Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Integrate Okta with Identity Domains for Single Sign-On and user provisioning
Introduction
In the real world there might be scenarios where the customers can have Okta as their corporate Identity provider, but the users also need access to the services hosted by Oracle Cloud. In such scenarios, we recommend setting up federation to automate the users and group auto provisioning from Okta to Identity Domains for better lifecycle management of users. This setup will enable users to use their Okta SSO credentials to log in to the services hosted by Oracle Identity Domain.
An identity domain is a container for managing users and roles, federating and provisioning of users, secure application integration through Oracle Single Sign-On (SSO) configuration, and SAML/OAuth based Identity Provider administration. With the recent merger of Oracle Cloud Infrastructure (OCI) and Oracle Identity Cloud Service into Identity Domains it is necessary for the customers to understand the navigation on the console for integrating Okta with Identity Domains.
Key Benefits
- Automated user and groups creation/updating and deactivation/deletion.
- Automated users and group synchronization.
Prerequisites
Admin accounts for Okta and Identity Domains
Objective
Use the Okta Catalog application for this federation to setup SAML based Single Sign-On and SCIM based automated user and group provisioning. Post this configuration, Okta will be setup as the Identity Provider for Identity Domain.
Task 1: Create an application in Okta
We must create an application in Okta available in the Okta marketplace for setting up SSO and SCIM provisioning with Identity Domain.
-
Log in to Okta as an administrator, navigate to Applications from the left-hand menu and locate Browse App Catalog option as highlighted in the following image.
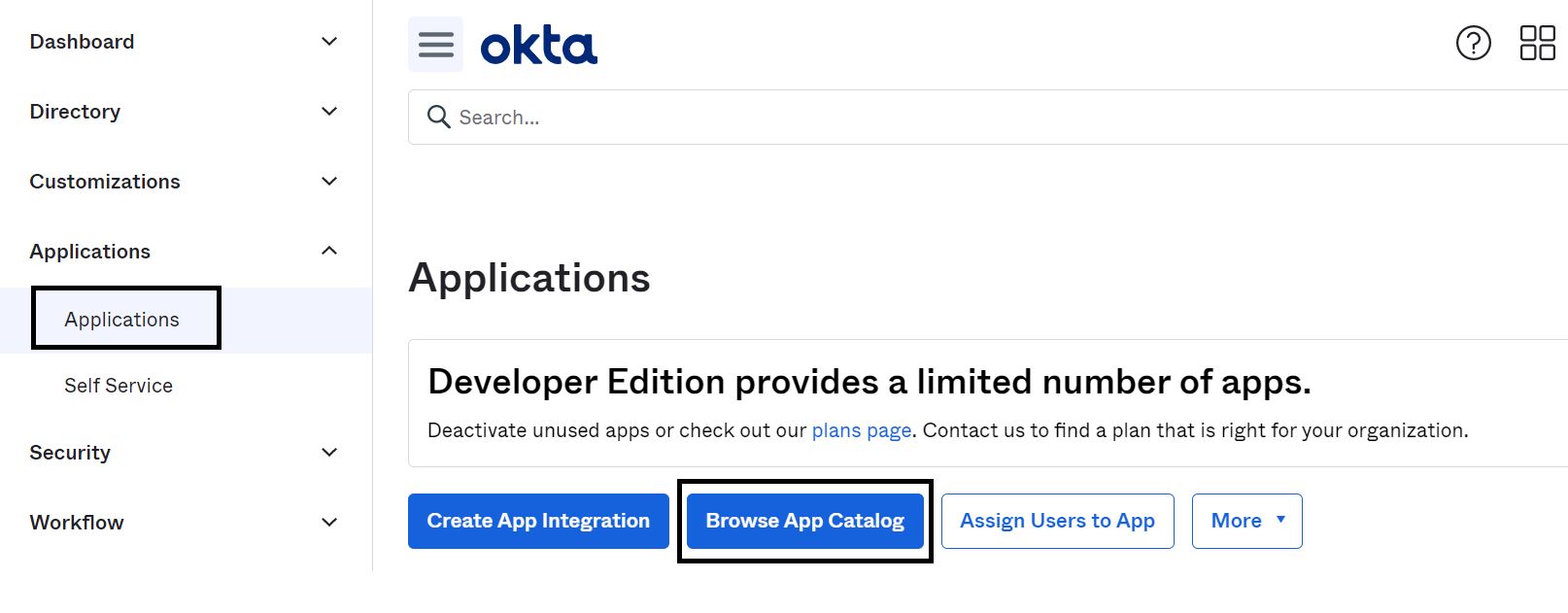
-
Search for Oracle Identity Cloud Service and add the application.
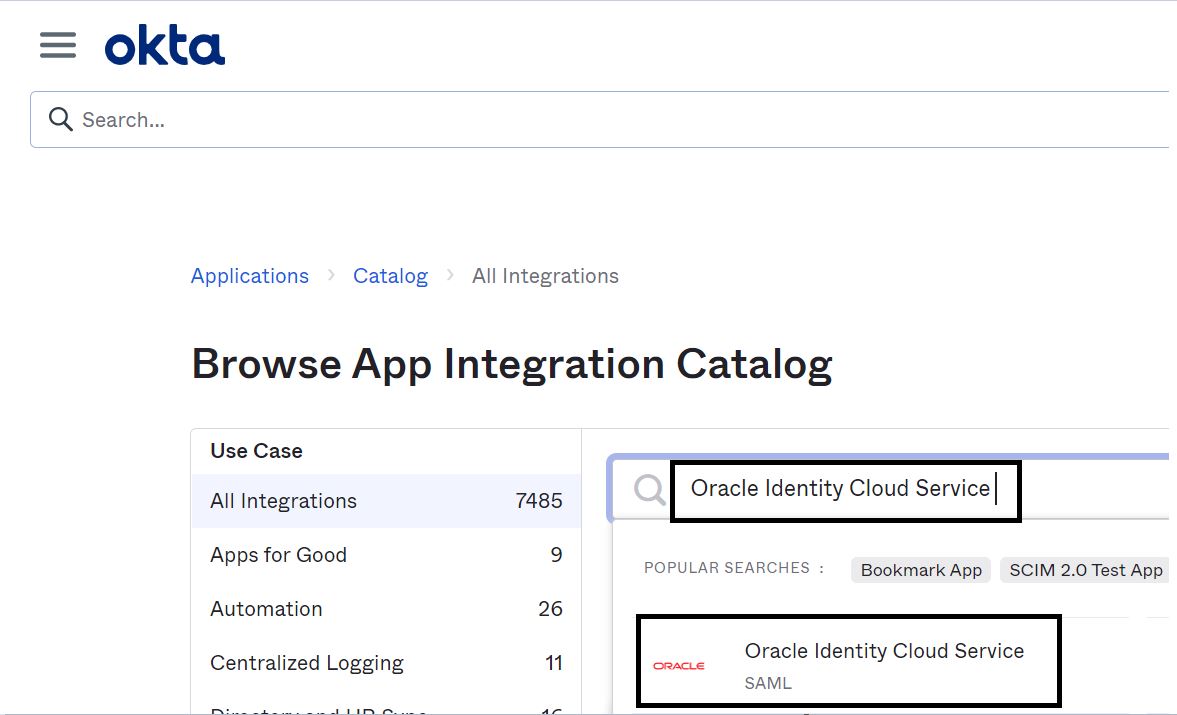

-
Complete the General settings required in the Application wizard with the required details and then click Done.
