Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Integrate OCI Streaming with Other Authorization Methods Using OCI API Gateway
Introduction
We often need our applications to consume Oracle Cloud Infrastructure (OCI) REST services. There are several ways to guarantee security between components, ensuring that the application can authenticate securely to the backend service.
Most of the time, this task is native within Oracle Cloud, as there are several ways to secure the network and access to existing services. Just a few settings and you are done. However, there are cases where the application may offer additional security and connectivity requirements. The use case of this tutorial meets a very common need in the hybrid or multicloud scenario (on-premises connected to Oracle Cloud, or Oracle Cloud connected to another cloud).
Let’s present the following scenario:
-
Application on an on-premises network connected to Oracle Cloud through Fast-Connect/VPN.
-
Application needs to consume an OCI Streaming service.
-
OCI service does not have an authentication mechanism that meets the application consumer’s possibilities.
-
Application needs to authenticate using OAuth2 to be able to access the service securely.
Therefore, the tutorial provides the following solution:
-
Configure the Oracle Identity Cloud Service cloud’s own Identity Provider to authenticate through OAuth2.
-
Configure OCI API Gateway to integrate with Oracle Identity Cloud Service to authenticate via an obtained token.
-
Code a function to produce the authentication for OCI Streaming (
draft-cavage-http-signatures-08method). -
Create groups and policies to limit access to cloud resources.
-
Deliver an Identity Provider that allows you to pass the Client ID, and Secret ID and obtain an authentication token.
-
Deliver a functional API Gateway REST service that authenticates through the obtained token and allows the consumer to use the OCI Streaming services.
Note: The OCI Functions code can be downloaded here: OAuthOCIService-fn.zip.
Objectives
-
Allow an external application to consume OCI REST services with OAuth2 authentication.
-
Provide an OAuth2 authentication service on OCI.
-
Configure OCI API Gateway and OCI Functions to run OCI services via a token.
Prerequisites
-
An OCI API Gateway instance created and exposed to the Internet. For more information, see Creating Your First API Gateway In The Oracle Cloud.
-
Network Connectivity between OCI API Gateway, OCI Functions and OCI PaaS resource.
-
VCN/Subnets
-
Security list
-
NAT Gateway/Internet Gateway
-
Public/Private Networks
-
-
Knowledge of OCI Functions and OCI REST API to code a call for the OCI service.
Task 1: Configure OAuth2 with Oracle Identity Cloud Service
-
Obtain the OCI API Gateway Parameters: Let’s start to configure the OAuth2 mechanism. We need to integrate your OCI API Gateway instance into an identity provider by configuring the Oracle Identity Cloud Service from Oracle Cloud to be the identity provider.
-
Go to the OCI API Gateway instance and copy Hostname. This information will be used in your Oracle Identity Cloud Service resource server configuration in the next step.

-
-
Create a Resource Application: We need to create an OAuth2 authorizer for your application. We can do it with the Oracle Identity Cloud Service in Oracle Cloud.
-
In the OCI Console, go to Identity & Security and select Federation.

-
Click OracleIdentityCloudSevice.

-
Click the Oracle Identity Cloud Service Console link for your Oracle Identity Cloud Service instance.

-
We will create two applications. Click Applications and Services.

-
In the Applications, click Add.

-
Select Confidential Application to start configuring your resource server.

