5 Using the Enterprise Deployment Workbook
The Enterprise Deployment workbook enables you to plan an enterprise deployment for your organization.
This chapter provides an introduction to the Enterprise Deployment workbook, use cases, and information on who should use the Enterprise Deployment workbook.
- Introduction to the Enterprise Deployment Workbook
The Enterprise Deployment workbook is a spreadsheet that is used by architects, system engineers, database administrators, and others to plan and record all the details for an environment installation (such as server names, URLs, port numbers, installation paths, and other resources). - Typical Use Case for Using the Workbook
It is important to understand the roles and tasks involved in a typical use case of the Enterprise Deployment workbook. - Who Should Use the Enterprise Deployment Workbook?
The details of the Enterprise Deployment workbook are filled in by the individual or a team that is responsible for planning, procuring, or setting up each category of resources. - Using the Oracle Identity and Access Management Enterprise Deployment Workbook
Locating and understanding the Oracle Identity and Access Management Enterprise Deployment Workbook enables you to use it efficiently.
Parent topic: Preparing for an Enterprise Deployment
Introduction to the Enterprise Deployment Workbook
The Enterprise Deployment workbook is a spreadsheet that is used by architects, system engineers, database administrators, and others to plan and record all the details for an environment installation (such as server names, URLs, port numbers, installation paths, and other resources).
The Enterprise Deployment workbook serves as a single document that you can use to track input variables for the entire process, allowing for:
-
Separation of tasks between architects, system engineers, database administrators, and other key organizational roles.
-
Comprehensive planning before the implementation.
-
Validation of planned decisions before the actual implementation.
-
Consistency during implementation.
-
A record of the environment for future use.
Parent topic: Using the Enterprise Deployment Workbook
Typical Use Case for Using the Workbook
It is important to understand the roles and tasks involved in a typical use case of the Enterprise Deployment workbook.
A typical use case for the Enterprise Deployment workbook involves the following roles and tasks, in preparation for an Oracle Fusion Middleware Enterprise Deployment:
-
Architects read through the first five chapters of this guide, and fill in the corresponding sections of the workbook.
-
The workbook is validated by other architects and system engineers.
-
The architect uses the validated workbook to initiate network and system change requests with the system engineering departments.
-
The Administrators and System Integrators who install and configure the software refer to the workbook and the subsequent chapters of this guide to perform the installation and configuration tasks.
Parent topic: Using the Enterprise Deployment Workbook
Who Should Use the Enterprise Deployment Workbook?
The details of the Enterprise Deployment workbook are filled in by the individual or a team that is responsible for planning, procuring, or setting up each category of resources.
The information in the Enterprise Deployment workbook is divided into categories. Depending on the structure of your organization and roles that are defined for your team, you can assign specific individuals in your organization to fill in the details of the workbook. Similarly, the information in each category can be assigned to the individual or team that is responsible for planning, procuring, or setting up each category of resources.
For example, the workbook can be filled in, reviewed, and used by people in your organization that fill the following roles:
-
Information Technology (IT) Director
-
Architect
-
System Administrator
-
Network Engineer
-
Database Administrator
Parent topic: Using the Enterprise Deployment Workbook
Using the Oracle Identity and Access Management Enterprise Deployment Workbook
Locating and understanding the Oracle Identity and Access Management Enterprise Deployment Workbook enables you to use it efficiently.
The following sections provide an introduction to the location and contents of the Oracle Identity and Access Management Enterprise Deployment Workbook:
- Locating the Oracle Identity and Access Management Enterprise Deployment Workbook
- Understanding the Contents of the Oracle Identity and Access Management Enterprise Deployment Workbook
Parent topic: Using the Enterprise Deployment Workbook
Locating the Oracle Identity and Access Management Enterprise Deployment Workbook
The Oracle Identity and Access Management Enterprise Deployment Workbook is available as a Microsoft Excel Spreadsheet in the Oracle Fusion Middleware documentation library. It is available as a link on the Install, Patch, and Upgrade page of the library.