Tip: To find your Subdomain, log in to the Identity Domain that you wish to integrate with Okta and navigate via the following options.
-
From the Main Menu, go to Identity and Security, Domains, select the appropriate Domain, Overview, Domain URL.
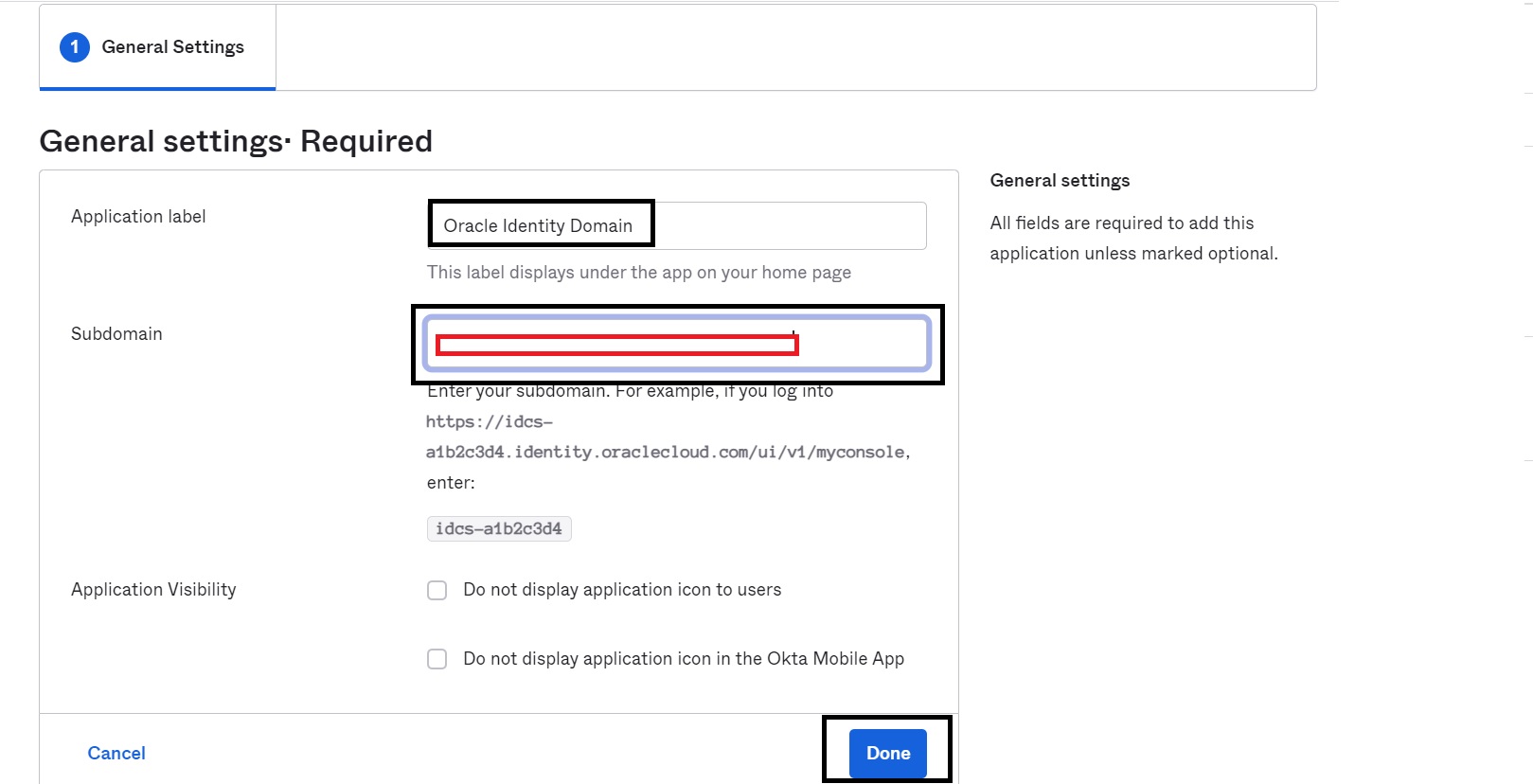
-
-
Navigate to the Sign On tab of the added application, update the following details and click Save.
-
Default Relay State: https://idcs-$DOMAIN_INSTANCE_ID.identity.oraclecloud.com/ui/v1/myconsole. This is the URL the user is logged into after Single Sign-On with Oracle Identity Domains. This can also be if required, an application URL that is protected by Oracle Identity Domains.
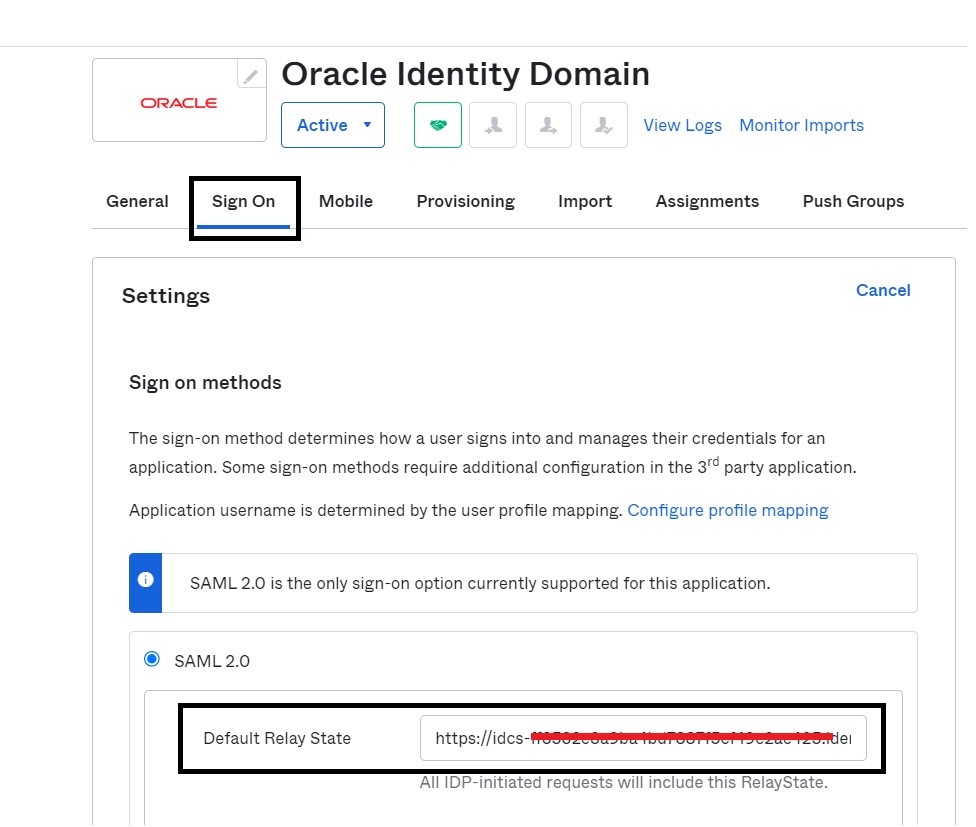
-
Provider ID: https://idcs-$DOMAIN_INSTANCE_ID.identity.oraclecloud.com:443/fed
-
Application username format: Email (This is assuming email address is same for the user in both Okta and Oracle Identity Domains)
-
Update application username on : Create and Update
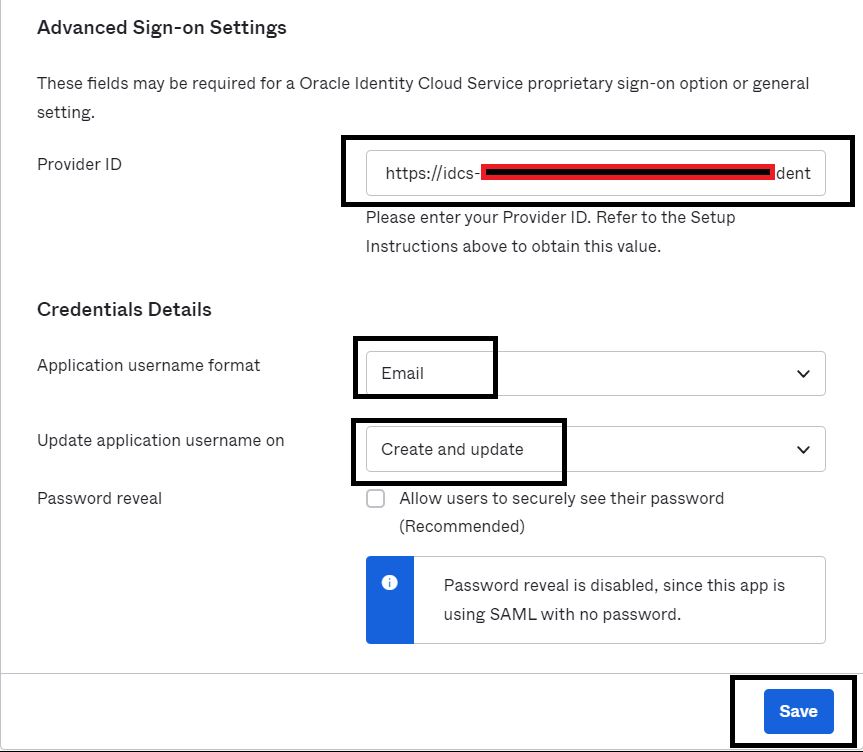
-
Note: We will revisit this step to enable Single Log out once we get the signing certificate from Identity Domain.