-
We will configure the first application. Enter a Name in your resource server application and click Next.
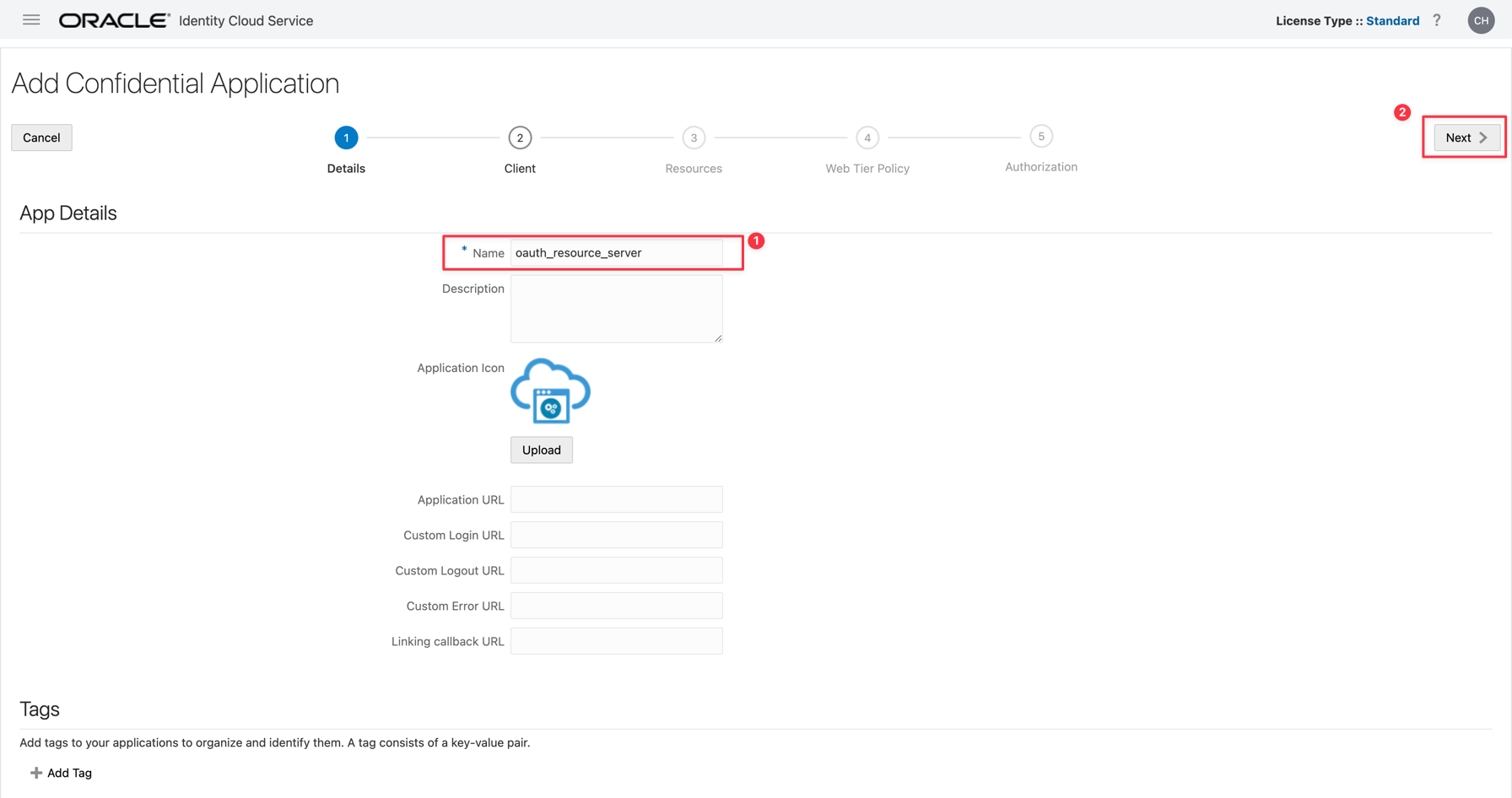
-
Click Skip for later. We need to configure the resource only.

-
Enter your API Gateway hostname obtained in Step 1.

-
Click Add Scope and enter the scope information.

-
Review your scope information, click Next two times and click Finish.

-
Click Activate to activate your application.

-
-
Create a Client Application.
-
In Applications, click Add.

-
Select Confidential Application to start configuring your resource server.

-
Enter a Name for your application and click Next.

-
Select Configure the application as a client now to enable the configurations for your client application. Select Client Credentials, JWT Assertion and On behalf of.

