Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Configure NAT gateway for private compute instances
Introduction
Many Oracle Cloud Infrastructure customers have compute instances in virtual cloud networks (VCNs) that, for privacy, security, or operational concerns, are connected to private subnets. To grant these resources access to the public internet for software updates, CRL checks, and so on, a customer’s only option has been to create a NAT instance in a public subnet and route traffic through that instance by using its private IP address as a route target from within the private subnet. Although many have successfully used this approach, it does not scale easily and provides a myriad of administrative and operational challenges.
NAT gateway addresses these challenges and provides Oracle Cloud Infrastructure customers with a simple and intuitive tool to address their networking security needs. NAT gateways provide the following features:
-
Highly scalable and fully managed: Instances on private subnets can initiate large numbers of connections to the public Internet. Connections initiated from the Internet are blocked.
-
Secure: Traffic through NAT gateways can be disabled with the click of a button.
-
Dedicated IP addresses: Each NAT gateway is assigned a dedicated IP address that can be reliably added to security whitelists.
Sign in to OCI Console and Create a VCN
Note: Screenshots in the instructions may be different than the actual UI.
-
Sign in to Oracle Cloud Infrastructure Console using your tenant name, user name and password.
-
From the OCI Services menu, click Virtual Cloud Networks under Networking, and select the appropriate compartment. Click Start VCN Wizard.
Note: Ensure that the correct compartment is selected under COMPARTMENT list.
-
Click VCN with Internet Connectivity and click Start VCN Wizard.
-
Fill out the dialog box and click Next:
- VCN NAME: Provide a name
- COMPARTMENT: Ensure your compartment is selected
- VCN CIDR BLOCK: Provide a CIDR block (10.0.0.0/16)
- PUBLIC SUBNET CIDR BLOCK: Provide a CIDR block (10.0.1.0/24)
- PRIVATE SUBNET CIDR BLOCK: Provide a CIDR block (10.0.2.0/24)
-
Verify all the information and click Create.
This will create a VCN with following components: VCN, Public subnet, Private subnet, Internet gateway (IG), NAT gateway (NAT), Service gateway (SG).
-
Click View Virtual Cloud Network to display your VCN details.
Create and Connect to Compute Instance
-
Create SSH encryption keys you can use to log into your VM by opening a terminal window in the directory where you want to store your keys and issuing the following OpenSSH command, where <my-key> is your desired key name:
ssh-keygen -t rsa -N "" -b 2048 -C <my-key> -f <my-key>The command generates random text art used to generate the keys. When complete, you should have two files:
- The private key file: <my-key>
- The public key file: <my-key>.pub
You use these files to connect to your compute instance.
-
Go to OCI Console. From the OCI Services menu, under Compute, click Instances.
-
Click Create Instance and fill out the dialog box:
- Name your instance: Enter a name
- Choose an operating system or image source: For the image, we recommend using the Latest Oracle Linux available.
- Availability domain: Select Availability Domain
- Instance type: Select Virtual Machine
- Instance shape: Select VM shape
Under Configure Networking:
-
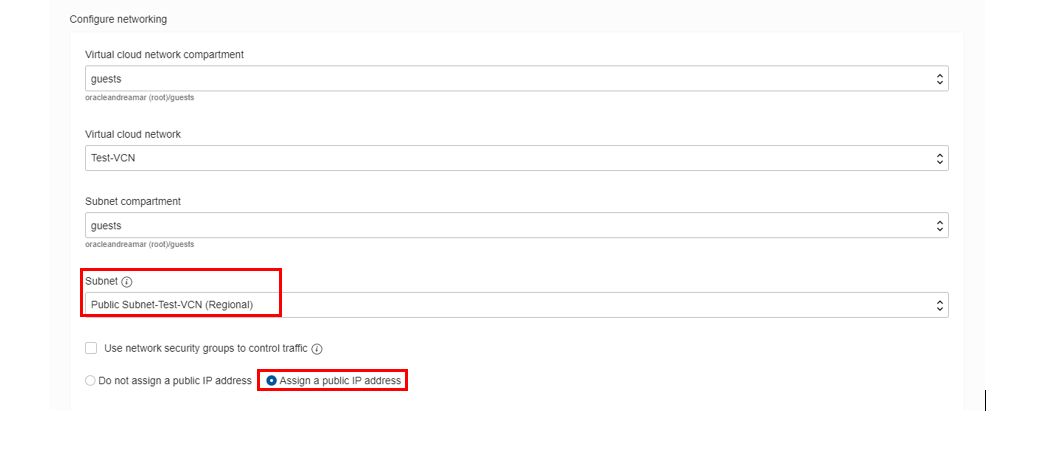
Virtual cloud network compartment: Select your compartment
-
Virtual cloud network: Choose the VCN
-
Subnet compartment: Choose your compartment
-
Subnet: Choose the Public Subnet under Public Subnets
-
Use network security groups to control traffic: Leave un-checked
-
Assign a public IP address: Check this option
Then enter the following:
- Boot Volume: Leave the default
- Add SSH Keys: Choose Paste SSH Keys and paste the public key saved earlier
-
Click Create.
