Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Deploy an HA Samba Cluster with Windows Active Directory on OCI
Introduction
We will discuss how to configure high availability (HA) with automatic failover of Samba on Ubuntu instances into Oracle Cloud Infrastructure (OCI). This solution is a robust and reliable file server infrastructure, leveraging the power of a clustered Server Message Block (SMB) setup and completely license free. The cost is related only to the consumption (oCPU and block volume size).
The benefits of implementing a clustered SMB file server service in an organization are:
-
Reliability: The clustered configuration ensures high availability, minimizing the risk of downtime and ensuring constant access to critical files.
-
Fault Tolerance: In the event of a server failure, the clustered setup provides automatic failover, guaranteeing uninterrupted access to files and maintaining business continuity.
-
Resource Utilization: Efficient resource allocation ensures optimal utilization of server resources, maximizing productivity while minimizing operational costs.
-
High Performance: Implementing a clustered SMB file server is a strategic move towards creating a resilient, high performance IT environment tailored to meet the evolving business needs.
Architecture
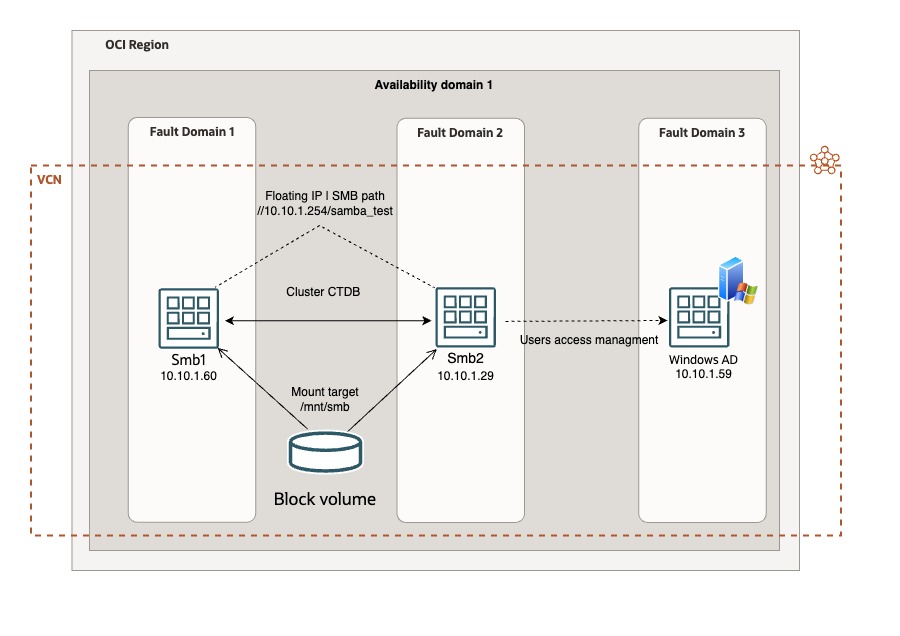
Objective
- Deploy a reliable file server in HA supporting SMB protocol integrated with Windows Active Directory.
Prerequisites
-
Access to an OCI tenancy.
-
Two Linux Ubuntu VMs.
-
One block volume.
Task 1: Set up the Environment
-
Create two Ubuntu 22.04 compute instances.
-
On both compute instances, establish the directory where you intend to store files and configure the Samba server. For example:
/mnt/smb. -
Create a block volume with the required size for your SMB datastore, and attach it to both compute instances (iSCSI, read/write - sharable). For more information, see Attaching a Volume to Multiple Instances.
-
Note the dev name assigned to the block volume attached using the following command.
sudo lsblk -
Assign a secondary private IP address on the first node. This is a floating IP address. For example:
10.10.1.254. -
Update the
/etc/hostsfile on both Ubuntu instances to include the IP addresses and hostnames of all nodes, including the Windows Active Directory server that will be used for user authentication. For example:10.10.1.60 smb1,10.10.1.29 smb2,10.10.1.59 ad.testad.oci testad.oci AD. -
Configure the
iptableson both Ubuntu instances according to the needs.Note: Ubuntu instances come with preconfigured iptables. The sixth rule in the INPUT section rejects everything else, so you have the option to either delete it or add specific protocols and ports that are allowed before this rule.
