Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Deploy Oracle Cloud Infrastructure Secure Desktops
Introduction
Oracle Cloud Infrastructure (OCI) Secure Desktops service enables an administrator to create an identical set of virtual desktops that individual users can securely access. Administrators can create pools of desktops in their tenancy using existing compute shapes and custom images.
The virtual desktops and OCI configuration are managed by the administrator, allowing non-technical users to easily and securely access the virtual desktop and use it for their daily work.
Objective
- Deploy OCI Secure Desktops and access OCI environment securely.
Prerequisites
- Access to an OCI tenancy and the compartment.
Task 1: Create a Dynamic Group
-
Create a dynamic group. For more information, see Managing Dynamic Groups.
-
Select Match any rules defined below for the dynamic group.
-
Add a matching rule of this form for each compartment that contains desktop pools.
All {resource.type = 'desktoppool', resource.compartment.id = '<OCID-Of-Compartment>'}
Task 2: Create Policies for the Dynamic Group
In the root compartment, add the following policies for the dynamic group created in Task 1. This allows the desktop pools in the dynamic groups to access and interact with the required tenancy level resources.
Allow dynamic-group <dynamic-group> to {DOMAIN_INSPECT} in tenancy
Allow dynamic-group <dynamic-group> to inspect users in tenancy
Allow dynamic-group <dynamic-group> to inspect compartments in tenancy
Allow dynamic-group <dynamic-group> to use tag-namespaces in tenancy
Allow dynamic-group <dynamic-group> to use virtual-network-family in compartment <compartment-name>
Allow dynamic-group <dynamic-group> to {VCN_ATTACH, VCN_DETACH} in compartment <compartment-name>
Allow dynamic-group <dynamic-group> to manage virtual-network-family in compartment <compartment-name>
Allow dynamic-group <dynamic-group> to read instance-images in compartment <compartment-name>
Allow dynamic-group <dynamic-group> to manage instance-family in compartment <compartment-name>
Allow dynamic-group <dynamic-group> to manage volume-family in compartment <compartment-name>
Allow dynamic-group <dynamic-group> to manage dedicated-vm-hosts in compartment <compartment-name>
Allow dynamic-group <dynamic-group> to manage orm-family in compartment <compartment-name>
Allow dynamic-group <dynamic-group> to {VNIC_CREATE, VNIC_DELETE} in compartment <compartment-name>
Allow dynamic-group <dynamic-group> to manage instance-configurations in compartment <compartment-name>
<dynamic-group> is the name of the dynamic group specifying a set of desktop pools.
Task 3: Create Policies for User Authorization
Note: For tenancy administrators, no separate polices are required.
Set up the appropriate user access to enable desktop administrators to manage pools and desktop users to connect to desktops. Two types of groups are required.
-
Administrator Groups: Administrator groups for the desktop administrators that use the service to provide desktops.
Create desktop administrators group with an appropriate name and assign the following policies to the group.
Allow group <desktop-administrators> to manage desktop-pool-family in compartment <compartment-name> Allow group <desktop-administrators> to read all-resources in compartment <compartment-name> Allow group <desktop-administrators> to use virtual-network-family in compartment <compartment-name> Allow group <desktop-administrators> to use instance-images in compartment <compartment-name>Note:
<desktop-administrators>is the group name. -
User Groups: User groups for the desktop users that connect to the desktops.
Create desktop users group with an appropriate name and assign the following policies to the group.
Allow group <desktop-users> to use published-desktops in compartment <compartment-name>
Task 4: Import Custom Image
To use OCI Secure Desktops, you must import a custom image. For more information, see Importing an Image.
Note: To get the list of supported images, see Supported Images.