Understanding the Contents of the Oracle Identity and Access Management Enterprise Deployment Workbook
The following sections describe the contents of the Oracle Identity and Access Management Enterprise Deployment Workbook. The workbook is divided into tabs, each containing a set of related variables and values you will need to install and configure the Oracle Identity and Access Management Enterprise Deployment topologies:
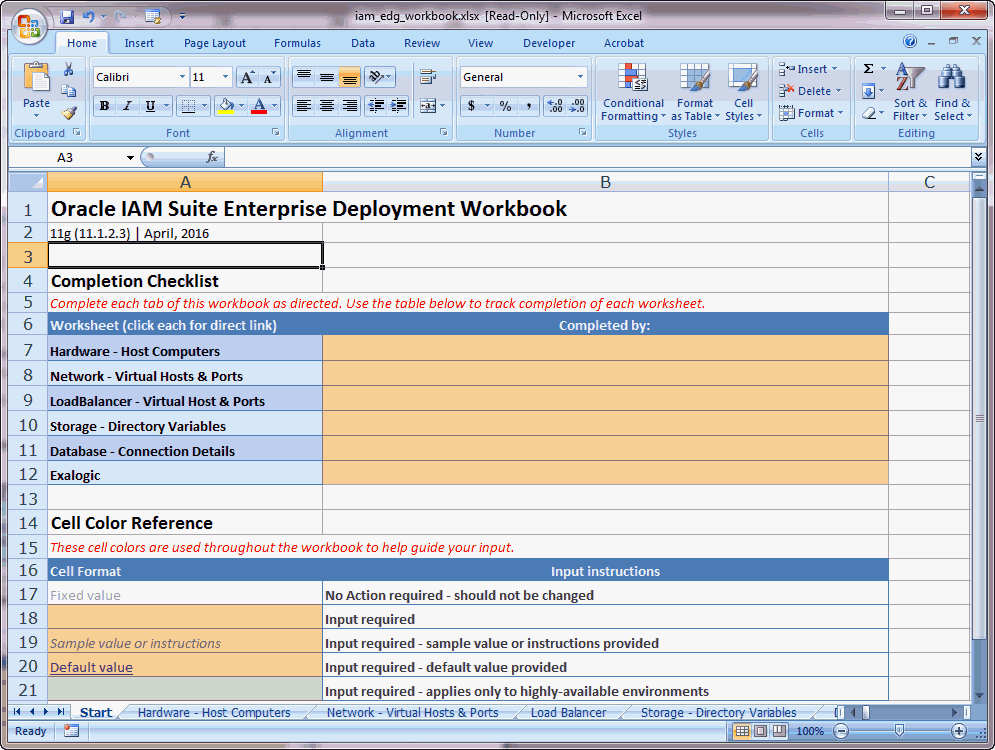
Using the Start Tab
The Start tab of the Enterprise Deployment Workbook serves as a table of contents for the rest of the workbook. You can also use it to identify the people who will be completing the spreadsheet.
The Start tab also provides a key to identify the colors used to identify workbook fields that need values, as well as those that are provided for informational purposes.
Figure 5-1 shows the Start tab of the spreadsheet.
Figure 5-1 Start Tab of the Oracle Identity and Access Management Enterprise Deployment Workbook
Description of "Figure 5-1 Start Tab of the Oracle Identity and Access Management Enterprise Deployment Workbook"
Using the Hardware - Host Computers Tab
The Hardware - Host Computers tab lists the host computers required to install and configure the Oracle Identity and Access Management Enterprise Deployment Topology.
The reference topologies described in About the Primary and Build-Your-Own Enterprise Deployment Topologies require a minimum of six host computers: two for the Web tier, two for the application tier, and two for the Oracle RAC database on the data tire.
A common deployment model typically uses 10 servers however. These being made up of: 2 for the Web Tier, 2 for the Access Components Application Tier, 2 for the Governance Components Application Tier, 2 For the LDAP servers and 2 for the RAC database servers. If you decide to expand the environment to include more systems, add a row for each additional host computer.
The Abstract Host Name is the name used throughout this guide to reference the host. For each row, procure a host computer, and enter the Actual Host Name.
For example, if a procedure in this guide references OAMHOST1, you can then replace the OAMHOST1 variable with the actual name provided on the Hardware - Host Computers tab of the workbook.
About Multi-Networked Host Computers
If you are deploying on a multi-networked host, the real host name may not be attached to the network on which you wish communication to occur. If the network you wish to use for communication is different from that attached to the Real Host Name, then you can override this by providing a different Listen Address Host Name, which is attached to the network you wish to use. Most platform deployments do not require a different Listen Host Name, however the majority of Exalogic Deployments do.
A typical example would be where the real host name is attached to the management network but network communication should happen through a client network or in the case of Exalogic the internal IPoIB network.
Using the Spreadsheet in a Consolidated Deployment
If you are using a consolidated deployment, where you have larger machines, then you can use the same host name for multiple entries in the spreadsheet.
