11 Preparing the Oracle Cloud Infrastructure for an Enterprise Deployment
If you plan to deploy Identity and Access Management on Oracle Cloud Infrastructure (OCI), you have to configure OCI to facilitate the deployment. Create the required OCI components to perform the deployment.
Note:
The instructions provided in this guide are correct at the time of publishing. Due to the evolving nature of the OCI interface, you may find minor changes in the options. See the Oracle Cloud Infrastructure documentation to obtain the latest steps.- About the OCI Deployment
It is important to understand the OCI components that you require to deploy Oracle Identity and Access Management on OCI. - Creating an SSH Key Pair
You must create an SSH key pair in order to connect to the bastion node, compute instances, and database hosts - Creating an OCI Compartment
Create a container in your OCI tenancy to hold the deployment. - Creating OCI Networking
Create the network components in your OCI tenancy for the deployment. - Creating Compute Instances
Create the compute instances in your OCI tenancy for the deployment. - Creating File Systems and Mount Targets
You need to create NFS file systems for Persistent Volumes and Oracle HTTP Server installations. - Creating Load Balancers
You need to create two OCI load balancers. One of these load balances is used to direct public traffic and the other for internal call backs. The load balancer used for internal traffic is not available outside the OCI container. - Creating a Database
You must create a database to store all the schema information for Oracle Identity Management. - Creating a DNS Server
It is important that all host names are resolvable, including the load balancer virtual hosts. You can make them resolvable by adding entries to the local hosts files. However, in OCI, using a private DNS server is the simpler method. - Validating Your Environment
Perform checks to ensure that your environment is ready for a deployment.
Parent topic: Preparing for an Enterprise Deployment
About the OCI Deployment
It is important to understand the OCI components that you require to deploy Oracle Identity and Access Management on OCI.
This illustrations below shows all the required OCI components. It shows the different network requirements and how the OCI components fit into those networks. Each subnet is protected by security lists.
Figure 11-1 An Illustration of the OCI Layout in an End to End SSL Topology
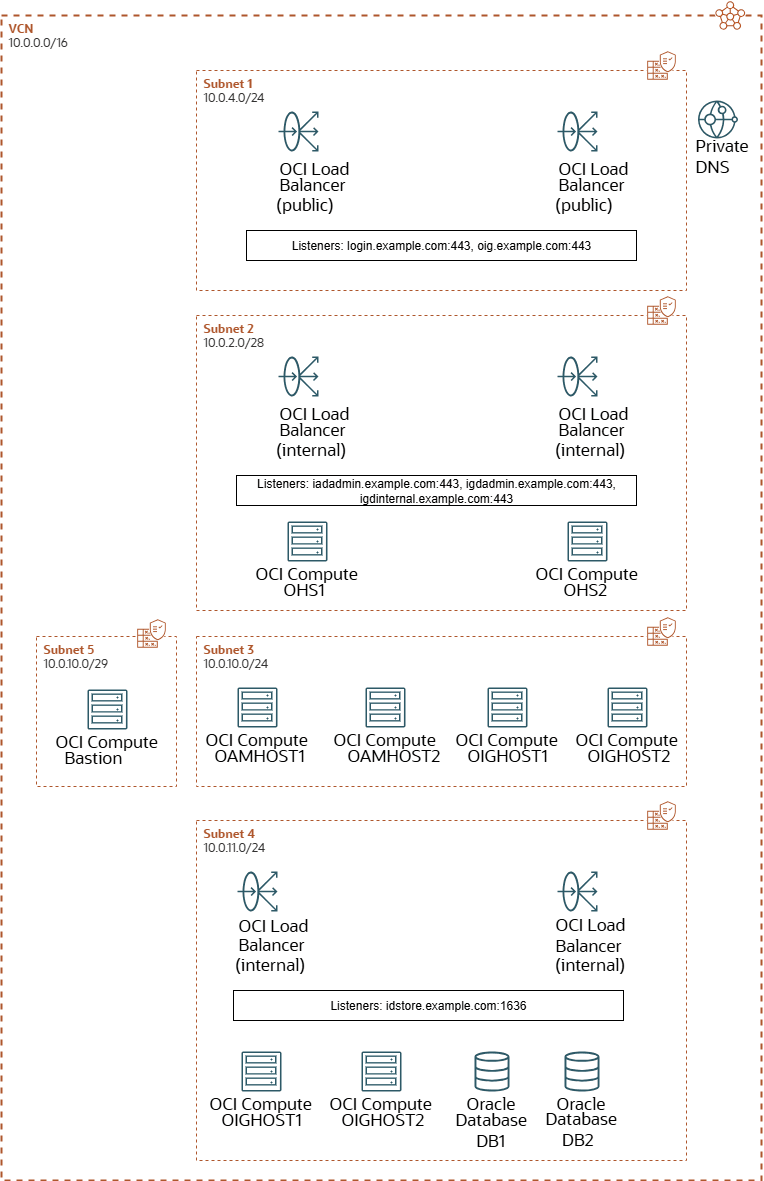
Figure 11-2 An Illustration of the OCI Layout in a SSL Terminated Topology
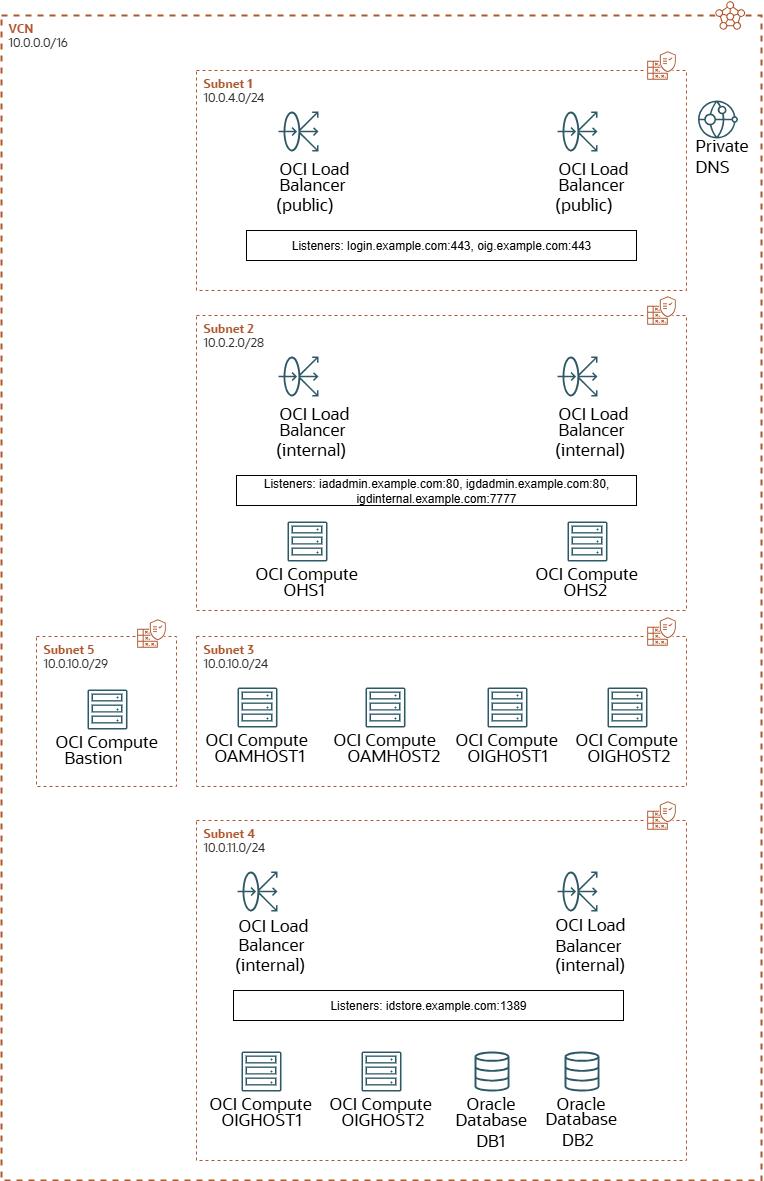
- VCN: There will be one public Virtual Cloud Network which provides external access to the environment. For security reasons, the VCN is broken down into a several subnets.
- Subnets: The VCN is divided into several subnets to ensure that the network traffic is routed only to the areas requiring it. For instance, traffic to the database subnet will not be available directly from the internet. Traffic is available only to the Application tier, which interacts with the database subnet.
- Security Lists: Security lists provide an additional layer of security that allows traffic only into and out of a subnet, based on the ports and protocols permitted.
