Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Configure federation and user provisioning between Oracle Identity Cloud Service and CyberArk
Introduction
Companies use Identity Providers (commonly called as IDPs) to manage users/groups, their login/passwords and to authenticate users to access specific resources. If someone wants to access oracle cloud infrastructure (OCI) console to manage/use any resources, they should sign in with their username and password through native login. However, companies have option to federate with their existing IDPs, so that employees can use their existing login credentials to access Oracle Cloud Infrastructure (OCI) resources without the need to remember a different set of credentials.
In short, Identity Federation is the process of delegating an individual’s or entity’s authentication responsibility to a trusted external party. Each partner in federation plays the role of either an identity provider (IdP) or a service provider (SP). In this tutorial, CyberArk is the Identity Provider and Oracle Identity Cloud Service is the Service Provider.
Federation flow
The federation is where the SP trusts identities provided by an IdP. Technically, the identity provider provides a security token which contains information about the user which is used to authorize the user and give access to the particular service.
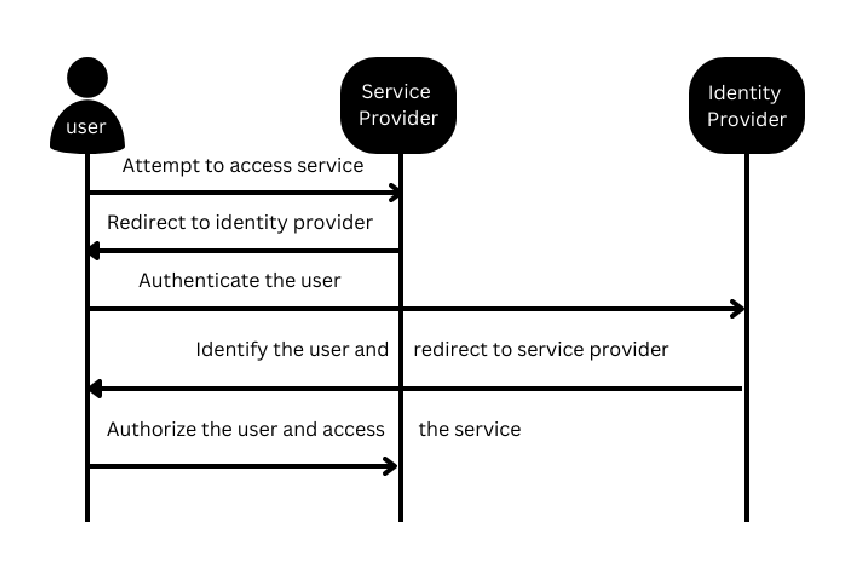
The federated flow is as below.
- The user tries to access service provider using a browser.
- Service Provider sends a redirect request to the user’s browser.
- The browser connects identity provider and identity provider performs an authentication.
- After successful authentication, service provider creates a security token and redirects the browser back to the service provider.
- The browser accesses the service provided by the service provider.
Audience
This tutorial is intended for IT professionals and OCI security/identity administrators.
Objective
In this tutorial, the configuration of federation and automatic user provisioning between CyberArk and Oracle Identity Cloud Service is covered.
Note: As the process is ongoing to replace Oracle Identity Cloud Service with OCI IAM Identity Domains, the concept and configuration of federation and automatic user provisioning will be the same as covered in this tutorial. However, all configuration steps should be performed in the OCI IAM Domain console and there will be no separate Oracle Identity Cloud Service console.
Prerequisites
- Oracle Identity Cloud Service Administrator access
- Access to CyberArk Admin portal
Task 1: Configure federation between CyberArk and Oracle Identity Cloud Service
-
Add the Oracle Cloud Infrastructure web app template.
-
In the CyberArk Admin Portal, select Apps & Widgets, Web Apps, and then click Add Web Apps.
-
On the Search tab, enter Oracle Cloud Infrastructure in the Search field and click the search icon.
-
Next to Oracle Cloud Infrastructure, click Add.
-
In the Add Web App screen, click Yes to confirm.