Note: If you want to validate OAuth2 in your function code, you MUST set the Introspect flag. This will enable the
/oauth2/v1/introspectOracle Identity Cloud Service REST API service.
-
Scroll down and click Add Scope.
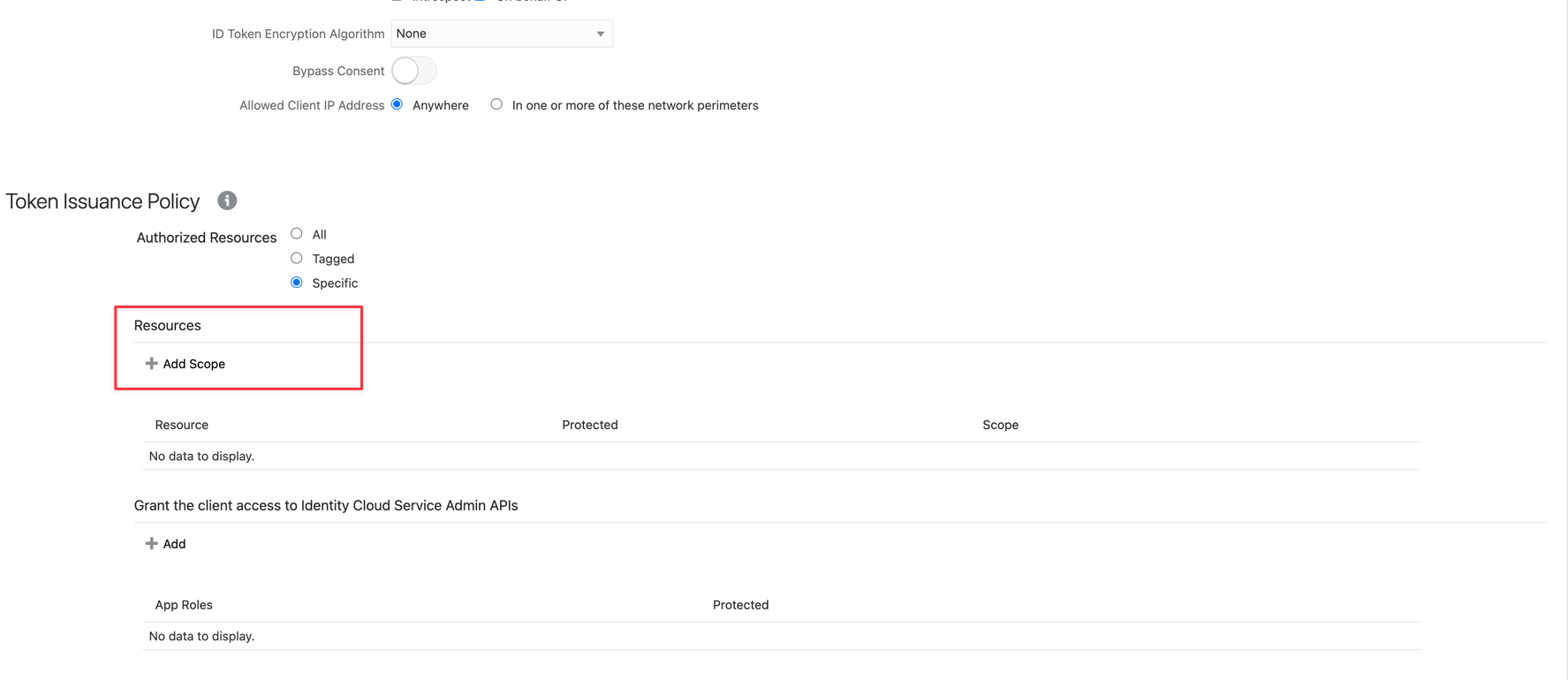
-
Find your resource application created before (
oauth_resource_server) and click Add.
-
You can see your scope added to your application. Click Next.

Note: Note the scope value, you will need to use it to request a token.
-
Skip the Resources and the Web Tier Policy window. In Authorization, select Enforce Grants as Authorization and click Finish.

-
Note the Client ID and the Client Secret information. You will need this to obtain your token.

-
Click Activate to activate the application and your OAuth2 authorizer is ready to test.

