Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Access OCI OpenSearch Dashboards and REST APIs outside a VCN
Introduction
OpenSearch is a distributed, open-source search and analytics suite used for multiple use cases like real-time application and server monitoring, log analytics, and website search.
OpenSearch also provides a highly scalable system for providing fast access and response to large volumes of data with an integrated visualization tool - OpenSearch Dashboards, that makes it easy for users to explore their data.
By default, OCI OpenSearch Dashboards and APIs can be accessed only within the VCN. To access the OpenSearch Dashboards, end-users need to set up a VM and set up port-forwarding every time to access it. The same applies for APIs too.
Objective
Access OCI OpenSearch Dashboards and REST APIs outside a VCN using NGINX Reverse Proxy Setup.
Prerequisites
- An OCI OpenSearch cluster. For reference, see Creating an OpenSearch cluster.
- Users/Groups with permissions to create an Instance (which will be our Reverse Proxy Server).
Architecture
We are following the Reverse Proxy architecture, where a reverse proxy server accepts a request from a client, forwards it to a server that can fulfill it, and returns the server’s response to the client. Here we are using NGINX, a free, open-source, high-performance HTTP server and reverse proxy server as shown in the following architecture diagram.

Task 1: Verify the OpenSearch cluster
Once the OpenSearch cluster has been created successfully, you will see the cluster details as shown in the following image.

-
From the Cluster details page, copy the following values, which will be used in the setup.
- API endpoint
- OpenSearch Dashboard API endpoint
Also, note down the Username and Password which were provided while creating the cluster.
Task 2: Set up the reverse proxy server
-
Set up a Compute Instance (In this tutorial, we are using VM.Standard.E4.Flex based on Oracle Linux 8) in the same subnet that you have created for OpenSearch. You can also create it in another subnet, VCN or region if network connectivity is set up. The instance should be accessible from the Internet.
-
Once the VM is created, open the following ports in Security Lists for the required IPs and Firewall (in the VM).
- 443 - For Dashboard
- 80 - For Verification
- 9200 - For APIs
- 22 - For SSH Access (Added by default)

-
Log in to the VM and use the following commands to allow ports 80, 443 and 9200 from the VM Firewall.
sudo firewall-cmd --zone=public --add-port=443/tcp --permanent sudo firewall-cmd --zone=public --add-port=80/tcp --permanent sudo firewall-cmd --zone=public --add-port=9200/tcp --permanent sudo firewall-cmd --reload
Task 3: Set up NGINX
-
Install NGINX Reverse Proxy and Start in the VM, using the following command.
sudo yum install nginx -y -
Enable and start the NGINX Service.
sudo systemctl enable nginx && sudo systemctl start nginx -
By default, Oracle Linux comes with SELinux Enabled. In order allow NGINX to access the Internet, we need to provide access.
sudo setsebool -P httpd_can_network_connect on -
Enable access to ports 9200 and 443.
sudo semanage port -a -t http_port_t -p tcp 443 sudo semanage port -a -t http_port_t -p tcp 9200- If you get
ValueError: Port tcp/9200, already defined, use the following command.
sudo semanage port -m -t http_port_t -p tcp 443 sudo semanage port -m -t http_port_t -p tcp 9200 - If you get
Task 4: Enable HTTPS access
To set up the OpenSearch Dashboard and APIs with HTTPS enabled, we must use an SSL certificate provided by a certificate authority.
-
Create an SSL key pair using the following OpenSSL command. This command generates the key-pair under
/etc/nginxdirectory.sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/nginx/cert.key -out /etc/nginx/cert.crt
Task 5: Configure NGINX Reverse Proxy Server
We will use the following NGINX configuration for Reverse proxy setup.
user root;
worker_processes auto;
error_log /var/log/nginx/error.log;
pid /var/run/nginx.pid;
include /usr/share/nginx/modules/*.conf;
events
{
worker_connections 1024;
}
http
{
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /var/log/nginx/access.log main;
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
include /etc/nginx/mime.types;
default_type application/octet-stream;
include /etc/nginx/conf.d/*.conf;
server
{
listen 443;
server_name $host;
rewrite ^/$ https://$host/app/home redirect;
#OpenSearch Dashboard API endpoint without HTTPS in the front
set $domain_endpoint <OpenSearch Dashboard API endpoint>:5601;
ssl_certificate /etc/nginx/cert.crt;
ssl_certificate_key /etc/nginx/cert.key;
ssl on;
ssl_session_cache builtin:1000 shared:SSL:10m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4;
ssl_prefer_server_ciphers on;
location / {
proxy_pass https://<OpenSearch Dashboard API endpoint>:5601;
}
location /app/login {
proxy_http_version 1.1;
proxy_set_header Connection "Keep-Alive";
proxy_set_header Proxy-Connection "Keep-Alive";
proxy_set_header Authorization "";
proxy_set_header Authorization $http_authorization;
proxy_pass_header Authorization;
# Forward requests to Dashboards
proxy_pass https://$domain_endpoint/app/login;
# Handle redirects to Dashboards
proxy_redirect https://$domain_endpoint/app/login https://$host/app/login;
# Update cookie domain and path
proxy_cookie_domain $domain_endpoint $host;
proxy_cookie_path ~*^/$ /app/login/;
# Response buffer settings
proxy_buffer_size 128k;
proxy_buffers 4 256k;
proxy_busy_buffers_size 256k;
}
}
server
{
listen 9200;
server_name $host;
ssl_certificate /etc/nginx/cert.crt;
ssl_certificate_key /etc/nginx/cert.key;
ssl on;
ssl_session_cache builtin:1000 shared:SSL:10m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4;
ssl_prefer_server_ciphers on;
location / {
proxy_pass https://<API endpoint>:9200;
}
}
}
Variables Used in the Config:
OpenSearch Dashboard API endpoint: OpenSearch Dashboard API endpoint obtained from the Cluster details page.API endpoint: API endpoint obtained from the Cluster details page.
-
Take a backup of the
/etc/nginx/nginx.conffile. -
After replacing the variables with actual values, save the config in
/etc/nginx/nginx.confand restart the NGINX server.sudo systemctl restart nginx
Task 6: Verify the access
Now, we should be able to access both the OpenSearch Dashboard and Ingest APIs (with Credentials provided while creating the OpenSearch Cluster) using the Public IP of the Instance.
Dashboard Access
Password Prompt

