Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Understand Network Considerations for Oracle Cloud Infrastructure GoldenGate
Introduction
Oracle Cloud Infrastructure GoldenGate (OCI GoldenGate) is a fully managed cloud service that enables real-time data replication and streaming data processing from various data management systems to Oracle Cloud Infrastructure Database. It allows users to design, execute, and monitor data replication and streaming solutions without the need to manage compute environments.
In this tutorial, we will explore important networking considerations and supported architectures for OCI GoldenGate deployments.
Key Networking Aspects
When deploying OCI GoldenGate, there are two main networking aspects to consider:
- Endpoint type (public or private).
- Fully Qualified Domain Names (FQDNs)/Domain Name Service (DNS) configuration.
Let us go through each in detail.
-
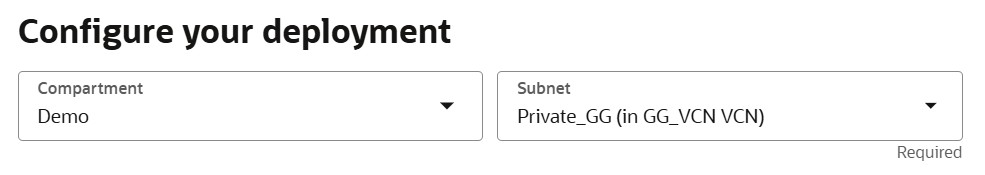
Private Endpoint: The private endpoint is the only required endpoint for a deployment. The public endpoint is optional and is covered later in the tutorial. Therefore, you must select a private subnet as public subnets will not display in the drop-down menu.
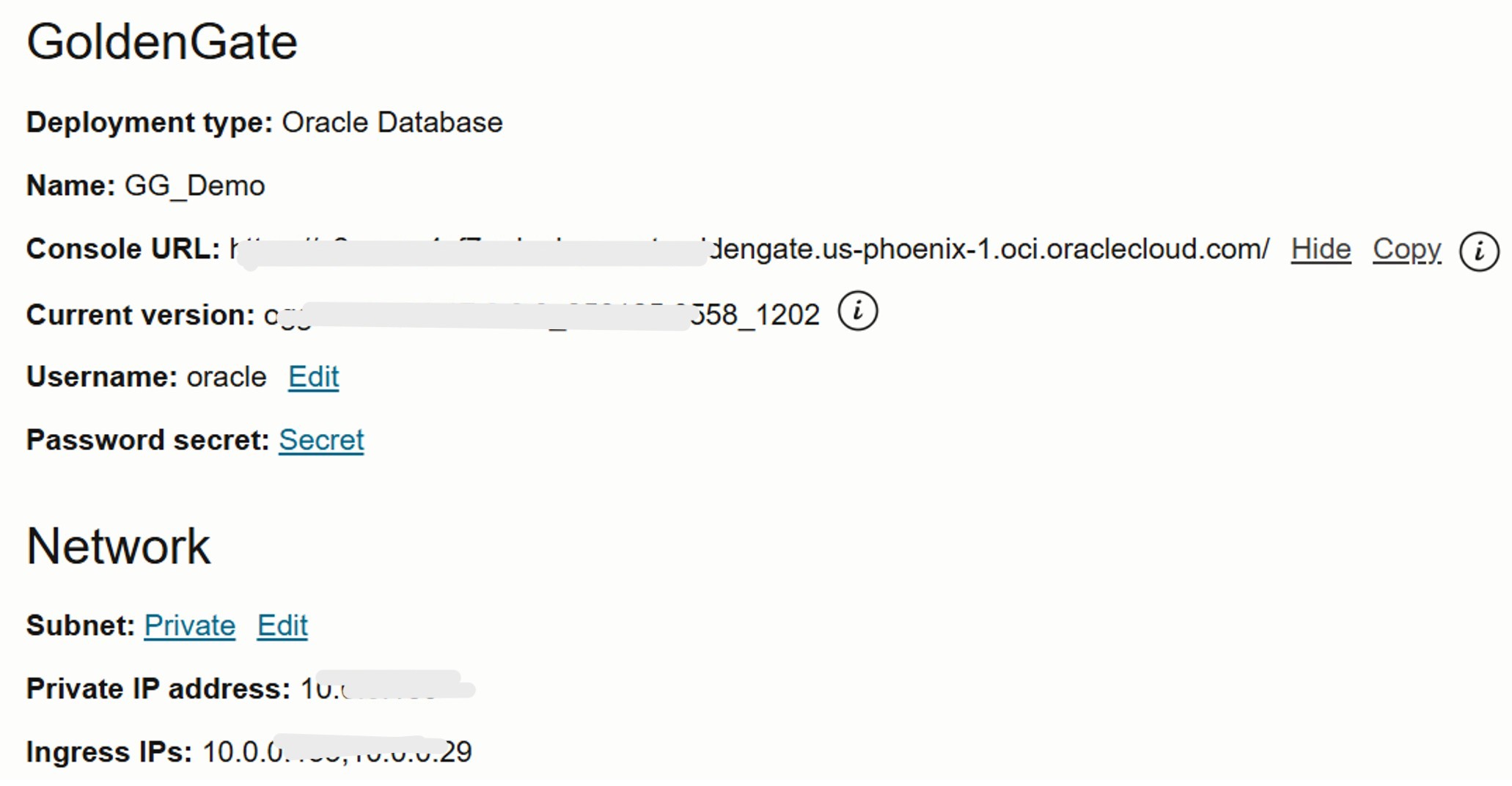
Console URL: The OCI GoldenGate console URL is used to access and manage your deployment.
It follows this format:
https://[random-characters].deployment.goldengate.[region].oci.oraclecloud.com/.For example:
https://v2cxxxxxxf7q.deployment.goldengate.us-phoenix-1.oci.oraclecloud.com/This URL is accessible over port 443. Access options depend on your network setup and also on which endpoint(s) users created; private only or private and public.
- Access from the same virtual cloud network (VCN).
- Access from a different VCN in the same region.
- Access from a different VCN in a different region or tenancy.
- Access from on-premises or another public cloud (Amazon Web Services, Microsoft Azure, Google Cloud Platform).
