Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Integrate Oracle Cloud Infrastructure Compute Instances to Microsoft Entra Domain Services Managed Domain
Introduction
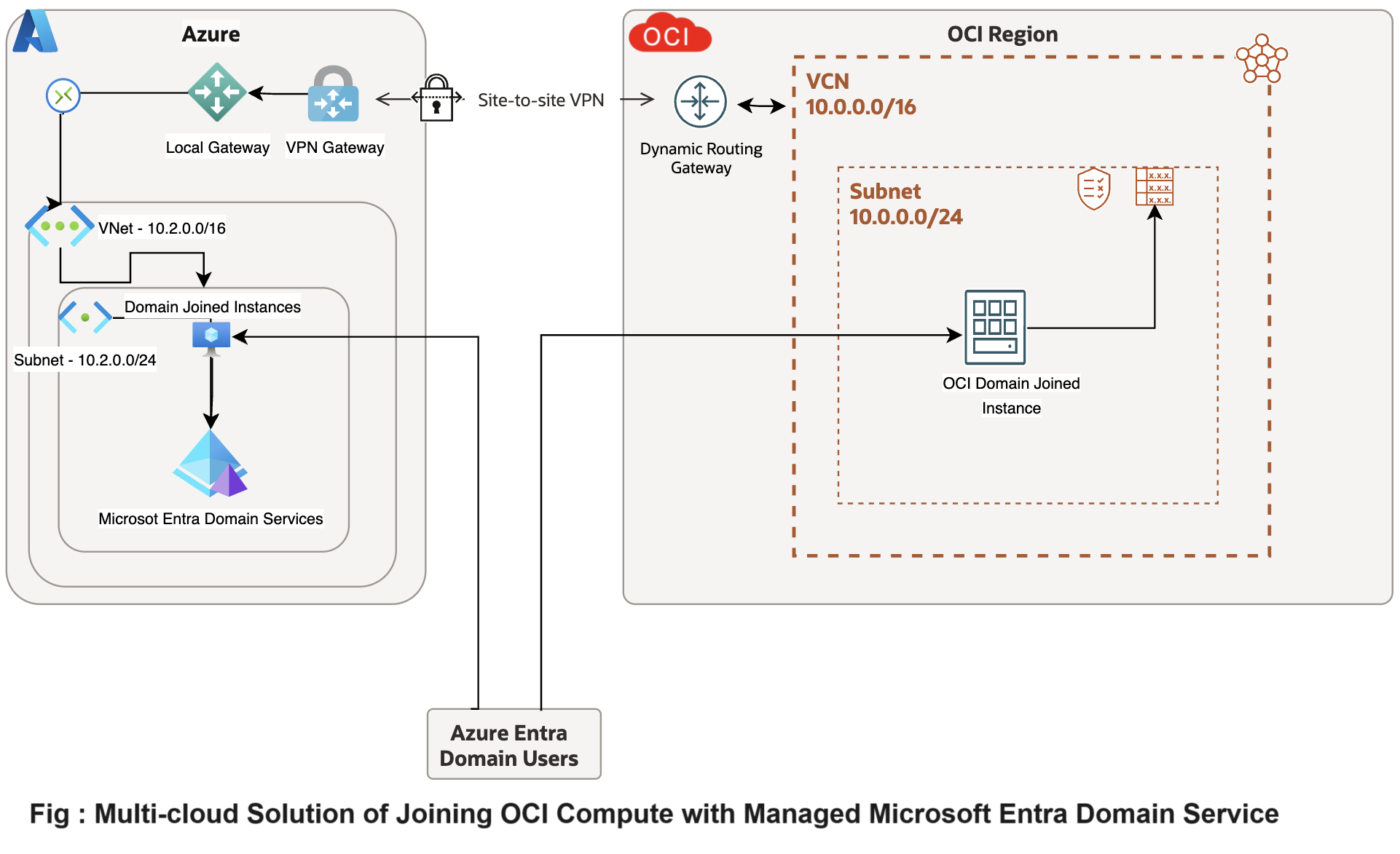
In modern multicloud and hybrid cloud environments, effective network management and seamless integration between different cloud services are crucial. One such integration challenge is joining an Oracle Cloud Infrastructure (OCI) Compute instance to Microsoft Entra Domain Services (formerly known as Azure Active Directory Domain Services). This set up allows organizations to leverage Microsoft’s robust identity management capabilities while running compute workloads on OCI.
To accomplish this, it is essential to properly configure the network infrastructure, including virtual cloud networks (VCNs), subnets, routing tables, and establishing a network connection between OCI and Microsoft Azure. This connection can be achieved using either a OCI Site-to-Site VPN or dedicated interconnect solutions like OCI FastConnect and Azure ExpressRoute. Additionally, managing Dynamic Host Configuration Protocol (DHCP) options in OCI to point to the correct Domain Name System (DNS) servers of Microsoft Entra Domain Services is a critical for domain-joining operations.
This tutorial provides a guide to set up network configurations to enable OCI instances to join Microsoft Entra Domain Services. We will deploy VCNs, establish a site-to-site VPN between OCI and Azure, configure route tables for inter-cloud communication,create and associate DHCP option sets or with forwarding rules to Azure Managed adds service IP’s in DNS resolver in OCI, deploy compute instances, and verify the connectivity and domain join process. By following these tasks, organizations can achieve seamless integration between OCI and Microsoft Azure, enabling a unified and secure multicloud environment.
