Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Secure your Oracle Cloud VMware Solution workloads with Oracle Cloud Infrastructure Network Firewall
Introduction
This document covers how you can use Oracle Cloud Infrastructure (OCI) Network Firewall to secure your workloads running in an Oracle Cloud VMware Solution. Oracle Cloud VMware Solution allows you to create and manage VMware Software-Defined Data Center (SDDCs) in OCI.
OCI Network Firewall can be deployed as a Distributed model or a Transit model. In this tutorial, we will deploy Transit model, where the Network Firewall is in Hub VCN, Oracle Cloud VMware Solution SDDC in a spoke VCN. Using Intra-VCN and Ingress routing capabilities of OCI Networking, you can inspect the traffic via Network Firewall running in Hub VCN.
Note: Even though this tutorial showcases OCI Network Firewall, most of the concepts should apply to any other 3rd party appliances like Fortinet, Palo Alto Networks, Cisco, Check Point, and more. The customer needs to work with the specific vendor/partner to make sure it is supported by the vendor.
Use Cases
OCI Intra VCN routing capabilities give us the simplicity of configuring routing to support OCI workload traffic within VCNs and you can also use a Firewall to inspect/secure your traffic. We will be using Intra-VCN and ingress routing capabilities which include:
-
Intra-VCN routing – This allows you to change the direct routing for intra-VCN traffic with your defined routes. You will be able to define subnet-level routes.
-
Internet Gateway/Network Address Translation Gateway ingress routing – This allows the definition of routes for inbound public traffic to the VCN towards a user-selected next-hop.
-
Software Gateway ingress routing enhancement – This allows you to define your routes for Software Gateway to route traffic from OCI services to destinations inside your VCN.
In this tutorial, we will validate different traffic scenarios and OCI Network Firewall supported key features:
-
North-South Traffic inspection between OCI and NSX Overlay: Secure traffic from OCI Native Compute VM to Oracle Cloud VMware Solution NSX Workload VMs.
-
North-South Traffic inspection between NSX Overlay and Public Internet: Secure traffic from Oracle Cloud VMware Solution NSX workloads to Internet-facing traffic.
-
East-West Traffic inspection within OCI Subnets and VLANs: Secure traffic from OCI Native Comute VM to Oracle Cloud VMware Solution vSphere which is hosted on OCI VLAN.
-
East-West Traffic Inspection within OCI Subnets: Secure traffic from OCI DB VM to Oracle Cloud VMware Solution SDDC ESXi Host which is hosted in a OCI Subnet.
-
Validate Network Firewall security features including Intrusion Prevention, Intrusion Detection, URL Filtering, and SSL Inbound inspection.
Note: You cannot inspect the east-west traffic within NSX workload VMs using the Transit model. If you want to inspect that traffic, it is recommended to deploy 3rd Party Partner solution within the Oracle Cloud VMware Solution environment, which is not covered in this tutorial.
Objective
This tutorial describes OCI Intra-VCN Routing capability with OCI Network Firewall solution in an Oracle Cloud VMware solution environment. We have covered the Virtual Cloud Networking Routing use case which simplifies your Firewall deployment on OCI.
Prerequisites
- A working Intra-VCN Network Topology can be set up as per the topology diagram.
- A working OCI Network Firewall in your Hub VCN:
- You can follow this workshop to get familiar with the OCI Network Firewall solution.
- A working Oracle Cloud VMware Solution SDDC environment deployed in a dedicated VCN, you can follow the Oracle Cloud VMware Solution documentation. For this tutorial, we have deployed a single host SDDC.
- In this tutorial, we have deployed a Linux Bastion VM and a Windows Jump Host VM in respective subnets to depict OCI Native workloads. These can be replaced with any other VMs which can host an application or database.
Note: In a production environment, you must deploy Firewalls in high availability.
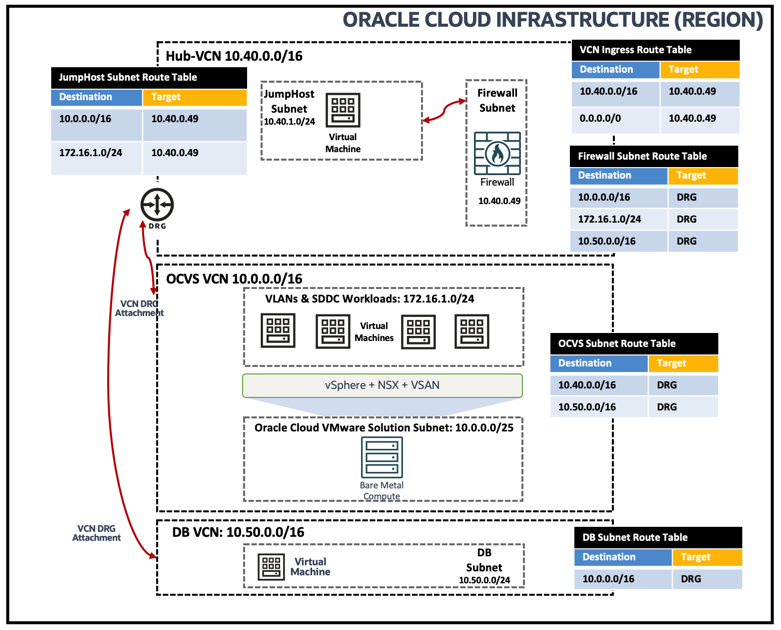
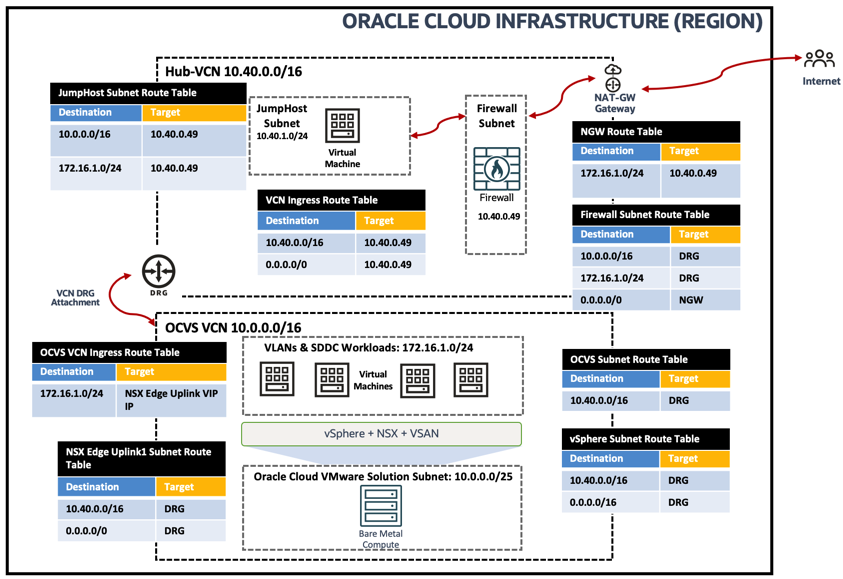
Architecture
You can refer to the following topology to support this use case.
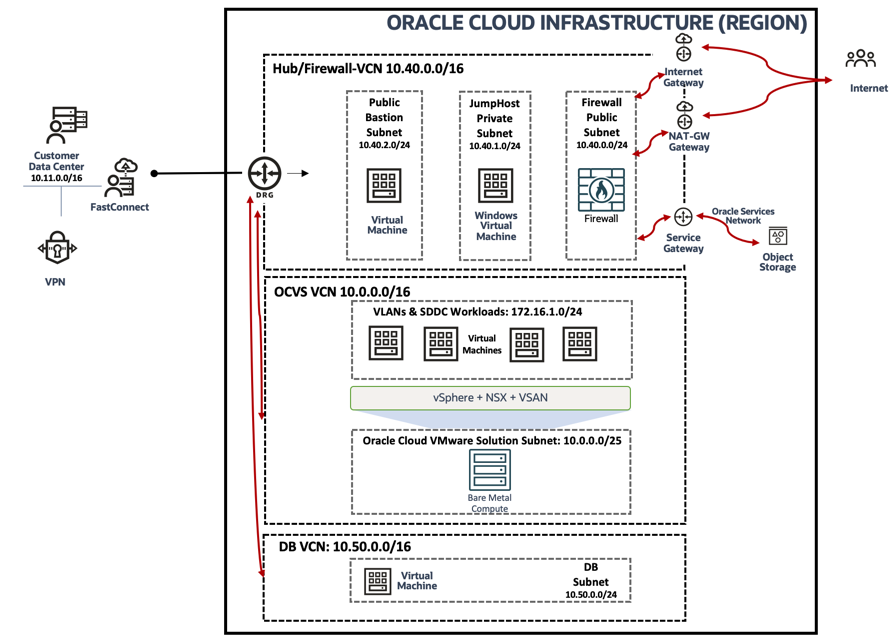
Task 1: Configure OCI Network Firewall
The following sections showcase the minimum required configuration of OCI Network Firewall. For more advanced configurations, refer to the official documentation.
-
VCN Subnets and VLANs: The first step is to make sure you have created required VCNs and subnets as described in the Prerequisites section to support your use case topology.
-
You can verify them using OCI Console by navigating to Virtual Cloud Networks, Virtual Cloud Network Details, Resources.
- Firewall-Subnet-IAD subnet to support Network Firewall in Hub-VCN
- Public-Bastion-Subnet-IAD, JumpHost-Subnet-IAD subnets in Hub-VCN to support VMs for traffic validations
- DB-Subnet-IAD subnet in DB-Spoke-VCN-IAD VCN to support DB workloads
- During the deployment of Oracle Cloud VMware Solution SDDC, appropriate Subnet and VLANs must have been created
-
The following image shows Hub-VCN (Firewall-VCN-IAD) and associated subnets.