For example, if you wish to deploy Access and Governance onto the same host then both OAMHOST1 and OIMHOST1 can be set to iamserver1, and both OAMHOST1 and OIMHOST2 can be set to iamserver2.
When you see OAMHOST1 or OIMHOST2 referenced in the guide, you'll know to replace them with the value of iamserver1 or iamserver2.
Including Additional Host Details
For easy reference, Oracle also recommends that you include the IP address, Operating System (including the version), number of CPUs, and the amount of RAM for each host. This information can be useful during the installation, configuration, and maintenance of the enterprise deployment.
Using the Network - Virtual Hosts & Ports Tab
The Network - Virtual Hosts & Ports tab lists the virtual hosts that must be defined by your network administrator before you can install and configure the enterprise deployment topology.
The port numbers are important for several reasons. You must have quick reference to the port numbers so that you can access the management consoles; the firewalls must also be configured to allow network traffic through specific ports.
Each virtual host, virtual IP address, and each network port serves a distinct purpose in the deployment. See Preparing the Load Balancer and Firewalls for an Enterprise Deployment.
In the Network - Virtual Hosts table, review the items in the Abstract Virtual Host or Virtual IP Name column. These are the virtual host and virtual IP names that are used in the procedures in this guide. For each abstract name, enter the actual virtual host name that is defined by your network administrator. Whenever this guide references one of the abstract virtual host or virtual IP names, replace that value with the actual corresponding value in this table.
Similarly, in many cases, this guide assumes that you are using default port numbers for the components or products you install and configure. However, in reality, you are likely to use different port numbers. Use the Network - Port Numbers table to map the default port values to the actual values that are used in your specific installation.
Using the Load Balancer Tab
The Load Balancer tab lists the virtual hosts your network administrator must create on your hardware load balancer before you can install and configure the Oracle IAM enterprise deployment topology.
The ports you specify in this section are the ports on the load balancer. They need not be the same as the target ports you are directing traffic to.
Each virtual host, virtual IP address, and each network port serves a distinct purpose in the deployment.
The Virtual Hosts are separated out to provide maximum flexibility. It is however acceptable to combine the multiple virtual hosts of the same type.
In the Load Balancer - Virtual Hosts table, review the items in the Abstract Virtual Host or Virtual IP Name column. These are the virtual host and virtual IP names used in the procedures in this guide. For each abstract name, enter the actual virtual host name defined by your network administrator. Whenever this guide references one of the abstract virtual host or virtual IP names, replace that value with the actual corresponding value in this table.
Similarly, in many cases, this guide assumes you are using default port numbers for the components or products you install and configure. However, in reality, you will likely have to use different port numbers. Use the Load Balancer - Port Numbers table to map the default port values to the actual values used in your specific installation.
The Load Balancer Pool configuration combines information that you enter in this tab with information entered in the Hardware and Network tabs to provide a summary of how the load balancer pools should be configured.
Using the Storage - Directory Variables Tab
As part of preparing for an enterprise deployment, it is assumed you are using a standard directory structure, which is recommended for Oracle enterprise deployments.
In addition, procedures in this book reference specific directory locations. Within the procedures, each directory is assigned a consistent variable, which you should replace with the actual location of the directory in your installation.
For each of the directory locations listed on this tab, provide the actual directory path in your installation.
In addition, for the application tier, it is recommended that many of these standard directories be created on a shared storage device. For those directories, the table also provides fields so you can enter the name of the shared storage location and the mount point that is used when you mounted the shared location. See Preparing the File System for an Enterprise Deployment.
Using the Database - Connection Details Tab
When you are installing and configuring the enterprise deployment topology, you will often have to make connections to a highly available Oracle Real Application Clusters (RAC) database. In this guide, the procedures reference a set of variables that identify the information you will need to provide to connect to the database from tools, such as the Configuration Wizard and the Repository Creation Utility.
To be sure you have these values handy, use this tab to enter the actual values for these variables in your database installation.
An Oracle Identity and Access Management installation can use more than one database if desired. This is typically the case where you wish to use a Multi Data Center deployment. It is perfectly acceptable however, to use a single database.
If you are using a single database, you must still use a different RCU prefix for artefacts belonging to each separate domain Access and Governance.
Using the LDAP - Users and Groups Tab
When you are installing and configuring the enterprise deployment topology, you will need to create users and groups to be imported into the OUD server. These users and groups are required for populating the LDAP server for the various Oracle Access Manager and Oracle Identity Governance applications.
To be sure you have these values handy, use the LDAP - Users and Groups tab to enter the actual values for these variables in your LDAP installation and configuration.