Objectives
- Integrate OCI Compute instances to Microsoft Entra Domain Services managed domain. This tutorial provides a simple guide to set up DNS forwarding in OCI to integrate with Microsoft Entra Domain Services. We will create compute instance, join Microsoft Azure Entra Domain, DNS resolvers and forwarding rules in OCI to direct specific domain queries to Microsoft Entra Domain Services without modifying DHCP options for the VCN.
Prerequisites
-
OCI and Microsoft Azure Cloud tenancies.
-
OCI and Microsoft Azure tenancy permissions to deploy and update the resources.
-
Basic understanding of networking: DNS, DHCP, and network routing.
Task 1: Configure Site-to-Site VPN or Dedicated Interconnect between OCI and Microsoft Azure
To enable secure communication between OCI and Microsoft Azure, we use a site-to-site VPN. This VPN creates a secure tunnel over the internet, connecting OCI’s Virtual Cloud Network (VCN) with Azure’s Virtual Network (VNet). For organizations requiring high reliability, low latency, and dedicated bandwidth, OCI FastConnect is preferred. OCI FastConnect offers a private connection, bypassing the public internet for enhanced security and consistent performance. However, in this set up, we opt for the simplicity and cost-effectiveness of a site-to-site VPN, which is essential for integrating services like Microsoft Entra Domain Services. For more information, see VPN Connection to Azure.
-
Create and configure VPN gateway in OCI.
-
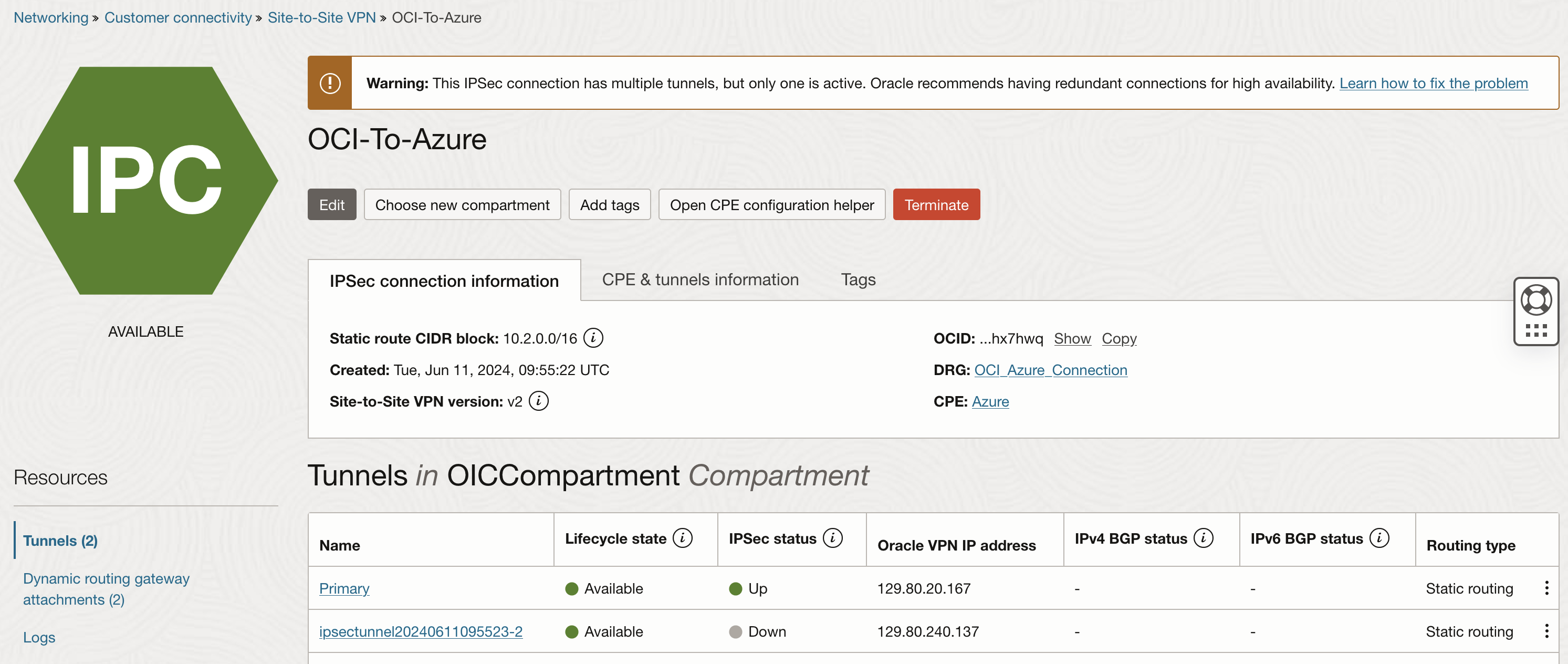
Log in to the OCI Console, go to Networking and select Dynamic Routing Gateway (DRG).
-
Create a DRG and attach it to your VCN. For this tutorial, OCI VCN is
10.0.0.0/16. -
Set up a Customer-Premises Equipment (CPE) object with the Azure VPN gateway public IP address.
-
Create an IPSec connection between the DRG and the Azure VPN gateway, using the provided IPSec configuration.
