Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Secure traffic between Oracle Cloud Infrastructure and Microsoft Azure using Network Virtual Appliance
Introduction
To create an integrated multicloud experience, Microsoft and Oracle offer direct interconnection between Microsoft Azure and Oracle Cloud Infrastructure (OCI) through Microsoft Azure ExpressRoute and OCI FastConnect. The Microsoft Azure ExpressRoute and OCI FastConnect interconnection, provides low latency, high throughput, and private direct connectivity between the two clouds.
You can set up interconnect connectivity between Microsoft Azure and Oracle Cloud Infrastructure using instruction provided in this step-by-step guide. Once interconnect is up you would need to connect Virtual Networks to ExpressRoute.
This tutorial outlines how you can extend interconnect connectivity using VNET Gateway and deploy Microsoft Azure Firewall and OCI Network Firewall to secure your traffic. You will be deploying Firewalls in a Hub and Spoke architecture for your use case, and this use case should be applicable to all supported network virtual appliance partners on respective CSPs.
You can follow this document to know more about network virtual appliance architectures recommendations.
Objective
Secure your traffic using network firewall appliance between Oracle Cloud Infrastructure and Microsoft Azure environment through OCI-Microsoft Azure Interconnect Network connectivity. We have covered deploying the environment with Microsoft Azure Firewall in Microsoft Azure and OCI Network Firewall in OCI. The last step is validating network connectivity between OCI/Microsoft Azure regions and ensuring traffic is validated through Firewall based on routing capabilities via Firewalls over OCI/Microsoft Azure Interconnect.
Prerequisites
-
An active Microsoft Azure subscription and an active OCI tenancy.
-
A Microsoft Azure ExpressRoute peering location in proximity to or in the same peering location as OCI FastConnect. See Region Availability.
-
Direct connectivity between Microsoft Azure and OCI interconnected regions are completed successfully. See Configure Direct Connectivity between ExpressRoute and FastConnect.
-
Familiarity with networking and cloud services is assumed, including OCI FastConnect, OCI Network Firewall, Microsoft Azure Firewall, and Microsoft Azure ExpressRoute.
-
Understanding of OCI Microsoft Azure Interconnect is required.
Audience
This tutorial is intended for Cloud Service Providers professionals and multicloud administrators.
Architecture
Below is the high level architecture of the solution.
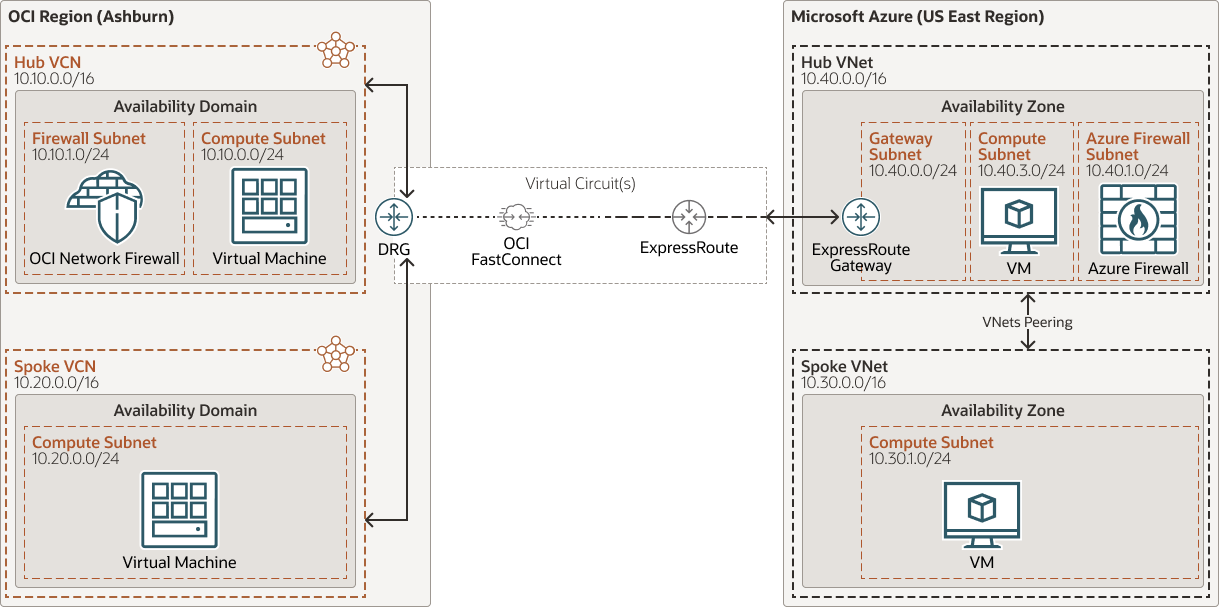
You can refer to this architecture when you want to setup an interconnected region and secure your traffic using Network Virtual Appliance in a Hub and Spoke architecture.