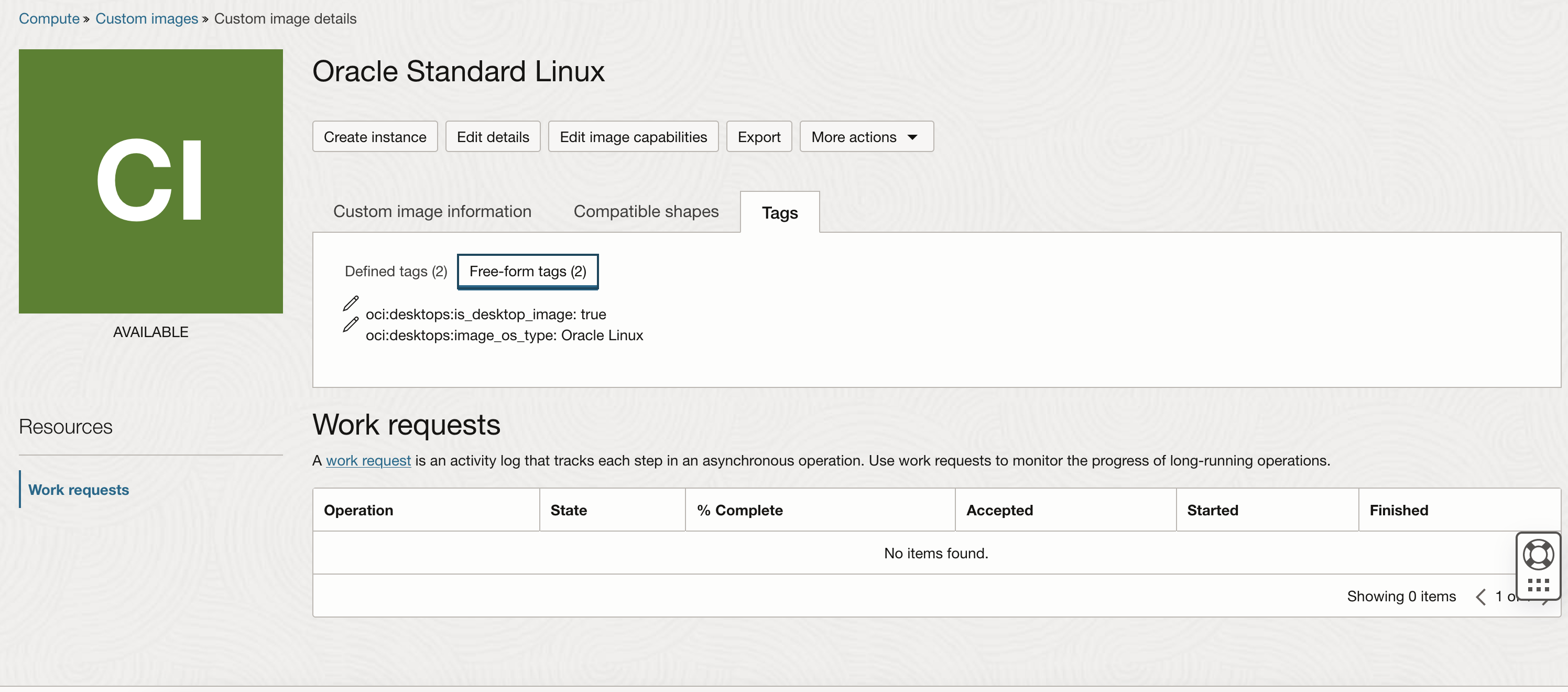
Import images into the compartment and add the following tags for each custom image. These tags allow the service to determine which images to display as an option when you create a desktop pool.
oci:desktops:is_desktop_image true
oci:desktops:image_version <version>, where <version> is a meaningful reference for your use.
oci:desktops:image_os_type [Oracle Linux | Windows]
Task 5: Create a Desktop Pool
After creating the custom image, we will create a desktop pool.
Note: To perform this task, you must be the desktop administrator. The compartment determines which user groups can access the pool.
-
Open the OCI Console and click Compute. Under Secure Desktops, click Desktop Pools.
-
Under List scope, select the compartment in which you want to create the pool and click Create Desktop Pool.
-
Enter a name for the desktop pool, you can edit this value later.
-
Enter the following Optional information.
- Description: Enter a description of the desktop pool.
- Pool Start Time: Select the date and time in UTC, when the pool becomes accessible. You can edit this value later.
- Pool Stop Time: Select the date and time in UTC when the pool stops and becomes inaccessible.
- Add Administrator contact details.
- Select Enable administrator privileges for users on their desktop to allow the desktop users to have administration privileges on their virtual desktops.
-
In the Pool Size section, enter the following information.
- Maximum size: The maximum number of desktops in the pool.
- Standby size: The number of available, unassigned desktops. Standby desktops consume resources because they are running and available for immediate allocation to desktop users. You can edit these values later.
-
Under Placement, select the availability domain in which to locate the desktop resources.
-
Under Image and Shape, select the OS image and shape you want to use for the desktop. For Windows desktop pools, which require dedicated virtual machine hosts, use one of the following preferred shapes. They are mapped to DVH shapes for allocation of OCPUs and memory.
- Flex Low (2 OCPUs, 4GB RAM)
- Flex Medium (4 OCPUs, 8GB RAM)
- Flex High (8 OCPUs, 16GB RAM)
Note: When a pool stops, it is shutdown but not deleted.
-
Optional To enter persistent storage to desktop users by creating a block volume associated with a user, select Enable desktop storage and then select volume size (in GB).
-
In the Networking section, enter the following information.
- Virtual cloud network: Select the virtual cloud network (VCN) for the desktops in this pool.
- Subnet: Select a public subnet in the VCN to use for the desktops.
- Optional Click Show advanced options to select use network security groups to control traffic.
-
In Device Access Policy, specify how the virtual desktop and the client device interact.
- Clipboard access: Specify whether and how the virtual desktop can access the clipboard on the client device.
- Audio access: Specify whether and how the virtual desktop can access the speakers and microphone on the client device. This option is supported only when using the installed client, and the Audio In or microphone value is supported only on Windows desktops.
- Drive mapping access: Specify whether and how the virtual desktop can access drives on the client device. If you select Read or Write, users can move content between their local system and the virtual desktop. You can edit these values later.