-
-
Configure VPN gateway in Microsoft Azure.
-
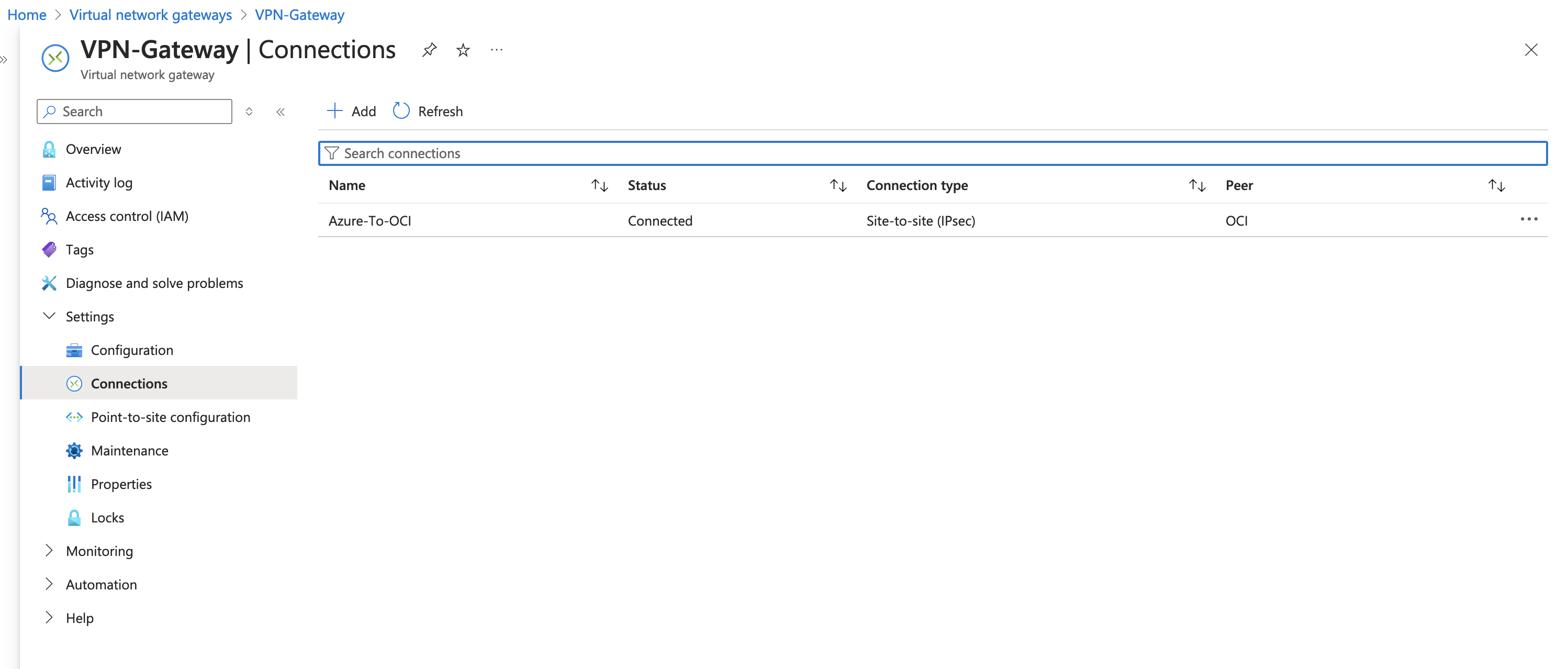
Log in to the Microsoft Azure Portal, navigate to Virtual Network Gateway.
-
Create a VPN gateway in the Azure VNet. For this tutorial, Azure VNet is
10.2.0.0/16. -
Set up a local network gateway with the OCI VPN gateway’s public IP address.
-
Establish an IPSec VPN connection to the OCI DRG using the configuration details from OCI.
-
Task 2: Set up Microsoft Entra Domain Services
After establishing the site-to-site VPN between OCI and Microsoft Azure, proceed with setting up Microsoft Entra Domain Services in Microsoft Azure. This service simplifies identity management with features like domain join and Lightweight Directory Access Protocol (LDAP), without needing traditional domain controllers.