Task 2: Configure Okta as the Identity Provider in Oracle Identity Domain
-
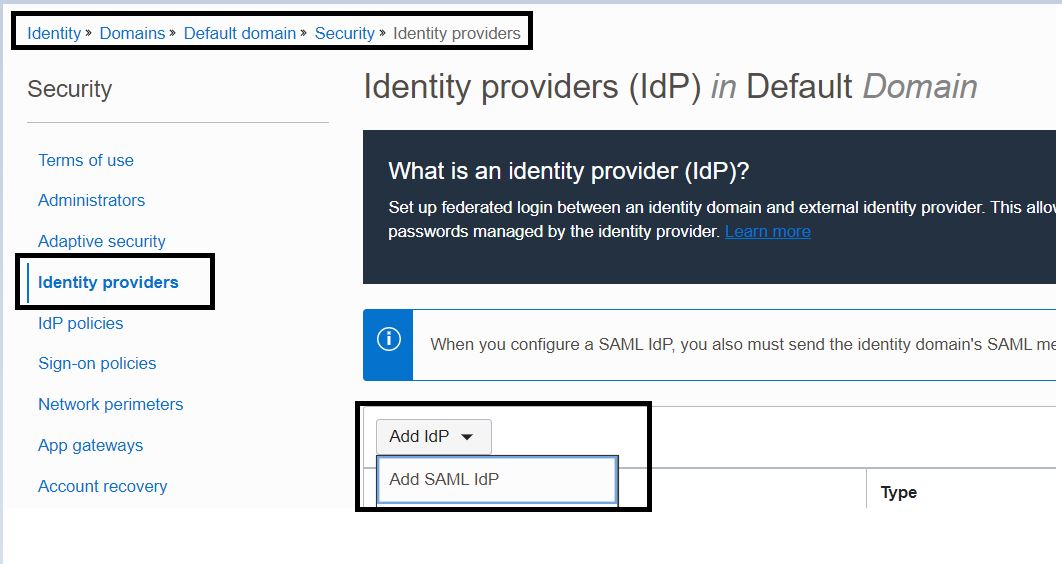
Log in to your Oracle Identity Infrastructure tenancy as an admin user, then navigate to Identity Provider settings and click Add a SAML IDP.
-
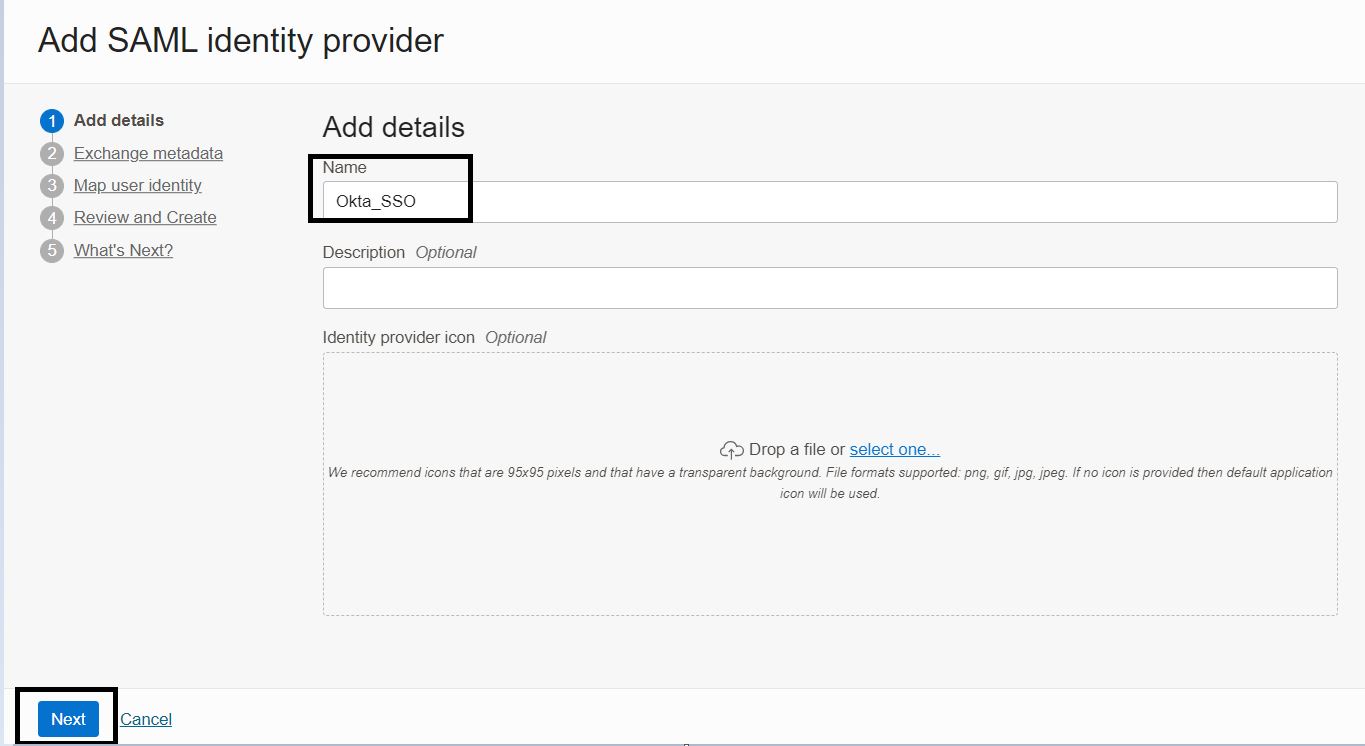
From the wizard that is launched, add the basic details on the screen and click Next.
