Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Integrate Oracle Cloud Infrastructure Resource Manager with Automation Process
Introduction
The Oracle Cloud Infrastructure (OCI) Resource Manager service automates the deployment and operations of all OCI resources. Using the infrastructure-as-code (IaC) model, the service is based on Terraform, an open source industry standard that allows DevOps engineers to develop and deploy their infrastructure anywhere.
A Terraform configuration encodes your infrastructure in declarative configuration files. The OCI Resource Manager service allows you to share and manage infrastructure configuration and state files across multiple teams and platforms.
Through the OCI Resource Manager it is possible to execute Terraform scripts in the OCI Console. It is also possible to make a REST call or use the Oracle Cloud Infrastructure Command Line Interface (OCI CLI), thus expanding the possibilities of integration with automation tools such as OCI Devops, Jenkins, GitHub and so on.

In this tutorial, we will automate the deployment of an Oracle Autonomous Database instance by obtaining the database admin password securely through OCI Vault secrets without exposing it in the files, so that the OCI Resource Manager execution user has proper access to create the database and stored password.
Objectives
- Configure the automation through Terraform so that you can create instances with their appropriate access credentials but without exposing any sensitive information such as password must be stored so that only authorized users can use it within the Terraform script.
Prerequisites
-
A user inside an user group without any policy. This user will be given the appropriate permissions to run Terraform in OCI Resource Manager.
-
OCI Object Storage bucket in a specific compartment (if you want to generate the Terraform script into this bucket).
-
The Terraform script will be executed through the OCI Resource Manager and the user must have permissions to:
- Create resources in the compartment.
- Create an Oracle Autonomous Database instance.
- Read an OCI Vault password.
- Execute Terraform script.
Task 1: Create a Secret for Oracle Autonomous Database in OCI Vault
We will create a password in OCI Vault to illustrate how to configure a new resource in Terraform without exposing sensitive data.
Secrets are credentials such as passwords, certificates, SSH keys, or authentication tokens that you use with OCI services. Storing secrets in an OCI Vault provides greater security than you might achieve storing them elsewhere, such as in code or configuration files. You can retrieve secrets from the OCI Vault service when you need them to access resources or other services.
You can create secrets by using the OCI Console, OCI CLI, or API. Secret contents for a secret are imported to the service from an external source. The OCI Vault service stores secrets in vaults.
Note: For this task, we need to log in as an Admin user in the OCI Console. You must have permission to create a password in OCI Vault.
-
Log in to the OCI Console, click Identity & Security and Vault.

-
Select the compartment where you want to store the secrets and click Create Vault.

-
Enter a name for your vault, confirm the compartment and click Create Vault.

-
Confirm that the vault is created and create a key. Click Master Encryption Keys and Create Key.

-
Confirm the compartment and enter a name for your key. For example, enter
autonomouskeyas Name and click Create Key.
Confirm that the key is created.

-
Click Secrets and Create Secret.

-
We will create the Autonomous Admin password. Enter the following information and click Create Secret.
- Compartment: Select compartment.
- Name: Enter name for your first secret.
- Select Manual secret generation to include the password.
- Secret Type Template: Enter
Plain-Text. - Secret Contents: Enter your password.

-
You will need the Secret OCID. To copy the OCID, click Copy.

Task 2: Create Policies for the OCI user
In this tutorial, consider your username TestUser included in a group named TestGroup. Now, create a policy with name TestPolicy.
This task is important because this controls all privileges needed to guarantee the security of Terraform automation.
Note: For this task, we need to log in with an Admin user in OCI.
-
Go to the OCI Console, click Identity & Security and Policies.

-
Click Create Policy.