-
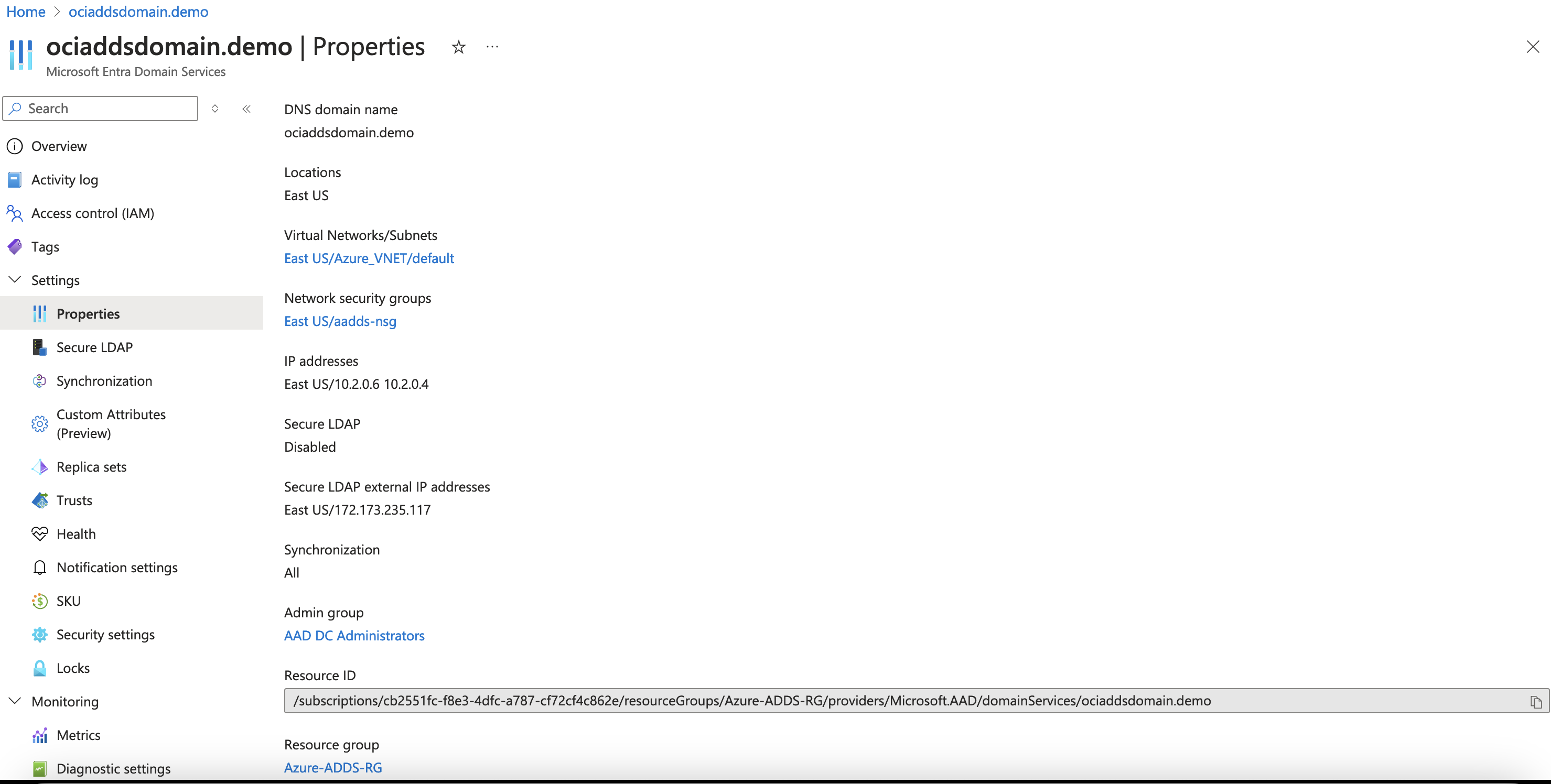
Deploy and configure Microsoft Entra Domain Services in Microsoft Azure.
-
Deploy Microsoft Entra Domain Services using the Microsoft Azure Portal.
-
Configure domain settings to meet organizational needs.
-
Ensure to utilize a subnet within the same VCN where the site-to-site VPN with OCI is configured.
-
-
Get the private IP addresses of Microsoft Entra Domain Services DNS servers.
-
Note the private IP addresses of DNS servers linked with Microsoft Entra Domain Services.
-
Configure these IPs for DNS resolution within OCI’s Virtual Cloud Network (VCN) to enable domain name resolution.
-
Task 3: Configure DNS Resolution in OCI VCN
Configure DNS resolution within OCI’s Virtual Cloud Network (VCN) to enable domain name resolution. Use the same VCN where you have configured the OCI Site-to-Site VPN established with Microsoft Azure.
