Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Automate Oracle Cloud Infrastructure Identity and Access Management Domain Group Membership with Okta Push Groups
Introduction
In the real world there might be scenarios where customers can have Okta as their corporate identity provider (IdP), but the users also need access to services hosted by Oracle Cloud Infrastructure (OCI). In such scenarios, we recommend setting up federation to automate the users and group auto provisioning from Okta to identity domains for better lifecycle management of users.
For more information about setting up federation and provisioning, see SSO With OCI and Okta and Identity Lifecycle Management Between OCI and Okta.
For managing group memberships in Okta and Oracle Cloud Infrastructure (OCI), Push Group play a crucial role. Let us look at various scenarios involving the provisioning and management of group memberships using Okta Push Group.
Key Benefits
- You can leverage the groups in Okta IdP and push it to Oracle Cloud Infrastructure Identity and Access Management (OCI IAM) domain.
- You can also push multiple groups by creating the rules and sync to OCI IAM domain.
Objectives
- Automate Oracle Cloud Infrastructure Identity and Access Management (OCI IAM) domain group membership with Okta Push Group.
Prerequisites
- Oracle apps premium SKU for OCI IAM domains.
- Admin account for OCI IAM domain.
- Okta as IdP added to the OCI IAM domain.
- Admin account for Okta.
Task 1: Sync Group Membership to OCI IAM domains
When a group does not exist on the OCI IAM domains, you can create Push Groups by name.
-
Select the Okta group with members in it.
-
Select Create group for OCI.
This process ensures that the group appears on the OCI IAM domain but does not have members in it.

Next, you can assign users from the Okta group to the application under Assignments.
You will notice that the users you assigned on Okta get provisioned in the OCI IAM domain, and the membership of the group gets updated.
Note: Regardless of the number of users in the Okta group on the Okta side, the users assigned to the app will be shown under the membership of the pushed group on OCI IAM domain. Also, Okta recommends that you should assign the group to the application when pushing it through push groups.
Or
In the scenario where a group already exists in the OCI IAM domain, the process for ensuring efficient group synchronization involves the following steps.
-
Identify the Okta group containing the necessary members.
-
Link the group and select the pre-existing group on the OCI IAM domains.
Note: When a group with the same name is found in the OCI IAM domains, the system will seamlessly move the members to this existing group. Conversely, if the group names do not match, the selected group will be automatically renamed to align with the Okta group name, thereby maintaining consistency between the two platforms.
By following these guidelines, organizations can streamline the management of group memberships, ensuring that members are accurately allocated while upholding naming conventions across the OCI IAM domain and Okta platform.
Task 2: Dissociate Groups from Push Provisioning
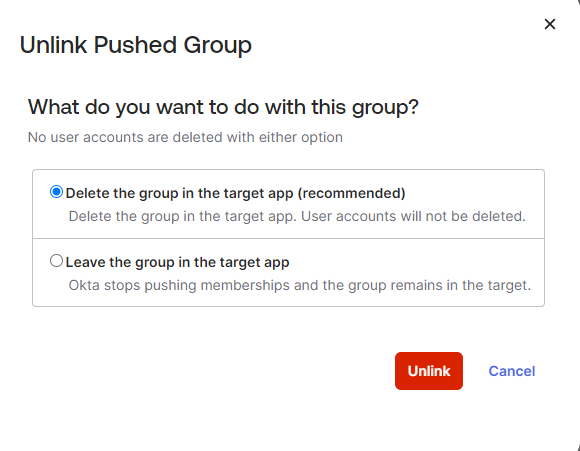
When a group is unlinked from push on the Okta end, you have two ways to unlink the group effectively.
-
Delete the group in the target app (recommended): By deleting the group in the target app, you effectively unlink it. This action will delete the group in the OCI IAM domain while ensuring that users remain in the OCI IAM domain and remain in an active state. If the Push Group link is created again for the same group, the group, along with its membership, will be recreated on the OCI IAM domain.
-
Leave the group in the target app: Opting to leave the group in the target app will also unlink the group, but the group will persist on the OCI IAM domain along with its membership.
Upon creating the group link again, you will see a match found with the group on the OCI IAM domain. This process will re-establish the link between the groups.
Important Points to Note
When a linked group is explicitly deleted from the OCI IAM domains, certain steps need to be taken.
-
Even after deletion, the link may still appear in Okta, but the push process will encounter an error stating Linked group is missing in OCI IAM. Change the linked group to resume pushing group memberships.
-
Re-creating the group with the same name on the OCI IAM domain will not automatically re-link the Okta group. The recommended solution is to delete the link on Okta and then re-create the link.
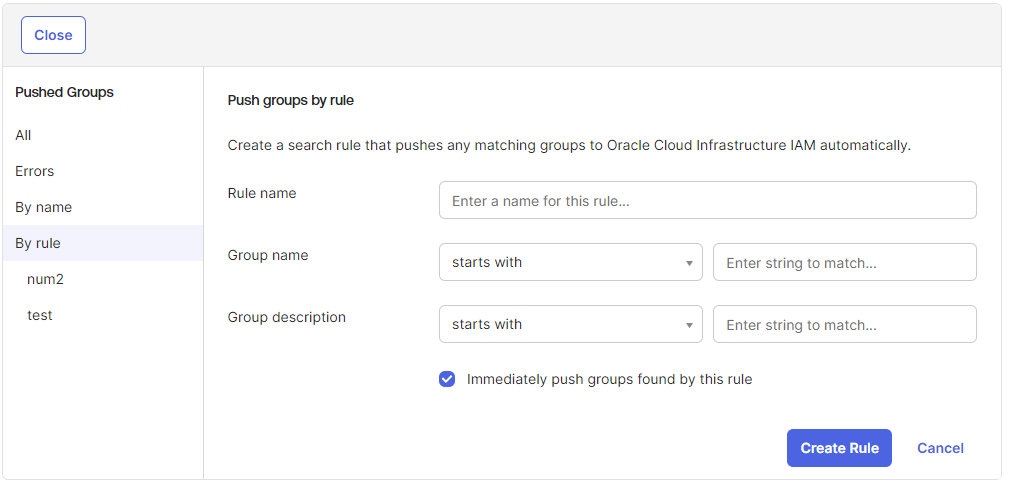
Additionally, there is a useful feature for Push Groups called Push Groups by Rule. Here is how it works.
-
You can create a rule with conditions on when to push groups from Okta to the OCI IAM domain.
-
The conditions can be based on group name or group description, with various operators available for both fields, such as starts with, ends with, and contains.
Next Steps
Pushing the groups with its membership from the Okta to OCI IAM domain helps you to maintain the access to your end applications easily by assigning those groups to the applications. Further, you can update the membership to allow or disallow the access to end applications by simply updating the membership on Okta.
Acknowledgments
- Author - Sagar Takkar
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Automate OCI IAM Domain Group Membership with Okta Push Groups
G13390-01
August 2024