Understanding Security Realms, Providers and Control Flags
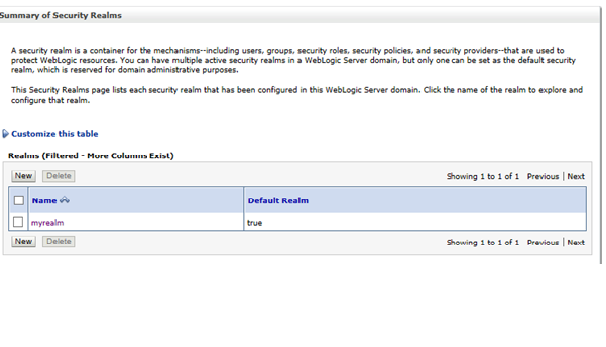
A WebLogic domain can contain one or more Security Realms. Each realm defines a security configuration, users and groups. Only one realm can be active at any one time, and generally there is no benefit in creating additional realms. The default realm in a WebLogic domain is named 'myrealm':
Figure 4-1 Summary of Security Realms
Each realm contains a number of security 'providers'. Providers are 'authenticators', which handle user authentication and user stores, or 'identity asserters', which can determine user identity from data embedded in a request, such as X.509 certificates or SAML tokens. The Oracle Access Manager Identity Asserter, used for OAM integration, is explained in WebLogic Configuration.
The default security realm has one authenticator and two identity asserters:
Figure 4-2 Myrealm Settings
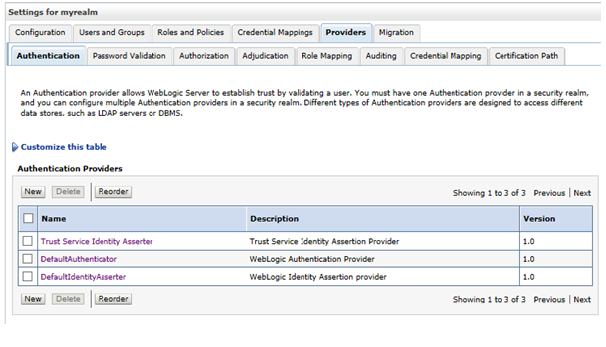
The DefaultAuthenticator handles users in the internal WebLogic store.
Each Authenticator provider has a control flag setting. The flag determines the part that the provider plays in authenticating a user. There are four possible flag values, but the two of importance here are:
REQUIRED: authentication in this provider must succeed for the overall process to complete.
SUFFICIENT: if authentication in this provider succeeds, the overall process is successful, as long as no other authenticator has the REQUIRED control flag.
The DefaultAuthenticator is pre-configured with the control flag set to REQUIRED so that it is required to succeed even if an LDAP authentication provider is configured. Part of the process of configuring LDAP support is to change this value to SUFFICIENT.
The order of providers is also important. When more than one authenticator is enabled and configured with the correct control flags, a user supported by any of the authenticators is able to login to the WebLogic Administration Console. However EDQ has access to the first authenticator in the list only; users from authenticators lower in the list will not be recognized. Therefore it is important that when an LDAP authenticator is added, it is moved to the top of the list. This is also covered below.