-
Go to the OCI Console, navigate to Networking, Virtual Cloud Network and DNS Resolver.
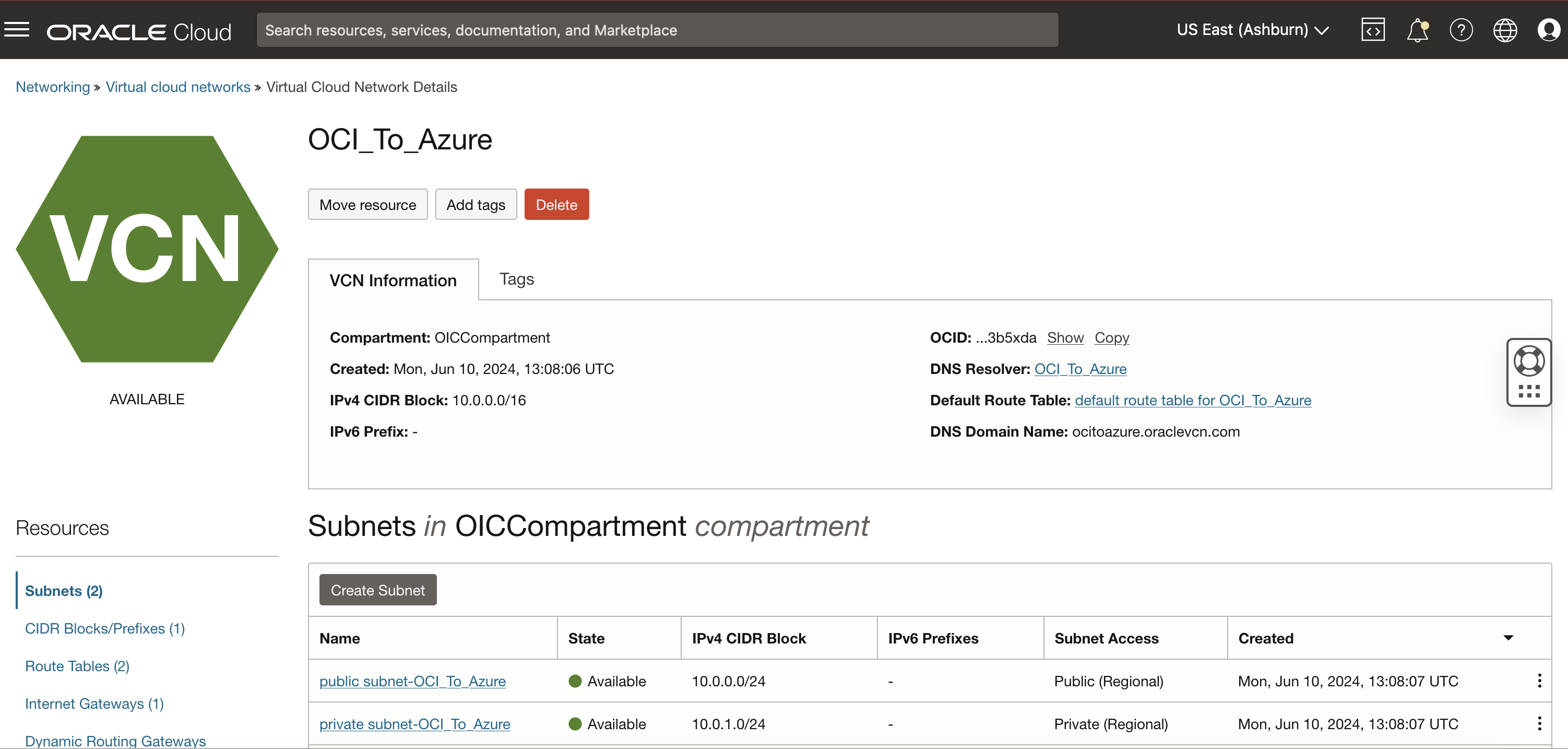
-
Create both listening and forwarding endpoints.
-
Set up endpoints to forward DNS queries for the domain managed by Microsoft Entra Domain Services.
-
Under Endpoints, click Create Endpoint to configure DNS forwarding.
-
Enter the Name for the endpoint.
-
Select a VCN subnet from the list (same VCN subnet for which you configured the site-to-site with Azure VNet) and select the Endpoint Type as Forwarding. Leave the optional fields and click Create.
-
Repeat substeps 1 to 4 for listening endpoints.
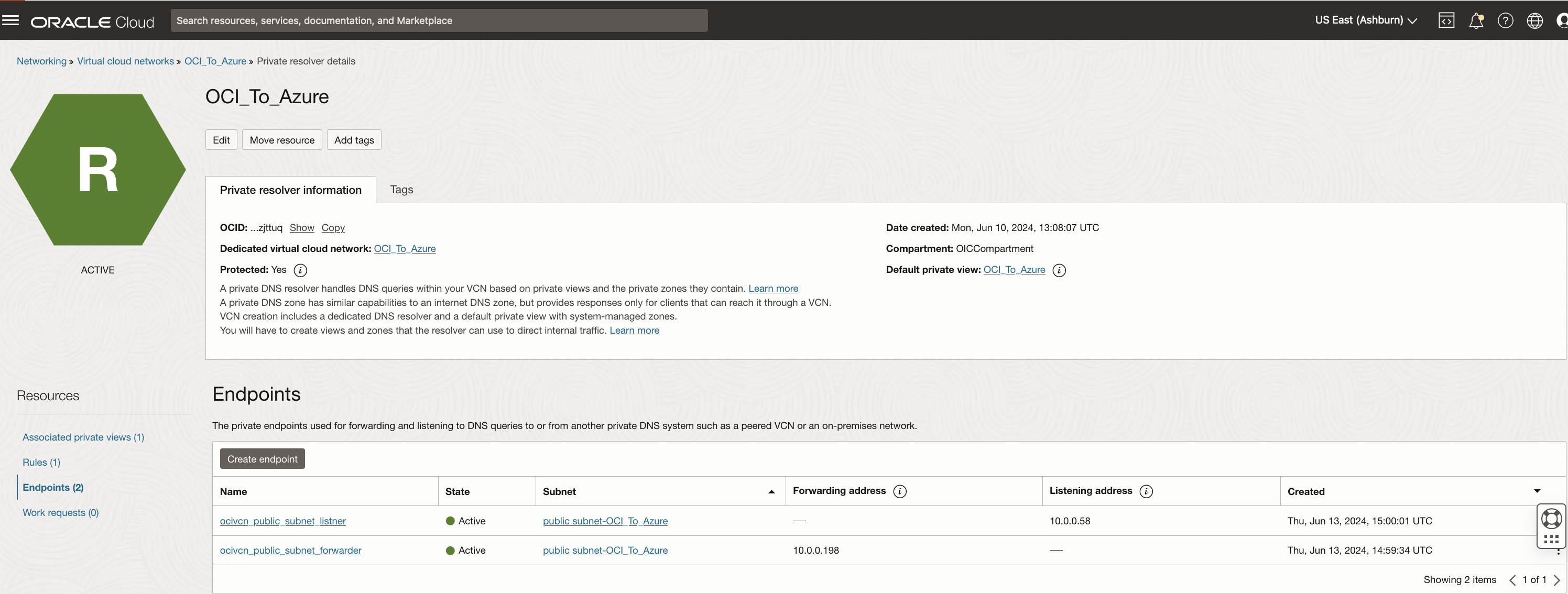
-
-
Configure rules in OCI.