- Access from the Internet.
- Access from a custom endpoint.
Objectives
- Understand network considerations and supported architectures for OCI GoldenGate deployments.
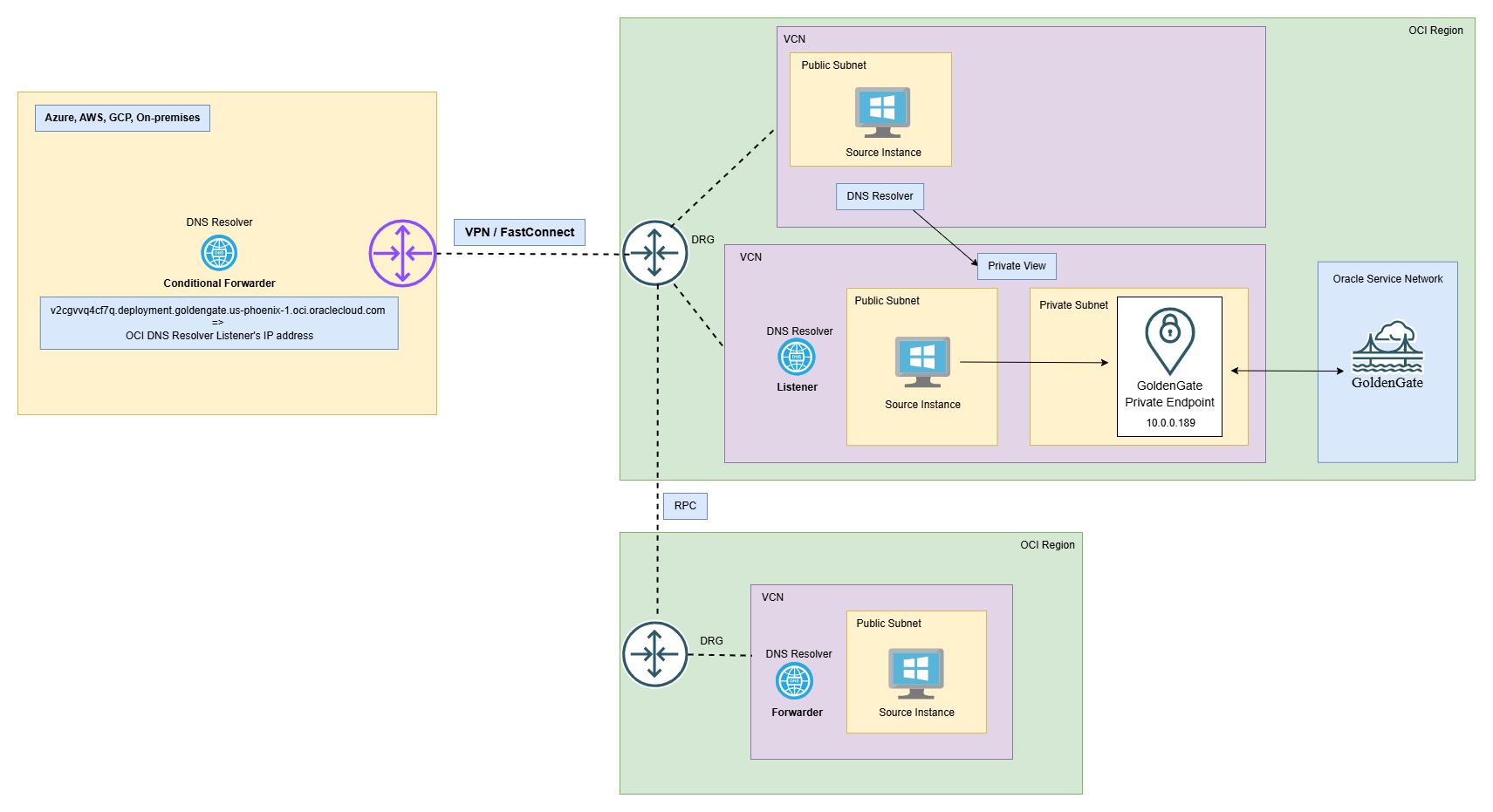
Scenario 1: Access from the Same VCN
Access to the OCI GoldenGate console URL from within the same VCN is allowed by default.
The Console URL internally resolves to a private IP address assigned to the private endpoint from the subnet selected during deployment. This private IP is accessible only to resources within the same VCN.
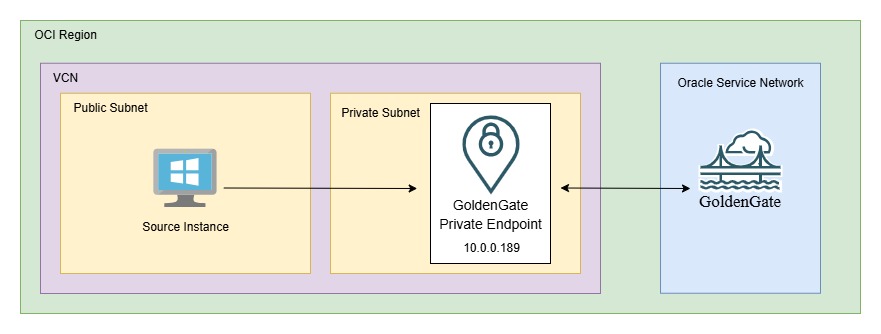
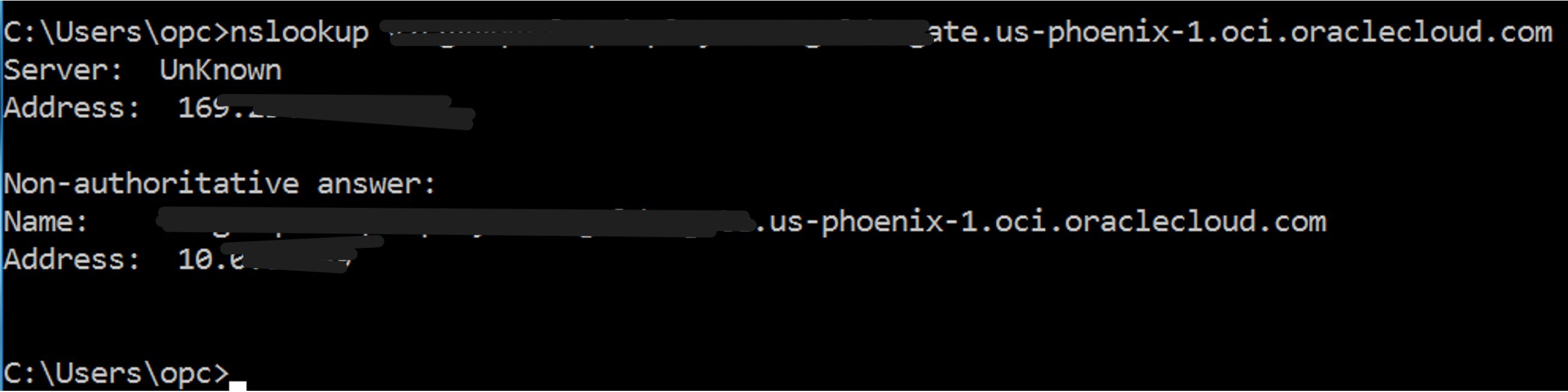
This setup is straightforward and works reliably.