Task 1: Create Virtual Network and Subnet on Microsoft Azure
-
Sign in to the Microsoft Azure Portal.
-
On the upper-left side of the screen, select Create a resource, Networking, Virtual network or search for Virtual network in the search box.
-
In Create virtual network, enter or select this information in the Basics tab:
Project Details
-
Subscription: Select your Azure subscription.
-
Resource Group: Select Create new, enter resource-group-name, then select OK, or select an existing resource-group-name based on parameters.
Instance details
-
Name: Enter virtual-network-name.
-
Region: Select region-name.
-
-
Select the IP Addresses tab or select the Next: IP Addresses button at the end of the page.
-
In the IP Addresses tab, enter this information:
- IPv4 address space: Enter ipv4-address-range; Example: Hub VNET: 10.40.0.0/16 for US East Region, Spoke VNET: 10.30.0.0/16 for US East Region.
-
Under Subnet name, select the word default.
-
In Edit subnet, enter this information:
-
Subnet name: Enter subnet-name.
-
Subnet address range: Enter subnet-address-range Example: Compute Subnet: 10.40.3.0/24 for Hub VNET, Compute Subnet: 10.30.1.0/24 for Spoke VNET.
-
-
Select Save.
-
Select the Review + create tab or select the Review + create button.
-
Select Create.
Repeat Steps 1-9 for both Hub and Spoke VNets and then proceed to the next section to create Microsoft Azure Firewall Subnet.
Task 2: Create a Microsoft Azure Firewall Subnet
Follow the step-by-step guide to create a Firewall Subnet using the following minimum parameters.
-
firewall-subnet-name: AzureFirewallSubnet name must be filled.
-
subnet-address-range: Enter Firewall Subnet Address Range; Example: 10.40.1.0/24 in Hub VNET.
Proceed to the next section to create Gateway Subnet and Virtual Network Gateway.
Task 3: Create a Gateway Subnet and Virtual Network Gateway on Microsoft Azure
You can follow the step-by-step guide to create a Gateway Subnet and Virtual Network Gateway using the minimum parameters described in the following tables.
Gateway Subnet Parameters
| Parameter | Value |
|---|---|
| gateway-subnet-name | GatwaySubnet name filled automatically. |
| subnet-address-range | Enter Gateway Subnet Address Range; Example: 10.40.0.0/24 in Hub VNET |
VNET Gateway parameters:
| Setting | Value |
|---|---|
| Project Details | |
| Subscription | Select your Microsoft Azure subscription |
| Resource Group | This will be automatically selected on your VNET selection. |
| Gateway details | |
| Name | Enter gateway-name |
| Region | Select (US) East US or Region where you have created VNET |
| Gateway type | Select ExpressRoute |
| SKU | Select the Gateway SKU from dropdown |
| Virtual Network | Select VNET created earlier within your region. |
| Public IP Address | |
| Public IP address | Select Create new. |
| Public IP address name | Enter a name for Public IP address. |
Once you have created required resources in Microsoft Azure Region, proceed to next section to deploy Microsoft Azure Firewall.
Task 4: Deploy Microsoft Azure Firewall in the Hub Virtual Network on Microsoft Azure
You can follow the step-by-step guide to deploy a Microsoft Azure firewall in your Hub VNET using the minimum parameters described in the following table.
| Parameter | Value |
|---|---|
| Subscription | Select your subscription. |
| Resource group | Select your-resource-group. Select the resource group which you must have created during pre-reqs steps. |
| name | Enter firewall-name |
| firewall-sku | Select Firewall SKU from provided option |
| firewall-policy | Click on Add New and Create a new Firewall Policy. |
| choose-a-virtual-network | Select your Virtual Network created earlier |
| public-ip-address | Select or Create a new Public IP |
Proceed to the next section to connect your ExpressRoute Circuit to the Virtual Network Gateway.
Task 5: Connect your ExpressRoute Circuit to the Virtual Network Gateway via a connection on Microsoft Azure
You can follow the step-by-step guide to create a ExpressRoute connection using the minimum parameters described in the following table.
| Parameter | Value |
|---|---|
| Subscription | Select your subscription. |
| Resource group | Select your-resource-group. Select the resource group which you must have created during pre-reqs steps. |
| connection-type | Select ExpressRoute |
| Name | Enter connection-name |
| Region | Select (US) East US or Region where you have created VNET Gateway. |
| virtual-network-gateway | Select VNET gateway created earlier. |
| expressroute-circuit | Select ExpressRoute Circuit created in pre-requisites steps. |
Once you have created required connections in both Microsoft Azure Regions, proceed to the next section to create user-defined route tables for subnets in VNets.