-
Define rules to control DNS traffic within the VCN.
-
Configure forwarding rules to direct queries for the domain managed by Microsoft Entra Domain Services to the endpoints created in Task 3.2.
-
Under Rule condition, click Domains and Manage rules.
-
In Domains, enter the domain created in Task 2.
-
Under Source endpoint, select the endpoints created in Task 3.2.
-
Enter the IP address of Microsoft Entra Domain Services noted in Task 2.
-
Repeat substeps 1 to 6 for the second IP address.
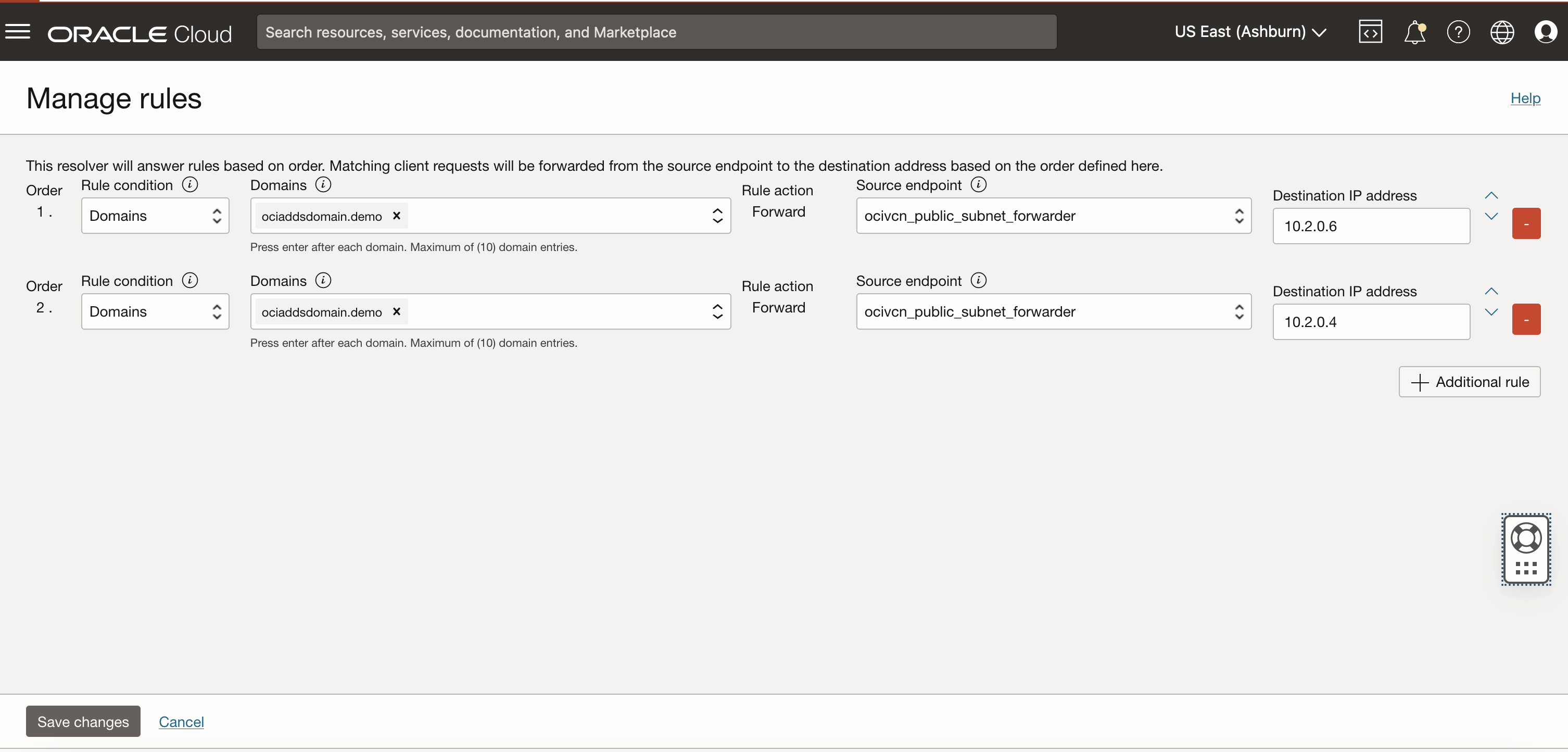
-
DNS resolution set up in OCI VCN ensures that OCI instances can securely resolve domain names managed by Microsoft Entra Domain Services over the established VPN connection to Microsoft Azure.
Note: If you want to make the Microsoft Entra Domain Servers as DNS servers of OCI Instnaces, then you can skip Task 3 and Edit the Default DHCP Options –> DNS Type: Select Custom Resolver –> Enter the DNS Servers IP address(Azure Domain Service IP’s) –> Select Custom Search Domain and under the Search Domain Mention the domain name of the “Created Microsoft Entra Domain Service”. Stop and Start all the servers of OCI to get reflected.