-
Install and configure the Oracle Cloud Infrastructure Command Line Interface (OCI CLI) on both Ubuntu instances. For more information, see Install the OCI CLI and configure it (configuration command: oci setup config).
Note: Install OCI CLI into
/usr/binor your user path to avoid permission problems, by default it is root.bash -c "$(curl -L https://raw.githubusercontent.com/oracle/ocicli/master/scripts/install/install.sh)"
Task 2: Configure Oracle Cluster File System version 2 (OCFS2)
Oracle Cluster File System version 2 (OCFS2) is a general purpose shared disk file system developed by Oracle Corporation and released under the GNU General Public License.
To manage a shared writable block volume, we have to deploy OCFS2. For more information, see A Simple Guide to Oracle Cluster File System (OCFS2) using iSCSI on Oracle Cloud Infrastructure.
-
Run the following command on both nodes.
sudo apt-get install ocfs2-tools -y -
Update the value of
O2CB_ENABLEDfrom false to true in the/etc/default/o2cbfile.O2CB_ENABLED=true -
Enter the following code in the
/etc/ocfs2/cluster.conffile.Note: Take care of indentation and format of the file.
cluster: name = ocfs2 heartbeat_mode = local node_count = 2 node: cluster = ocfs2 number = 0 ip_port = 7777 ip_address = 10.10.1.60 name = smb1 node: cluster = ocfs2 number = 1 ip_port = 7777 ip_address = 10.10.1.29 name = smb2 -
Now, start the
o2cbservice.sudo /etc/init.d/o2cb start -
Format the block volume device with OCFS2 file system. Run the following command only on the first node.
Note: The path of the device that we noted in step 3.
sudo mkfs.ocfs2 "MyOCFS2Cluster" /dev/sd* -
Register the cluster using the following command.
sudo o2cb register-cluster ocfs2 -
Mount the block volume on the directory assigned for Samba server. For example:
/mnt/smb.sudo mount /dev/sd* /mnt/smb -
Check the cluster status using the following command.
sudo o2cb list-nodes ocfs2 -
Enable the services using the following command.
sudo systemctl enable o2cb sudo systemctl enable ocfs2 -
Update the
fstabin/etc/fstabto mount the block volume automatically at startup.Note: Adjust the
/dev/sd\*device according to your dev name./dev/sd* /mnt/smb ocfs2 _netdev,defaults 0 0
Task 3: Set up the Samba Cluster
Samba allows file and print sharing between computers running on Microsoft Windows and Unix. It is an implementation of dozens of services and protocols, including: NetBIOS over TCP/IP (NBT) and SMB - sometimes referred to as Common Internet File System (CIFS).
-
Install Samba and Cluster Trivial Database (CTDB) on both nodes using the following command.
sudo apt-get install ctdb samba samba-common winbind smbclient -y -
Edit the Samba configuration file.
sudo nano /etc/samba/smb.confCopy and paste the following parameters.
Note:
- You have to configure it accordingly with your environment and windows
domain/workgroup. - The
netbios nameparameter has to be the same for all your nodes.
[global] server string = samba_server workgroup = TESTAD password server = ad.testad.oci realm = testad.oci winbind enum groups = yes winbind enum users = yes winbind use default domain = yes security = ADS debuglevel = 2 wins support = no idmap config TESTAD : backend = rid idmap config TESTAD : range = 10000 - 50000 idmap config * : backend = tdb idmap config * : range = 1000-9999 template shell = /bin/false winbind offline logon = false interfaces = lo ens3 clustering = yes guest ok = yes bind interfaces only = no disable netbios = no netbios name = sambacluster1 smb ports = 445 log file = /var/log/samba/smb.log max log size = 10000 veto files = /._*/.DS_Store/.Trashes/.TemporaryItems/ delete veto files = yes nt acl support = yes inherit acls = yes map acl inherit = yes map archive = yes map hidden = yes map read only = yes map system = yes store dos attributes = yes inherit permissions = yes unix extensions = no [samba_test] path = /mnt/smb browseable = yes writeable = yes read only = no public = yes inherit acls = no admin users = "testad.oci\administrator" create mask = 0744 directory mask = 0755 - You have to configure it accordingly with your environment and windows
-
To set up the cluster, edit the CTDB configuration file.
sudo nano /etc/ctdb/ctdb.confCopy and paste the following parameters.