- Bastion Node: The Bastion node is a compute instance inside the VCN that you can log in to. The Bastion node can communicate with all the components inside the deployment. The Bastion node is used for setting up the environment and for ongoing management. Therefore, you must lock down access to the Bastion node to ensure that it is accessed only by clients on your corporate network who are registered with it using an SSL key pair.
- Load balancer: The three LBaaS services are created within the OCI framework. The public-facing load balancer is used to access the Oracle Identity and Access Management deployment from the internet. The private load balancers are for internal traffic and routing it is not available outside of the VCN. The public load balancer is the only internet-facing part of your deployment (except for the Bastion node).
- Compute Instances: You require a minimum of two compute instances to host your Oracle HTTP servers. These are placed into a demilitarized zone (DMZ) below the load balancers. The load balancers send requests to the OHS servers which pass traffic onto the applications residing in the application compute instances.You require a minimum of two compute instances for your applications. For example, two compute Instances for OAM, two compute instances for OIG and two compute instances for LDAP.
- Database: The database(s) are present in a dedicated subnet.
- DNS: The DNS server is optional. It is used internally to provide name resolution. You can achieve name resolution by maintaining entries in the individual host files.
The following sections describe the procedure to set up the components depicted in this illustration:
Creating an SSH Key Pair
You must create an SSH key pair in order to connect to the bastion node, compute instances, and database hosts
You can configure OCI by using the Oracle Cloud Console and a bastion node. The SSL certificates provide a secure access to the bastion node, compute instances, and database hosts. You have to create an SSL certificate on the host you use to configure OCI. This host could be a laptop or a desktop.
After you create the certificate on the device, share it with the OCI resources to enable access to the resources and to manage them. If you use more than one device, you have to register the SSL keys for all those devices.
If you do not have an SSL certificate for the device you are using, create the cetificate using the following command:
ssh-keygen -t rsa -N "" -b 2048 -f id_rsaThis command creates two files id_rsa and
id_rsa.pub in the .ssh directory under the
home directory. These are the certificate files you will use to access the OCI
resources.
Creating an OCI Compartment
Create a container in your OCI tenancy to hold the deployment.
- Log in to the Oracle Cloud Infrastructure Console, select Identity and Security, and then select Compartments under Identity.
- Click Create Compartment.
- Specify a Name and Description.
- Click Create Compartment.
Creating OCI Networking
Create the network components in your OCI tenancy for the deployment.
Creating an Oracle Virtual Cloud Network
These steps will create a public and private subnet.
Parent topic: Creating OCI Networking
Creating Gateways
You need to create a gateway to allow data to flow from one network to another. Gateways serve as an entry and exit point for a network as all data going outside of a network must pass through it. As the name suggests it acts as a gate between two networks.
