About Authorization
Authorization is about ensuring users can do and see what they are authorized to do and see.
After a user has been authenticated, the next critical aspect of security is ensuring that the user can do and see what they are authorized to do and see. Authorization for Oracle Analytics Server is controlled by a security policy defined in terms of application roles.
About Application Roles
Application roles define the security policy for users.
Instead of defining the security policy in terms of users in groups in a directory server, Oracle Analytics Server uses a role-based access control model. Security is defined in terms of application roles that are assigned to directory server groups and users. For example, application roles BIServiceAdministrator, BI Consumer, and BIContentAuthor.
Application roles represent a functional role that a user has given the user the privileges required to perform that role. For example, the Sales Analyst application role might grant a user access to view, edit, and create reports on a company's sales pipeline.
This indirection between application roles and directory server users and groups allows the administrator to define the application roles and policies without creating additional users or groups in the corporate LDAP server. Instead, the administrator defines application roles that meet the authorization requirements and assigns those roles to preexisting users and groups in the corporate LDAP server.
In addition, the indirection afforded by application roles allows moving artifacts between development, test, and production environments. No change to the security policy is needed as a result of the environment moves, and all that is required is to assign the application roles to the users and groups available in the target environment.
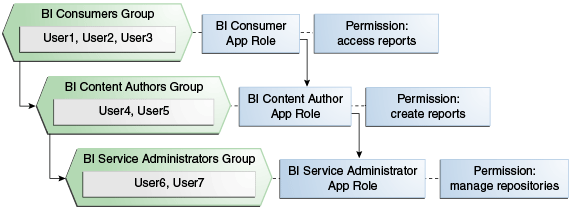
For example, the diagram below shows a set of groups, users, application roles, permissions, and inheritance.
The diagram shows the following:
-
The group named BI Consumers Group contains User1, User2, and User3. Users in the BI Consumers Group are assigned the application role BI Consumer, which enables the users to view reports.
-
The group named BI Content Authors Group contains User4 and User5. Users in the BI Content Authors Group are assigned the application role BI Content Author, which enables the users to create reports.
-
The group named BI Service Administrators Group contains User6 and User7. Users in the BI Service Administrators Group are assigned the application role BI Service Administrator, which enables the users to manage repositories (semantic models).
About the Security Policy
The security policy is split across Presentation Services, the semantic model, and the policy store.
Presentation Services
Presentation Services defines the specific catalog objects and functionality that users can access with specific application roles. Access to functionality is defined in the Managing Privileges page and access to catalog objects is defined in the Permission dialog.
Semantic Model
The semantic model defines the metadata items in the semantic model that user can access with assignment to specific application roles. You can define the security policy using Model Administration Tool.
Policy Store
The Policy Store defines the BI Server and Publisher functionality that user can access with specific application roles. In the default Oracle Analytics Server configuration, the policy store is managed using the grant and revoke scripts or by using Oracle WebLogic Scripting Tool (WLST).