Scenario 2: Access from a Different VCN in the Same Region
If your source/bastion host is in another VCN but within the same region.
-
Set up connectivity using Dynamic Routing Gateway (DRG) attachment (recommended) or Local Peering Gateway (LPG). For more information, see Dynamic Routing Gateways.
-
For DNS resolution, you have the following options for Name Resolution:
-
Associate Private View (Recommended):
Go to the source VCN’s DNS resolver and associate the private view of the OCI GoldenGate VCN.
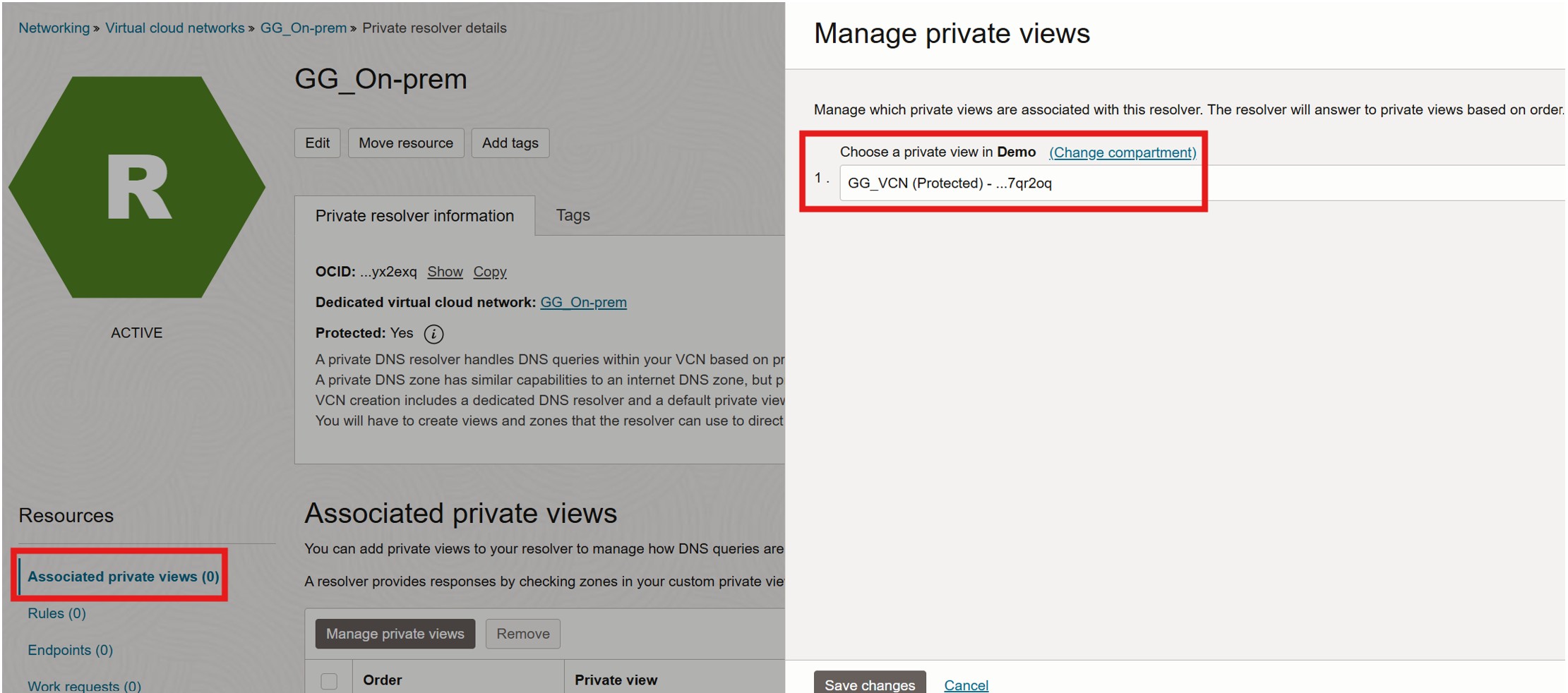
-
Create Conditional Forwarding:
Set up a custom forwarding rule using a VCN DNS forwarder or a private DNS server.
-
Update the Host File:
We can also update the operating system’s host file. This will resolve the FQDN locally on our host and connect through the OCI GoldenGate console’s private IP. This option is useful when we want to resolve the OCI GoldenGate FQDN only from specific compute instances and do not want to use Associate Private View for the entire VCN. However, this option has the limitation that it is a manual process for each host and is not easily scalable.