- Internet Gateway: Used to access the internet from a VCN (say, network) in OCI. It supports connections initiated from within the VCN (egress) and connections initiated from the internet (ingress).
- NAT Gateway: Used to provide resources without public IP addresses, access to the Internet without exposing these resources to the incoming internet connections.
- Service Gateway: Gives resources in your VCN and on-premises network, private access to multiple Oracle services within OCI without the traffic going over the internet. Any traffic from your VCN that is destined for one of the supported public services uses the instance’s private IP address for routing, travels over the Oracle Cloud Infrastructure network fabric, and never traverses the internet.
- Dynamic Routing Gateway (DRG): Used to connect to your existing on-premises network to your VCN. A DRG provides a single point of entry for remote network paths coming into the VCN. It provides a path for VCNs to communicate across regions or outside the region to On-premise. Each VCN can have a single DRG.
To create the required gateways:
Parent topic: Creating OCI Networking
Creating Security Lists
You need to create security lists which enable different subnets to communicate with each other.
This section describes the minimum steps you need to perform to enable this access. You should harden your security lists to ensure that only certain machines/networks have access to this node. This part is outside the scope of this guide.
Required Security Lists
You need to create security lists which enable the OCI components to communicate with each other across different subnets and where necessary the internet.
The following tables show the security lists that need to be created.
bastion-private-seclist
Table 11-1 Description of Ingress and Egress Rules for Security List bastion-private-seclist
| Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Destination Port Range |
|---|---|---|---|---|---|
|
Ingress |
CIDR |
10.0.1.0/29 |
TCP SSH Connections |
22 |
|
|
Ingress |
CIDR |
10.0.1.0/29 |
ICMP |
||
|
Egress |
CIDR |
0.0.0.0/0 |
All Protocols |
Note:
10.0.1.0 is the subnet you will use for the bastion node. You can change this value if required.bastion-public-seclist
Table 11-2 Description for Ingress and Egress Rules for Security List bastion-public-seclist
| Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Destination Port Range | Type |
|---|---|---|---|---|---|---|
|
Ingress |
CIDR |
0.0.0.0/0 |
TCP |
22 |
||
|
Ingress |
CIDR |
10.0.1.0/29 |
ICMP |
3 |
||
|
Egress |
CIDR |
0.0.0.0/0 |
All Protocols |
Note:
10.0.1.0 is the subnet you will use for the bastion node. You can change this value if required. Unless otherwise stated, leave the values blank.setup-seclist
During the set up of Oracle Identity and Access Management, the bastion node requires access to some of the services that get created as part of the build process. The access is not required after the build process is complete. For manageability reasons, a separate security list is created for this purpose. This way, after the setup is complete, you just have to remove the security list from the subnet. If further setups are required, you can add as needed.
- Private subnet for Node Manager
- db-subnet
Table 11-3 Description for Ingress Rules for Security List setup-seclist
| Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Source Port Range | Destination Port Range - SSL Terminated | Destination Port Range - End to End SSL | Comment |
|---|---|---|---|---|---|---|---|---|
|
Ingress |
CIDR |
10.0.1.0/29 |
TCP |
7001 |
9002 and 7002 |
OAM Administration Server |
||
|
Ingress |
CIDR |
10.0.10.0/24 |
TCP |
111 |
111 |
|||
|
Ingress |
CIDR |
10.0.10.0/24 |
TCP |
2048-2050 |
2048-2050 |
|||
|
Ingress |
CIDR |
10.0.10.0/24 |
UDP |
111 |
111 |
|||
|
Ingress |
CIDR |
10.0.10.0/24 |
UDP |
2048 |
2048 |
|||
|
Ingress |
CIDR |
10.0.1.0/29 |
TCP |
1389 |
1636 |
LDAP Connections |
||
|
Ingress |
CIDR |
10.0.2.0/24 |
TCP |
111 |
111 |
|||
|
Ingress |
CIDR |
10.0.2.0/24 |
TCP |
2048-2050 |
2048-2050 |
|||
|
Ingress |
CIDR |
10.0.2.0/24 |
UDP |
111 |
111 |
|||
|
Ingress |
CIDR |
10.0.2.0/24 |
UDP |
2048 |
2048 |
|||
|
Egress |
CIDR |
10.0.2.0/24 |
TCP |
111 |
111 |
|||
|
Egress |
CIDR |
10.0.2.0/24 |
TCP |
2048-2050 |
2048-2050 |
|||
|
Egress |
CIDR |
10.0.2.0/24 |
UDP |
111 |
111 |
|||
|
Egress |
CIDR |
10.0.2.0/24 |
UDP |
2048-2050 |
2048-2050 |
Note:
The destination ports listed above are dependent on the values you provide to your installation. Sample values will be used for consistency within this guide.