Note: If a ‘Service limit’ error is displayed, choose a different shape from VM.Standard2.1, VM.Standard.E2.1, VM.Standard1.1, VM.Standard.B1.1, or choose a different AD.
-
Wait for the instance to be in Running state. In the cloud shell terminal, enter the command:
cd .ssh -
Enter ls and verify that your SSH key file exists.
-
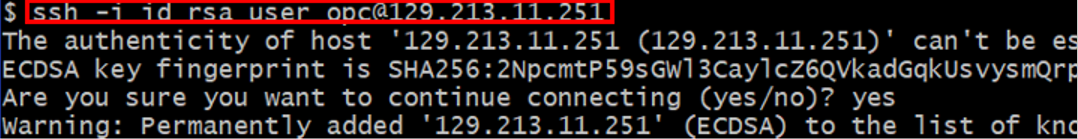
Enter the command:
bashssh -i id_rsa opc@PUBLIC_IP_OF_COMPUTEHint: If ‘Permission denied error’ is seen, ensure you are using
-iin the SSH command. You MUST type the command; do NOT copy and paste the SSH command. -
Enter
yeswhen prompted for the security message. -
Verify that opc@
<COMPUTE_INSTANCE_NAME>appears on the prompt.
Configure the NAT Gateway
We will now create a route table in the VCN.
-
Switch to the OCI Console. From the OCI Services menu, click Virtual Cloud Networks under Networking. Locate your VCN and click the VCN name to display the VCN details.
-
Click NAT Gateways.
-
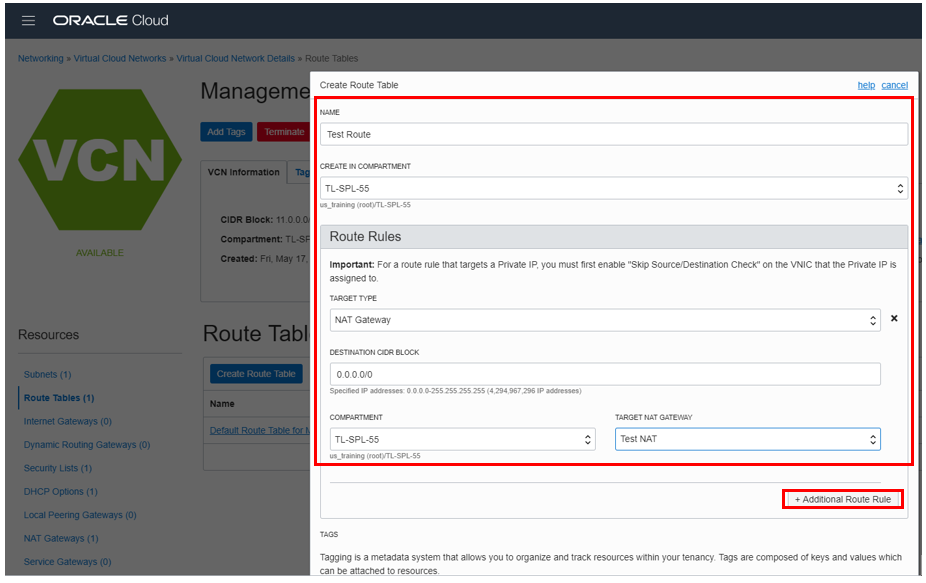
Click Route Tables then Create Route Table. Fill out the dialog box:
- Create in Compartment: This field defaults to your current compartment; make sure that the correct compartment is selected
- Name: Enter a name
Click +Additional Route Rules
- Target Type: Select NAT Gateway
- Destination CIDR Block: Enter 0.0.0.0/0
- Compartment: Make sure the correct compartment is selected
- Target NAT Gateway: Select the NAT Gateway for your VCN
-
Click Create Route Table.