-
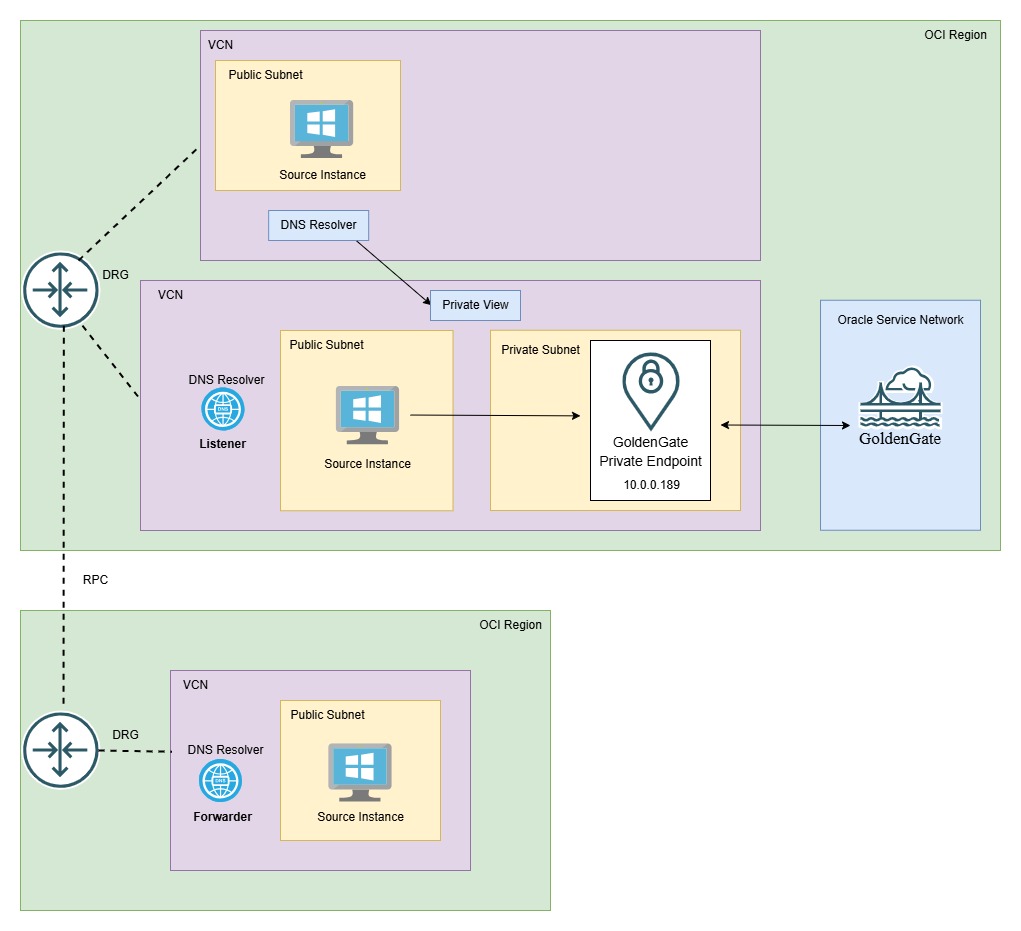
Scenario 3: Access from a Different VCN in a Different Region or Different Tenancy
Follow these steps if your source/bastion host is in a different region/tenancy. Since associating private views across tenancies or regions is not supported.
-
Set up Remote Peering Connection (RPC) between VCNs in a different region/tenancy. For more information, see Remote VCN Peering through an Upgraded DRG.
-
For DNS resolution, you have the following options for Name Resolution:
-
Create Conditional Forwarding (Recommended):
Set up DNS resolver endpoints (listener and forwarder) and configure forwarding rules for the OCI GoldenGate FQDN. Follow the steps to create OCI DNS resolver conditional forwarding:
-
Go to the OCI GoldenGate VCN, navigate to DNS Resolver, Endpoints, Create Endpoint and click Create Listener.
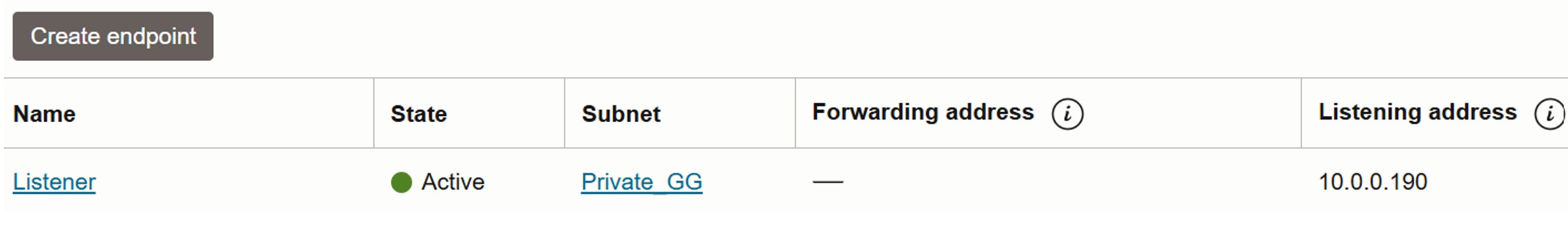
-
Go to the source VCN in a different region or tenancy, navigate to DNS Resolver, Endpoints, Create Endpoint and click Create Forwarder.
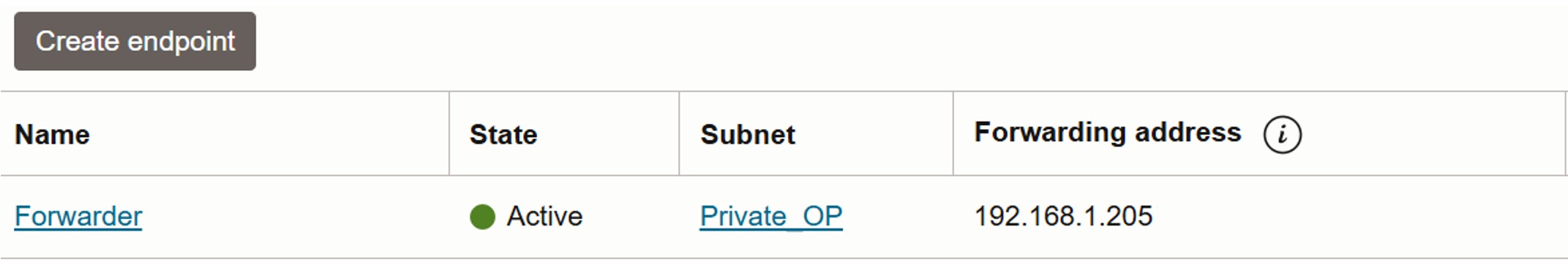
-
Click Rules, Manage Rules and add a forwarding rule for the OCI GoldenGate console FQDN, pointing to the listener’s IP created in step 1.