-
Click Close to exit the Application Catalog.
-
The Oracle Cloud Infrastructure application opens to the Settings page.
-
-
Configure the Settings page.
- Set an app name, description, category, and logo if you want to change them.
-
Configure the Trust page.
-
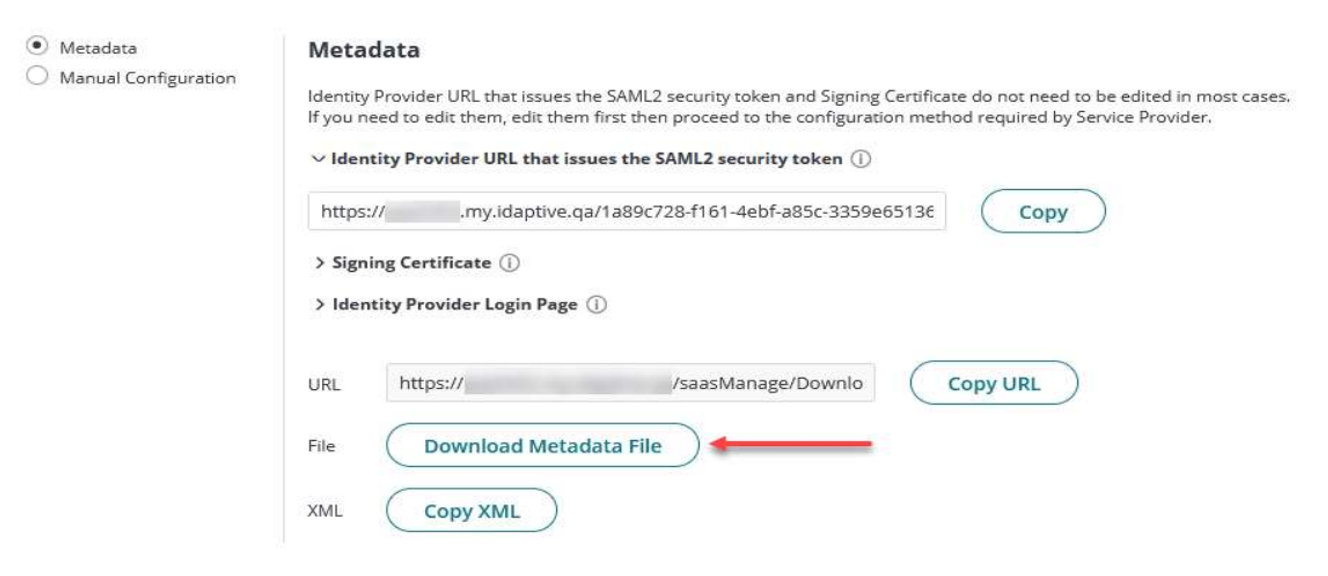
In the Identity Provider Configuration section, select Metadata, then click Download Metadata File to download the IDP metadata. This file is used later when you configure the SAML integration in Oracle Cloud Infrastructure.
-
Configure your Identity Provider URL that issues the SAML2 security token and Signing Certificate, if needed. Your SAML Service Provider will require you to send IDP configuration values in a certain method. Choose the method, then follow the instructions.
-
-
Configure the SAML Response page.