-
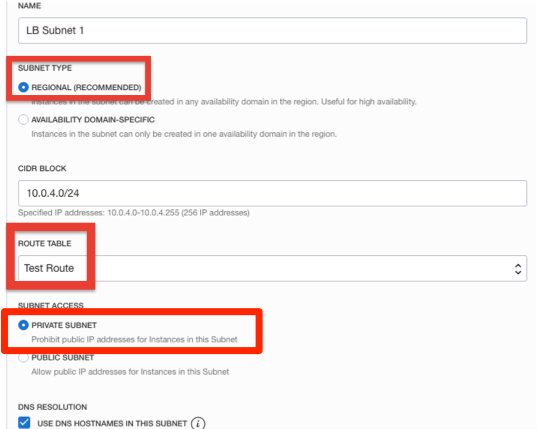
Click your VCN name to display the VCN details. Click Create Subnet. Fill out the dialog box:
- Name: Enter a name
- Subnet Type: Regional
- CIDR Block: Provide a CIDR (e.g. 10.0.5.0/24)
- Route Table: Choose the Route table created earlier
Note: Do not choose the Default route table. This is being done so all routing for compute instances in this subnet are via the NAT gateway.
- Subnet access: Private Subnet
- DHCP Options: Select the default
- Security Lists: Select the security list that you created earlier
-
Leave all other options as default and click Create Subnet.
-
Go to your cloud shell terminal and generate the SSH key pair. Enter the command:
ssh-keygen -
Press Enter when asked for
Enter File in which to save the key,Created Directory,Enter passphrase, andEnter Passphraseagain. -
Enter the command:
cd ~/.sshand then
lsYou should have the private and public keys: /home/opc/.ssh/<sshkeyname> (private key) and /home/opc/.ssh/<sshkeyname>.pub (public key).
-
Enter the command:
cat ~/.ssh/id_rsa.pubCopy and paste the public key content to Notepad. We will use this public key to launch a compute instance in private subnet of the VCN.
-
Switch to the OCI Console window and launch a second compute instance as done previously. Ensure the subnet chosen is the private subnet that we created previously.
-
Once the instance is running, note down the private IP address of the instance from the instance detail page (by clicking the instance name).
-
Switch to a git-bash window with an SSH session to public compute instance (first compute instance created earlier). Enter the command:
cd ~/.sshthen
bashssh –i id_rsa opc@Private_IP_OF_COMPUTE_INSTANCENote: User name is opc.
Hint: If a “Permission denied error” is seen, ensure you are using
-iin the SSH command.Note: Use the private IP of the second compute instance noted earlier.
-
Enter
Yeswhen prompted for the security message. -
In the private compute instance, enter the command:
ping 8.8.8.8and verify there is internet connectivity.
The compute instance in private subnet has Internet access. This is possible since traffic is being routed through the NAT gateway that we created and attached to the VCN. Next we will use the traffic toggle function on NAT gateway to block/allow traffic with a single click.
-
Switch to the OCI Console window. In your VCN’s detail page, click NAT Gateways.
-
Hover over the Action icon and choose Block Traffic.
-
Switch back to the SSH session to the private compute instance and enter the command
ping 8.8.8.8(if not already running). Verify there is no response. -
Switch back to the OCI Console window and, using above step, this time choose Allow Traffic. Switch back to the SSH session and verify that the
pingresponse is received.
Delete the Resources
-
Switch to the OCI Console window.
-
If your compute instance is not displayed, from the OCI services menu, click Instances under Compute.
-
Locate the compute instance, click the Action icon, and then click Terminate.
-
Make sure Permanently delete the attached Boot Volume is checked, and click Terminate Instance. Wait for the instance to fully terminate.
-
Repeat the steps to delete the second compute instance.
-
From the OCI services menu, click Virtual Cloud Networks under Networking. A list of all VCNs will appear.
-
Locate your VCN, click the Action icon and then click Terminate. Click Terminate All in the confirmation window. Click Close once the VCN is deleted.
Acknowledgements
- Authors - Flavio Pereira, Larry Beausoleil
- Contributors - Kamryn Vinson (QA Intern), Yaisah Granillo (Cloud Solution Engineer)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Configure NAT gateway for private compute instances
F35836-03
November 2021
Copyright © 2021, Oracle and/or its affiliates.