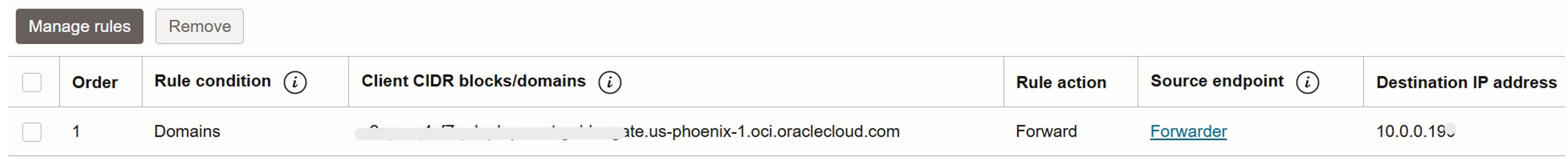
-
-
Update the Host File:
Modify the host file on individual machines (manual and not scalable).
-
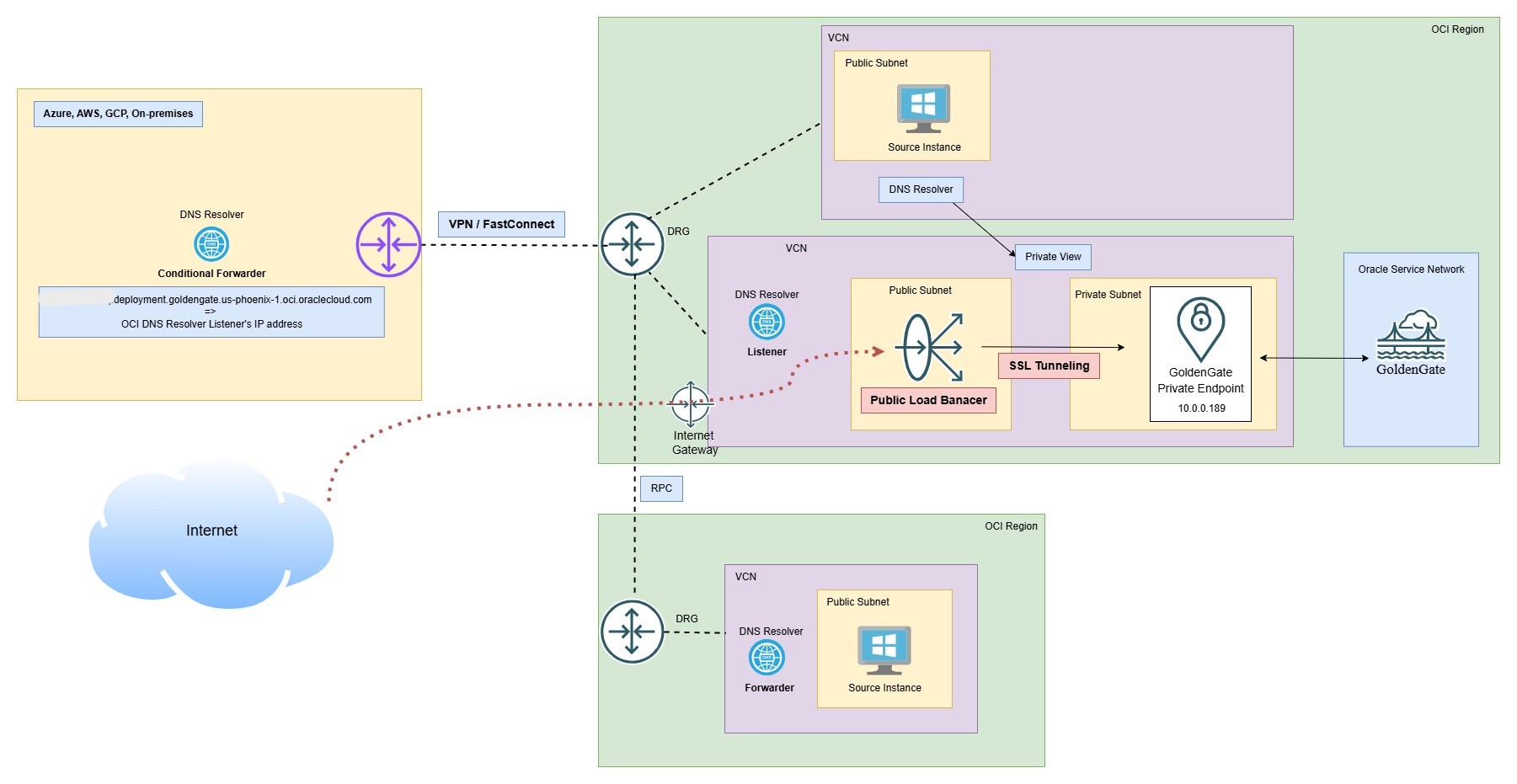
Scenario 4: Access from On-Premises or Other Public Clouds (AWS, Azure and GCP)
This is a common scenario when accessing the OCI GoldenGate service console privately from on-premises environments or other public clouds (such as Amazon Web Services, Microsoft Azure, or Google Cloud Platform).
-
The first requirement is to establish network connectivity, with the primary options being OCI Site-to-Site VPN or OCI FastConnect private peering. These connectivity methods provide access to OCI private services. For more information, see Site-to-Site VPN Overview and FastConnect Overview.
-
DNS resolution remains a challenge because the service FQDNs are local to the VCN. To resolve these FQDNs from on-premises environments or other clouds, the following options are available:
-
Create Conditional Forwarding (Recommended):
In this approach, you set up a DNS forwarding endpoint or a private DNS server (such as a Windows DNS server) with conditional forwarding for name resolution. The DNS server will forward resolution requests to the OCI DNS resolver listener’s IP address.
-
Update the Host File:
Modify the host file on individual machines (manual and not scalable).