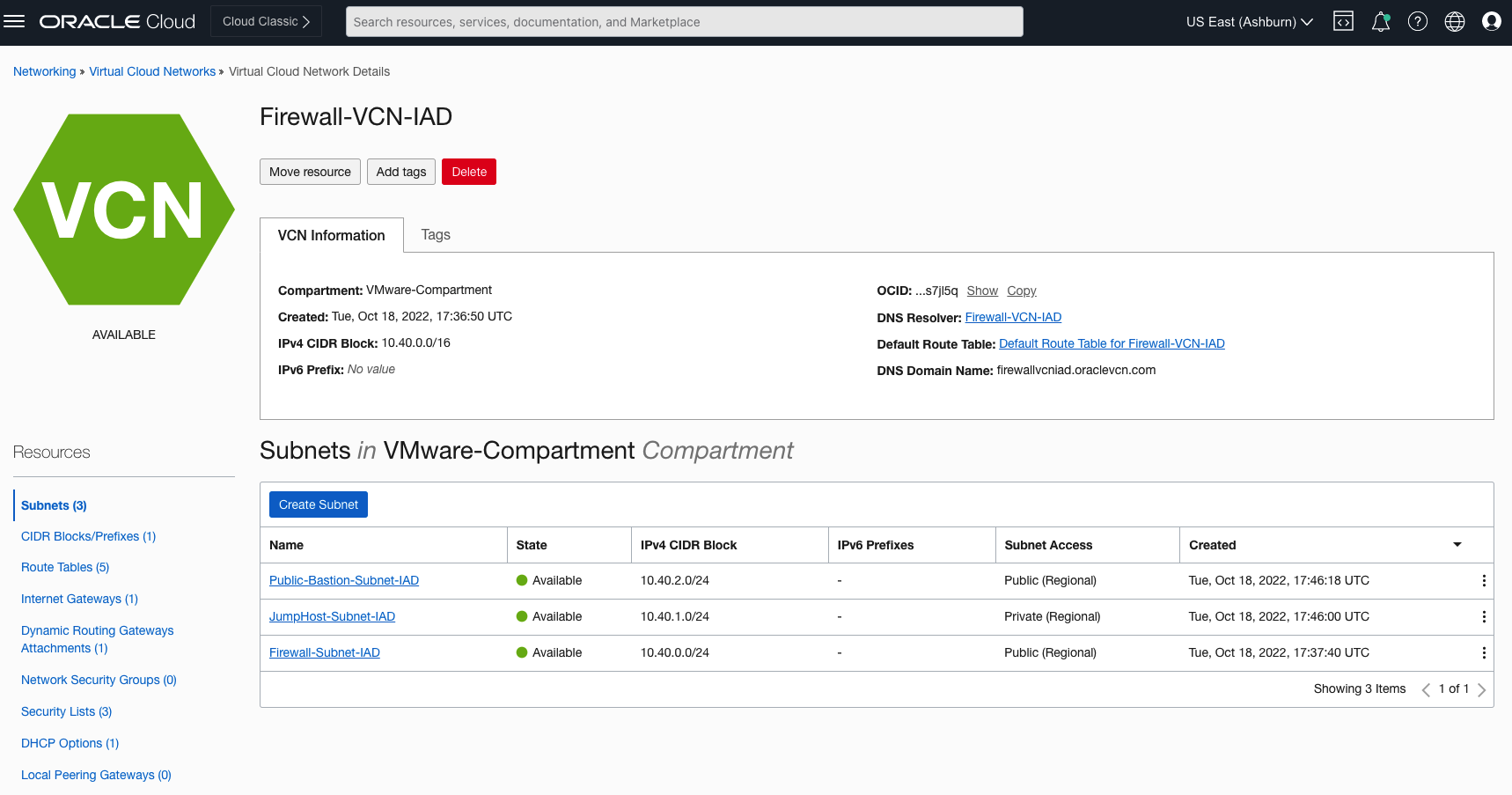
-
Next, you need to deploy OCI Network firewall deployed in firewall-subnet. For more information follow the official documentation.
-
-
OCI Network Firewall Policy Rules: Ensure required firewall security rules are added to support use case traffic. For more information on how to configure rules, follow the official documentation.
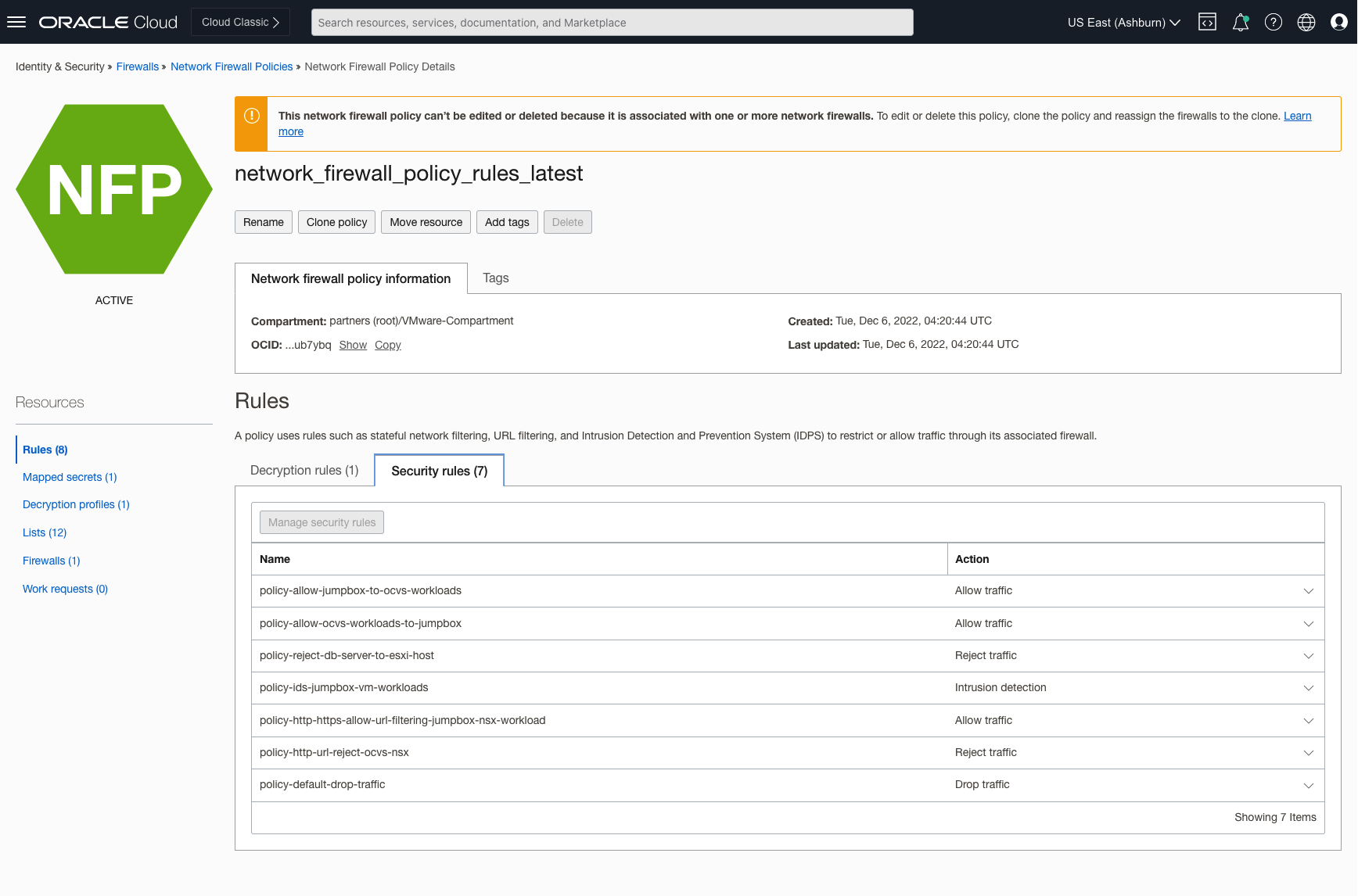
-
OCI Network Firewall: In the Hub-VCN, deploy the Network firewall as per prerequisites. Once your Firewall VM is active, use that to secure your traffic.
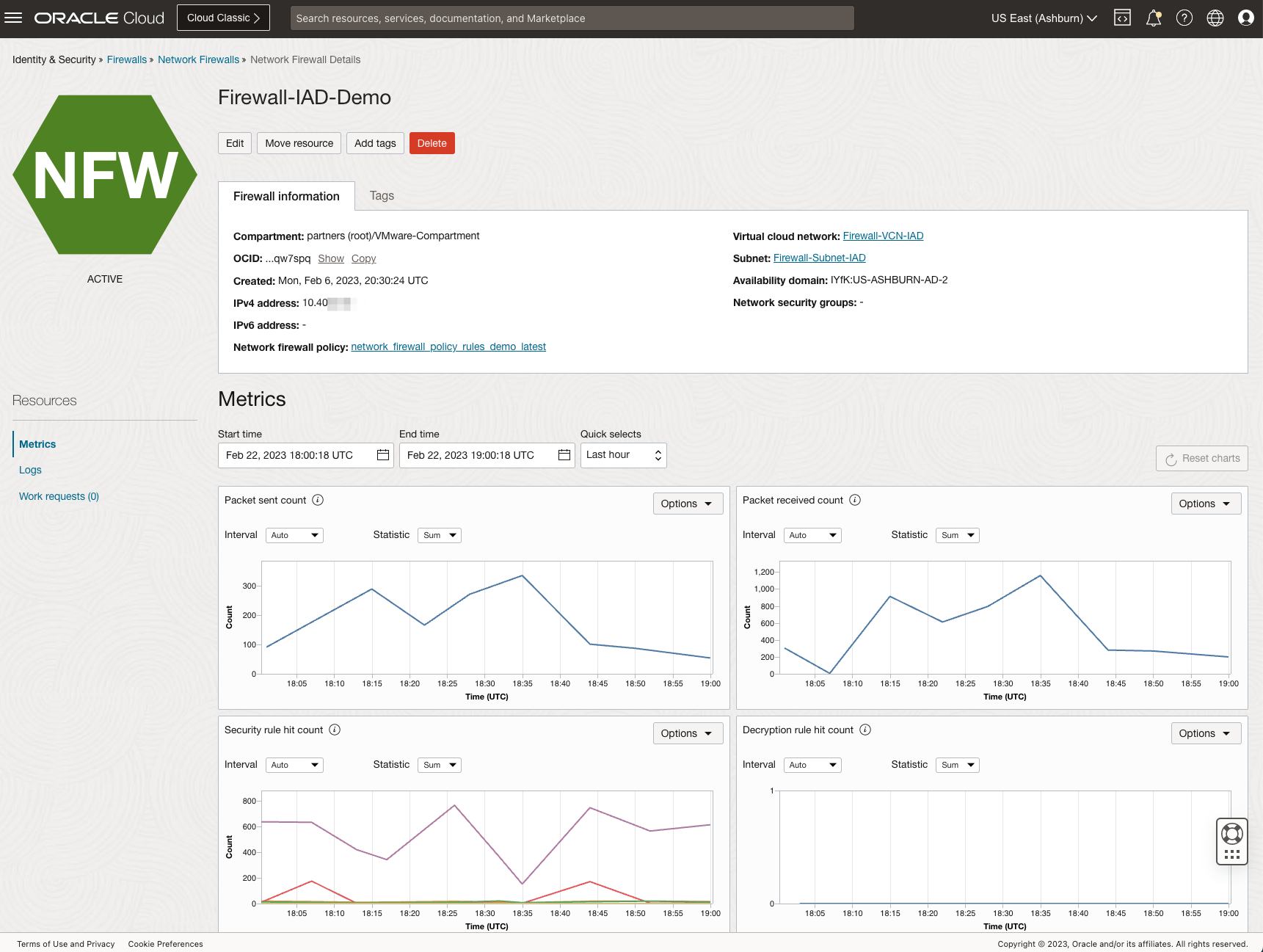
-
Route tables for VCN, Subnets, VLANs and DRG Attachments: You would need to configure the route tables to reflect the correct route rules for the use-case topology. At a high level, you would need to modify the route tables in the VCNs as follows:
-
Firewall-VCN
- Firewall Subnet Route Table: Create entries with each subnet CIDR as the destination and the target as an internet gateway, nat gateway, service gateway, or DRG.