Dashboard
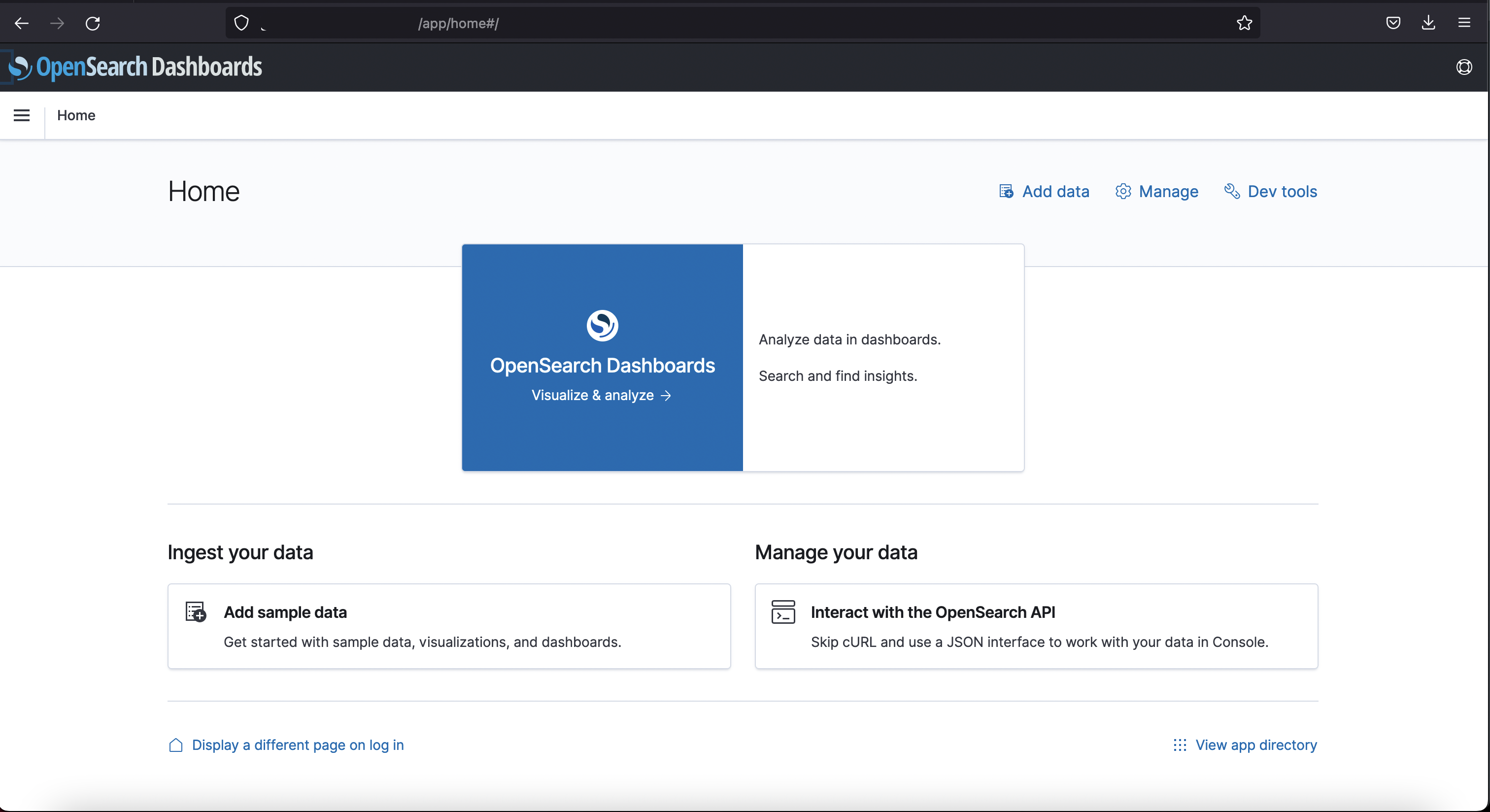
REST API Access
We should use same credentials when using OpenSearch API.
API Success

API Failure

Related Links
Acknowledgments
Author - Rithesh Subramanian (OCI Cloud Architect)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Access OCI OpenSearch Dashboards and REST APIs outside a VCN
F74482-02
June 2023
Copyright © 2023, Oracle and/or its affiliates.