Task 4: Verify DNS Configuration and Network Connectivity
We have configured DNS resolution in OCI VCN and deployed VMs. Now, verify the set up and enable Internet Control Message Protocol (ICMP) ping to Microsoft Entra Domain Services IP from OCI Windows Server instances.
-
Create Windows Server VM in OCI.
-
Go to the OCI Console, navigate to Compute and Instances.
-
Click Create Instance.
-
Select Windows Server 2016 or 2019 Standard image from the available images.
-
Specify the subnet where DNS resolution and VPN connectivity are configured.
-
Configure other instance details as needed (shape, boot volume and networking).
-
-
Configure network security rules in OCI.
-
Go to the OCI Console, navigate to Networking and Virtual Cloud Networks (VCNs).
-
Edit the security list associated with the subnet where your Windows Server VM is deployed.
-
Add an ingress rule to allow TCP traffic on port
3389(RDP) from your network. -
Add an ingress rule to allow ICMP traffic (ping) from Azure VNet CIDR range (
10.2.0.0/16) to the IP address of Azure VM’s.
-
-
Verify the network connectivity.
-
Log in to the Windows Server VM in OCI.
-
Open the command prompt and use the
pingcommand to test connectivity to the private IP address of the Microsoft Entra Domain Services.Example commands:
ping <Azure Entra Domain Service IP>ping <Azure Entra Domain>nslookup <Azure Entra Domain>
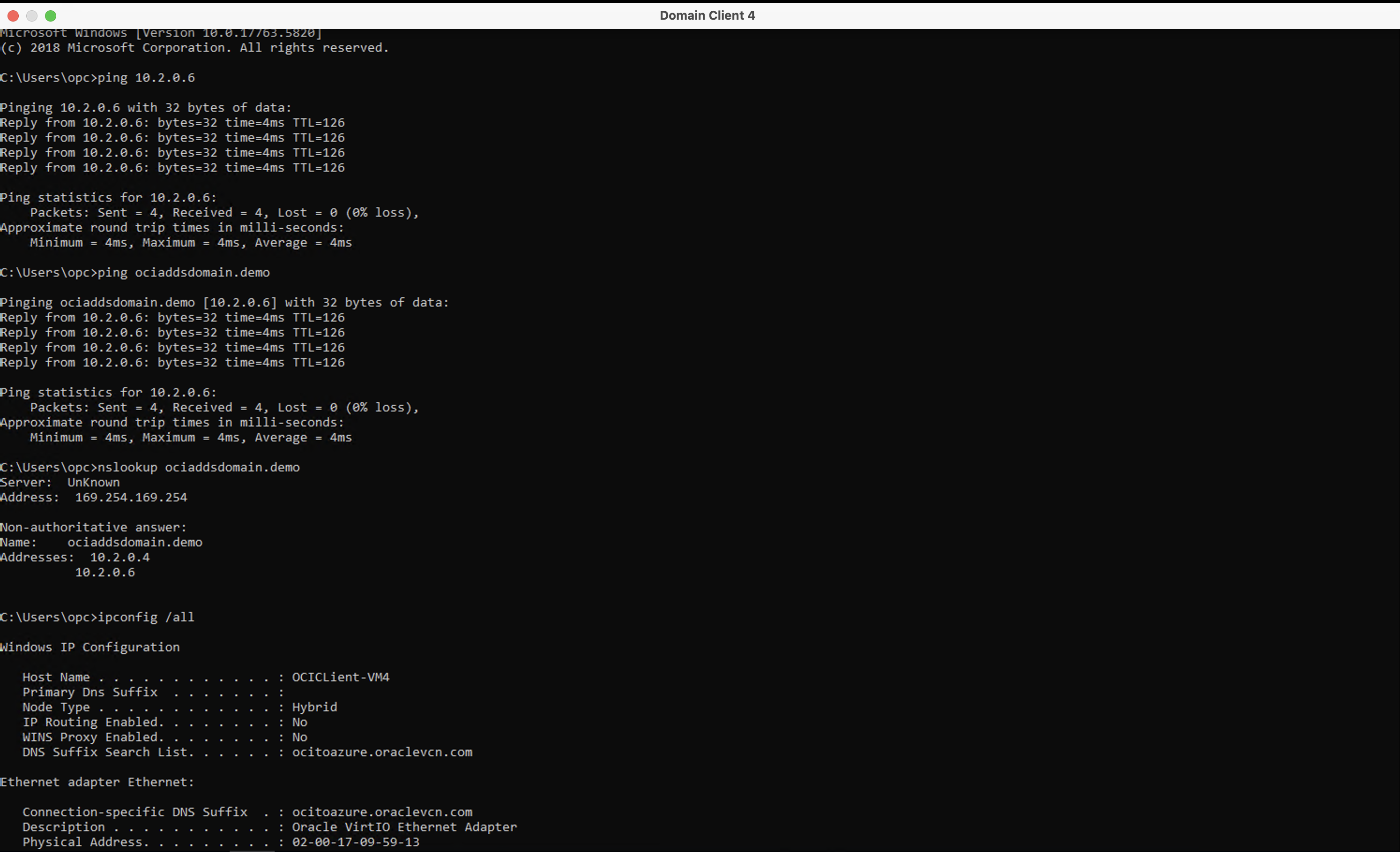
ICMP ping and
nslookuptest confirms connectivity between OCI Windows Server instances and Microsoft Entra Domain Services. -
Task 5: Join Windows Server VM to Microsoft Entra Domain Services
After verifying DNS and network connectivity, the next task is to join your OCI Windows Server VM to Microsoft Entra Domain Services. Follow these steps to complete the domain join process.