app-seclist
Table 11-4 Description for Ingress Rules for Security List app-seclist
| Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Destination Port Range - SSL Terminated | Destination Port Range - End to End SSL | Type | Code | Comment |
|---|---|---|---|---|---|---|---|---|---|
|
Ingress |
CIDR |
10.0.10.0/24 |
All protocols |
||||||
|
Ingress |
CIDR |
10.0.0.0/28 |
ICMP |
3 |
4 |
||||
|
Ingress |
CIDR |
0.0.0.0/0 |
TCP |
22 |
22 |
SSH Connections |
|||
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
9002 |
OAM Admin Server Secure Port |
||||
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
7001 |
7002 |
OAM Admin Server Port |
|||
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
14100 |
14101 |
OAM Server Port |
|||
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
14150 |
14151 |
OAM Policy Manager Port |
|||
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
9102 |
OIG Admin Server Secure Port |
||||
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
7101 |
9102, 7102 |
OIG Admin Server Port |
|||
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
14001 |
14002 |
OIG OIM Port |
|||
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
7003 |
7004 |
OIG SOA Port |
|||
|
Ingress |
CIDR |
10.0.10.0/24 |
TCP |
5556 |
5556 |
Node Manager |
|||
|
Ingress |
CIDR |
10.0.10.0/24 |
TCP |
All |
All |
All communication within the subnet |
|||
|
Egress |
CIDR |
10.0.10.0/24 |
All protocols |
||||||
|
Egress |
CIDR |
10.0.0.0/28 |
TCP |
6433 |
|||||
|
Egress |
CIDR |
10.0.0.0/28 |
TCP |
12250 |
|||||
|
Egress |
CIDR |
10.0.0.0/28 |
ICMP |
3 |
4 |
||||
|
Egress |
CIDR |
10.0.11.0/24 |
TCP |
1521 |
1521 |
Database Connections |
|||
|
Egress |
Service |
All Services in Oracle Service Network |
TCP |
443 Loadbalancer |
public-lbr-seclist
This security list determines who can access the load balancer and where the load balancer is allowed to send requests.
Table 11-5 Description for Ingress Rules for Security List public-lbr-seclist
| Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Destination Port Range - SSL Terminated | Destination Port Range - End to End SSL | Comment |
|---|---|---|---|---|---|---|---|
|
Ingress |
CIDR |
0.0.0.0/0 |
TCP |
80 |
80 |
HTTP requests from anywhere |
|
|
Ingress |
CIDR |
0.0.0.0/0 |
TCP |
443 |
443 |
HTTPS requests from anywhere |
|
|
Egress |
CIDR |
10.0.2.0/28 |
TCP |
7777 |
Oracle HTTP Server. Only for SSL terminated environments. |
||
|
Ingress |
CIDR |
10.0.10.0/24 |
- |
TCP |
1389 |
1636 |
Application Tier LDAP calls |
|
Ingress |
CIDR |
10.0.11.0/24 |
- |
TCP |
1389 |
1636 |
Database Tier LDAP calls |
|
Egress |
CIDR |
- |
10.0.2.0/28 |
TCP |
80,443,7777 |
4443-4449 |
Oracle HTTP Server calls |
storage-seclist
Create a security list for the OHS mount target.
Table 11-6 Description for Ingress Rules for Security List storage-seclist
| Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Source Port Range | Destination Port Range |
|---|---|---|---|---|---|---|
|
Ingress |
CIDR |
10.0.10.0/24 |
TCP |
111 |
||
|
Ingress |
CIDR |
10.0.10.0/24 |
TCP |
2048-2050 |
||
|
Ingress |
CIDR |
10.0.10.0/24 |
UDP |
111 |
||
|
Ingress |
CIDR |
10.0.10.0/24 |
UDP |
2048 |
||
|
Ingress |
CIDR |
10.0.1.0/29 |
TCP |
111 |
||
|
Ingress |
CIDR |
10.0.1.0/29 |
TCP |
2048-2050 |
||
|
Ingress |
CIDR |
10.0.1.0/29 |
UDP |
111 |
||
|
Ingress |
CIDR |
10.0.1.0/29 |
UDP |
2048 |
||
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
111 |
||
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
2048-2050 |
||
|
Ingress |
CIDR |
10.0.2.0/28 |
UDP |
111 |
||
|
Ingress |
CIDR |
10.0.2.0/28 |
UDP |
2048 |
||
|
Egress |
CIDR |
10.0.10.0/24 |
TCP |
111 |
||
|
Egress |
CIDR |
10.0.10.0/24 |
TCP |
2048-2050 |
||
|
Egress |
CIDR |
10.0.10.0/24 |
UDP |
111 |
||
|
Egress |
CIDR |
10.0.1.0/29 |
TCP |
111 |
||
|
Egress |
CIDR |
10.0.1.0/29 |
TCP |
2048-2050 |
||
|
Egress |
CIDR |
10.0.1.0/29 |
UDP |
111 |
||
|
Egress |
CIDR |
10.0.2.0/28 |
TCP |
111 |
||
|
Egress |
CIDR |
10.0.2.0/28 |
TCP |
2048-2050 |
||
|
Egress |
CIDR |
10.0.2.0/28 |
UDP |
111 |
db-seclist
Create a security list for the Database.
