11 Switching to External Authentication
For maximum security in production environments, Oracle recommends integrating Oracle WebCenter Sites with Oracle Access Management, for an advanced identity management solution and a seamless single sign-on user experience. You also have the option of integrating WebCenter Sites with an external LDAP authentication provider directory.
The following topics describe how to configure WebCenter Sites for authentication against either external identity management solution:
- Switching to Authentication Against an LDAP Directory
This topic describes how to switch WebCenter Sites to authentication against an external LDAP authentication provider directory. This is a recommended solution for production environments if integration with Oracle Access Management is not viable. - Switching to Authentication Against Oracle Access Manager
You can configureWebCenter Sites for authentication against Oracle Access Manager. This solution is recommended for production environments. - Switching to Authentication OAM Using Detached Credential Collector
This topic will show the steps to configure the two webgates and two OHS. You can configure Site Capture, Satellite Server, and Visitor Services to OAM in the similar using the steps in this topic.
Parent topic: Configuring WebCenter Sites Components
Switching to Authentication Against an LDAP Directory
This topic describes how to switch WebCenter Sites to authentication against an external LDAP authentication provider directory. This is a recommended solution for production environments if integration with Oracle Access Management is not viable.
Parent topic: Switching to External Authentication
Switching to Authentication Against Oracle Access Manager
You can configureWebCenter Sites for authentication against Oracle Access Manager. This solution is recommended for production environments.
oamconsole and some configuration changes in the Sites.
- Integrating SiteCapture with OAM
This topics covers steps to integrate SiteCapture with OAM. - Integrating OAM with Oracle WebCenter Sites: Satellite Server
This topics covers steps to integrate OAM with Oracle WebCenter Sites: Satellite Server. - Integrating OAM with Visitor Services
This topic covers steps to integrate OAM with Visitor Services.
Parent topic: Switching to External Authentication
Integrating SiteCapture with OAM
This topics covers steps to integrate SiteCapture with OAM.
Integrating OAM with Oracle WebCenter Sites: Satellite Server
This topics covers steps to integrate OAM with Oracle WebCenter Sites: Satellite Server.
Note:
The code example below gives the RSS configuration inOAM OHS, and mod_wl_ohs.conf file.<IfModule weblogic_module>
<Location /ss>
SetHandler weblogic-handler
WebLogicHost SATELLITESERVER_HOST
WebLogicPort SATELLITESERVER_HOST
</Location>
</IfModule>Integrating OAM with Visitor Services
This topic covers steps to integrate OAM with Visitor Services.
Note:
The code example below gives the Visitor configuration inOAM OHS, and mod_wl_ohs.conf file.<IfModule weblogic_module>
<Location /oamlogin>
SetHandler weblogic-handler
WebLogicHost SITES_HOST
WebLogicPort SITES_PORT
</Location>
</IfModule>
<IfModule weblogic_module>
<Location /visitors-webapp>
SetHandler weblogic-handler
WebLogicHost VISITORSERVICES_HOST
WebLogicPort VISITORSERVICES_HOST
</Location>
</IfModule>Switching to Authentication OAM Using Detached Credential Collector
This topic will show the steps to configure the two webgates and two OHS. You can configure Site Capture, Satellite Server, and Visitor Services to OAM in the similar using the steps in this topic.
- Prerequisites
This chapter lists the prerequisites required for configuring the Detached Credential Collector. - DCC WebGate Configuration
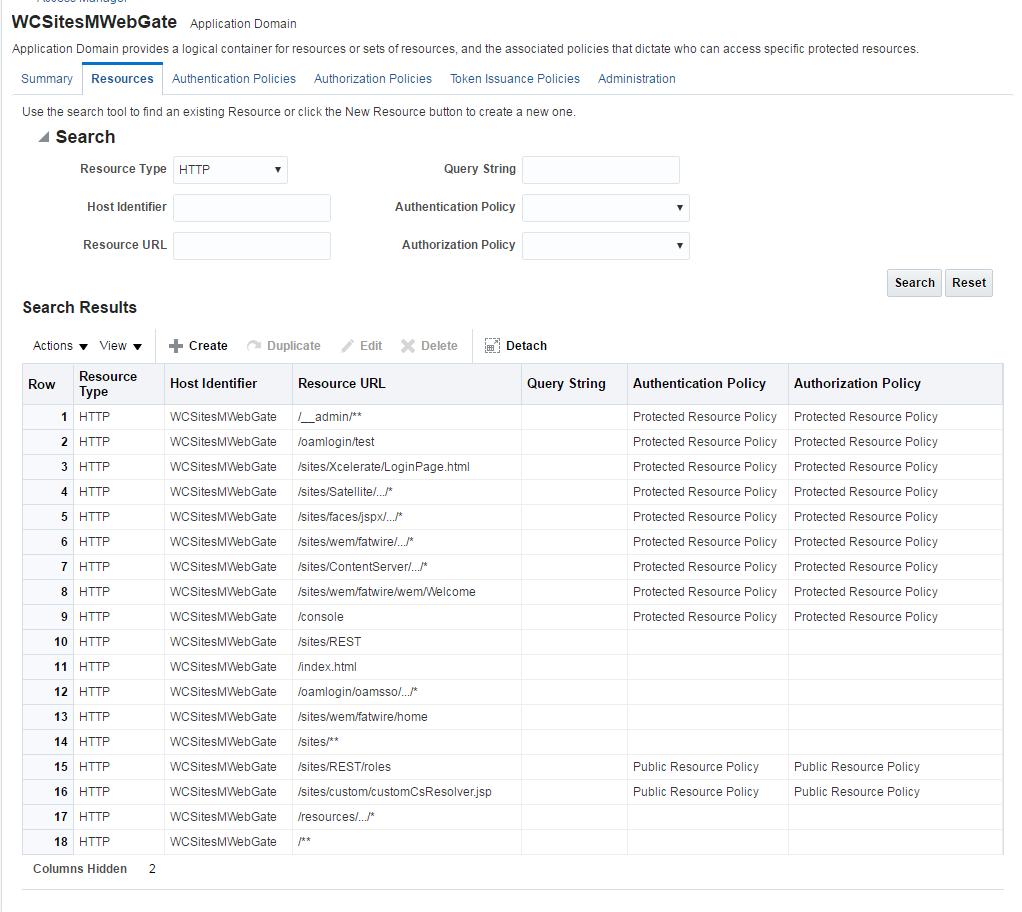
This topic describes hot to configure DCC Webgate. - Resource WebGate Configuration
This topics provides steps to configure the Resource Webgate. - Sites OAM Integration
This topic provides steps to configure the Sites OAM integration with DCC
Parent topic: Switching to External Authentication
Prerequisites
This chapter lists the prerequisites required for configuring the Detached Credential Collector.
DCC WebGate Configuration
This topic describes hot to configure DCC Webgate.
Resource WebGate Configuration
This topics provides steps to configure the Resource Webgate.