Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Configure two way domain name resolution for Oracle Cloud Infrastructure and On-Premises services
Introduction
Domain Name System (DNS) is a common service used in On-Premises environments, however once you are in the cloud the same technology can be applied but with particular configurations. Name Resolution can be useful if you want to access systems, computers, services and other resources using the common names you already have without hardcoding IP addresses on your applications.
Objective
Configure two way domain name resolution for Oracle Cloud Infrastructure (OCI) and On-Premises services.
Prerequisites
- Access to Oracle Cloud Infrastructure (OCI) console with enough IAM permissions to configure VCN service check. For more details, see Required IAM Service Policy.
- On-Premises DNS Server (Installation not covered in this tutorial).
- OCI VCN deployed with public and private subnets (initial configuration not covered in this tutorial).
- Connectivity between OCI and On-Premises (FastConnect or VPN deployment is not covered in this tutorial).
- Connectivity between OCI and On-Premises (On-Premises security access list, OCI Security list or Network security groups) to allow DNS traffic flow (for example, TCP/UDP port 53, and so on).
- In this tutorial we will use 2 servers, one deployed on OCI, one deployed On-Premises. Ensure you have this set up and have access to these servers to run name resolution tests.
Considerations:
- Connectivity between OCI Subnet A (10.0.0.0 /24) and On-Premises Subnet (172.16.11.0 /24) where
example.localDNS server resides. The detailed steps for establishing connectivity are out of scope for this tutorial. For more information, see FastConnect, DRG, VPN documentation. - The user who configures the OCI DNS must have enough privileges to make changes on VCN. Policies definition is out of scope for this tutorial. For more details, see Required IAM Service Policy.
Topology
This tutorial uses the following topology:

DNS Service on OCI
When you initially create a VCN and subnets, you may specify DNS labels for each. Subnet DNS labels can only be set if the VCN itself is created with a DNS label. The labels, along with the parent domain of oraclevcn.com form the VCN domain name and subnet domain name:
- VCN domain name:
<VCN DNS label>.oraclevcn.com - Subnet domain name:
<subnet DNS label>.<VCN DNS label>.oraclevcn.com
When you launch an instance, you may assign a hostname. It is assigned to the VNIC that is automatically created during instance launch (the primary VNIC). Along with the subnet domain name, the hostname forms the fully qualified domain name (FQDN):
- Instance FQDN:
<hostname>.<subnet DNS label>.<VCN DNS label>.oraclevcn.com
For example: instance-remote.publicsubnet.vcnremote.oraclevcn.com.
Task 1: Set up the initial configuration
On-Premises initial state
-
example.localdomain is configured as local domain -
Main DNS Server is 172.16.11.55
-
Static host registry is created as
server1.example.local, ip address 172.16.11.3
-
There is no connectivity to OCI resources via name resolution

OCI initial state
-
We have default DNS configuration
-
Local OCI Names are resolved

-
There is no connectivity to On-Premises resources via name resolution

Task 2: Set up the OCI environment
In order to resolve DNS entries from On-Premises to OCI, we will create some rules on both DNS. These rules will forward DNS queries to specific domains as required. On-Premises queries looking for OCI domains will be forwarded to OCI DNS Service; OCI queries looking for On-Premises domains will be forwarded to On-Premises DNS Server.
Note: DNS Resolver has impact at VCN level, any change on it will apply to all Subnets within.
-
Navigate to the VCN Details page and verify the DNS Resolver configuration

-
In the VCN/DNS Resolver Details page, click Create Endpoint. You can select Listening or Forwarding as described in the following steps.

-
If you select Listening Endpoint Type, all DNS queries forwarded to OCI will be listened by this Endpoint.