-
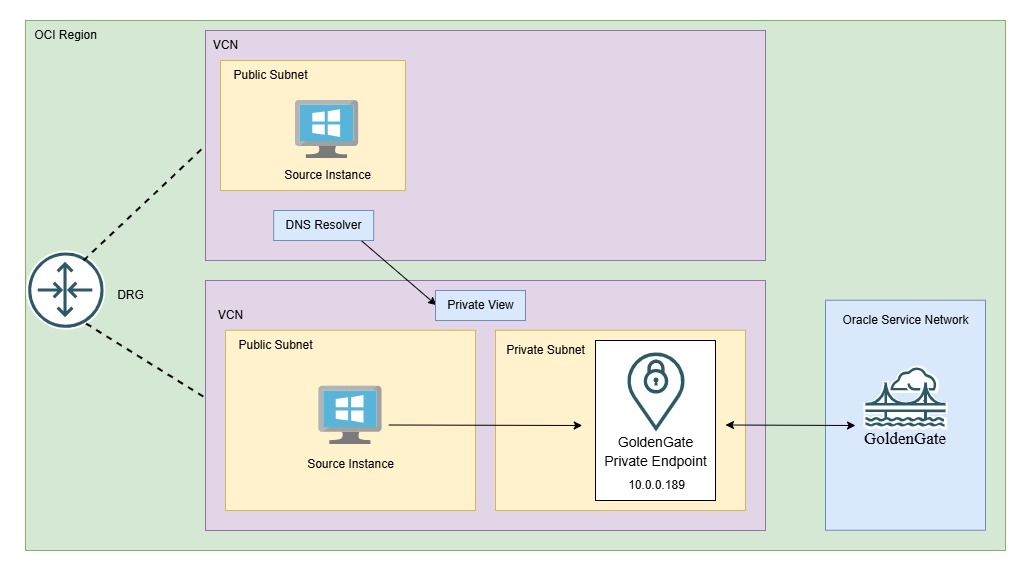
Scenario 5: Access from the Internet
When we deploy the OCI GoldenGate service, the private endpoint is the only required endpoint for a deployment, and we must select a private subnet. In fact, it does not even show any public subnets in the drop-down menu.
The public endpoint is optional and there is a separate option to enable OCI GoldenGate console public access, which allows us to select a public subnet under Show advanced options.
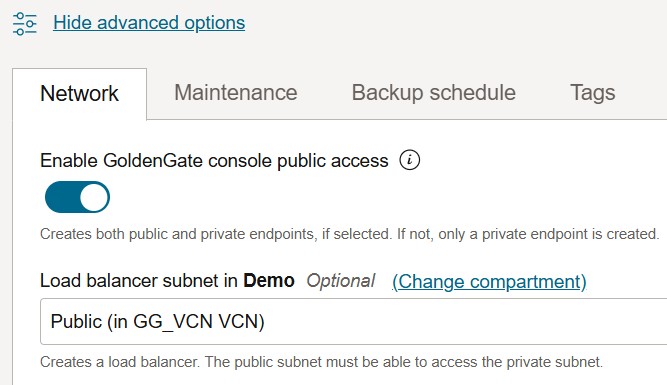
This provisions a public OCI Load Balancer with SSL tunneling in the public subnet. This option resolves the OCI GoldenGate