-
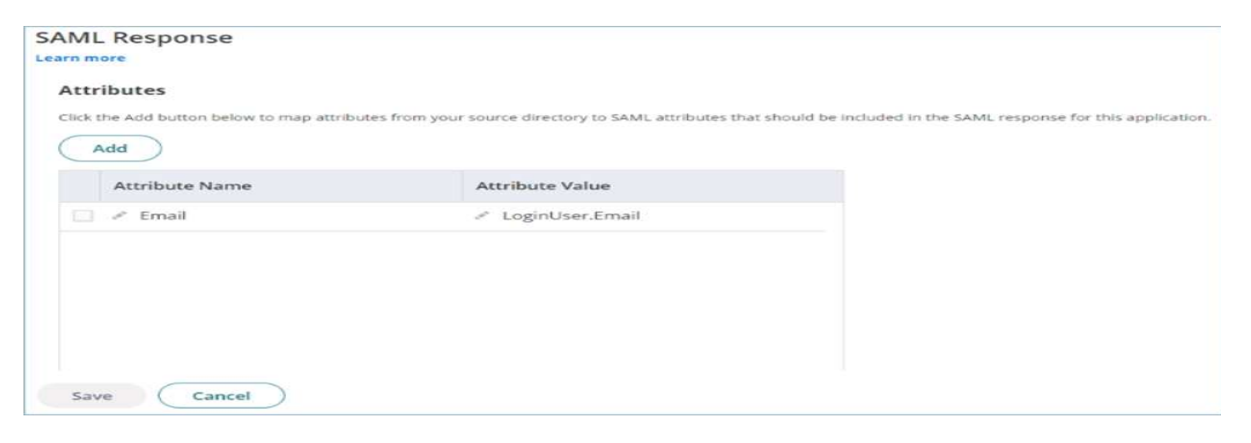
Add email attribute as shown in the image below.
-
-
Configure the Permission page.
- Select users and groups to assign the application.
-
Review and save.
-
Login to the Oracle Identity Cloud Service console and go to Identity Providers under Federation. Add new IDP and enter the following details.
- Name: Enter the name of the Identity Provider.
- Description: Enter the information about the Identity Provider.
- Icon: Click to upload an icon to represent the IDP. The icon must have 48X48 pixels in size and have a transparent background. Supported file types are png, jpg, jpeg.
-
Configure the following details in the Configure IDP tab and click Next.
- Import Identity Provide Metadata: Click to configure federation for the IDP by importing the metadata.
- Metadata: Click Upload. Select the
.xmlfile which contains the IDP metadata you want to import. - Signature Hashing Algorithm: Select the SHA-1 or SHA-256 hash algorithm when signing SAML messages to the IDP.
- Include signing certificate: Select this checkbox to include the Oracle Identity Cloud Service signing certificate with signed SAML messages sent to the IDP. If you don’t want to include the signing certificate, then leave it de-selected.
-
Add the following details in the Map attributes tab.
- Identity Provider User attribute: This is to configure the unique user identifier which comes in the SAML assertion. If you select Name ID, then Oracle Identity Cloud Service matches the user based on the value of the subject NameID in the assertion. If you select SAML attribute, then you must enter a name of the attribute in the assertion and the user will be matched based on the value of the SAML attribute.
- Oracle Identity Cloud Service user attribute: Select the user identity attribute in Oracle Identity Cloud Service which will match the user identity attribute received in the IDP’s SAML assertion.
- Requested NameID format: Select the NameID format which Oracle Identity Cloud Service will specify in the SAML authentication requests sent to the IDP. If you don’t want to specify a format, leave it as None Requested.
-
Export the service provider metadata for future use. Use the same service provider metadata to complete the configuration for CyberArk also.
-
In the Test IDP tab, click Test Login to test the configuration settings for the IDP and click Next.
-
In the Activate pane, click Activate IDP to activate the IDP and click Finish.
-
After activating IDP, go to IDP Policies, select Default Identity Provider Policy.