Task 6: Create user defined routes on Microsoft Azure
You can follow the step-by-step guide to create user defined routes to each subnet’s associated table using the minimum parameters described in the following tables.
Configure Gateway Subnet’s route table entries
| Parameter | Value |
|---|---|
| route-name | Enter Route Name |
| address-prefix-destination | Enter Destination Prefixes. Example: Hub Compute Subnet: 10.40.3.0/24, Spoke Compute Subnet: 10.30.1.0/24 |
| next-hop-type | Select Virtual Appliance. |
| next-hop-address | Enter Next hop address as Firewall’s Private IP Example: 10.40.1.4 |
Ensure that you have required entries and associate that route table to Gateway Subnet of Hub VNet.
Configure Compute Subnet’s in Hub VNet route table entries
| Parameter | Value |
|---|---|
| route-name | Enter Route Name |
| address-prefix-destination | Enter Destination Prefixes; Example: OCI Hub Compute Subnet: 10.10.0.0/24, OCI Spoke Compute Subnet: 10.20.0.0/24, Microsoft Azure Spoke Subnet: 10.30.1.0/24, Microsoft Azure Hub VNET: 10.40.0.0/16 |
| next-hop-type | Select Virtual Appliance. |
| next-hop-address | Enter Next hop address as Firewall’s Private IP Example: 10.40.1.4 |
Ensure that you have required entries and associate this route table to Compute Subnet of Hub VNet.
Configure Compute Subnet’s in Spoke VNet route table entries
| Parameter | Value |
|---|---|
| route-name | Enter Route Name |
| address-prefix-destination | Enter Destination Prefixes; Example: OCI Hub Compute Subnet: 10.10.0.0/24,OCI Spoke Compute Subnet: 10.20.0.0/24,Microsoft Azure Hub Compute Subnet: 10.40.3.0/24 |
| next-hop-type | Select Virtual Appliance. |
| next-hop-address | Enter Next hop address as Firewall’s Private IP Example: 10.40.1.4 |
Ensure that you have required entries and associate this route table to Compute Subnet of Spoke VNet.
Once you have created the required routes, proceed to the next section to create Virtual machines to validate the traffic between Microsoft Azure and OCI.
Task 7: Create user defined routes on Microsoft Azure
In this section you will create virtual machines to validate the connectivity from Microsoft Azure to Oracle Cloud Infrastructure.
-
On the upper-left side of the screen in the Microsoft Azure portal, select Create a resource, Compute, Virtual machine.
-
In Create a virtual machine - Basics, enter or select this information.
Setting Value Project details Subscription Select your subscription. Resource group Select your-resource-group. Select the resource group which you must have created during pre-requisites steps. Instance details Virtual machine name Enter vm-name. Region Select (US) East US or Region where you are deploying. Availability options Leave the default No infrastructure redundancy required. Image Select Ubuntu Server 18.04 LTS - Gen1. Size Select Standard_B2s. Administrator account Authentication type Select Password. You can also choose SSH based authentication and update required value as needed. Username Enter a username of your choosing. Password Enter a password of your choosing. The password must be at least 12 characters long and meet the defined complexity requirements. Confirm Password Re-enter password. Inbound port rules Public inbound ports Select None. -
Select Next: Disks.
-
In Create a virtual machine - Disks, leave the defaults and select Next: Networking.
-
In Create a virtual machine - Networking, select this information.
Setting Value Virtual network Select virtual-network. Subnet Select compute-subnet for example: 10.40.3.0/24 in Hub VNet, 10.30.1/24 in Spoke VNet Public IP Leave the default (new) my-vm-ip. Public inbound ports Select Allow selected ports. Select inbound ports Select SSH. -
Select Review + create. You are taken to the Review + create page where Microsoft Azure validates your configuration.
-
When you see the Validation passed message, select Create.
Repeat Steps 1-7 for both Spoke and Hub VNet VMs and proceed to the next section to create required resources on Oracle Cloud Infrastructure.
Task 8: Create resources on Oracle Cloud Infrastructure
In this section you will create the required resources to support validation from OCI console within interconnected regions. In the OCI console, create following resources in each region.
-
Create a Hub Virtual Cloud Network with a Compute Subnet.
-
Create required Management and Traffic Subnets in Hub VCN.
-
Deploy OCI Network Firewall in Hub VCN.
-
Create a Spoke Virtual Cloud Network with a Compute Subnet.
