Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Create redundancy for Asymmetric Keys in Oracle Cloud Infrastructure Virtual Vaults
Introduction
In today’s fast-paced digital world, data security is of utmost importance. As organizations increasingly rely on cloud-based infrastructure, ensuring the confidentiality of sensitive information becomes paramount. To achieve this, they often use encryption, which requires secure key management. However, key management can pose significant challenges, particularly when it comes to redundancy and availability. In this blog post, we’ll explore how you can achieve redundancy for Asymmetric keys in virtual vaults and how applications in two different regions can leverage this for encryption and decryption.
Oracle Cloud Infrastructure (OCI) offers Virtual Private Vault (VPV), a fully managed key management service that enables you to centrally manage keys used for data encryption, decryption, and signing. One of the most critical features of VPV is cross-region backup and restore. With this feature, you can backup and restore keys across regions, making them available for use in a region different from where they were created.
It’s worth noting that backup and restore only works for VPV, not for Virtual Vault (VV), another key management service offered by OCI. Moreover, there’s no way to backup Hardware Security Module (HSM) keys in Virtual Vault. However, with the Bring Your Own Key (BYOK)/import key option, you can import the same key material in two different regions’ vaults, and even if a region is entirely down, the copy in another region will serve as a backup. This redundancy ensures that your keys are always available, even if a region experiences an outage or disaster. It also enables you to meet regulatory and compliance requirements that mandate key redundancy and disaster recovery.
Objective
This tutorial walks you through the high-level steps for importing the same RSA key into virtual vaults located in two different regions. The key import will be performed in one region using a step-by-step procedure, while a script will be utilized in the other region for the import. After importing the key, we will encrypt test data using the key in one region, and then decrypt the resulting ciphertext using the same key in the vault located in the other region.
Prerequisites
An OCI account with access to create and manage Vaults and Keys.
Note: For the “Bring your own key (BYOK)” scenario, you must patch the OpenSSL. To patch OpenSSL, privileged access is required to execute the necessary shell commands. It is recommended to execute the shell commands in a Linux box with privileged access. OCI CLI commands can be executed either in the cloud shell or in a Linux box where OCI CLI is installed and configured. Follow this procedure to install and configure OCI CLI on a Linux box.
Task 1: Import key into a vault in the first region (example:Phoenix)
Follow this procedure for importing an Asymmetric Key (RSA) into a Virtual Vault.
-
Patch the OpenSSL: For the “Bring your own key(BYOK)” scenario, you must patch the OpenSSL for
RSA_OAEP_AES_SHA256wrapping. Follow this procedure to patch the OpenSSL. -
Generate the key material: Use key material that is generated by a tool or source based on your requirements. In this tutorial, we are using OpenSSL to generate the key material.
$HOME/local/bin/openssl.sh genrsa -out PRIVATEKEY.pem 2048 -
Get the Public RSA Wrapping Key.
oci kms management wrapping-key get --endpoint <control_plane_URL>oci kms management wrapping-key get --endpoint https://abcdefghijk-management.kms.us-phoenix-1.oraclecloud.com --raw-output --query 'data."public-key"' > VAULT_PUBLIC_WRAPPING_KEY.pem -
Apply RSA-OAEP with AES to wrap key material using the CLI interface.
a. Generate a temporary AES key.
openssl rand -out <temporary_AES_key_path> 32$HOME/local/bin/openssl.sh rand -out TEMP_AES_KEY.key 32b. Wrap the temporary AES key with the public wrapping key using RSA-OAEP with SHA-256.
openssl pkeyutl -encrypt -in <temporary_AES_key_path> -inkey <vault_public_wrapping_key_path> -pubin -out <wrapped_temporary_AES_key_file> -pkeyopt rsa_padding_mode:oaep -pkeyopt rsa_oaep_md:sha256$HOME/local/bin/openssl.sh pkeyutl -encrypt -in TEMP_AES_KEY.key -inkey VAULT_PUBLIC_WRAPPING_KEY.pem -pubin -out WRAPPED_TEMP_AES_KEY.bin -pkeyopt rsa_padding_mode:oaep -pkeyopt rsa_oaep_md:sha256c. Generate hexadecimal of the temporary AES key material.
temporary_AES_key_hexdump=$(hexdump -v -e '/1 "%02x"' < temporary_AES_key_path)TEMPORARY_AES_KEY_HEXDUMP=$(hexdump -v -e '/1 "%02x"' < TEMP_AES_KEY.key)d. If the RSA private key you want to import is in PEM format, convert it to DER.