Table 11-7 Description for Ingress Rules for Security List db-seclist
| Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Destination Port Range - SSL Terminated | Destination Port Range - End to End SSL | Comment |
|---|---|---|---|---|---|---|---|
|
Ingress |
CIDR |
0.0.0.0/0 |
TCP |
22 |
SSH Calls |
||
|
Ingress |
CIDR |
10.0.11.0/24 |
TCP |
1521 |
|||
|
Ingress |
CIDR |
10.0.11.0/24 |
TCP |
6200 |
|||
|
Ingress |
CIDR |
10.0.10.0/24 |
TCP |
1521 |
|||
|
Ingress |
CIDR |
10.0.10.0/24 |
TCP |
6200 |
|||
|
Ingress |
CIDR |
10.0.10.0/24 |
TCP |
1389 |
1636 |
||
|
Ingress |
CIDR |
10.0.11.0/24 |
TCP |
1389 |
1636 |
||
|
Ingress |
CIDR |
10.0.11.0/24 |
TCP |
4444 |
4444 |
OUD Administration Port |
|
|
Ingress |
CIDR |
10.0.11.0/24 |
TCP |
8989 |
8989 |
OUD Replication Port |
|
|
Ingress |
CIDR |
10.0.1.0/29 |
TCP |
1521 : |
Used for set up only | ||
|
Egress |
CIDR |
0.0.0.0/0 |
All Protocols |
web-seclist
To be assigned to web-subnet (just adding this from review comment so I can add to relevant section later)
Table 11-8 Description for Ingress Rules for Security List web-seclist
| Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Destination Port Range |
|---|---|---|---|---|---|
|
Ingress |
CIDR |
0.0.0.0/0 |
TCP |
22 |
|
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
111 |
|
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
2048-2050 |
|
|
Ingress |
CIDR |
10.0.2.0/28 |
UDP |
111 |
|
|
Ingress |
CIDR |
10.0.2.0/28 |
UDP |
2048 |
|
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
4445-4449 |
|
|
Ingress |
CIDR |
10.0.4.0/24 |
TCP |
4445-4449 |
|
|
Egress |
CIDR |
10.0.2.0/28 |
TCP |
111 |
|
|
Egress |
CIDR |
10.0.2.0/28 |
TCP |
2048-2050 |
|
|
Egress |
CIDR |
10.0.2.0/28 |
UDP |
111 |
|
|
Egress |
CIDR |
10.0.2.0/28 |
UDP |
2048 |
Parent topic: Creating Security Lists
Creating the Required Security Lists
To create the security lists in Required Security Lists:
Parent topic: Creating Security Lists
Creating Route Tables
Required Route Tables
The following table shows the route tables that need to be created.
Table 11-9 Description of Route Tables
| Name | Target Type | Destination CIDR Block / Destination Service | Target Internet Gateway |
|---|---|---|---|
|
bastion-route-table |
Internet Gateway |
0.0.0.0/0 |
Internet Gateway |
|
lbr-route-table |
Internet Gateway |
0.0.0.0/0 |
Internet Gateway |
|
web-route-table |
Service Gateway |
All Services in Oracle Services Network |
Service Gateway |
|
db-route-table |
Service Gateway |
All Services in Oracle Services Network |
Service Gateway |
|
app-route-table |
Service Gateway |
All Services in Oracle Services Network |
Service Gateway |
Parent topic: Creating Route Tables
Creating the Required Route Tables
To create the route tables in Required Route Tables:
Parent topic: Creating Route Tables
Creating Subnets
Required Subnets
The following table shows the subnets that need to be created.
Table 11-10 Description of Subnets
| Name | Subnet Type | IPv4 CIDR Block | Route Table | Subnet Access | Security Lists |
|---|---|---|---|---|---|
|
bastion-subnet |
Regional |
10.0.1.0/29 |
bastion-route-table |
Public |
bastion-public-seclist setup-seclist |
|
app-subnet |
Regional |
10.0.10.0/24 |
app-route-table |
Private |
bastion-private-seclist app-seclist storage-seclist web-seclist setup-seclist |
|
web-subnet |
Regional |
10.0.2.0/28 |
web-route-table |
Private |
web-seclist storage-seclist setup-seclist |
|
db-subnet |
Regional |
10.0.11.0/24 |
db-route-table |
Private |
db-seclist setup-seclist storage-seclist |
|
lbr-subnet |
Regional |
10.0.4.0/24 |
lbr-route-table |
Public |
public-lbr-seclist |
Note:
setup-seclist is only required during initial setup.Parent topic: Creating Subnets
Creating the Required Subnets
To create the subnets in Required Subnets:
Parent topic: Creating Subnets
Creating Compute Instances
Create the compute instances in your OCI tenancy for the deployment.
Required Compute Instances
The following table shows the compute instances that need to be created.
Table 11-11 Compute Instances to Create
| Name | Min CPUs | Min Memory (GB) | Subnet | Public IP Address |
|---|---|---|---|---|
|
bastion |
1 |
8 |
bastion-subnet |
Yes |
|
webhost1 |
1 |
16 |
web-subnet |
No |
|
webhost1 |
1 |
16 |
web-subnet |
No |
|
oamhost1 |
4 |
32 |
app-subnet |
No |
|
oamhost2 |
4 |
32 |
app-subnet |
No |
|
oighost1 |
4 |
32 |
app-subnet |
No |
|
oighost2 |
4 |
32 |
app-subnet |
No |
|
ldaphost1 |
2 |
16 |
db-subnet |
No |
|
ldaphost2 |
2 |
16 |
db-subnet |
No |
Parent topic: Creating Compute Instances
Creating the Required Compute Instances
To create the compute instances in Required Compute Instances:
The summary screen displays the IP addresses assigned to the compute instance. Make a note of this address. You will need it for connecting to the node.
Parent topic: Creating Compute Instances
Assigning a Secondary IP Address to a Compute Instance
In an Enterprise deployment you need to assign an additional IP address to the hosts OAMHOST1 and OIGHOST1.
This IP address is used for Admin Server Failover. The Admin Server listens on this secondary IP address. If the host to which the IP address becomes unavailable, the IP address can be assigned to a different host and the admin server is started there.
Before you can add a secondary IP address, you need to look for an IP address in the same subnet as the main IP address that is not being used. For example, if the IP address of your OAMHOST1 is 10.0.10.96 then you may see that IP address 10.0.10.97 is not being used, and this can therefore be used as a Virtual IP address.
To add the Virtual IP address to the network card, perform the following steps:
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- Select Compute and click Instances.
- Click on the Compute instance you want to add the IP address to, for example OAMHOST1.
- Select the Networking tab.
- Click on the VNIC listed in the Attached VNICs. This will most likely have the same name as the compute instance.
- In the VNIC Information select the IP administration tab.
- In IPv4 Addresses, click Assign Secondary IP Address
- Enter the IP Address you wish to add and a hostname.
- Click Assign.
- Repeat the above steps for OIGHOST1.