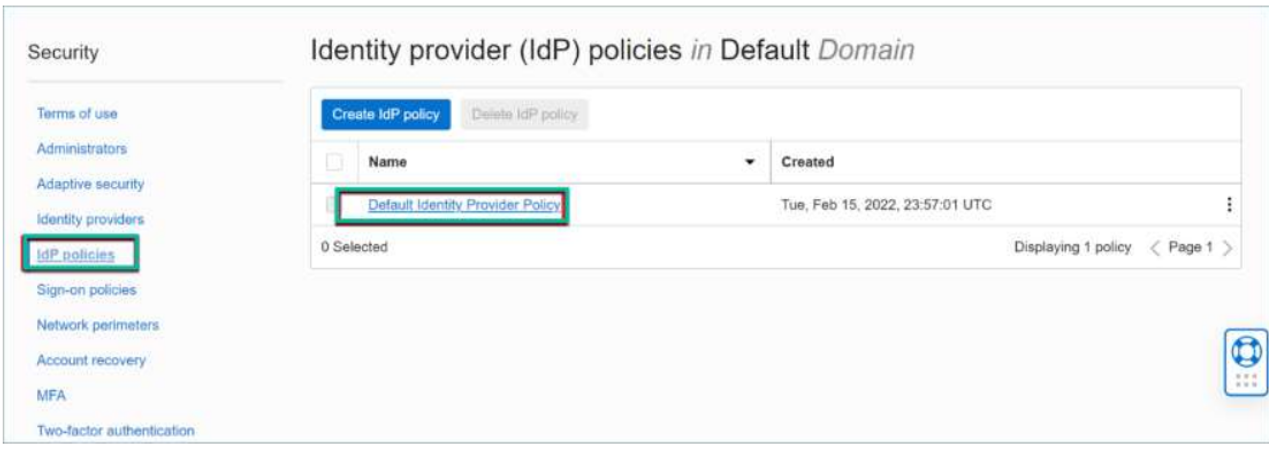
-
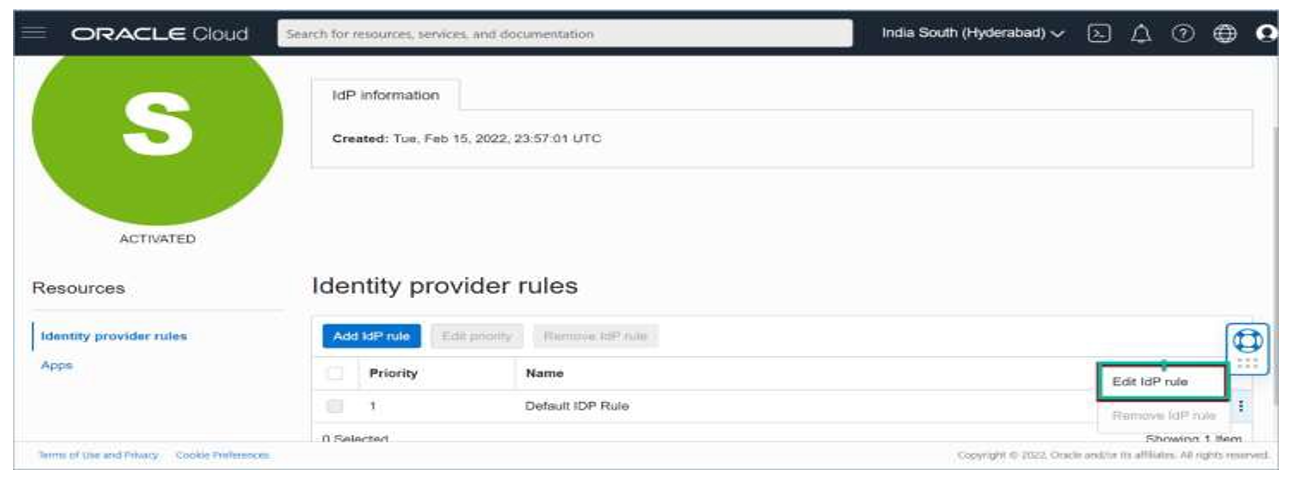
Click Edit IDP rule and include the Identity Provider name you activated in earlier steps in the Assign Identity providers list and save it. Post this user will get an option to login with the CyberArk credentials to the OCI environment.
Task 2: Enable SCIM user provisioning from CyberArk to Oracle Identity Cloud Service
-
Create a confidential application under Oracle Identity Cloud Service, Applications with the following configuration details and save the client ID and client Secret for future use.
- Provide a name for the confidential application.
- In the next screen, select Configure this application as a client now option.
- From the list of available grant types, select the Client Credentials grant type.
- Click on the Add button below, Grant the client access to Identity Cloud Service Admin APIs. Select the User Administrator App Role and click Add.
- Click Next.