-
-
Get a Token: Now we can test the OAuth2 authorizer to obtain the token.
-
Compose the URL for the authorizer. You can obtain this by getting your Oracle Identity Cloud Service URL in the browser. In the Oracle Identity Cloud Service URL, you can see something like this:
https://idcs-xxxxxxxxxxxxx.identity.oraclecloud.com/ui/v1/adminconsole. -
You will need the URL link until the
oraclecloud.com, which is the root endpoint. For example,https://idcs-xxxxxxxxxxxxx.identity.oraclecloud.com. -
We need to add the oAuth authentication path. This URL will be executed as a
POSTREST request. For example,https://idcs-xxxxxxxxxxxxx.identity.oraclecloud.com/oauth2/v1/token. You will need to enter some parameters to request the token. -
Enter the credentials as Basic Authentication, Client ID and Client Secret.
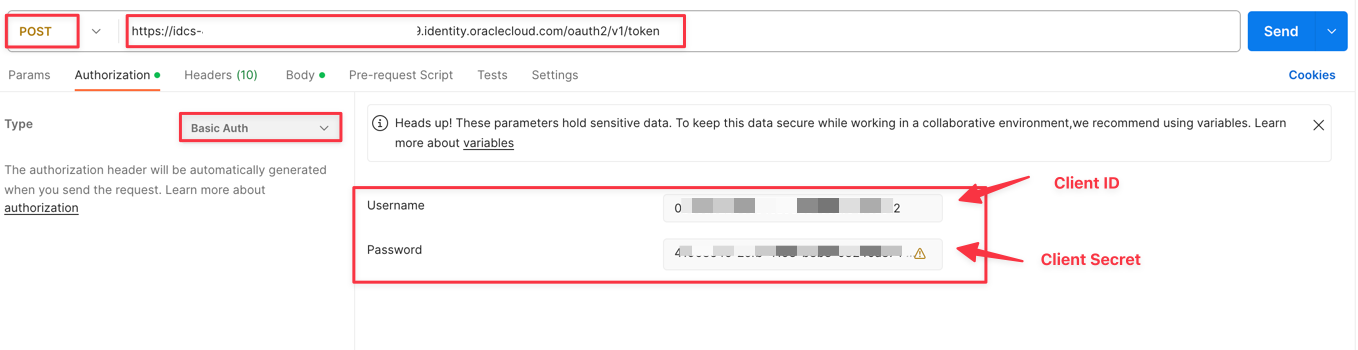
-
In the Body content, enter the grant_type and scope values. Remember, the scope was captured in the Oracle Identity Cloud Service configuration.

-
Click Send and execute the
POSTrequest and view the token.
-
Task 2: Configure OCI Functions to call your OCI SDK API
-
Understand the OCI Functions and OCI API Gateway: It is a best practice to expose your services through an OCI API Gateway. Authentication can be done bypassing the credentials from OCI API Gateway to the backend services, but if the backend authentication was not the appropriate method for your client application, we can do some configuration in the OCI API Gateway level.
In this step, let’s understand how OCI API Gateway can help us to integrate the OAuth2 authentication and the request for any OCI service, like OCI Streaming through the OCI Functions.
OCI Functions can do the job to produce the correct authentication/authorization and pass to the OCI service without the necessity of passing user credentials or private keys to the consumer applications. Some services in the OCI service cannot authenticate using OAuth2 method, so we can do it with OCI Functions. To create and deploy OCI Functions, see OCI Functions Quickstart.
In this example, the OCI Streaming service can authenticate by the OCI private key in OCI IAM through draft-cavage-http-signatures-08 method and consumers can authenticate by OAuth2.
-
Understand the Code: This code will be used with OCI API Gateway. In your API deployment, we will configure the OCI Streaming endpoint in the OCI API Gateway and it will be passed as a HEADER authorization parameter. So you can use this function for many services in each OCI API Gateway deployment you need.

-
This function in Python will create a date and time in format for the authentication. This date and time needs to be generated one time and used in two points. To the header Date on the OCI Streaming request and the Signature cryptographed HEADER.
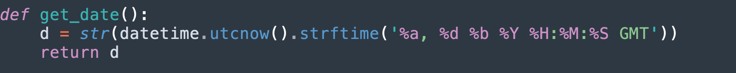
-
This is the function for signature encryption. The assembly consists of using the OCI IAM user’s private key with SHA-256 and then in base64.

-
The signature encryption will be used on the complete Authorization HEADER.

-
This is the Oracle Identity Cloud Service OAUTH2 token validation code. You need to configure the
config.jsonfile with your Oracle Identity Cloud Service application parameters.
-
This is the beginning of the function and initializes some information from OCI IAM security and OCI Streaming variables created for this API deployment (
streaming_hostandoci_region).
-
This is the main part of this function, there are two parts.
In the first part, we obtain the token passed in the API Gateway request. After this, we call the auth_idcs() function to validate the token in Oracle Identity Cloud Service. Before generating the draft-cavage-http-signatures-08 string, we validate the Oracle Identity Cloud Service token. If it is not a valid token, the response will give a 401 unauthorized error.
In the second part, we will create two values. The date (d) with the date format will be used in the creation of the signature (a). The rdata will construct the response for the function with the authorization and date values that will be used by OCI API Gateway to authenticate on OCI Streaming.