-
In the Statements section, enter the following policies.
-
These policies give the permission to group
TestGroupcreated previously to manage a stack and jobs in OCI Resource Manager.- Allow group 'Default'/'TestGroup' to manage orm-stacks in compartment integration - Allow group 'Default'/'TestGroup' to manage orm-jobs in compartment integration - Allow group 'Default'/'TestGroup' to read orm-config-source-providers in tenancy -
This policy gives the right to create an Oracle Autonomous Database instance in the compartment integration.
- Allow group 'Default'/'TestGroup' to manage autonomous-database in compartment integration -
The group can read the password stored in OCI Vault through Terraform scripts.
- Allow group 'Default'/'TestGroup' to use secret-family in tenancy -
This policy gives the right to save the Terraform scripts on a specific compartment.
- Allow group 'Default'/'TestGroup' to manage all-resources in compartment kubernetes -
This policy allows the users of
TestGroupto edit code in the OCI Code Editor.- Allow group 'Default'/'TestGroup' to use cloud-shell in tenancy

-
Task 3: Create a Stack from a Template
Create a stack for an Oracle Autonomous Database instance. We can use a template for this. The first step is log in as the user created in Task 2.
-
Go to the OCI Console and click the hamburger menu.

-
Click Developer Services and Stacks.

-
Select your Compartment and click Create stack.
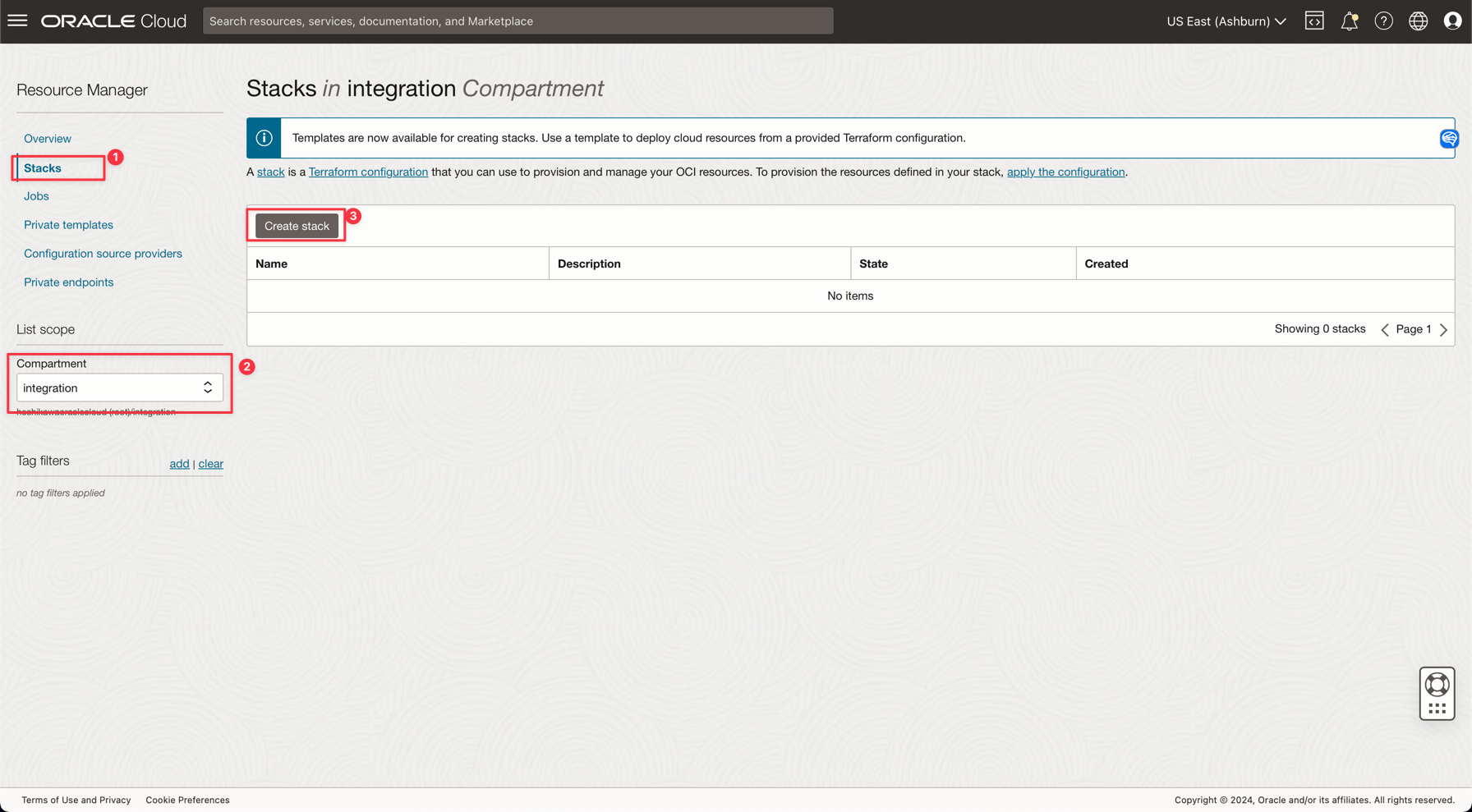
-
In the Stack information page, select Template and click Select template to generate a Terraform script for Oracle Autonomous Database.