Parent topic: Creating Compute Instances
Connecting to a Compute Instance
You can now connect to the compute instances using the following SSH command:
ssh -i id_rsa opc@IPAddressAlternatively, if you are using SSH agent forwarding, which enables you to use your local SSH keys instead of leaving the keys (without passphrases) on the server, then you can use the following command:
ssh -A opc@IPAddressXQuartz for MacOS. You will then
need to connect as the oracle user, for
example:ssh -AX oracle@IPAddressParent topic: Creating Compute Instances
Configuring the Compute Instances (General)
After creating the compute instances, you need to configure them.
You must perform the following steps on all the compute instances unless otherwise stated:
- Installing X11 and Additional Packages
- Enabling X11 Forwarding
- Editing Compute Instance Fault Domain
- Creating a Software Owner Account
- Creating Local Directories
- Creating Mount Points for Shared Storage
- Preparing the Compute Instance
- Using the Firewall
Parent topic: Creating Compute Instances
Installing X11 and Additional Packages
In order to install the Identity Management products on the compute notes, you must install some Linux packages on all the compute nodes (LDAPHOSTn, OAMHOSTn, OIGHOSTn, WEBHOSTn).
Run the following command to install the packages on each of the compute nodes:
sudo yum install -y libXrender libXtst xauth xterm nc gtk3* at-spi2-cor* libXScrnSaver* libnotify* openldap* javasudo yum install -y xorg-x11* libaio-devel* gcc-c++-* ksh* libnsl* xorg-x11-utils* libstdc++-devel sysstat* Parent topic: Configuring the Compute Instances (General)
Enabling X11 Forwarding
Parent topic: Configuring the Compute Instances (General)
Editing Compute Instance Fault Domain
Parent topic: Configuring the Compute Instances (General)
Creating a Software Owner Account
It is not good practice to install the Oracle software using the OPC user. It is better to create a custom user to own the software. You can create a custom user by running the following commands:
sudo adduser -u 1001 oracle
sudo groupadd -g 1002 oinstall
sudo usermod -a -G oinstall oracle
sudo usermod -g oinstall oracleParent topic: Configuring the Compute Instances (General)
Creating Local Directories
If your deployment requires the use of local directories, for example local binaries, local instance/domain files or certificates, then create local directories.
If you are using /u02 as described in this Enterprise Deployment
Guide, you will need to create these local directories as root and then
change the ownership to your oracle account.
sudo mkdir -p /u02/oracle/config /u02/oracle/products
sudo chown -R oracle:oinstall /u02For a list of locations to create, see Preparing the File System for an Enterprise Deployment.
Parent topic: Configuring the Compute Instances (General)
Creating Mount Points for Shared Storage
Before you can mount shared storage to a host you must pre-create the location to which it will be attached. For example:
sudo mkdir -p /u01/oracle/productssudo chown -R oracle:oinstall /u01/oracleFor a list of locations to create, see Preparing the File System for an Enterprise Deployment.
Parent topic: Configuring the Compute Instances (General)
Preparing the Compute Instance
For each compute instance you must also perform the tasks outlined in Preparing the Host Computers for an Enterprise Deployment.
Parent topic: Configuring the Compute Instances (General)
Using the Firewall
The compute instance is created using an Oracle Linux image. The image comes with a built-in firewall, which is enabled by default. Even though you have security rules defined in your network, the Linux server rejects these requests because of the built-in Linux firewall.
You can decide to use this extra firewall or rely on your OCI security rules.
Parent topic: Configuring the Compute Instances (General)
Opening the Ports in the Firewall
Parent topic: Using the Firewall
Disabling the Firewall
To disable the firewall, run the following commands:
sudo systemctl stop firewalldsudo systemctl disable firewalldParent topic: Using the Firewall
Configuring the Bastion Node
Perform the following steps to configure the bastion node:
Installing Git
Git contains sample code to deploy Oracle Fusion Middleware. Install GIT using the following command on the bastion only:
sudo yum install git -yParent topic: Configuring the Bastion Node
Setting Up the Hosts File
curl commands to the load balancer. Because the bastion node uses the private DNS, the IP addresses returned for the load balancer end points is through the internal network that the bastion host does not have access to. To get around this issue, create an entry in the bastion hosts file for each entry point that points to the public IP address of the load balancer.
Note:
You cannot perform this step until you have created the load balancers. See Creating Load Balancers.129.1.1.3 login.example.com oig.example.com iadadmin.example.com igdadmin.example.comParent topic: Configuring the Bastion Node
Configuring the OHS Nodes
Perform the following steps to configure the OHS nodes:
Parent topic: Creating Compute Instances
Preparing the Compute Instance for Use by Oracle HTTP Server
You may also need to install additional Linux packages required to install the Oracle HTTP server, as well as setting the kernel parameters. See Preparing the Host Computers for an Enterprise Deployment.
Parent topic: Configuring the OHS Nodes
Preparing the Hosts File
The nature of the networks in an OCI environment means that the Oracle HTTP Server instances will not have access to the public load balancer. This can cause issues when the Oracle HTTP Server tries to access some virtual hosts.
In later sections, you will create a public load balancer for connections from the outside world to your system. See Creating a Public Load Balancer.
You will also create a private load balancer to allow you to route requests from the private subnets to this load balancer. See Creating a Private Load Balancer.
/etc/hosts file on the web hosts, which looks as
follows:PRIVATE_LOAD_BALANCER_IP login.example.com10.0.2.7 login.example.comParent topic: Configuring the OHS Nodes
Creating File Systems and Mount Targets
You need to create NFS file systems for Persistent Volumes and Oracle HTTP Server installations.