${OpenSSL_path} pkcs8 -topk8 -nocrypt -inform PEM -outform DER -in <your_pem_RSA_private_key_path> -out <your_RSA_private_key_file>$HOME/local/bin/openssl.sh pkcs8 -topk8 -nocrypt -inform PEM -outform DER -in PRIVATEKEY.pem -out TARGET_KEY.keye. Wrap your RSA private key with the temporary AES key.
openssl enc -id-aes256-wrap-pad -iv A65959A6 -K temporary_AES_key_hexdump -in <your_RSA_private_key_file> -out <wrapped_target_key_file>$HOME/local/bin/openssl.sh enc -id-aes256-wrap-pad -iv A65959A6 -K $TEMPORARY_AES_KEY_HEXDUMP -in TARGET_KEY.key -out WRAPPED_TARGET_KEY.binf. Create the wrapped key material by concatenating both wrapped keys.
cat <wrapped_temporary_AES_key_file> <wrapped_target_key_file> > <wrapped_key_material_file>cat WRAPPED_TEMP_AES_KEY.bin WRAPPED_TARGET_KEY.bin > WRAPPED_KEY_MATERIAL.bing. Apply base64 encoding on the wrapped key material and then import it to create a key via CLI.
base64 WRAPPED_KEY_MATERIAL.bin -w 0 > WRAPPED_KEY_MATERIAL.base64 -
Import Key Material as an External Key using OCI CLI.
oci kms management key import --wrapped-import-key <wrapped_key_material> --compartment-id <compartment_id> --display-name <key_name> --endpoint <control_plane_URL> --key-shape <key_encryption_information> --protection-mode <key_protection_mode>echo "{ \"wrappingAlgorithm\": \"RSA_OAEP_AES_SHA256\", \"keyMaterial\": \"$(cat WRAPPED_KEY_MATERIAL.base64)\" }" > WRAPPED_IMPORT_KEY.jsonecho "{ \"algorithm\": \"RSA\", \"length\": \"256\" }" > KEY_SHAPE.jsonoci kms management key import --wrapped-import-key file://WRAPPED_IMPORT_KEY.json --compartment-id ocid1.compartment.oc1..aaaaaaaabbbbbbbbbccccccccdddddddeeeeeefffff --display-name IMPORTEDKEY --endpoint https://abcdefghijk-management.kms.us-phoenix-1.oraclecloud.com --key-shape file://KEY_SHAPE.json --protection-mode SOFTWARE
Task 2: Import the same key into a virtual vault in the second region (example: Ashburn)
-
Use the following script for importing an Asymmetric Key (RSA) into a Virtual Vault.
-
Open a command prompt and then run the following script, replacing example file names and values as appropriate.
#!/bin/bash #This script is for demonstration purposes only. It provides #a functioning set of calls to show how to import RSA keys #into the OCI Vault service. set -e; #set -x; #OPENSSL_PATH="<path to patched openssl.sh>" #PRIVATE_KEY="<path to target private key which needs to be imported>" #KEY_SIZE="<key size in bytes>" #DISPLAY_NAME="<Display Name>" #VAULT_KEYMANAGEMENT_ENDPOINT="<Vault Management Endpoint>" #COMPARTMENT_ID="<Compartment OCID>" #Sample OPENSSL_PATH="$HOME/local/bin/openssl.sh" PRIVATE_KEY="$HOME/local/bin/PRIVATEKEY.pem" KEY_SIZE="256" DISPLAY_NAME="IMPORTEDKEY" VAULT_KEYMANAGEMENT_ENDPOINT="https://abceefghijk-management.kms.us-ashburn-1.oraclecloud.com" COMPARTMENT_ID="ocid1.compartment.oc1..aaaaaaaabbbbbbccccccccdddddddeeeeeeeffffffff" WORK_DIR=$(mktemp -d -t kms_XXXX) BASE64="base64" echo "Openssl Path: ${OPENSSL_PATH}" echo "Work Dir: ${WORK_DIR}" #Getting Vault Public RSA Wrapping Key oci kms management wrapping-key get --endpoint ${VAULT_KEYMANAGEMENT_ENDPOINT} --raw-output --query 'data."public-key"' > ${WORK_DIR}/vault_public_wrapping_key.pem WRAPPING_KEY="${WORK_DIR}/vault_public_wrapping_key.pem" #Convert the private key to PKCS8 DER format. target_key_path=${WORK_DIR}/target_key.key ${OPENSSL_PATH} pkcs8 -topk8 -nocrypt -inform PEM -outform DER -in ${PRIVATE_KEY} -out ${target_key_path} #Generate a temporary AES key. temp_aes_key_path=${WORK_DIR}/temp_aes_key.key ${OPENSSL_PATH} rand -out ${temp_aes_key_path} 32 #Wrap the temporary AES key by using RSA-OAEP with SHA-256. wrapped_temp_aes_key=${WORK_DIR}/wrapped_temp_aes_key.bin ${OPENSSL_PATH} pkeyutl -encrypt -in ${temp_aes_key_path} -inkey ${WRAPPING_KEY} -pubin -out ${wrapped_temp_aes_key} -pkeyopt rsa_padding_mode:oaep -pkeyopt rsa_oaep_md:sha256 #Wrap the target RSA key. wrapped_target_key=${WORK_DIR}/wrapped_target_key.bin temp_aes_key_hexdump=$(hexdump -v -e '/1 "%02x"' < ${temp_aes_key_path}) ${OPENSSL_PATH} enc -id-aes256-wrap-pad -iv A65959A6 -K ${temp_aes_key_hexdump} -in ${target_key_path} -out ${wrapped_target_key} #Create the wrapped key material. wrapped_key_material_bin=${WORK_DIR}/wrapped_key_material.bin cat ${wrapped_temp_aes_key} ${wrapped_target_key} > ${wrapped_key_material_bin} echo "Binary wrapped key for console is available at: ${wrapped_key_material_bin}" #Import the wrapped key to the Vault service after base64 encoding the payload. wrapped_key_material_base64=${WORK_DIR}/wrapped_key_material.base64 ${BASE64} ${wrapped_key_material_bin} -w 0 > ${wrapped_key_material_base64} echo "Base64 encoded wrapped key for CLI or API is available at: ${wrapped_key_material_base64}" #####1. IMPORT NEW KEY USING CONSOLE ##### #browse and upload ${WORK_DIR}/wrapped_key_material.bin file in key import section on console. #####2. IMPORT NEW KEY USING OCI_CLI ##### key_material=$(${BASE64} ${wrapped_key_material_bin}) echo "{ \"wrappingAlgorithm\": \"RSA_OAEP_AES_SHA256\", \"keyMaterial\": \"$(cat ${wrapped_key_material_base64})\" }" > wrapped_import_key.json echo "{ \"algorithm\": \"RSA\", \"length\": ${KEY_SIZE} }" > key_shape.json oci kms management key import --wrapped-import-key file://wrapped_import_key.json --compartment-id ${COMPARTMENT_ID} --display-name ${DISPLAY_NAME} --endpoint ${VAULT_KEYMANAGEMENT_ENDPOINT} --key-shape file://key_shape.json --protection-mode SOFTWARE
Task 3: Encrypt and Decrypt your Data
Now that you have a key created in your vault, you can use it to encrypt and decrypt your data.
-
Obtain the key ID for the key you created. You can find the key ID by clicking on your key in the vault, then looking for the “Key ID” field in the key details pane.
-
You can use the keys to encrypt and decrypt your data. Plaintext included in the example request is a base64-encoded value of a UTF-8 string.
-
Plaintext: OCI is a security-first public cloud infrastructure
-
Base64: T0NJIGlzIGEgc2VjdXJpdHktZmlyc3QgcHVibGljIGNsb3VkIGluZnJhc3RydWN0dXJl
-
-
Encrypt using RSA Key present in the vault for first region.
oci kms crypto encrypt --key-id <key_ocid> --plaintext <plaintext Base64 Encoded> --encryption-algorithm <Encryption Algorithm> --endpoint <Vault Crypto Endpoint>-
To encrypt using RSA key encryption-algorithm is mandatory parameter and the accepted values are RSA_OAEP_SHA_1, RSA_OAEP_SHA_256
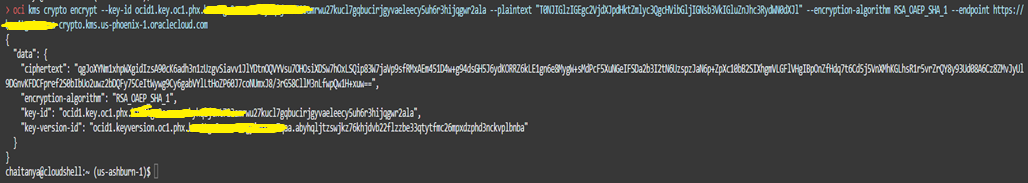
-
-
Decrypt using RSA Key present in the vault for second region.
oci kms crypto decrypt --key-id <key_ocid> --ciphertext <cipher text> --encryption-algorithm <Encryption Algorithm> --endpoint <Vault Crypto Endpoint>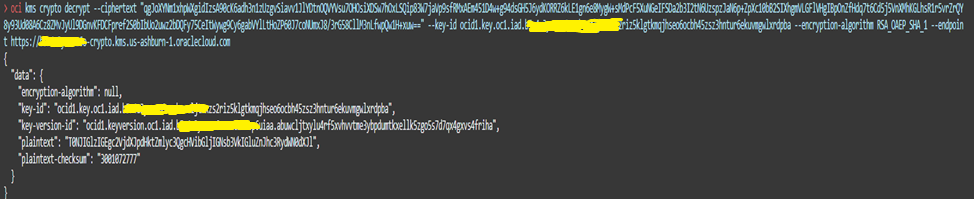
OCI Key Management offers robust features that enable you to achieve key redundancy and securely manage your encryption keys. With cross-region backup, restore and replication for Virtual Private Vault and BYOK/key import option for virtual vault, you can ensure that your data remains secure even if one region is entirely down. Applications hosted in different regions can leverage these features to encrypt and decrypt data securely across different regions.
Related Links
Acknowledgments
Author - Chaitanya Chintala (Cloud Security Advisor)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Create redundancy for Asymmetric Keys in Oracle Cloud Infrastructure Virtual Vaults
F82529-01
June 2023
Copyright © 2023, Oracle and/or its affiliates.