-
Here we can generate a log in the OCI Observability and this step is optional. Enter the Oracle Cloud Identifier (OCID) for the log. You need to create a Custom Log previously.
Note: To create a custom log in OCI Observability, see Use OCI API Gateway, Functions and Observability to Validate JSON Content and Monitor API Headers and Body.

-
This is the final step and returns with a valid authentication.

This is the
requirements.txtlibraries that will need to be loaded in this function (fn).requirements.txt --------------------- fdk>=0.1.54 requests oci cryptography six PyJWT py3_lru_cache simplejsonThis is the
config.jsonfile.
And this is the OCI config file. You can copy this file from your OCI CLI installation but it is important to modify the
key_filesection and remove the path of your OCI CLI installation. This will be used in the Python code to generate thedraft-cavage-http-signatures-08cryptographic string.
Before deploying the function, create two variables and fill with the OCI Streaming OCID and OCI region values like this.
fn config app <function-app> streaming_host ocid1.stream.oc1.iad.xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxqhgw275qp7a fn config app <function-app> oci_region us-ashburn-1Deploy your function and let’s configure it in the OCI API Gateway.
-
Task 3: Configure an API Gateway Deployment
Note: Develop a function and call it in OCI API Gateway, see OCI Functions: Validate an API Key with API Gateway.
-
Configure your OCI API Gateway service. In this example, we will configure an OCI Streaming service. In basic information, enter the Path prefix as
/20180418/streams/plus the OCID of your streaming instance.For example:
/20180418/streams/ocid1.stream.oc1.iad.xxxxxxxxxxxxxxxxxxxxxxxxxxxx
-
In the Authentication, select Single Authentication and Authorizer Function. Select the compartment and Oracle Function as
get-authorization.
-
Configure your request HEADERs parameters.
Header Parameter 1 Context table=request.headers Header name=Date Argument name=Date Header Parameter 2 Context table=request.headers Header name=token Argument name=token -
To configure the HEADER for Oracle Identity Cloud Service parameters, you need to click Show route request policies.

-
In the HEADER transformations, click Edit and enter Behavior to
Overwritein both parameters, Header name asAuthorization,Dateand Values as${request.auth[authorization]}and${request.auth[date]}respectively. The${request.auth[authorization]}and${request.auth[date]}are the values returned by the function Python code and will be passed as the HEADERs for the backend service.
Task 4: Configure the OCI Group and Policies
To configure the policies for OCI Streaming, see OCI Streaming Policies and you can use common policies, see Common Policies.
Task 5: Test the API
Let’s simulate your application OAuth2 request for your Model Deployment Service in OCI Streaming.
-
Obtain the token and pass the Client ID and Client Secret to your Oracle Identity Cloud Service provider.
Verb: POST URL: https://idcs-xxxxxxxxxxxxxxxxxxxxxxx.identity.oraclecloud.com/oauth2/v1/token BODY (x-www-form-urlencoded): scope: xxxxxxxxxxxxxxxxxxx.apigateway.us-ashburn-1.oci.customer-oci.com/super-scope grant_type: client_credentials HEADER Authorization: clientID:clientSecret\* - convert your clientID:clientSecret to a base64 value
-
Test the request to OCI API Gateway. Enter your API Gateway deployment endpoint and select POST to your REST request. You need to declare six HEADERs in the BODY of your request.
Content-Type: application/json access-control-allow-origin: * access-control-allow-method: POST,PUT,GET,HEAD,DELETE,OPTIONS access-control-allow-credentials: true Date: put an actual date in this format -> Thu, 21 Dec 2023 13:53:59 GMT token: put your <access_token> here* * Remember that your token have 1 hour duration.
And here is the result.

In the Logs, you can see the payloads for your custom code authorization logic.

Related Links
Acknowledgments
- Author - Cristiano Hoshikawa (Oracle LAD A-Team Solution Engineer)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Integrate OCI Streaming with Other Authorization Methods Using OCI API Gateway
F91369-02
November 2024