The filesystems that you have to create are described in Shared Storage Recommendations When Installing and Configuring an Enterprise Deployment.
Overview of Preparing the File System for an Enterprise Deployment
It is important to set up your storage in a way that makes the enterprise deployment easy to understand, configure, and manage.
This chapter provides an overview of the process of preparing the file system for an enterprise deployment. Oracle recommends setting up your storage according to information in this chapter. The terminology defined in this chapter is used in the diagrams and procedures throughout the guide.
Parent topic: Creating File Systems and Mount Targets
Summary of File Systems
The following table lists a summary of the hosts and file systems to be mounted.
You have to mount the file systems to the bastion node only during the initial set up.
Table 11-12 Summary of Hosts and the File Systems to be Mounted
| Mount Host | File Systems | Exports | Mount Directories | Comments |
|---|---|---|---|---|
|
All nodes |
installers |
|
|
Used as a staging directory to temporarily store installers and patches. |
|
oamhost1 |
oamBinaries1 |
|
|
|
|
oamhost1 |
oamConfig |
|
|
|
|
oamhost2 |
oamBinaries2 |
|
|
|
|
oighost1 |
oigBinaries1 |
|
|
|
|
oighost1 |
oigConfig |
|
|
|
|
oighost2 |
oigBinaries2 |
|
|
Parent topic: Creating File Systems and Mount Targets
Creating a File System
Note:
Create a new mount target only for the first persistent volume (PV). Subsequent PVs should use the same mount target.Parent topic: Creating File Systems and Mount Targets
Setting the Mount Target Storage Reporting
When you install Oracle products, the installer checks the available disk storage. This check fails when you use an OCI file system. The system displays a message saying that there is insufficient disk space. To overcome this error, you can configure OCI to report a specified amount of free space.
Parent topic: Creating File Systems and Mount Targets
Mounting File Systems on Hosts
Each mount target has a different IP address. To determine how to mount a given file system:
Parent topic: Creating File Systems and Mount Targets
Creating Load Balancers
You need to create two OCI load balancers. One of these load balances is used to direct public traffic and the other for internal call backs. The load balancer used for internal traffic is not available outside the OCI container.
For more information about load balancers, see Getting Started with Load Balancing.
Creating a Public Load Balancer
This load balancer directs traffic from the internet to the Oracle HTTP Servers, which in turn pass on the traffic to the Application tier.
The public load balancer will send traffic to and from the user via SSL. After the traffic moves inside the OCI Virtual Network, it is sent unencrypted in an SSL terminated topology, and encrypted in an end to end SSL topology. You will need to provide your own SSL certificate or create a self-signed certificate for testing purposes.
To create a public load balancer, perform the following steps:
- Creating a Self-Signed Certificate
- Creating a Load Balancer
- Uploading Load Balancer Certificates
- Creating Host Names
- Creating Backend Sets
- Creating Listeners
- Updating the Default Listener
Parent topic: Creating Load Balancers
Creating a Self-Signed Certificate
You can create a self-signed certificate on any host which has access to the
openssl packages. The following example is from a Linux box (in
this case the bastion server was used).
A script has been provided as part of the Identity and Access Management Automation
scripts called create_lbr_certs.sh which can be used to create
self-signed certificates for the load balancer. To obtain the scripts, see Automating the Enterprise Deployment.
For more information, see Doc ID 2617046.1.
If you prefer, you can also use a certificate provided by a recognized certificate authority.
To create a self-signed certificate:
ca.crtloadbalancer.crtloadbalancer.key
Parent topic: Creating a Public Load Balancer
Uploading Load Balancer Certificates
As the load balancer routes SSL requests, you need to upload the certificates for the load balancer. If you have created a self-signed certificate, add the details of that certificate. If you have your own certificates, upload those.
To upload the certificates:
Parent topic: Creating a Public Load Balancer
Creating Host Names
Host names are used to filter the different entry points into the load balancer. You need to create a host name for each load balancer virtual host described in Summary of the Virtual Servers Required for an Enterprise Deployment.
You have to create the following host names:
login.example.comoig.example.comiadadmin.example.comigdadmin.example.comigdinternal.example.com
To create the load balancer host names:
Note:
If you want to limit the admin access to users inside the network, you should create the hostsiadadmin.example.com and
igdadmin.example.com in the private load balancer.
Parent topic: Creating a Public Load Balancer
Creating Backend Sets
In End to End SSL deployments, you need to create additional backend sets that points to each OHS virtual host as outlined below. If using SSL Terminated, you can ignore this section.
Table 11-13 End to End SSL Deployments
| Name | SSL | Healthcheck | Backends | Backend Port |
|---|---|---|---|---|
|
ohs_login |
Yes |
https:4447 |
webhost1, webhost2 |
4447 |
|
ohs_oig |
Yes |
https:4448 |
webhost1, webhost2 |
4448 |
Perform the following steps to create a backend set:
Parent topic: Creating a Public Load Balancer
Creating Listeners
You need to create a listener for each host name you have created
earlier. See Creating Host Names. The login listener has been created at the time
of creating the load balancer. See Creating a Load Balancer.
Table 11-14 SSL Terminated Deployments
| Name | Protocol | Port | SSL | Backend Set | Host Name |
|---|---|---|---|---|---|
|
login (default) |
https |
443 |
Yes |
ohs_servers |
login_hostname |
|
oig |
https |
443 |
Yes |
ohs_servers |
oig_hostname |
Table 11-15 End to End SSL Deployments
| Name | Protocol | Port | SSL | Backend Set | Host Name |
|---|---|---|---|---|---|
|
login_listener (default) |
https |
443 |
Yes |
ohs_login |
login_hostname |
|
oig_listener |
https |
443 |
Yes |
ohs_oig |
oig_hostname |
Note:
In both of the above deployments the administration URLs are not included in the public loadbalancer. This ensures that it is physically impossible to access administration functions from the internet. They are available from inside the network or via a browser running on your bastion host.Should you have a requirement to expose these end points to the internet you will need to add in extra listeners for the administration functions. Access to these URLs should however be tightly controlled via appropriate security lists.