-
Create a Hub VCN attachment to the DRG created in the prerequisites which has OCI/Microsoft Azure Interconnection virtual circuit.
-
Create a Spoke VCN attachment to the DRG created and extend the ingress route to OCI Network Firewall.
-
Create a Virtual Machines within Compute Subnet of Hub and Spoke VCNs and update required routes/security lists to connect with Microsoft Azure VNETs.
-
Extend Virtual Cloud Network connectivity to Microsoft Azure VNET via DRG. You can follow this step-by-step guide.
-
Follow this step-by-step workshop to deploy OCI Network Firewall on OCI in a Hub and Spoke architecture.
-
Follow this step-by-step guide to create a VM and complete required Virtual Cloud Network/Subnet work.
-
Follow this step-by-step guide to establish region peering between OCI Regions through DRG.
Task 9: Validate the traffic in OCI/Microsoft Azure Interconnect
In this section you will connect to Linux VMs of both Cloud Providers and do a ping test to check the connectivity.
-
Connect to Linux VMs on both cloud providers using your terminal.
-
Initiate a ICMP RTT from Microsoft Azure VMs to OCI VMs and vice-versa.
-
This will ensure network connectivity.
-
Below table shows a connectivity test performed based on shared network topology and reflects you can reach from Hub and Spoke of Microsoft Azure environment to Hub and Spoke of OCI.
-
You can also monitor the traffic from Firewall logs available within Virtual Appliance.
Traffic Validation SRIOV/Accelerated Networking ICMP RTT (Milliseconds) OCI Hub VM to Microsoft Azure Hub VM; 10.10.1.168 > 10.40.3.4 yes 3.9 OCI Hub VM to Microsoft Azure Spoke VM; 10.10.1.168 > 10.30.1.4 yes 4.5 OCI Hub VM to OCI Spoke VM; 10.10.1.168 > 10.20.0.190 yes 0.75 OCI Spoke VM to Microsoft Azure Hub VM; 10.20.0.190 > 10.40.3.4 yes 4.52 OCI Spoke VM to Microsoft Azure Spoke VM; 10.20.0.190 > 10.30.1.4 yes 5.33 OCI Spoke VM to OCI Hub VM; 10.20.0.190 > 10.10.0.168 yes 0.64 Microsoft Azure Hub VM to Microsoft Azure Spoke VM; 10.40.3.4 > 10.30.1.4 yes 4.35 Microsoft Azure Hub VM to OCI Hub VM; 10.40.3.4 > 10.10.0.168 yes 4.46 Microsoft Azure Hub VM to OCI Spoke VM; 10.40.3.4 > 10.20.0.190 yes 4.68 Microsoft Azure Spoke VM to Microsoft Azure Hub VM; 10.30.1.4 > 10.40.3.4 yes 4.72 Microsoft Azure Spoke VM to OCI Hub VM; 10.30.1.4 > 10.10.0.168 yes 4.24 Microsoft Azure Spoke VM to OCI Spoke VM; 10.30.1.4 > 10.20.0.190 yes 4.43
ICMP RTT between Microsoft Azure and OCI reflects connectivity established between OCI and Microsoft Azure regions using interconnect and traffic going through native firewall services as per our network topology.
Note: Above table reflects ICMP RTT as a reference point which could vary depending on the regions and use case architecture. It is recommended to do a POC.
You can find more information about Microsoft Azure latency between regions in: Microsoft Learn: Microsoft Azure network round-trip latency statistics
For more information on how to test Virtual Machine latency consult: Microsoft Learn: Test Microsoft Azure virtual machine network latency in an Microsoft Azure virtual network
Task 10: Clean up resources
When you are done using the resources, delete the resource group and associated resources.
-
Delete the interconnect link if you haven’t done already. For details, see the step-by-step guide.
-
Enter your-resource-group-name in the Search box at the top of the portal and select your-resource-group-name from the search results.
-
Select Delete resource group.
-
Enter your-resource-group-name for TYPE THE RESOURCE GROUP NAME and select Delete.
-
Similarly delete the resources deployed in Oracle Cloud Infrastructure.
Related Links
-
Overview of Oracle Applications and solutions on Microsoft Azure
-
Blog: Step-by-Step Guide: Interconnecting Oracle Cloud Infrastructure and Microsoft Azure
Acknowledgments
-
Author - Arun Poonia, Principal Solution Architect
-
Contributor - Daniel Mauser, Principal Solutions Specialist Global Black Belt – Microsoft Azure Networking
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Secure traffic between Oracle Cloud Infrastructure and Microsoft Azure using Network Virtual Appliance
F81212-02
July 2023
Copyright © 2023, Oracle and/or its affiliates.