-
In the Service tab, select Autonomous Transaction Processing Database and click Select template.

-
You can generate the Terraform scripts and store in the OCI Object Storage bucket. Select Use custom Terraform providers, enter the bucket Compartment and Name, and save your stack.

Your stack is saved.

-
This template does not read the secret stored in your OCI Vault. To make the Terraform to read the secret, we need to change the code.
Click Edit and select Edit Terraform configuration in code editor.

-
You can edit the code. The default code generates a random string for the password.
-
main.tffile.

You need to add a new data named
oci_secrets_secretbundleand assign it to the following attributes:admin_passwordatautonomous_data_warehouseandautonomous_databasesections.passwordatautonomous_database_walletsection.
-
main.tf-autonomous_data_warehousesection.data "oci_secrets_secretbundle" "bundle" { secret_id = var.secret_ocid } admin_password = base64decode(data.oci_secrets_secretbundle.bundle.secret_bundle_content.0.content)
-
main.tf-autonomous_databasesection.
-
main.tf-autonomous_database_walletsection.

Add the following code in the
variables.tffile and replace the OCID for your secret generated in Task 1.variable "secret_ocid" { default = "ocid1.vaultsecret.oc1.iad.xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx" }-
variables.tffile.
Note: Save your files. Move the mouse cursor over your stack (on the right side of the editor, in Autonomous Transaction Processing…. title), right-click and save your project. If you leave without saving, the execution assumes you will use the random string in the original code script.
-
Task 4: Test the Permissions
You can test the policies and see how you have control of the OCI Resource Manager, OCI Vault and Oracle Autonomous Database instances in a specific compartment.
-
Log in to the OCI Console with your Admin user credentials and remove all the policies for the
TestGroupgroup in theTestPolicypolicy. Click Delete and confirm.
-
Now, log in with your user in the
TestGroupgroup and you cannot see the stack, so you cannot execute it.
-
Add the following statements with the Admin user.
Allow group 'Default'/'TestGroup' to manage orm-stacks in compartment integration Allow group 'Default'/'TestGroup' to manage orm-jobs in compartment integration Allow group 'Default'/'TestGroup' to read orm-config-source-providers in tenancy Allow group 'Default'/'TestGroup' to manage all-resources in compartment kubernetes
The following statements grant your user in
TestGrouppermissions to use the OCI Resource Manager stack.
-
We removed the grant for your user to create an Oracle Autonomous Database instance and read the secret in OCI Vault. So you can execute your stack but with no success. To test, click apply in your stack detail page.


-
Add Oracle Autonomous Database and OCI Vault permissions on the
TestPolicy.Allow group 'Default'/'TestGroup' to manage all-resources in compartment kubernetes Allow group 'Default'/'TestGroup' to manage autonomous-database in compartment integration
-
Click apply in your stack detail page and you can see you have the control for all resources without exposing any password.

Task 5: Call your OCI Resource Manager Automation with REST
All the resources in OCI have an OCI REST API or an OCI CLI command to call services as is executed in your OCI Console.
For more information about OCI REST API, see OCI REST API. You can see the list of OCI CLI commands here: Oracle Cloud Infrastructure CLI Command Reference.
Now, we can choose to execute the OCI Resource Manager stack with an OCI REST API or an OCI CLI command. To create a Job, see CreateJob or you can use the following sample code curl-oci.zip with curl-oci.sh prepared with OCI parameters.