- Public Bastion Subnet Route Table: Create entries with each subnet CIDR as the destination and the target as the network firewall IP address.
- Private JumpHost Subnet Route Table: Create entries with each subnet CIDR as the destination and the target as the network firewall IP address.
- VCN Ingress Route Table: Create entries with each destination CIDRs and the target as firewall IP address to inspect the traffic from Spoke VCNs.
-
Oracle Cloud VMware Solution VCN
- Subnet SDDC Route Table: Create entries with each subnet CIDR as the destination and the target as DRG.
- vSphere VLAN Route Table: Create entries with each subnet CIDR as the destination and the target as DRG.
- NSX Edge Uplink 1 VLAN Route Table: Create entries with each subnet CIDR as the destination and the target as DRG.
- VCN Ingress Route Table: Create entries with each destination Overlays CIDRs and the target as NSX-EDGE-UPLINK IP address to ensure traffic returns to overlay hosts.
-
DB VCN
- DB Subnet Route Table: Create entries with each subnet CIDR as the destination and the target as DRG to inspect traffic via OCI Network Firewall.
-
DRG VCNs Attachment
- Firewall-VCN Attachment Route Table: Create entries with each NSX workload CIDRs as the destination and the next hop as Oracle Cloud VMware Solution VCN attachment. Import Route Distribution with Oracle Cloud VMware Solution and DB VCN matched criteria.
- Oracle Cloud VMware Solution-VCN Attachment Route Table: Create entries with each subnet CIDR as the destination and the target as Firewall-VCN Attachment to inspect traffic via OCI Network Firewall.
- DB Attachment Route Table: Create entries with each subnet CIDR as the destination and the next hop as Firewall-VCN Attachment to inspect traffic via OCI Network Firewall.
-
Note: Ensure that route symmetry is used so traffic is inspected properly in both directions.
Task 2: Validate and inspect traffic from the OCI Network Firewall
At this point, you can validate the traffic from the JumpHost Windows VM, Bastion VM, Oracle Cloud VMware Solution SDDC environment, NSX Overlay VMs, and DB Spoke VM and inspect the traffic from the OCI Network Firewall. The following image shows the required VMs running as per the use case topology.
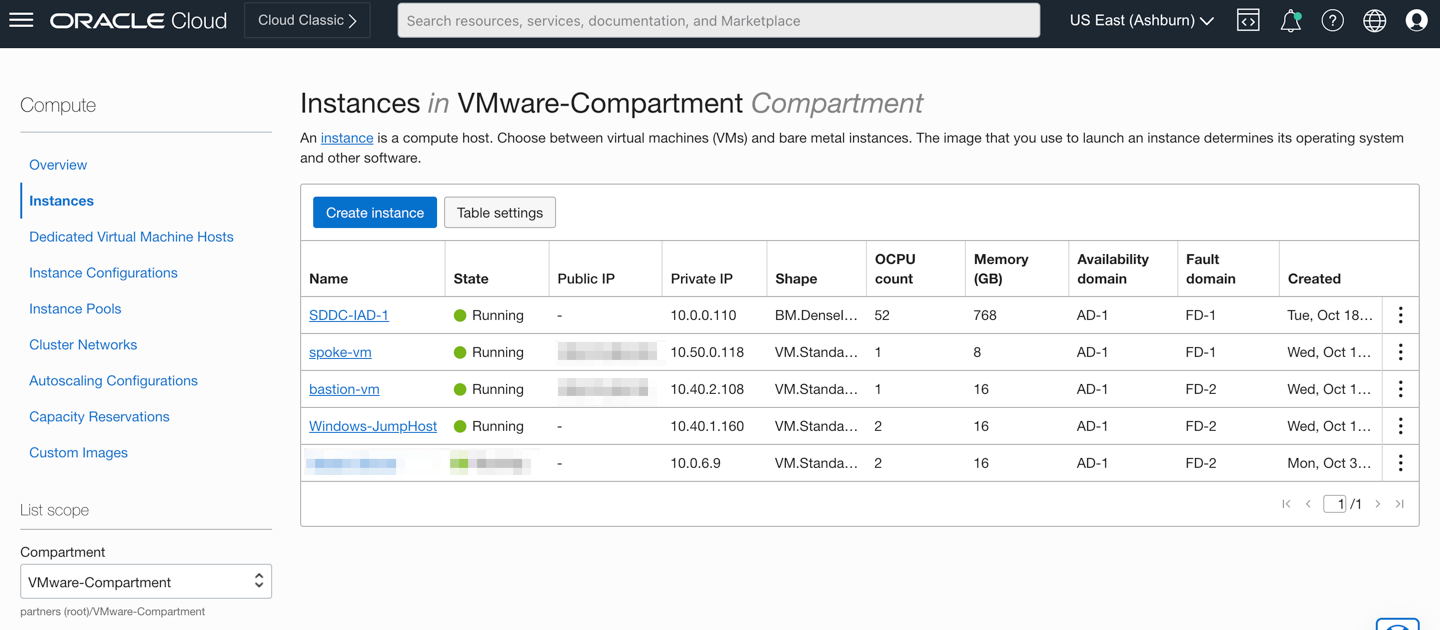
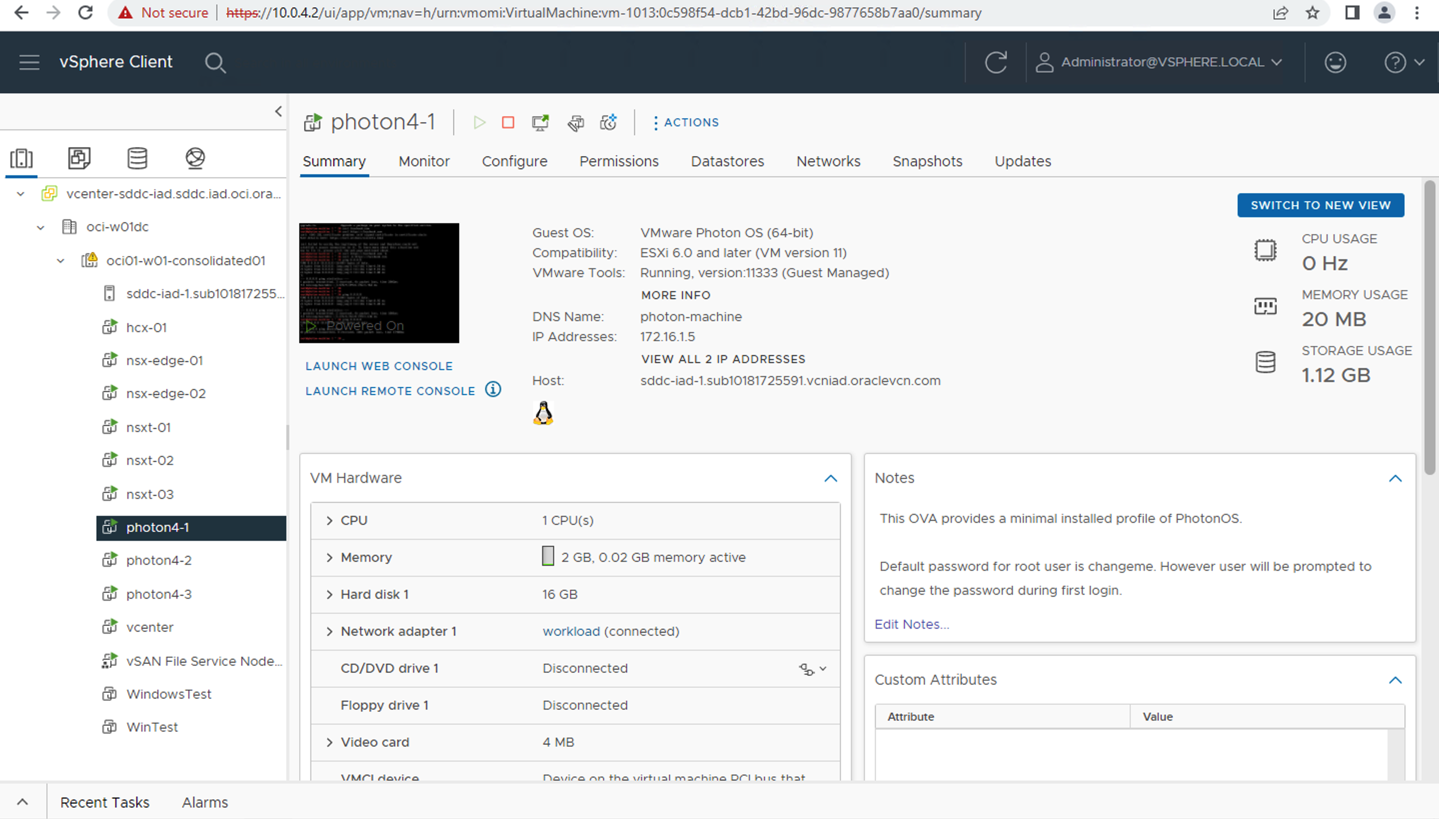
North-South traffic inspection from JumpBox Windows VM to NSX Overlay VMs via Intra-VCN Routing (IVR)
-
IVR routing capabilities allow you to route traffic within VCN and user-defined route to Firewall private IP. The following image shows logical traffic flow and different routing tables associated to ensure JumpHost Windows VM can communicate to Oracle Cloud VMware Solution NSX workload VMs.
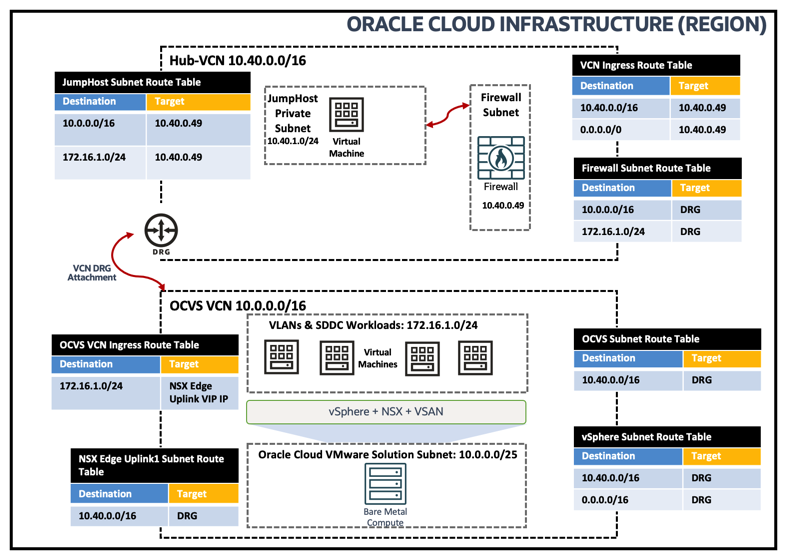
-
You have already pushed the required security rule as below which will ensure traffic gets inspected through Firewall.