-
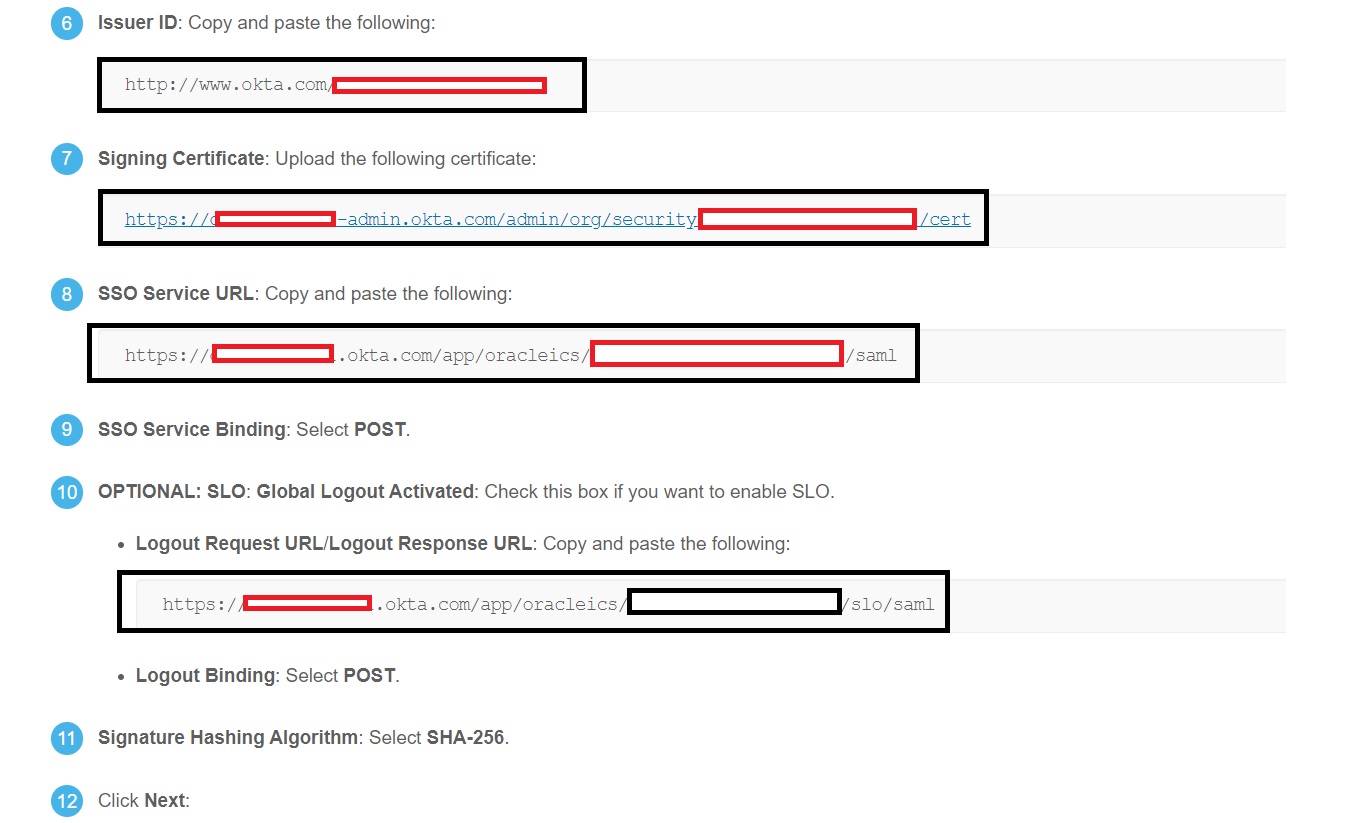
On the Exchange Metadata page, select the Enter IDP metadata - Enter parameters manually option, update the following details and click Next.
Tip: On the Sign On Tab of your configured Okta Application scroll down to locate the View SAML Setup Instruction link for the required details.