-
Access system properties.
-
In Server Manager, click Local Server in the left pane.
-
In the Properties section, click Computer Name/ WorkGroup, it will show system properties window.
-
-
Join the domain.
-
Click Change in the System Properties window.
-
Select Domain and enter the Microsoft Entra Domain Services domain name.
-
Click OK.
-
-
Enter credentials.
- When prompted, enter the credentials of a user who is a member of the AAD DC Administrators group.
- Use the format
username@domain.com, Microsoft Entra ID users which are the members of admin group AAD DC Administrators.
- Use the format
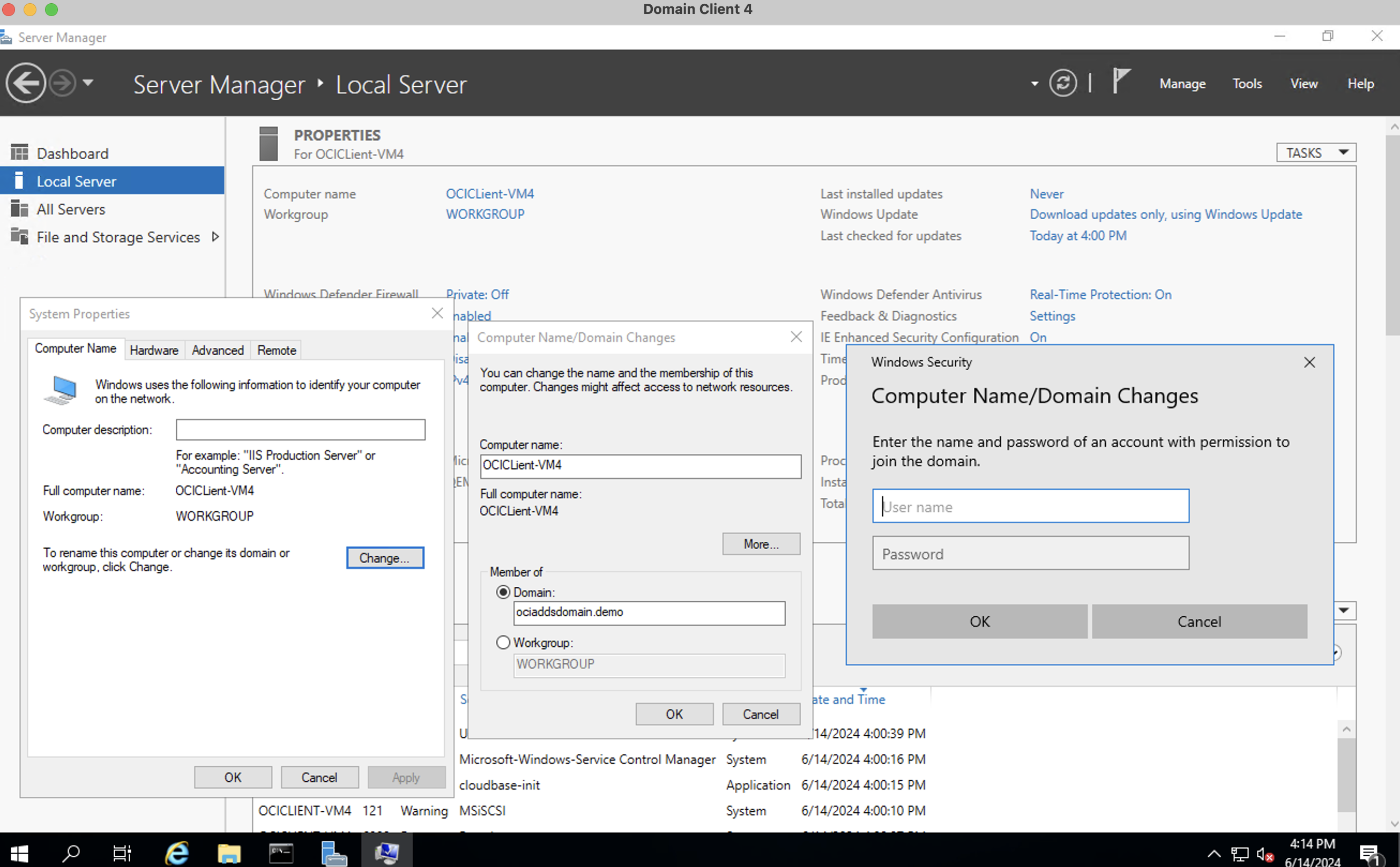
- When prompted, enter the credentials of a user who is a member of the AAD DC Administrators group.
-
Restart the VM to complete the domain join process.
By following these tasks, your Windows Server VM in OCI will be joined to Microsoft Entra Domain Services.
Related Links
Acknowledgments
- Author - Akarsha I K (Cloud Architect)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Integrate Oracle Cloud Infrastructure Compute Instances to Microsoft Entra Domain Services Managed Domain
G10552-01
June 2024