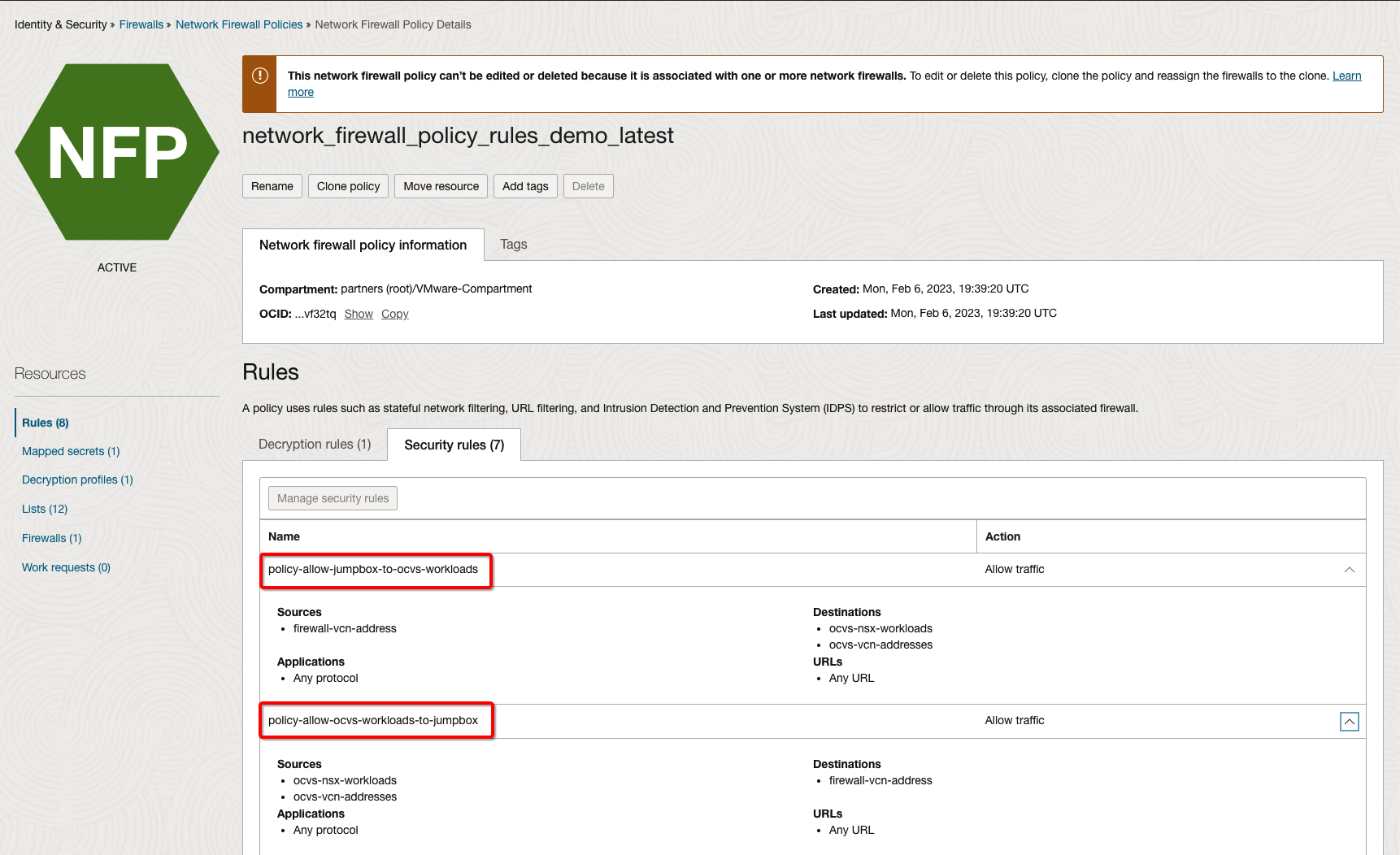
-
You can access the Oracle Cloud VMware Solution Workload VMs (172.16.X.X) from JumpHost Windows VM (10.40.1.160).
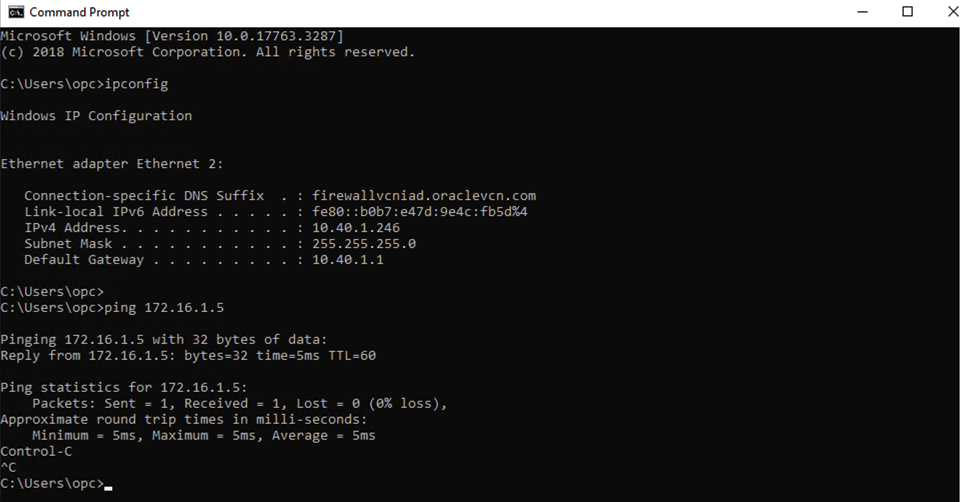
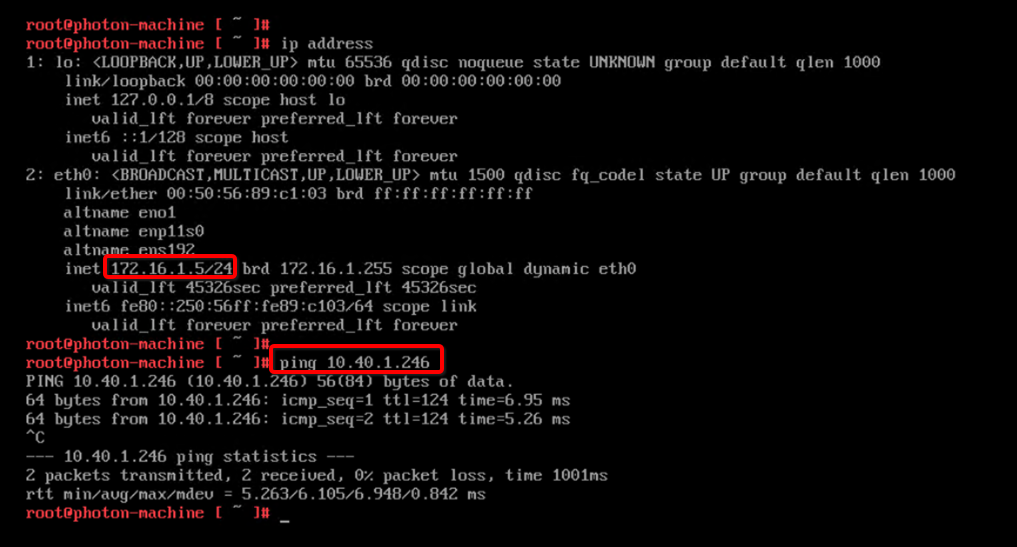
-
The following image shows traffic logs on OCI Network Firewall based on the applied security rules.
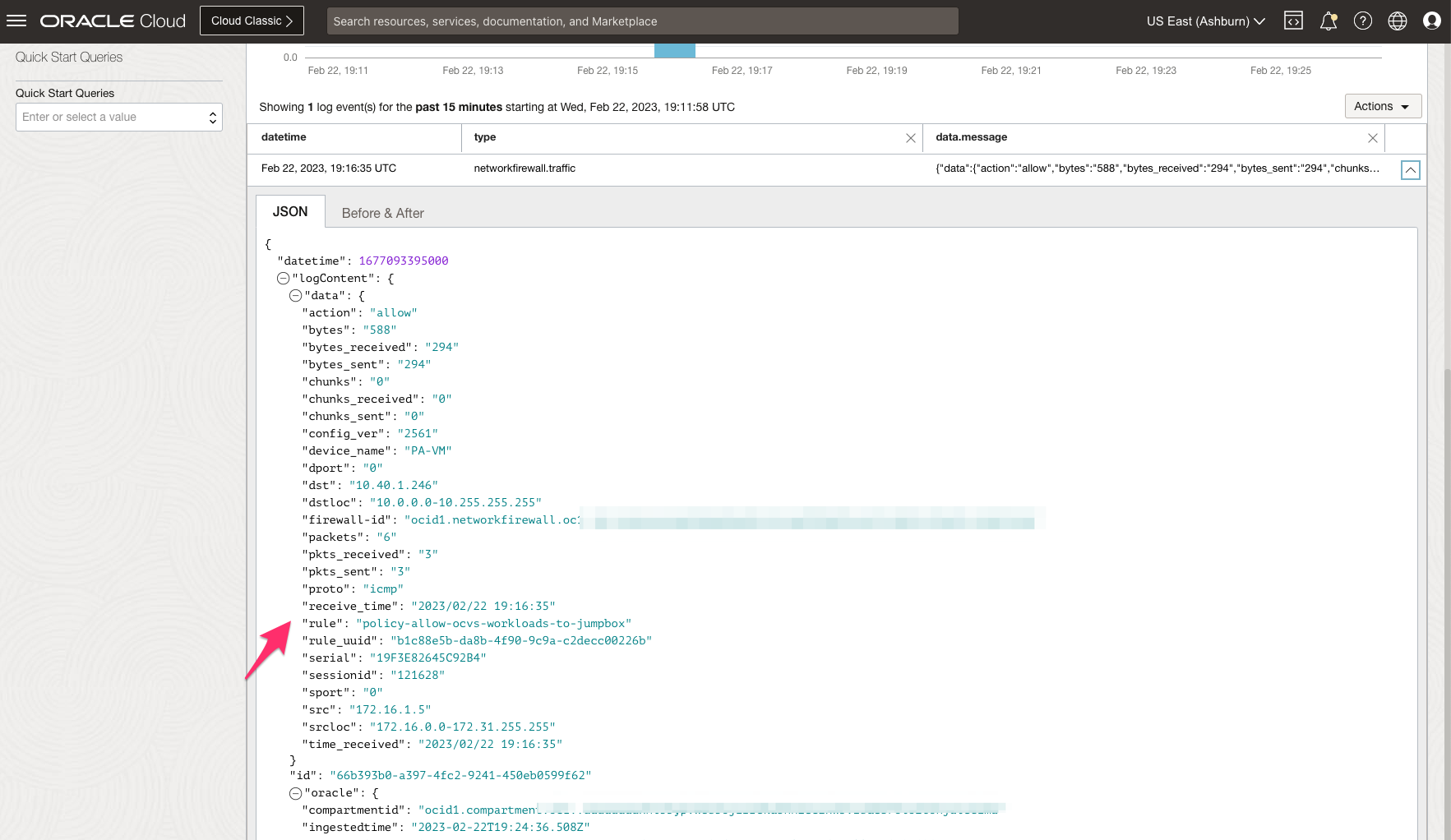
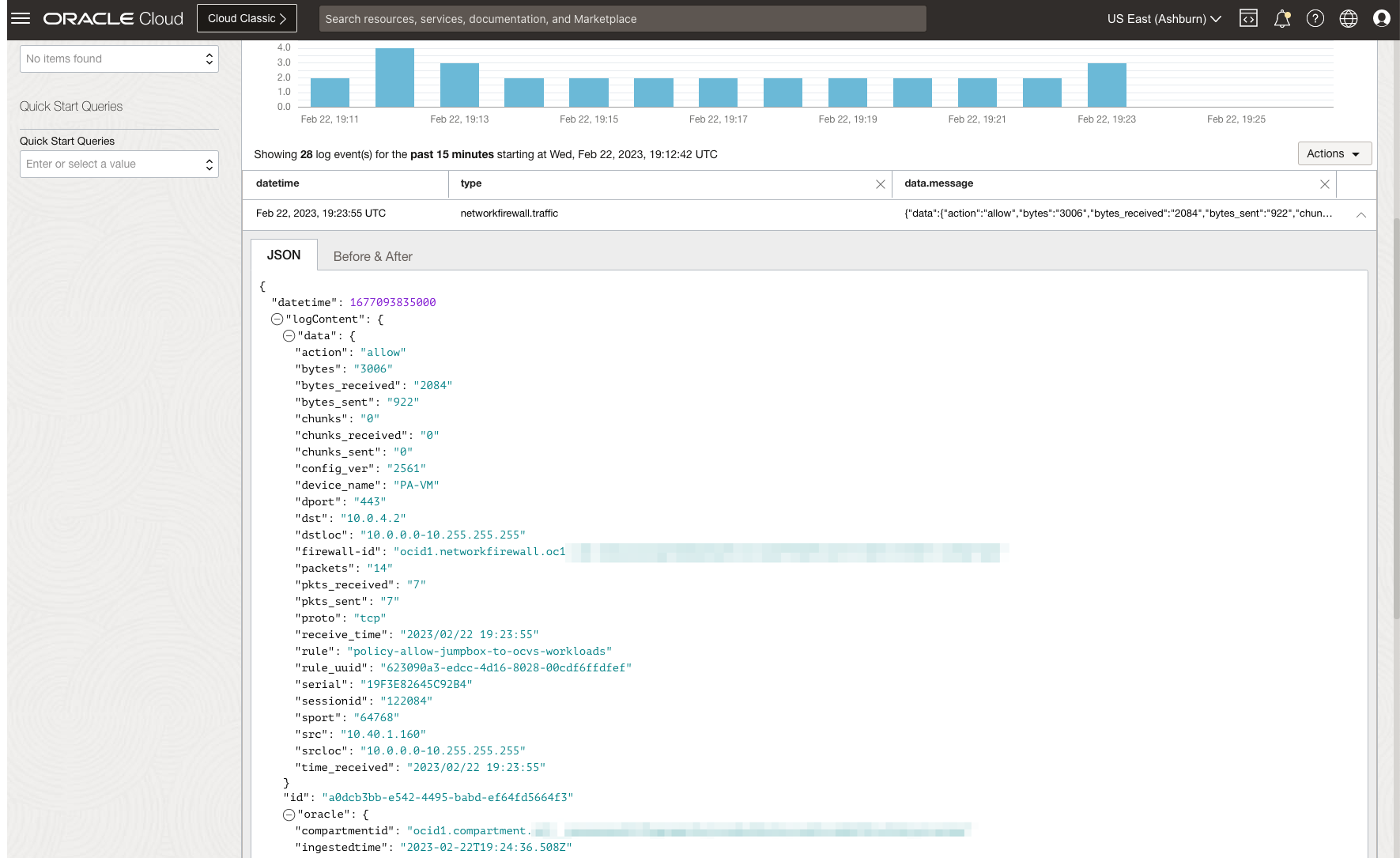
North-South traffic inspection from NSX Overlay VM to the Internet via Network Gateway Ingress Routing
-
The IVR routing and the Network Gateway ingress routing capabilities allow you to route traffic within a VCN and use a user-defined route to a Network Address Translation Gateway. The following image shows the logical traffic flow and the different routing tables used to enable IVR and Network Gateway ingress routings from Oracle Cloud VMware Solution Workload VMs to the Internet via OCI Network Firewall.
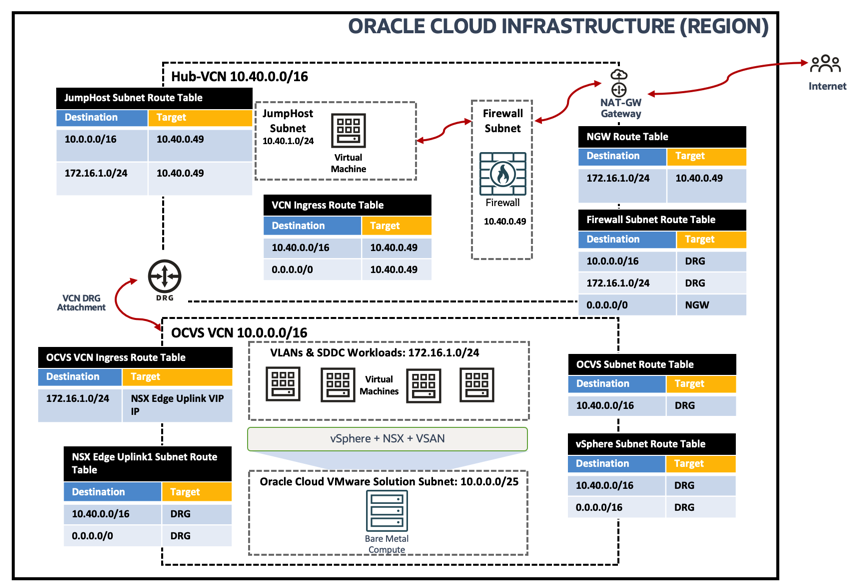