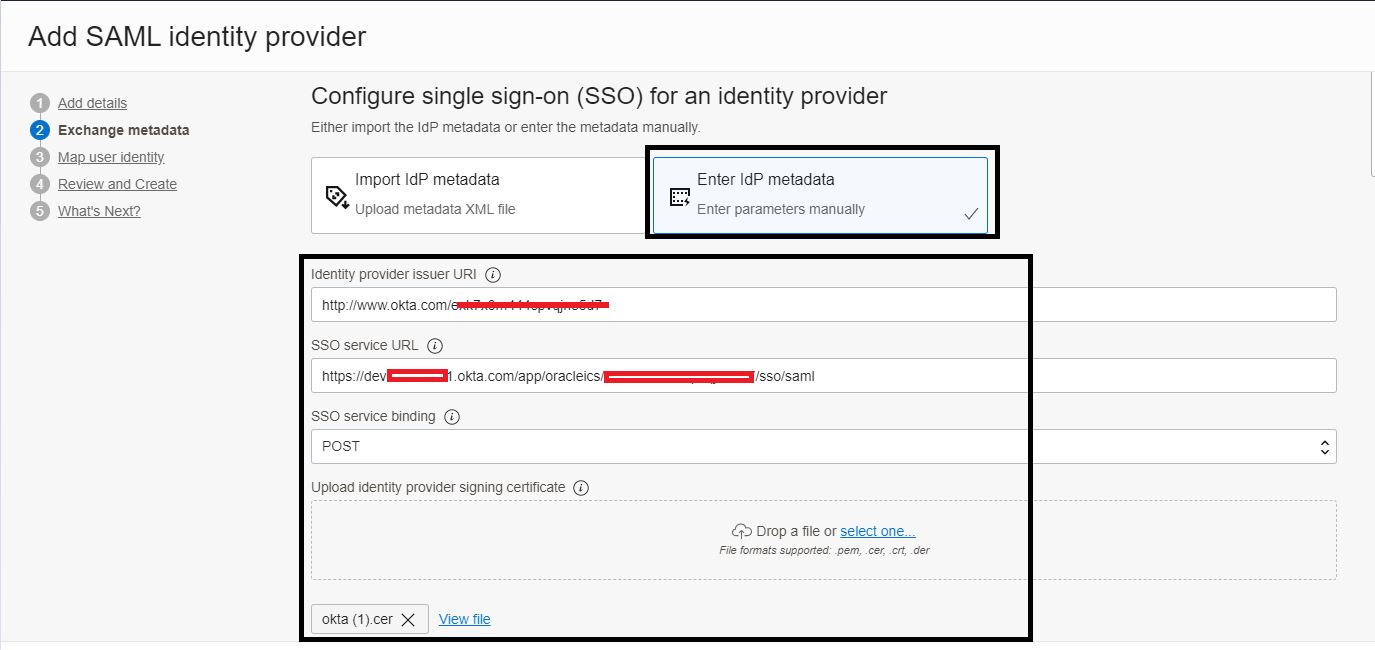
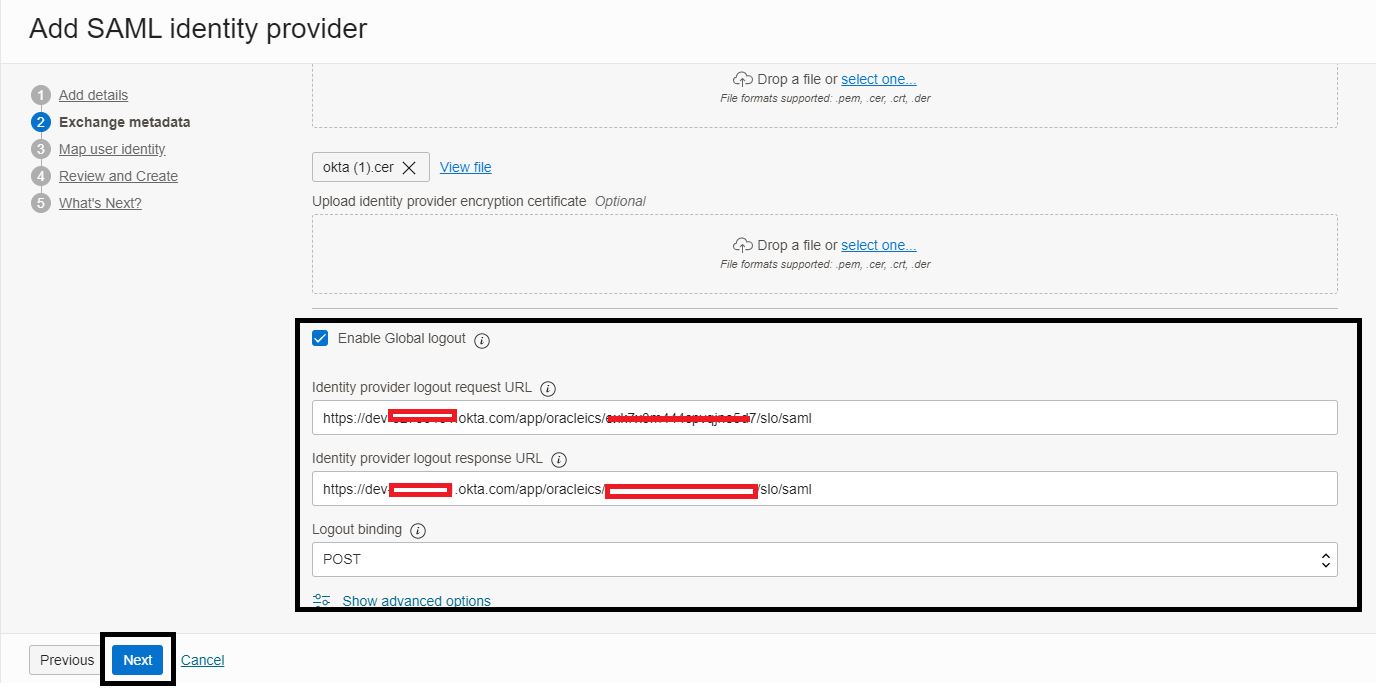
-
On the Map user identity page, update the following details and click Next.
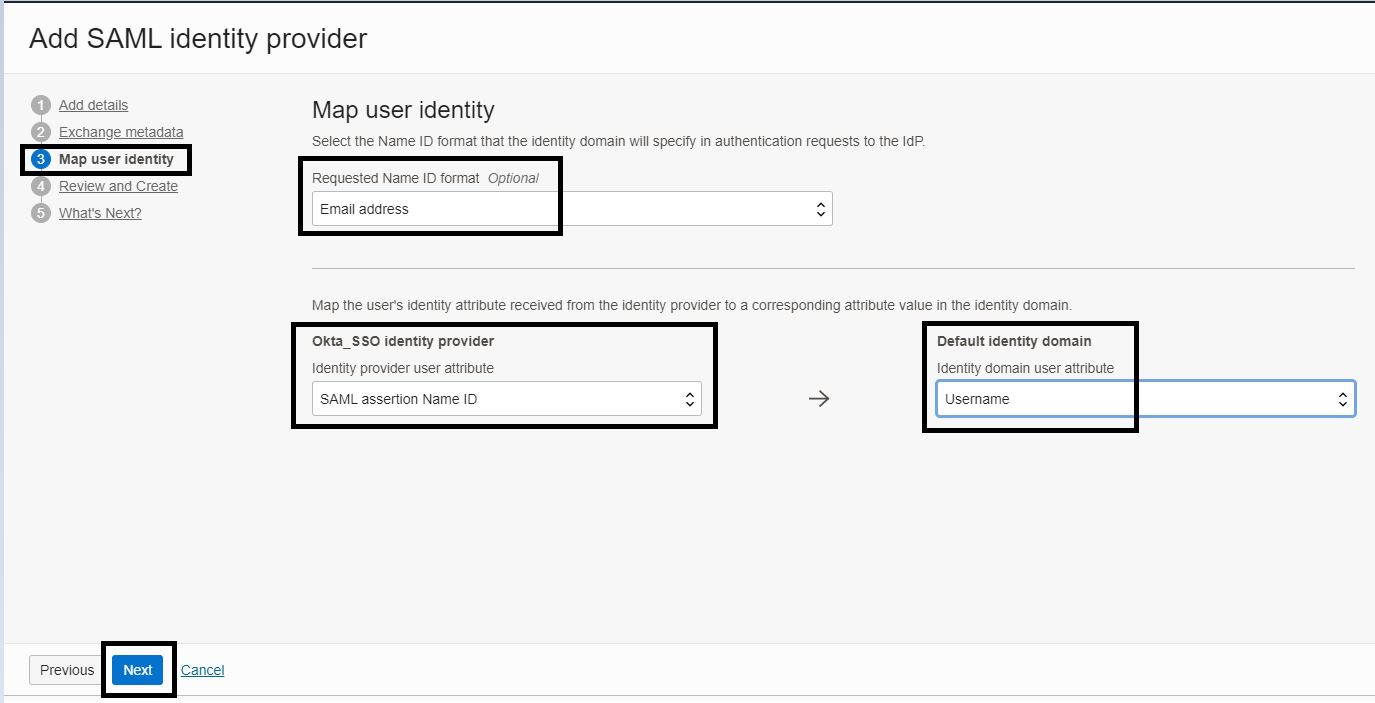
-
On the Review and Create page, review the settings and then click Create IdP.