Note: When planning networking requirements, be sure to include necessary ingress and egress rules. For example, to the open internet. After a pool is created, its NSG configuration cannot be changed.
-
Under Regular schedule, enter recurring times to start and stop the desktops in the pool. You can edit these values later.
-
Click Create.
Desktop pool will be deployed and once the pool status is ACTIVE as shown in the following image, users should be able to access the desktops.
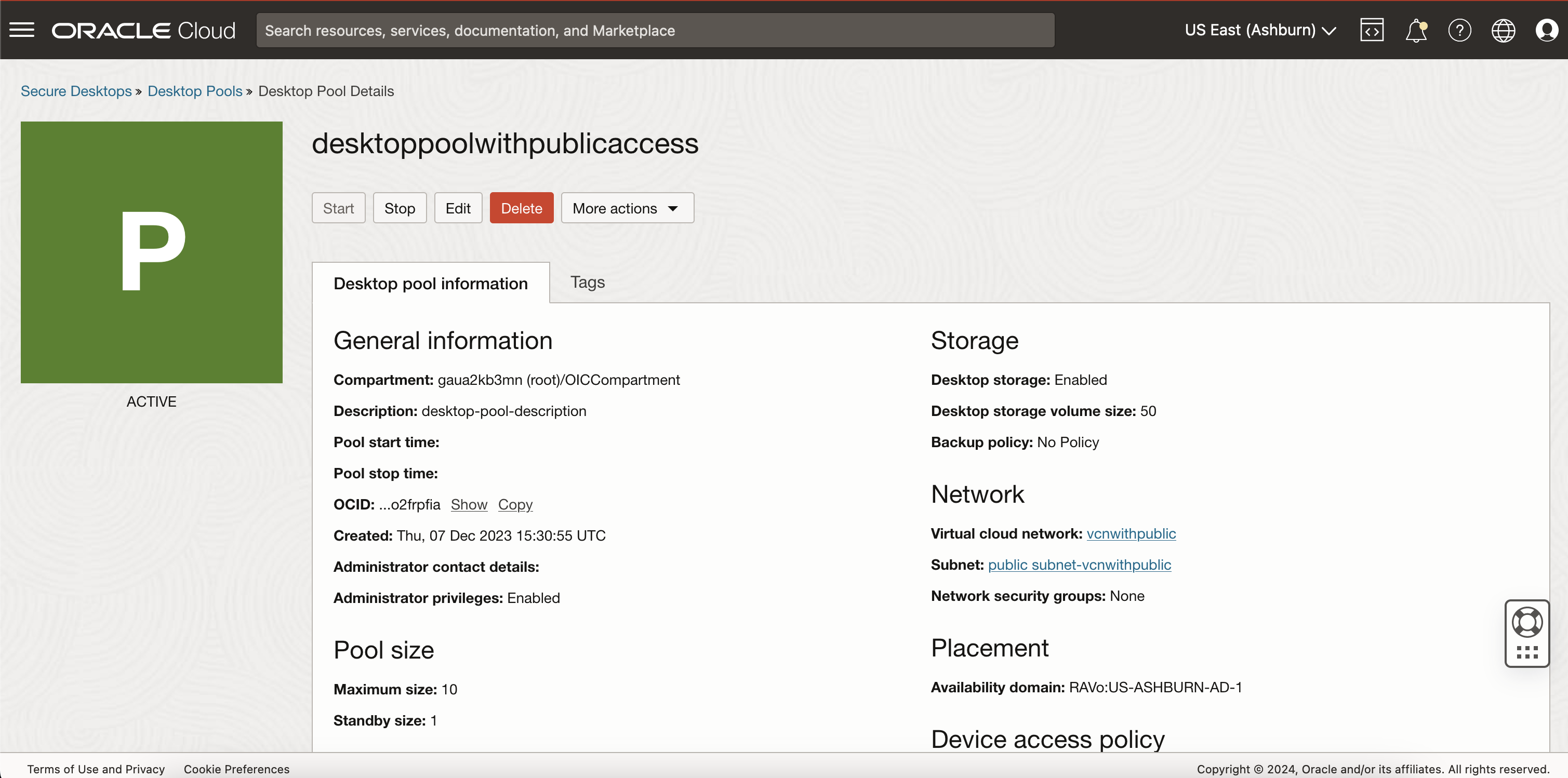
Task 6: Access the Desktop Pool
-
Add users to the
<desktop-users>group which we created in Task 3. -
Edit the following URL with the appropriate region identifier. For more information about identifier values for your region, see Regions and Availability Domains.
https://published.desktops.<RegionIdentifier>.oci.oraclecloud.com/client -
You can share the edited link with the end users who are added in the
<desktop-users>group to access the desktop.
Related Links
Acknowledgments
- Authors - Akarsha I K (Cloud Architect), Maninder Flora (Cloud Architect)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Deploy Oracle Cloud Infrastructure Secure Desktops
F94458-01
March 2024