-
You have already pushed the required security rule as below which will ensure traffic gets inspected through Firewall.

-
You can establish connectivity from Oracle Cloud VMware Solution NSX Workload VM (172.16.1.5) to Internet (info.cern.ch).
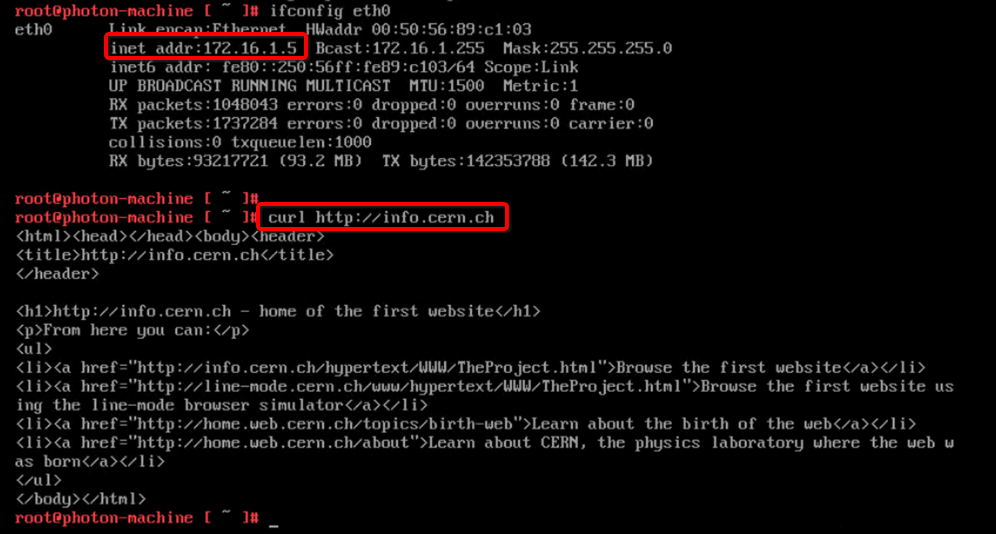
-
The following image shows traffic logs on OCI Network Firewall based on the applied security rules.
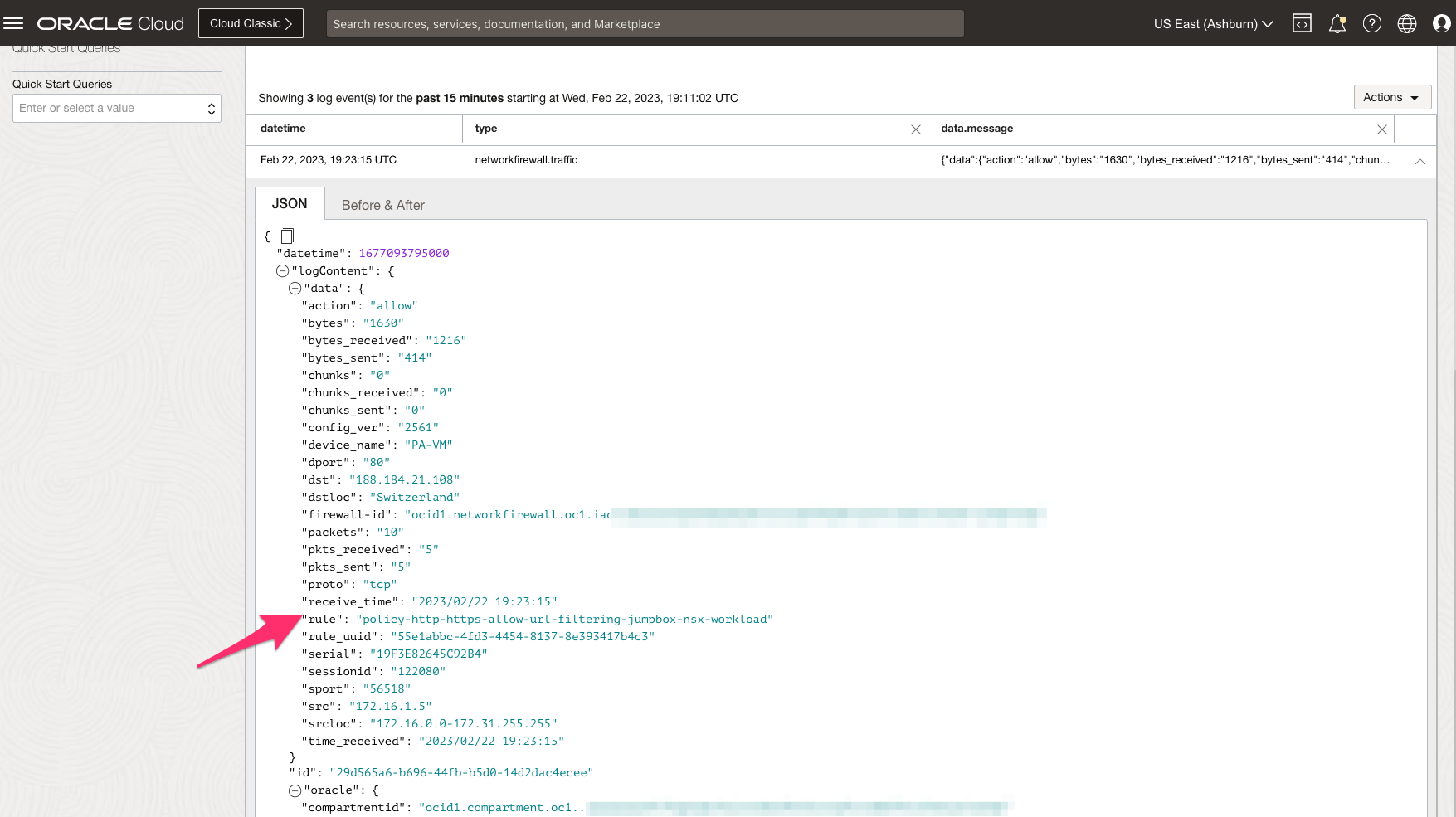
East-West traffic inspection from JumpBox Windows VM to vCenter via Intra-VCN Routing (IVR)
-
IVR routing capabilities allow you to route traffic within VCN and user-defined route to Firewall private IP. The following image shows logical traffic flow and different routing tables associated to ensure JumpHost Windows VM can reach Oracle Cloud VMware Solution vCenter Server:
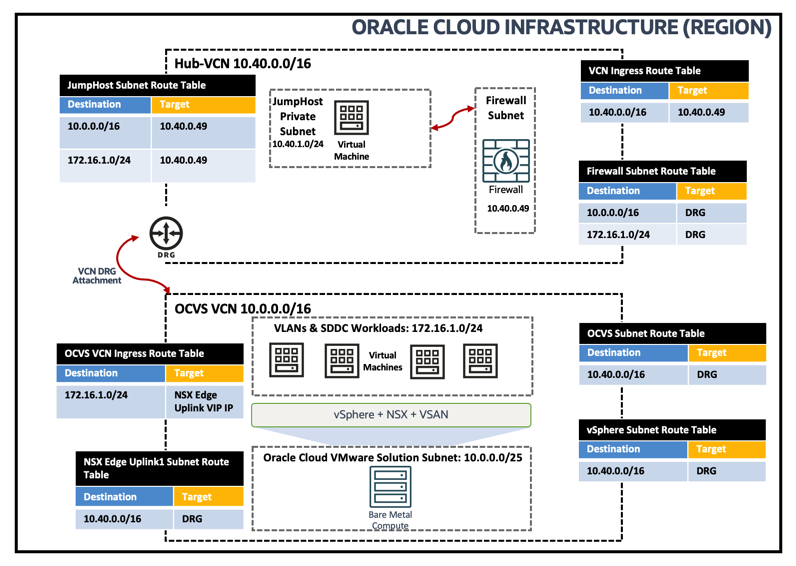
-
You have already pushed the required security rule as below which will ensure traffic gets inspected through Firewall.