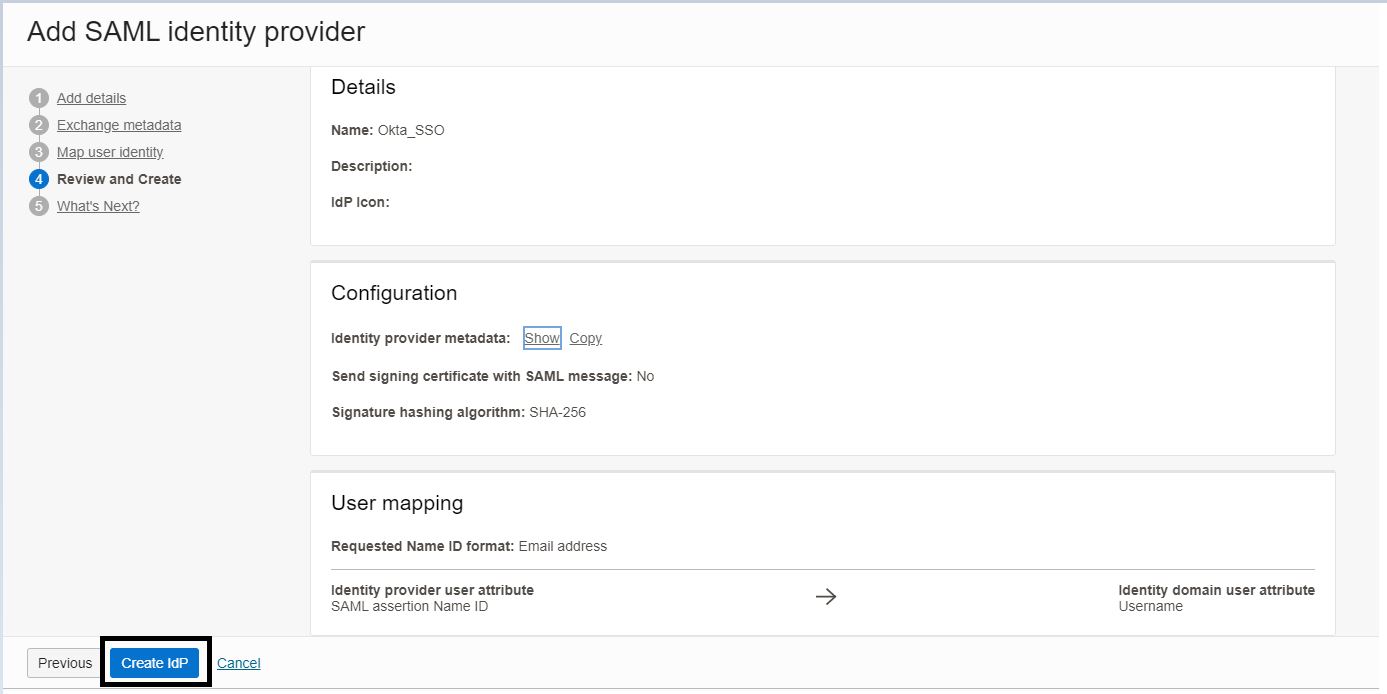
-
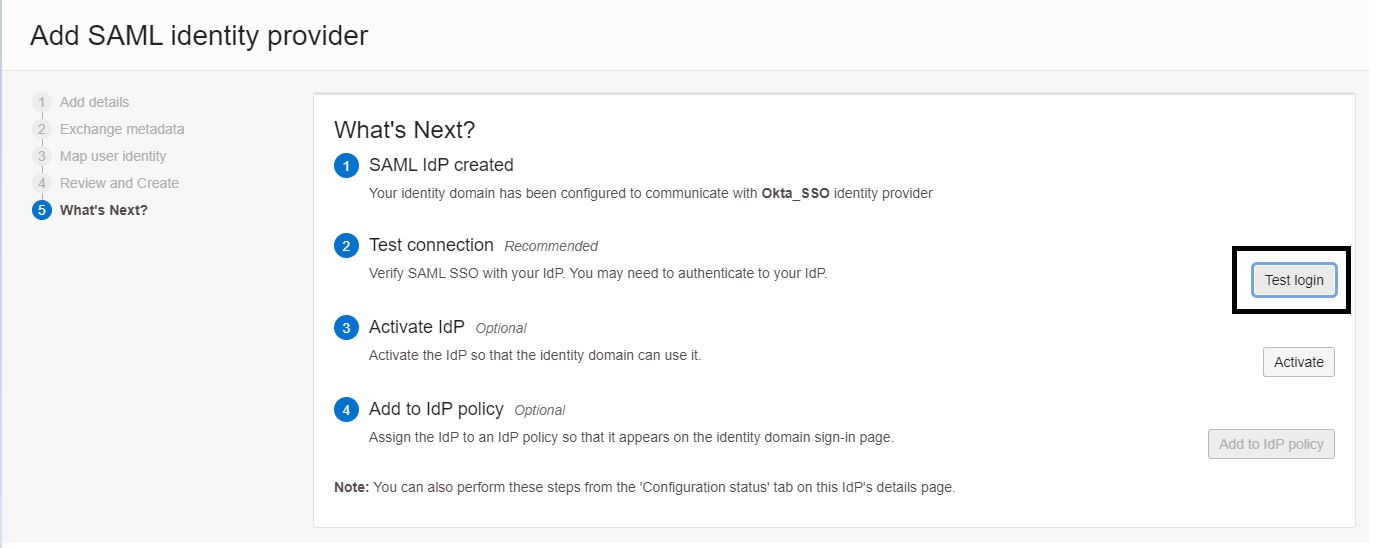
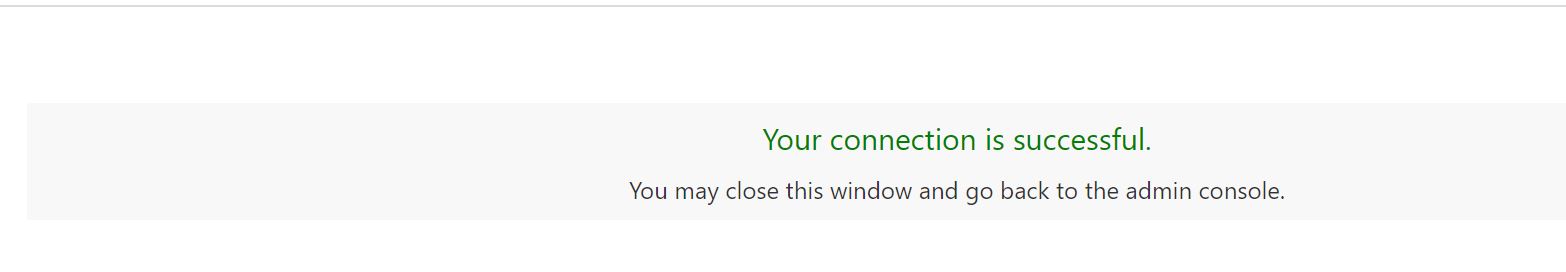
On the What’s next page, click Test login to validate the configuration. You should see a success message as displayed below.
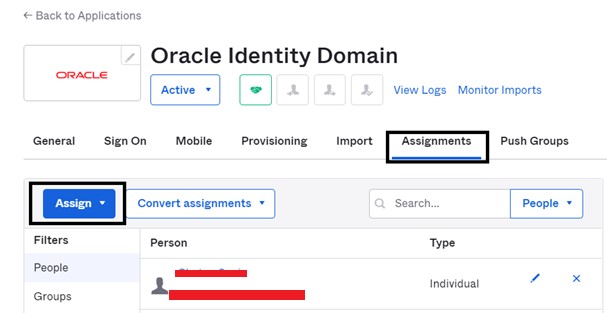
Note: The user that you are testing this integration with should be assigned on the Okta application as well as displayed below.
-
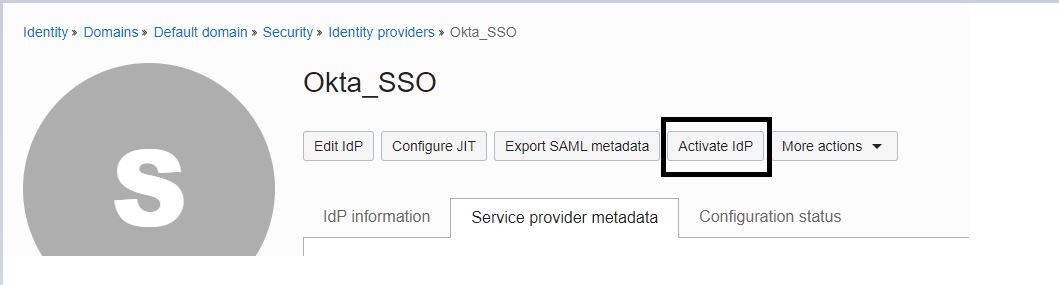
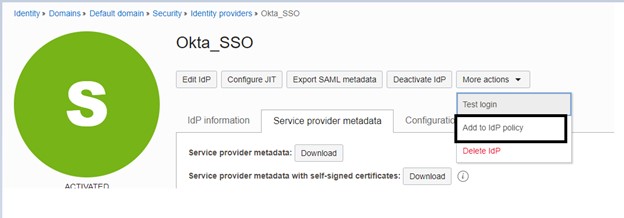
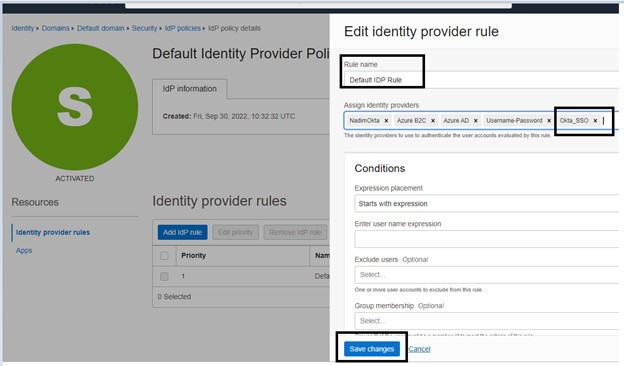
Click Activate IdP and add this to the Identity Provider Rule of your requirement as displayed below.