console access FQDN to the load balancer’s public IP address on the internet. Therefore, we can access the OCI GoldenGate console from the internet as well.
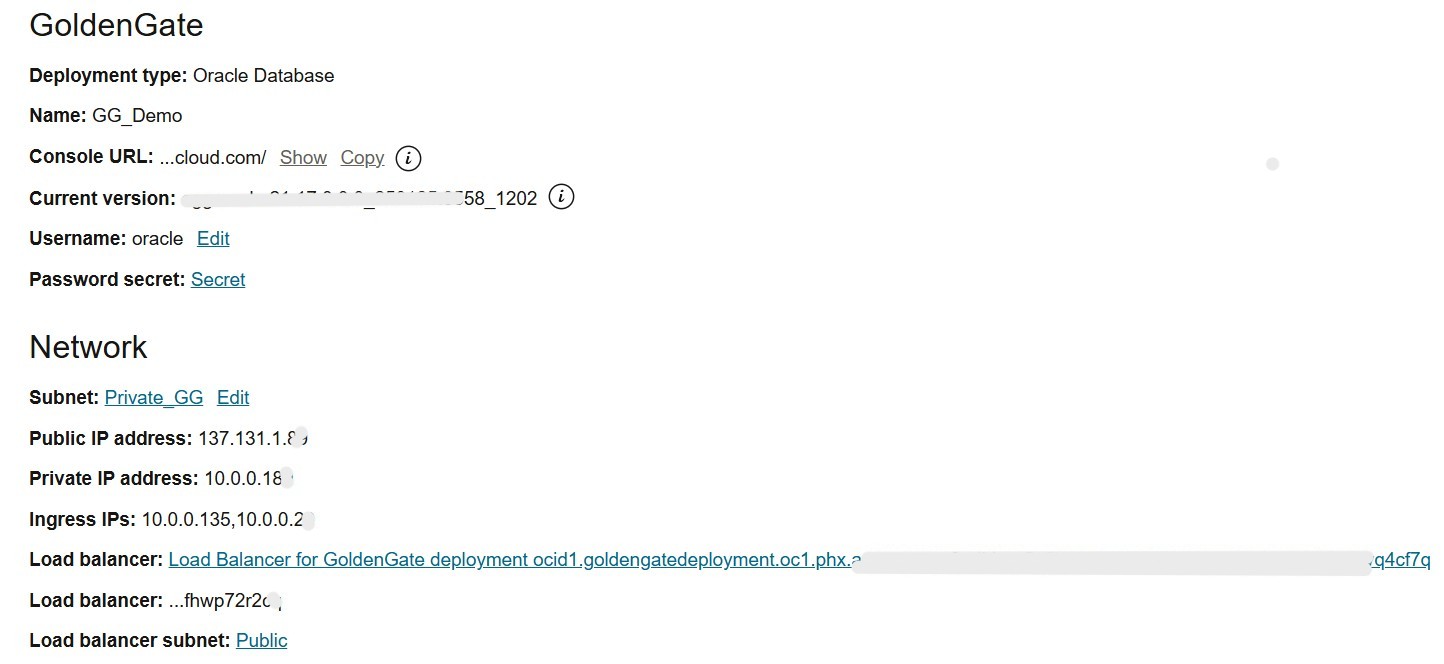
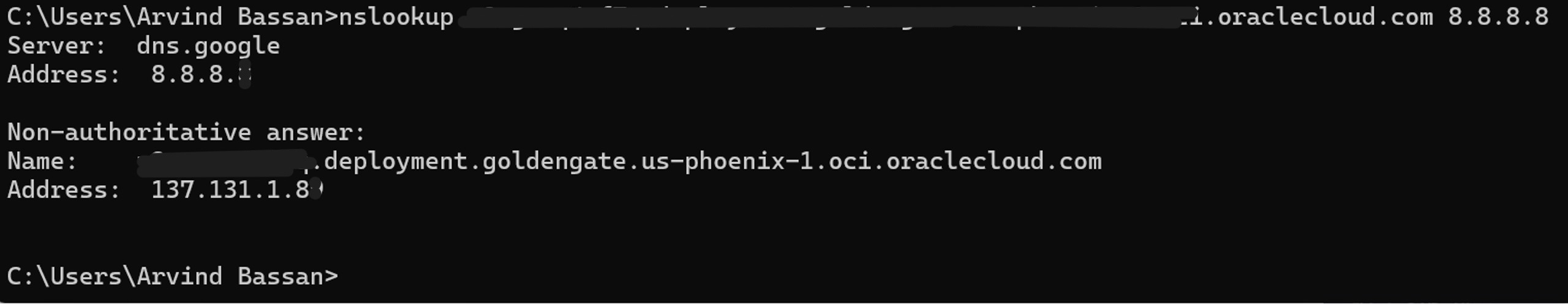
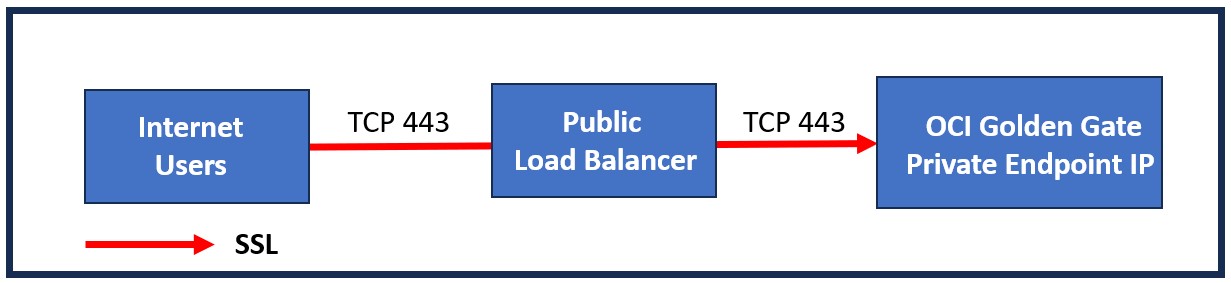
You can see all of this in the following image:
Scenario 6: Access from a Custom Endpoint
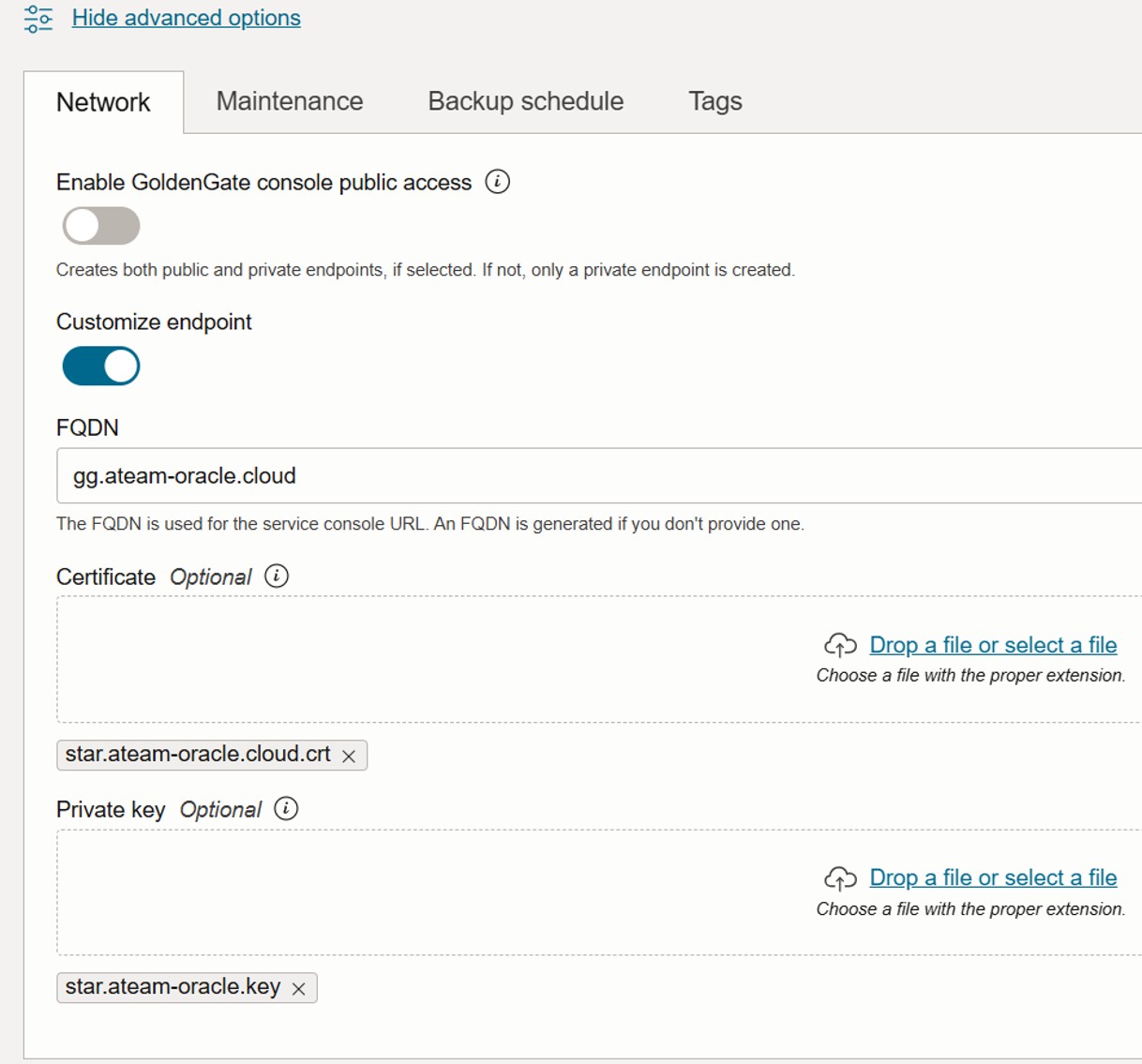
The OCI GoldenGate service also allows us to set up a custom endpoint to access the OCI GoldenGate console. We can enter a custom FQDN along with the corresponding SSL certificate and private key in .pem format under Show advanced options.
