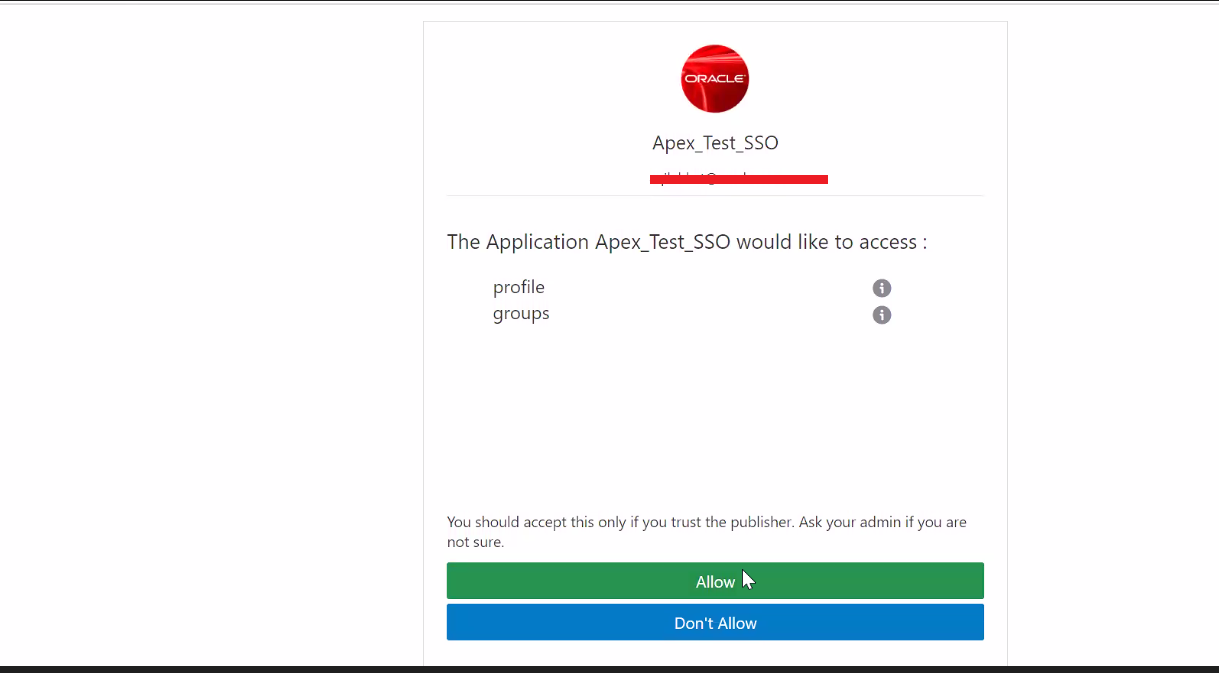
Click Allow.
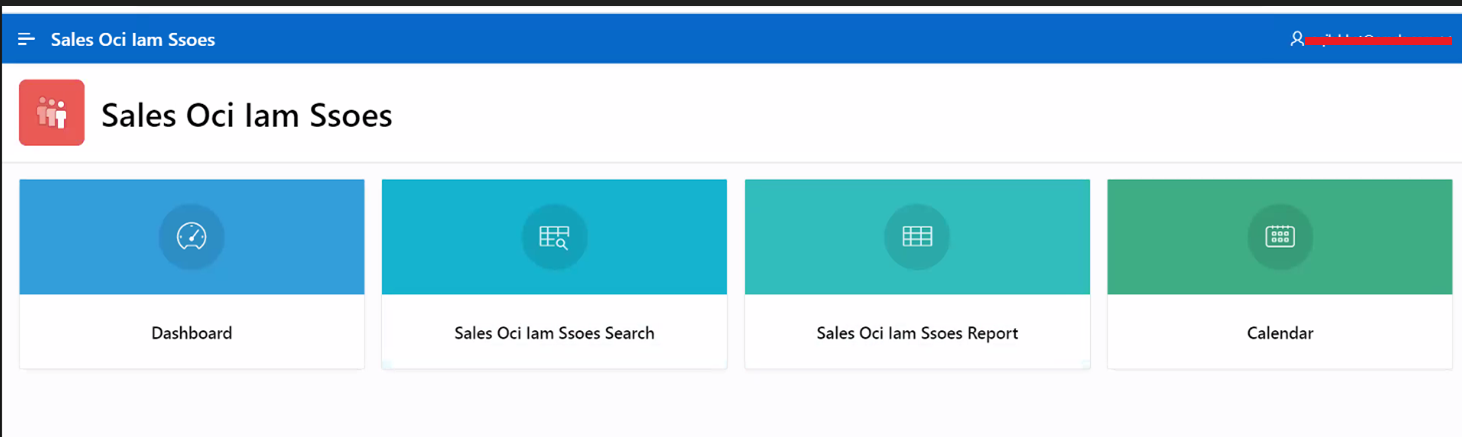
The application landing page is displayed.
Controlling Authorization
You can control authorization by enabling Enforce Grant as Authorization on the confidential application configured for SSO which will only allow users or groups assigned to this application to be able to access the Oracle APEX application. This is shown in Task 2.9.
The other way to control authorization is to use a PL/SQL procedure within the authentication scheme as shown in Task 4.7 and 4.8. After successful authentication, the userinfo_endpoint will be called and the results will be made available to the post-authentication procedure. The JSON results are converted to list of groups and stored in an Oracle APEX session built-in for group management, which can later be tied up with the authorization scheme under shared components to provide access to the application based on the group membership of the users.
Related Links
Acknowledgments
- Author - Aqib Javid Bhat (Senior Cloud Engineer)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Integrate Oracle APEX with Oracle Cloud Infrastructure Identity and Access Management Identity Domains
F78176-02
May 2024