Task 3: Set Up a Confidential application in Identity Domain for SCIM Provisioning
System for Cross-domain Identity Management (SCIM), is an open standard that allows for the automation of user provisioning. SCIM communicates user identity data between identity providers and service providers requiring user identity information.
-
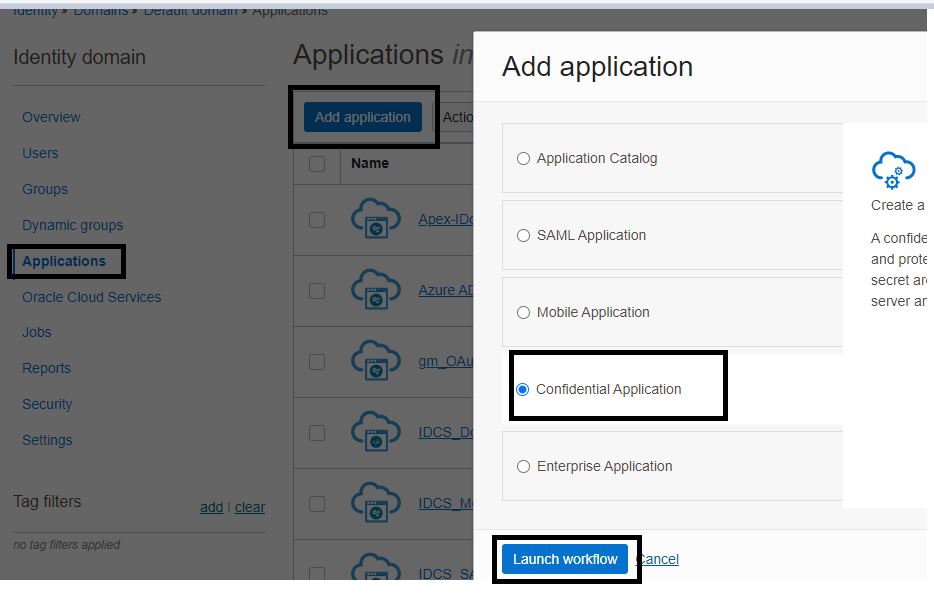
Navigate to the Applications tab under your Identity Domain, click Add application, then click Confidential Application and then click Launch workflow.
-
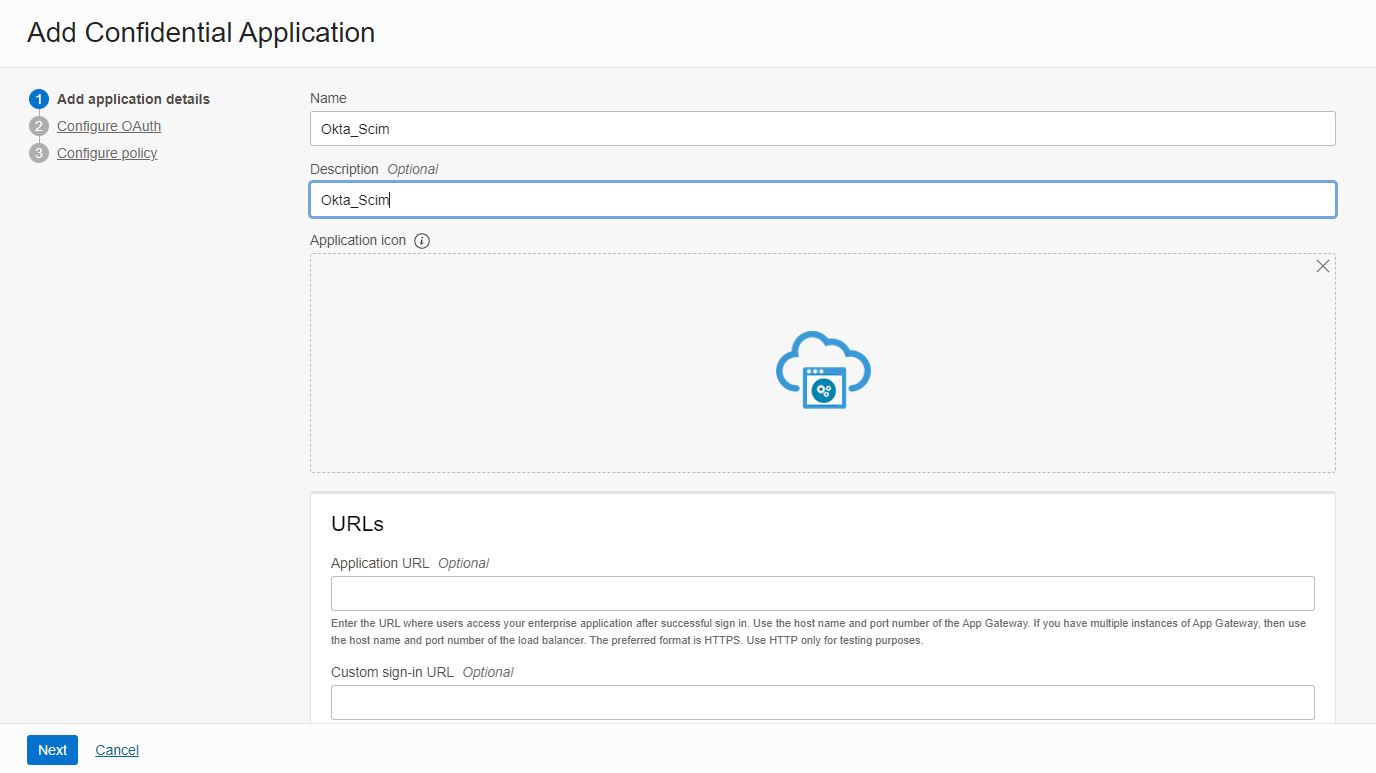
Enter an application Name and click Next.
-
Add the following details to the application and click Next.