CTDB_NODES=/etc/ctdb/nodes CTDB_PUBLIC_ADDRESSES=/etc/ctdb/public_addresses CTDB_RECOVERY_LOCK="/mnt/Samba/ctdb/.ctdb.lock" CTDB_MANAGES_SAMBA=yes CTDB_MANAGES_WINBIND=yes CTDB_SERVICE_SMB=smbd -
Edit the nodes configuration file for configuring the cluster.
sudo nano /etc/ctdb/nodesAdd the IP addresses of your nodes.
10.10.1.60 10.10.1.29 -
Edit the CTDB public address configuration file (the floating IP address).
Sudo nano /etc/ctdb/public_addressesAdd floating IP address.
10.10.1.254/0 ens3 -
We have to add the script to manage the floating IP address at the OCI level and to migrate it automatically in case of failover.
Sudo nano /etc/ctdb/functionsAdd the following code after the add_ip_to_iface () section.
Note: Change the Oracle Cloud Identifier (OCID) and the hostname with your nodes VNICs OCID and the hostname.
##### OCI vNIC variables server="`hostname -s`" smb1vnic="ocid1.vnic.oc1.eu-frankfurt-1.YOUR_NODE1_VNIC_OCID" smb2vnic="ocid1.vnic.oc1.eu-frankfurt-1.YOUR_NODE2_VNIC_OCID" vnicip="10.10.1.254" #export LC_ALL=C.UTF-8 #export LANG=C.UTF-8 #touch /tmp/vip.log ##### OCI/IPaddr Integration if [ $server = "smb1" ]; then /usr/bin/oci network vnic assign-private-ip --unassign-if-already-assigned --vnic-id $smb1vnic --ip-address $vnicip 2>/dev/null else /usr/bin/oci network vnic assign-private-ip --unassign-if-already-assigned --vnic-id $smb2vnic --ip-address $vnicip 2>/dev/null fi -
Use the following command to troubleshoot the floating IP address migration if it does not work.
sudo journalctl -u ctdb.service
Task 4: Integrate Windows Active Directory
-
To integrate user access with Windows Active Directory server, we have to install Kerberos on both nodes.
sudo apt -y install winbind libpam-winbind libnss-winbind krb5-config samba-dsdb-modules samba-vfs-modules -
Use the following command to configure Kerberos.
sudo nano /etc/krb5.conf -
Check the configuration file with the following code.
Note: Remember to use the Windows domain/realm configured in your environment.
[libdefaults] default_realm = TESTAD.OCI # The following krb5.conf variables are only for MIT Kerberos. kdc_timesync = 1 ccache_type = 4 forwardable = true proxiable = true # The following encryption type specification will be used by MIT Kerberos. # if uncommented. In general, the defaults in the MIT Kerberos code are # correct and overriding these specifications only serves to disable new # encryption types as they are added, creating interoperability problems. # The only time when you might need to uncomment these lines and change # the enctypes is if you have local software that will break on ticket # caches containing ticket encryption types it doesn't know about (such as # old versions of Sun Java). # default_tgs_enctypes = des3-hmac-sha1 # default_tkt_enctypes = des3-hmac-sha1 # permitted_enctypes = des3-hmac-sha1 # The following libdefaults parameters are only for Heimdal Kerberos. fcc-mit-ticketflags = true [realms] TESTAD.OCI = { kdc = ad.testad.oci admin_server = ad.testad.oci -
The last step is join both hosts into the Windows domain using the following command.
Sudo net ads join -U Administrator -S testad.oci
Now, try to connect your client to the Samba server using the floating IP address and Windows Active Directory users (for example: //10.10.1.254/samba_test) and test the business continuity if one nodes is shutdown or restarted.
The new Samba cluster is ready now!
Related Links
Acknowledgments
- Author - Marco Santucci (EMEA Enterprise Cloud Solution Architect)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Deploy an HA Samba Cluster with Windows Active Directory on OCI
F92316-02
February 2024
Copyright © 2024, Oracle and/or its affiliates.