- On the Resources tab, do not update anything and click Next.
- On the Authorization tab, do not update anything and click Finish.
- A message pops up saying application added with client credentials. Note the Client ID and Client Secret.
-
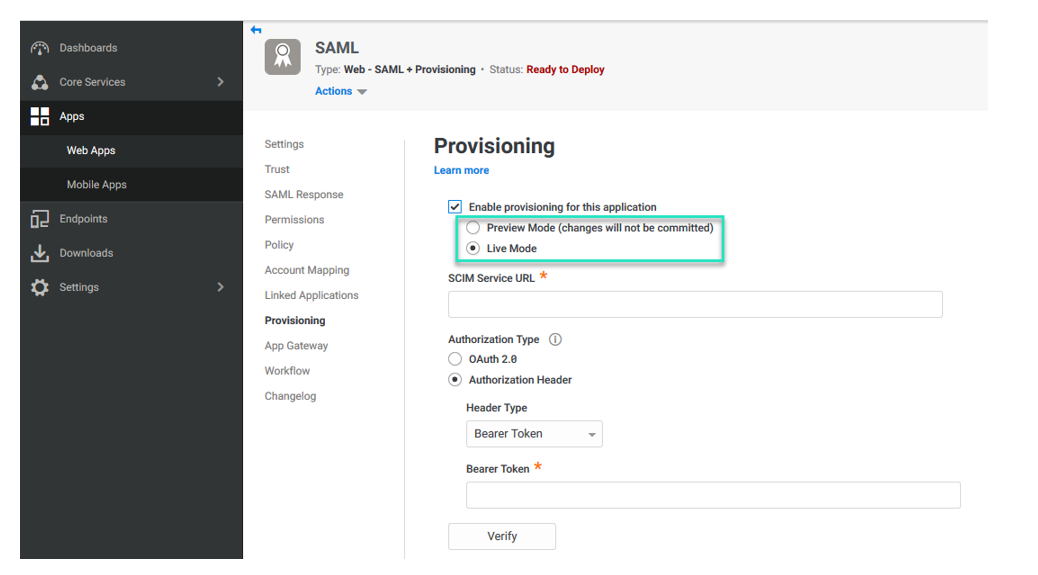
Configure the following details under the Provisioning tab in the CyberArk application.
-
In the Admin Portal, go to the Provisioning page of your deployed application.
-
Select Enable provisioning for this application.
-
Select Live Mode.
-
Enter the service provider’s SCIM URL for the SCIM Service URL.
-
Select Authorization header as Authorization type.
-
Select Header Type as bearer and paste your access token (base encoded value of ClientID:Clientsecret) into the Bearer Token field.
-
Verify the connection.
-
Once the verification is successful, you will be able to provision the users and groups.
Errors and troubleshooting
-
Authorization Type as “Oauth 2.0”, requires a user to validate the credentials as it’s using three-legged flow. Due to which the access token is valid only for one hour by default and whenever the user logs out from the session, they are asked to re-validate the provisioning configuration the next time they log in. This does not meet the requirement of automatic user provisioning. Therefore, it is not recommended to use this authorization type.
-
Issue: When you use the Authorization Type as “Authorization Header” (as described in the user provisioning session) and provision users, the following error message is displayed Unable to validate the user credentials.
Resolution: Verify if the
/GetServiceProviderConfigAPI call (used to get information related to schemas and endpoints that were supported) is failing with unauthorized error and add the schema and version manually through the following config flags. Also, the user endpoint call is case sensitive and is treating “users” and “Users” endpoint differently so add one more config for not changing the case.Generic SAML_doNotChangeSCIMURLCase.OCI = true Generic SAML_ScimVersion.OCI = v2 Generic SAML_Schemas_User.OCI (user schema )
Related Links
Acknowledgments
Author - Ranjini Rajendran (Senior Cloud Engineer)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Configure federation and user provisioning between Oracle Identity Cloud Service and CyberArk
F80211-01
April 2023
Copyright © 2023, Oracle and/or its affiliates.