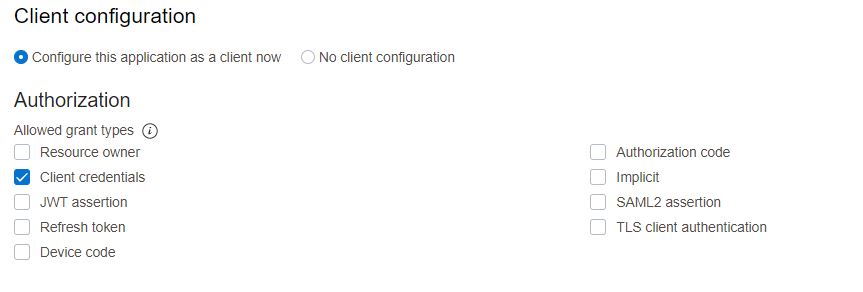
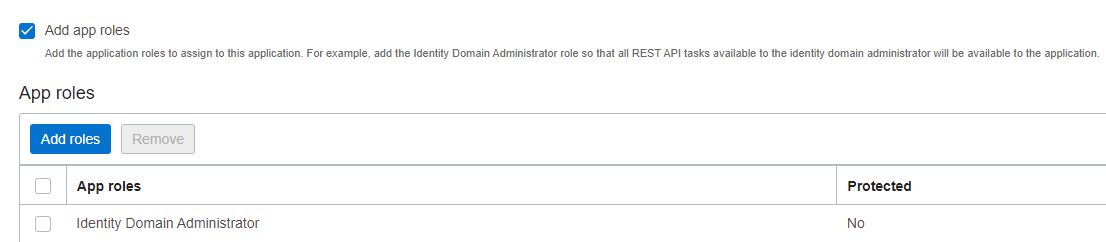
-
Activate the application and make a note of Client ID and Secret.
Task 4: Enable SCIM Provisioning from Okta to Identity Domain
-
Navigate back to the Okta Admin console for configuring the SCIM provisioning. Click on the configured application and click on the Provisioning tab.
-
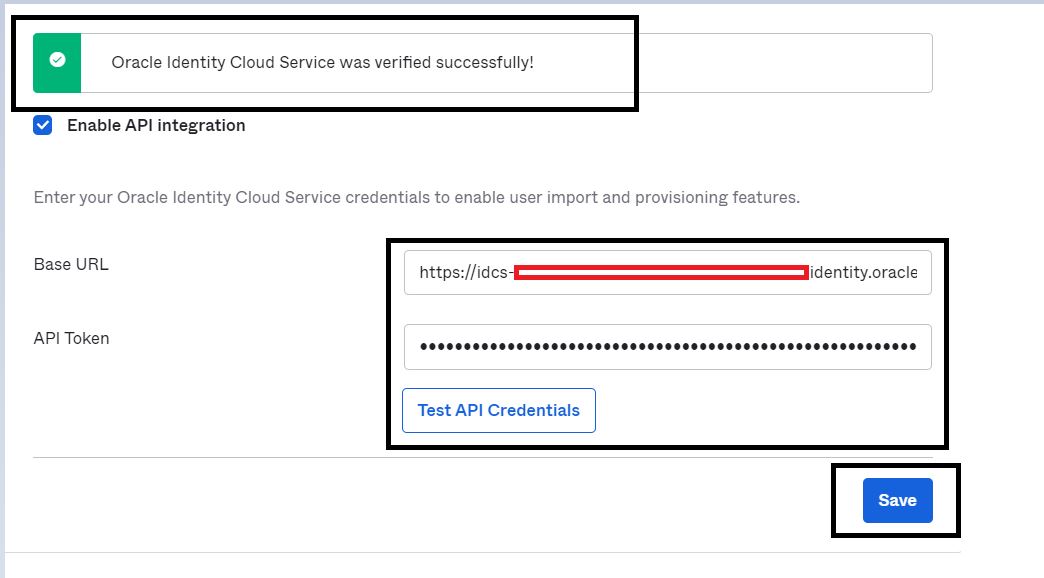
Add the following details in the Provisioning section of the configured application.
-
Base URL: https://$IDCS_SUBDOMAIN.identity.oraclecloud.com/admin/v1
-
API Token: Base64encoded(ClientID:ClientSecret) (From the previous step)
-
Click Test API Credentials.
-
You should be able to see the Successful message on your screen. Click Save.
-
-
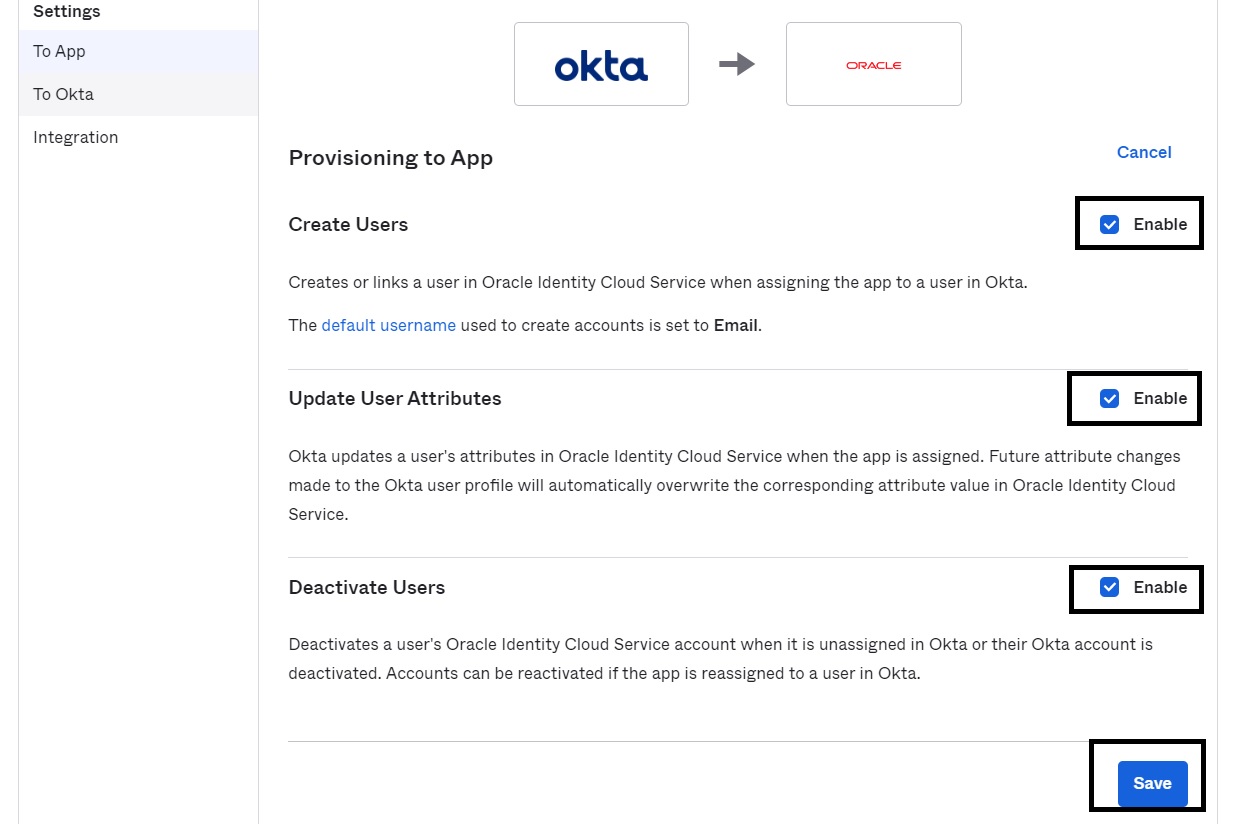
Click Edit, select all the Enable options, and then click Save to enable the user provisioning option.
-
From the Assign section, add the users and groups to be synchronized to Identity Domains.
Once you complete the setup steps, your users and groups will be synchronized from Okta to Identity Domains.
Related Links
Acknowledgments
Author - Chetan Soni (Cloud Solutions Engineer)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Integrate Okta with Identity Domains for Single Sign-On and user provisioning
F77055-01
February 2023
Copyright © 2023, Oracle and/or its affiliates.