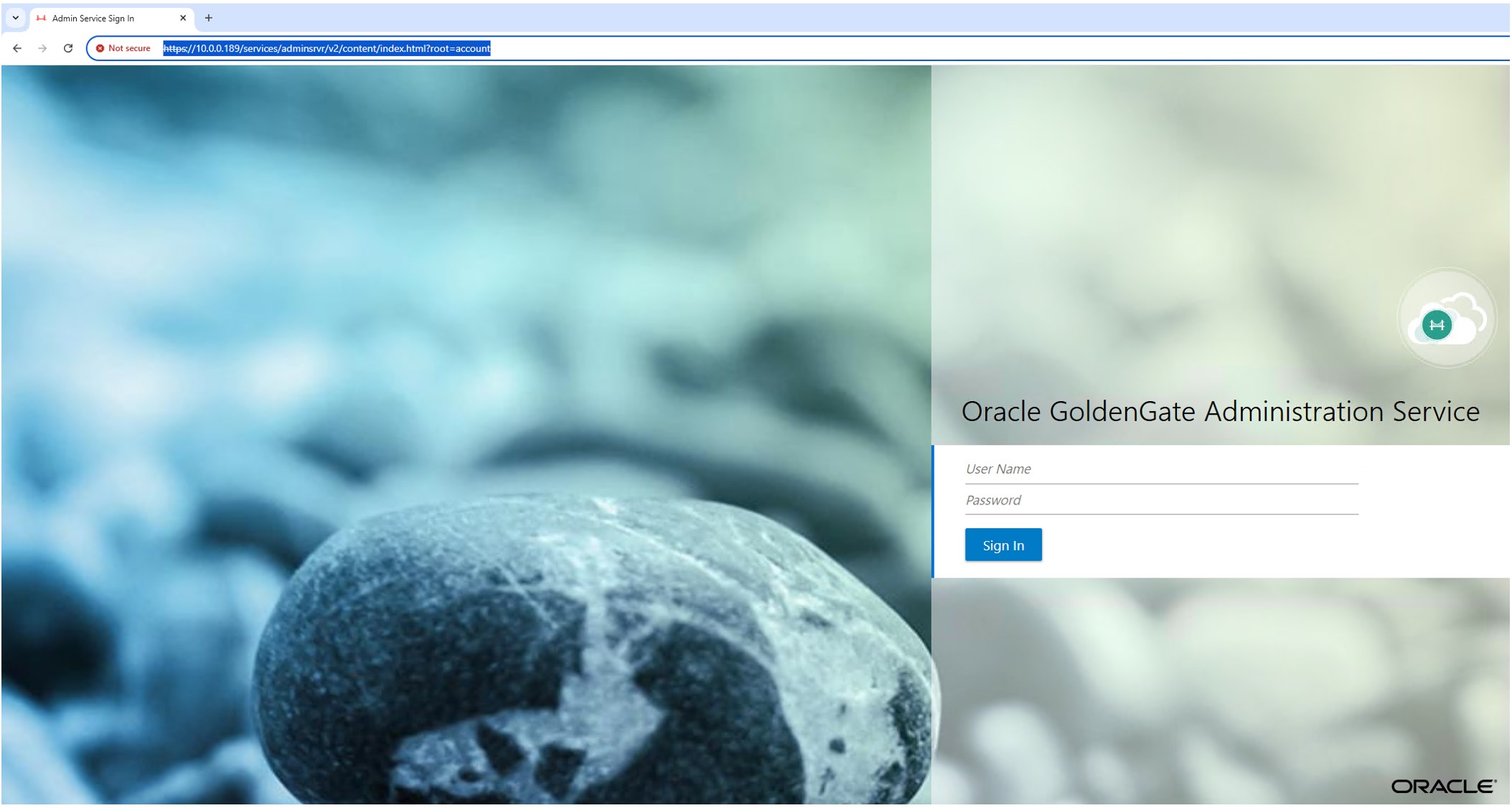
Note: We can also access the OCI GoldenGate console directly using its private or public IP. However, the browser will show a Not secure warning because the hostname will not match the backend certificate. Therefore, this is not a recommended method for accessing the OCI GoldenGate console, especially from the internet.
It is suggested to set up proper DNS resolution to ensure a complete SSL handshake.
Conclusion
Deploying OCI GoldenGate requires careful planning around networking and DNS resolution, depending on your access requirements:
- Within a VCN: Direct access is available. This setup is straightforward and works reliably.
- Across VCNs or Tenancies: Use a DRG, LPG, private views, and conditional forwarding.
- From On-Premises or Other Clouds: Establish connectivity using VPN or OCI FastConnect, combined with conditional forwarding for DNS resolution.
- Public Access: Deploy a public OCI Load Balancer with SSL tunneling to securely expose the service.
- Custom Domains: Implement custom FQDNs with SSL certificates to enable secure and user-friendly URLs.
Choosing the right networking and DNS strategy ensures secure and seamless access to your OCI GoldenGate deployments across various environments.
Acknowledgments
- Author - Arvind Bassan (Principal Cloud Architect)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Understand Network Considerations for Oracle Cloud Infrastructure GoldenGate
G34093-01
Copyright ©2025, Oracle and/or its affiliates.