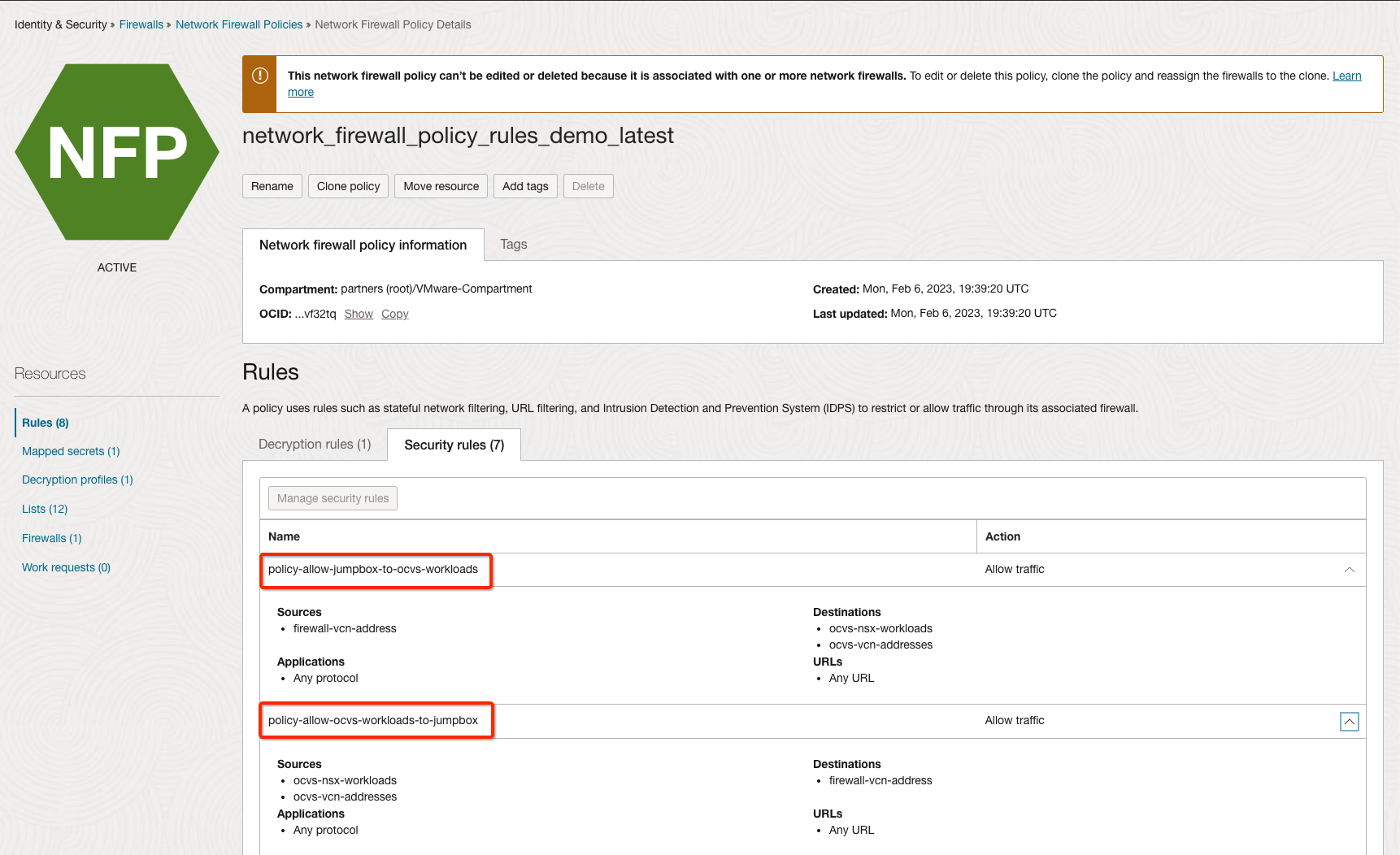
-
You can access the Oracle Cloud VMware Solution vCenter Server (10.0.4.2) from JumpHost Windows VM (10.40.1.160).
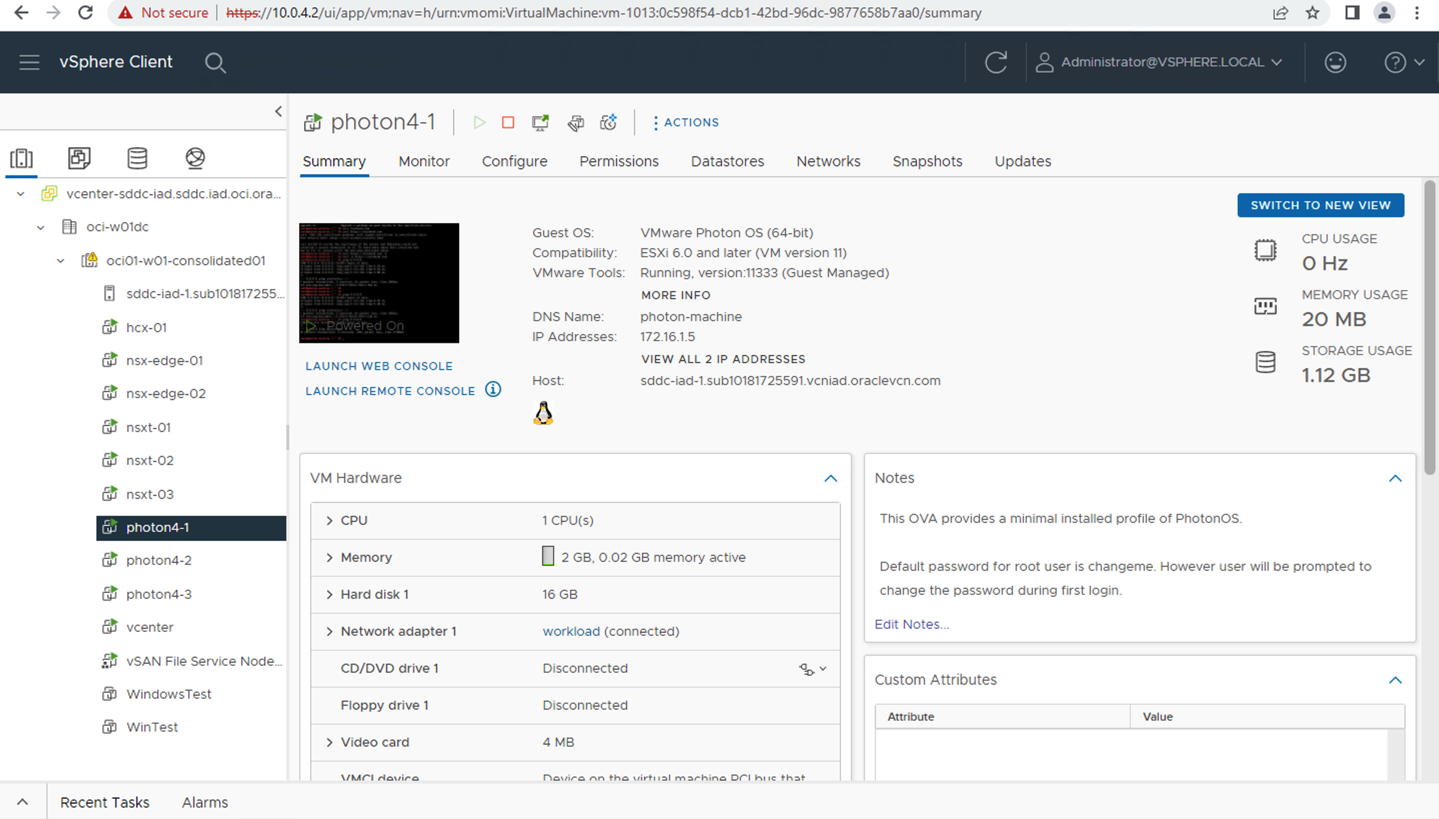
-
The following image shows traffic logs on OCI Network Firewall based on the applied security rules.