A. Select the Listening Endpoint Type.
B. Provide a Custom Name.
C. Select compartment and subnet for the Endpoint. Ensure that you can reach this subnet from your On-Premises network, specifically your On-Premises DNS server forwarding DNS queries must be able to access this network.
D. Provide a custom IP, if you don’t select one, service will choose one for you, this IP will be in the subnet.
E. You can restrict access to this Endpoint, a security best practice is to assign an NSG, be sure you have configured the inbound rules in order to allow DNS traffic from the On-Premises DNS Server IP.
-
If you select Forwarding Endpoint Type, all the DNS queries forwarded to On-Premises DNS will be forwarded by this Endpoint.

A. Select the Forwarding Endpoint Type.
B. Provide a Custom Name.
C. Select compartment and subnet for the Endpoint. Ensure that you can reach this subnet from your On-Premises network, specifically your On-Premises DNS server forwarding DNS queries must be able to access this network.
D. Provide a custom IP, if you don’t select one, service will choose one for you, this IP will be in the subnet.
E. You can restrict access to this Endpoint, a security best practice is to assign an NSG, be sure you have configured the inbound rules in order to allow DNS traffic from the On-Premises DNS Server IP.

Note:
- All DNS traffic to On-Premises DNS server will be forwarded using IP A.
- All DNS traffic to OCI DNS Service should be forwarded from On-Premises to IP B.
- Ensure connectivity from/to these IP addresses (routing, firewall access list, NSG, etc.) from On-Premises through VPN/FastConnect.
Set up the forwarding Rules
We will create a rule to forward all DNS queries from example.local domain to On-Premises DNS Server (172.16.11.55). This rule will match all DNS queries to example.local domain and will forward this query to 172.16.11.55 IP looking for name resolution.
-
Go to VCN/Private Resolver Details, Rules/Manage Rules.


A. Select Domain or CIDR Block to match rules, in this tutorial, we will use Domains.
B. You can add up to 10 domain entries to match the rule, you should group all the domains who share the same Destination DNS IP Address entry.
C. Select the Source Endpoint to forward queries, remember this IP should be routed and allowed on different access lists through VPN/FastConnect connection.
D. Enter the destination On-Premises DNS Server IP address.
Task 3: Set up the On-Premises environment
We are working with Microsoft® DNS Service running in a Domain Controller, we will create a conditional forward rule to forward all DNS queries looking for oraclevcn.com domain to OCI DNS Resolver Service.
-
In DNS Manager configuration page, right-click Conditional Forwarders/New Conditional Forwarder.


A. Enter the OCI DNS name you want to resolve from the On-Premises network.
B. Enter the OCI Listener Endpoint [IP Address].
C. Click OK.
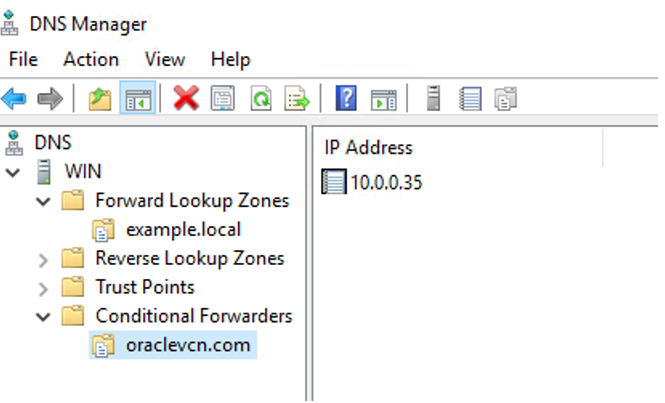
Now we have the DNS names resolution configured both ways from OCI to On-Premises and vice-versa.
Task 4: Test the configuration
Test the configuration and the results should be similar to the following screenshots.
On-Premises to OCI

OCI to On-Premises

Related Links
Acknowledgments
- Author - Jaime Rojas (LAD A-Team Engineer)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Configure two way domain name resolution for Oracle Cloud Infrastructure and On-Premises services
F78338-02
April 2023
Copyright © 2023, Oracle and/or its affiliates.