You need to create the signature for your REST requests. For more information, see Oracle Cloud Infrastructure (OCI) REST call walkthrough with curl.
-
Create a file named
STACK-RUN.sh. This will be your REST request using acurl-oci.sh(this tool will prepare your authorization string with your OCI information).
-
Create a file named
request.jsonwith your stack ID and compartment ID.
-
Open the
curl-oci.shfile and change the following parameters. These parameters are the same as your OCI CLI installation.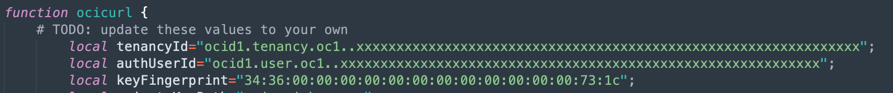
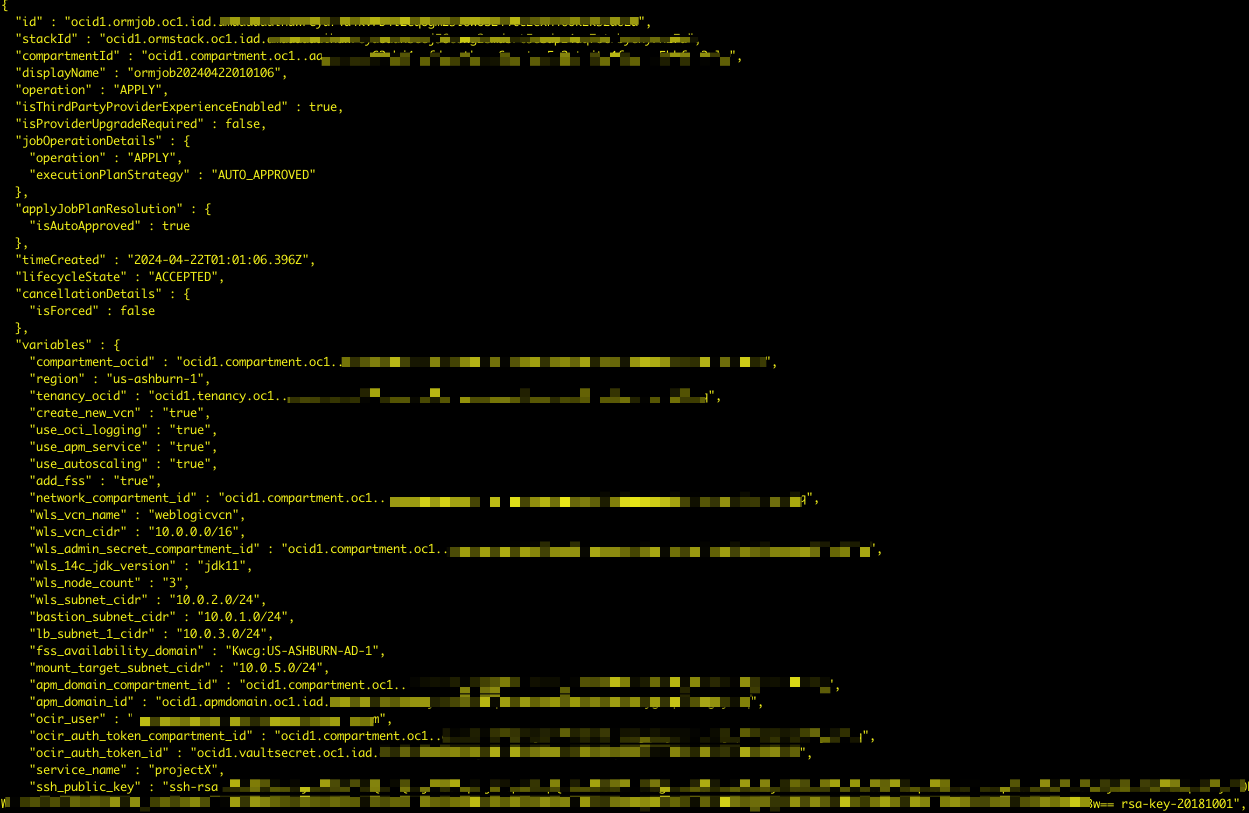
Now, execute the script.

You can see the success results.
Related Links
Acknowledgments
- Author - Cristiano Hoshikawa (Oracle LAD A-Team Solution Engineer)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Integrate Oracle Cloud Infrastructure Resource Manager with Automation Process
F98144-01
May 2024