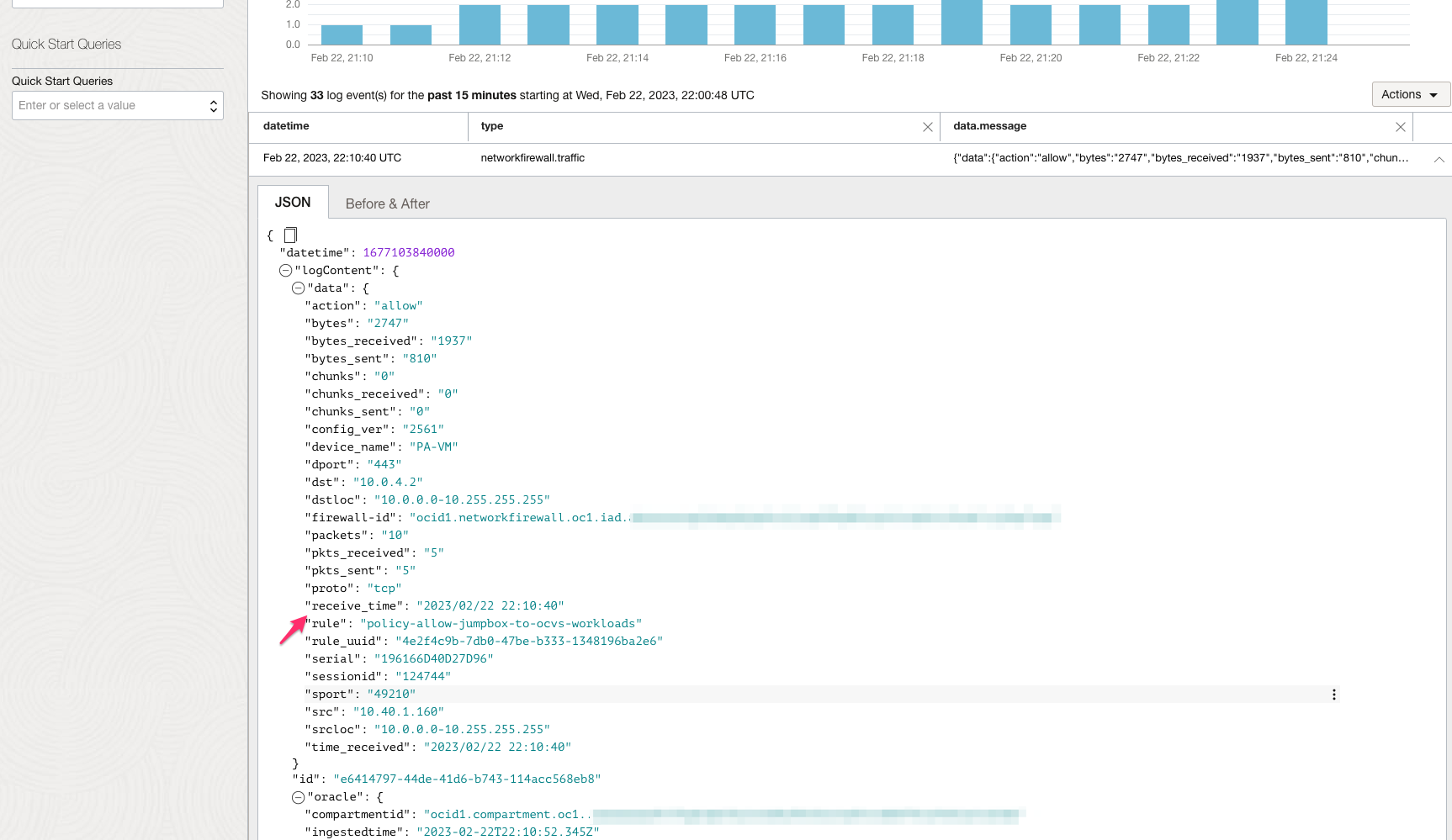
East-West traffic inspection from DB Spoke VM and ESXi Host and vice-versa
-
IVR routing capabilities allow you to route traffic within VCNs and user-defined route to Firewall private IP. The following image shows logical traffic flow and different routing tables associated to ensure Spoke VM traffic to a Oracle Cloud VMware Solution SDDC ESXi host is dropped for security purposes.
-
You have already pushed the required security rule as below which will ensure traffic gets inspected through Firewall.

-
You can access the Oracle Cloud VMware Solution ESXi Host (10.0.0.110) from DB VM (10.50.0.118) and traffic should be rejected based on the applied security rule.
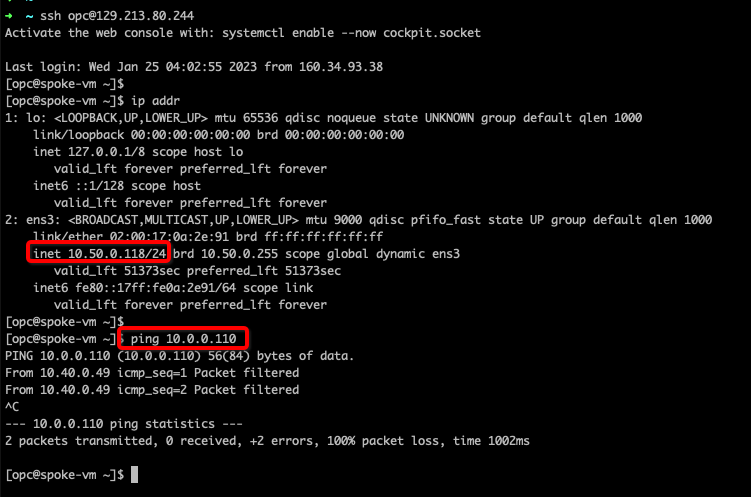
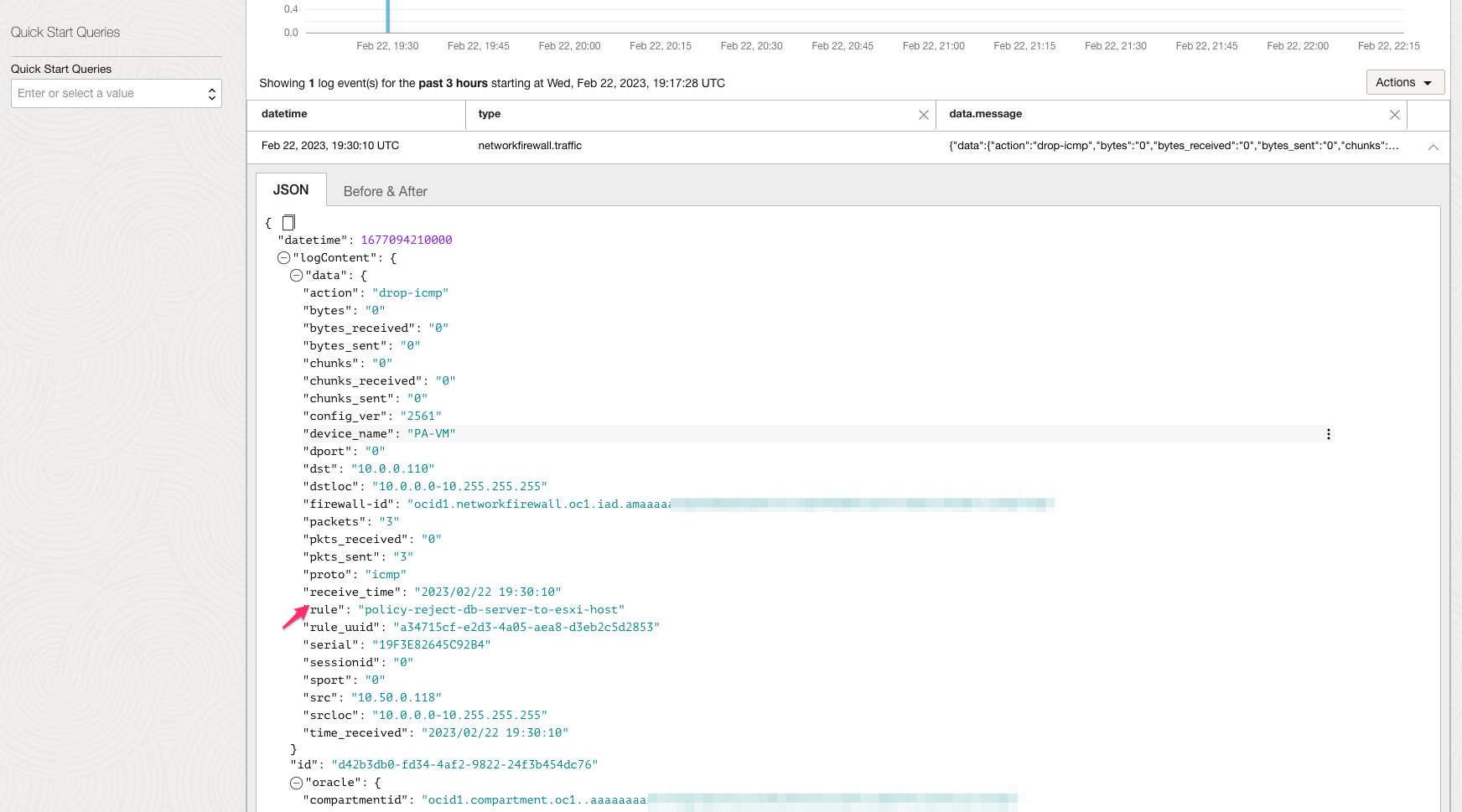
-
The following image shows traffic logs on OCI Network Firewall based on the applied security rule.
IPS/IDS, URL filtering, SSL forward proxy and SSL inbound Inspection Traffic from NSX Overlay VMs to the internet via Inter-VCN Routing
-
Network firewall key features provide you with next-generation firewall capabilities such use Intrusion Prevention, Intrusion Detection, URL Filtering, SSL Inbound Inspection, and more, you can use them in tandem with the Oracle Cloud VMware Solution SDDC environment.
-
The following image shows logical traffic flow and different routing tables associated to ensure NGFW capabilities can be used:
-
To learn more about these capabilities follow official documentation for OCI Network Firewall.
IPS/IDS
-
The following image shows IPS/IDS security rule associated with Firewall. In our case Jumpbox VM will download EICAR malware over HTTPS.

-
You can access the Internet-facing malware via Network Gateway ingress routing from Jumpbox VM. Traffic will flow through the Firewall.
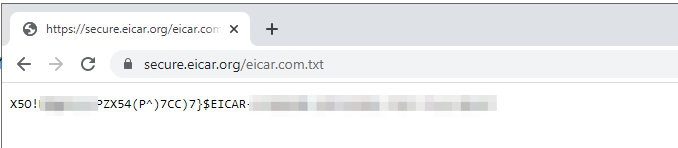
-
The following image shows traffic logs on OCI Network Firewall and an alert should be generated as per IDS action.
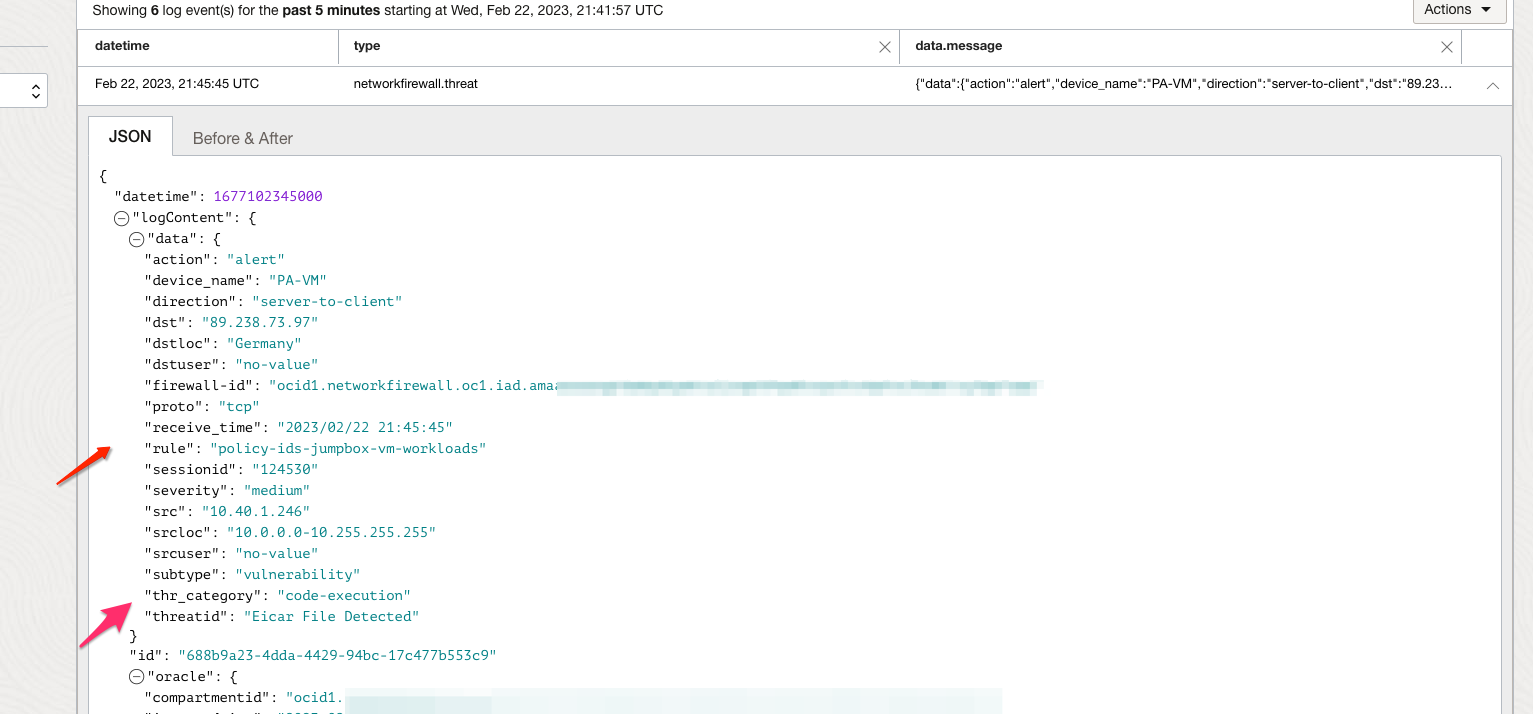
URL Filtering
-
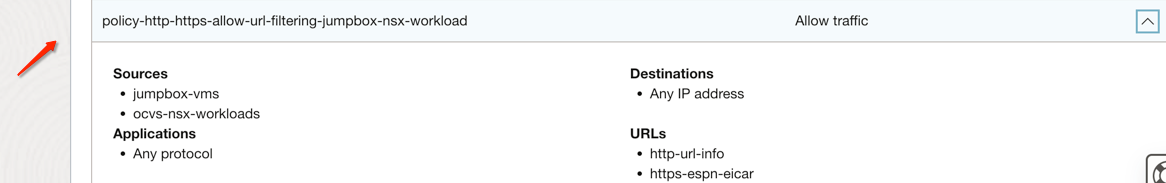
The following image shows URLs filtering security rule on Network Firewall. In our case Oracle Cloud VMware Solution NSX Workload VM accessing certain public URL and that should be rejected.

-
The following image shows traffic logs on OCI Network Firewall and should hit the correct security rule.
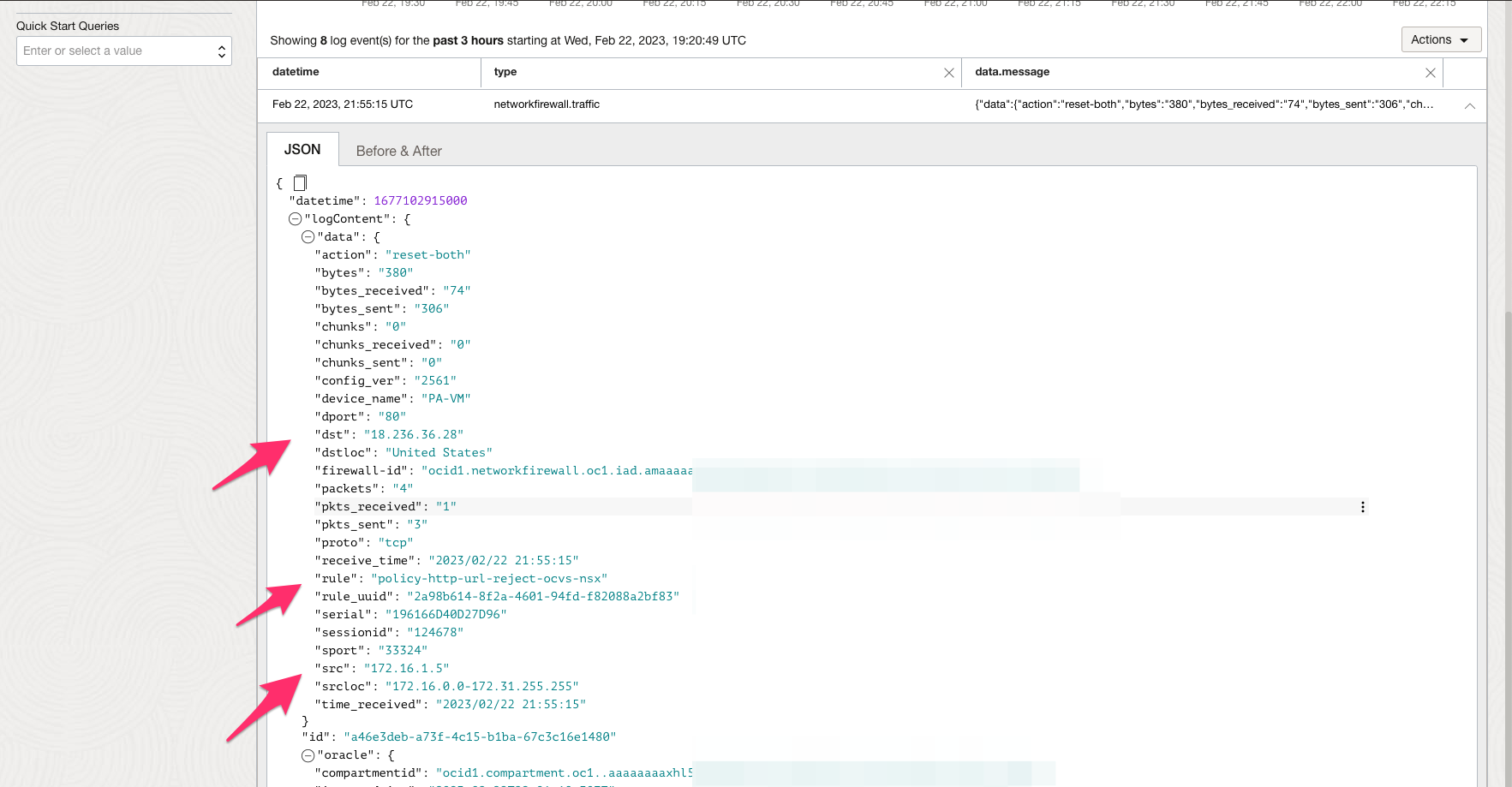
SSL Forward Proxy & SSL Inbound Inspection
-
We have created decryption rule to support SSL/TLS traffic which will ensure HTTPS traffic from Jumpbox VM to Internet is using SSL Forward proxy profile.
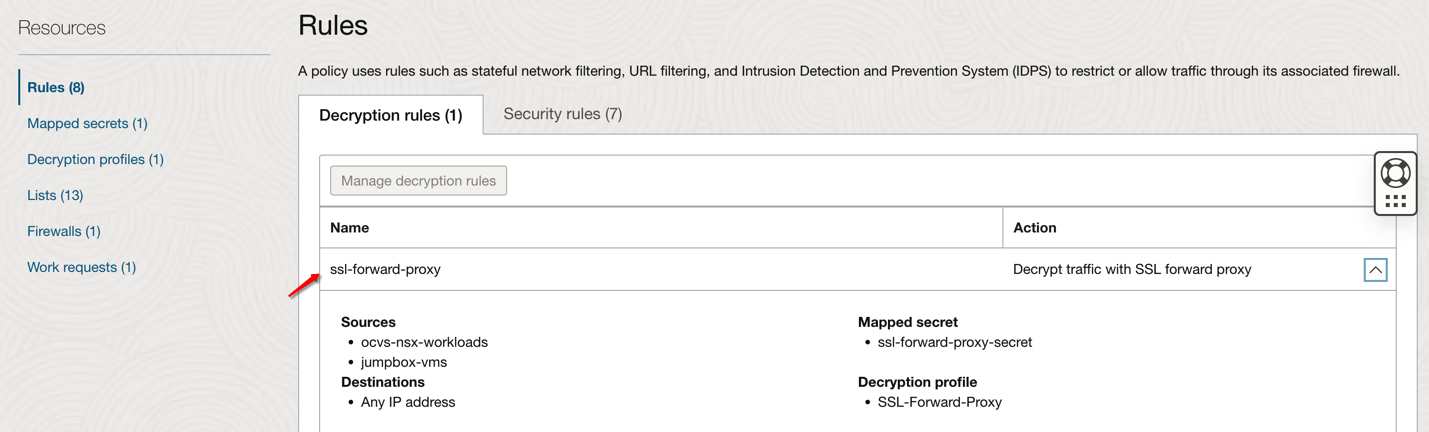
-
You can access the Internet-facing URLs over SSL/HTTPS via NGW from Jumpbox VM. Traffic will flow through the Firewall.
Related Links
- Oracle Cloud Infrastructure
- Overview of Oracle Cloud VMware Solution
- Oracle Cloud Virtual Cloud Network Routing
- Oracle Cloud Infrastructure hub and spoke architecture
- Oracle Cloud Infrastructure transit hub firewall using a DRG
- Oracle Dynamic routing gateway documentation
- OCI Network Firewall
- Overview of OCI Network Firewall
- OCI Network Firewall Workshop
- Defense in Depth, Layering using OCI Network Firewall
Acknowledgements
Authors:
- Arun Poonia (Principal Solutions Architect)
- Praveen Kumar Pedda Vakkalam (Principal Solutions Architect)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Secure your Oracle Cloud VMware Solution workloads with Oracle Cloud Infrastructure Network Firewall
F80966-01
April 2023
Copyright © 2023, Oracle and/or its affiliates.