To create the load balancer listeners:
Note:
If you want to limit the admin access to users inside the network, create the listenersiadadmin_listener and igdadmin_listener in the
private load balancer.
Parent topic: Creating a Public Load Balancer
Updating the Default Listener
When you created the load balancer, a default listener also gets created. You have to assign the newly created host name to this listener.
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- Navigate to Networking and click Load Balancers.
- Click the load balancer, for example: public-loadbalancer.
- Select the Listeners tab.
- To edit the listener, click the three dots next to the name, for example login, and then click Edit.
- Set the host name to the host name you created earlier, for example: login. See Creating Host Names.
- Click Save changes.
Parent topic: Creating a Public Load Balancer
Creating a Private Load Balancer
The private load balancer, which is used to route internal call backs, resides in the same subnet as the Oracle web servers. This load balancer services requests generated from inside the application.
Note:
Web servers issuecurl commands to
login.example.com. Therefore, you also need to define this on the
private load balancer because the web servers do not have direct access to the public
load balancer. You can use the same certificates that you used when you created the
public load balancer.
To create a private load balancer, perform the following steps:
- Creating a Load Balancer
- Creating Host Names
- Updating the Default Listener
- Uploading Load Balancer Certificates
- Creating Backend Sets
- Creating Listeners
Parent topic: Creating Load Balancers
Creating Host Names
Host names are used to filter the different entry points into the load balancer. You need to create a host name for each load balancer virtual host described in Summary of the Virtual Servers Required for an Enterprise Deployment.
igdinternal.example.comlogin.example.comiadadmin.example.comigdadmin.example.comoig.example.com
Note:
login.example.com is defined here for internal traffic routing. The EDG uses network segregation. If you do not define it here, calls to login.example.com will attempt to communicate using the public network and fail.
To create the load balancer host name:
Parent topic: Creating a Private Load Balancer
Updating the Default Listener
When you created the load balancer, a default listener also gets created. You have to assign the newly created host name to this listener.
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- Navigate to Networking and click Load Balancers.
- Click the load balancer. For example: internal_loadbalancer.
- Click on the Listeners tab.
- To edit the listener, click the three dots next to the name, and then click Edit.
- Set the host name to the host name you created earlier. For example: login. See Creating Host Names.
- Click Save changes.
Parent topic: Creating a Private Load Balancer
Uploading Load Balancer Certificates
As the load balancer routes SSL requests, you need to upload the certificates for the load balancer. If you have created a self-signed certificate, add the details of that certificate. If you have your own certificates, upload those.
To upload the certificates:
Parent topic: Creating a Private Load Balancer
Creating Backend Sets
In end to end SSL deployments, you need a backend set that points to each OHS virtual host. You have already created a backend set for login when you created the listener, you now need to create the following backend sets.
Table 11-16 End to End SSL Deployments
| Name | SSL | Healthcheck | Backends | Backend Port |
|---|---|---|---|---|
|
ohs_iadadmin |
Yes |
https:4445 |
webhost1, webhost2 |
4445 |
|
ohs_igdadmin |
Yes |
https:4446 |
webhost1, webhost2 |
4446 |
|
ohs_login (default) |
Yes |
https:4447 |
webhost1, webhost2 |
4447 |
|
ohs_oig |
Yes |
https:4448 |
webhost1, webhost2 |
4448 |
| ohs_igdinternal |
Yes |
https:4449 |
webhost1, webhost2 |
4449 |
Perform the following steps to create a backend set:
Parent topic: Creating a Private Load Balancer
Creating Listeners
You need to create a listener for each host name you have created earlier. See Creating Host Names.
Table 11-17 SSL Terminated Deployments
| Name | Protocol | Port | SSL | Backend Set | Host Name |
|---|---|---|---|---|---|
|
igdinternal_listener |
http |
7777 |
No |
ohs_servers |
|
|
login_listener (default) |
https |
443 |
Yes |
ohs_servers |
|
|
iadadmin_listener |
http |
80 |
No |
ohs_servers |
|
|
igdadmin_listener |
http |
80 |
No |
ohs_servers |
|
Table 11-18 End to End SSL Deployments
| Name | Protocol | Port | SSL | Backend Set | Host Name |
|---|---|---|---|---|---|
|
igdinternal_listener |
https |
443 |
Yes |
ohs_igdinternal |
igdinternal_hostname |
|
login_listener (default) |
https |
443 |
Yes |
ohs_login |
login_hostname |
|
oig_listener |
https |
443 |
Yes |
ohs_oig |
oig_hostname |
|
iadadmin_listener |
https |
443 |
Yes |
ohs_iadadmin |
iadadmin_hostname |
|
igdadmin_listener |
https |
443 |
Yes |
ohs_igdadmin |
igdadmin_hostname |
To create the load balancer listeners:
Parent topic: Creating a Private Load Balancer
Creating an LDAP Load Balancer
The LDAP load balancer is used to route internal LDAP requests to the LDAP Servers. It resides in the same subnet as the LDAP Servers. This load balancer services requests generated from inside the application.
To create an LDAP load balancer, perform the following steps:
Updating the Default Listener
When you created the load balancer, a default listener also gets created. You have to assign the newly created host name to this listener.
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- Navigate to Networking and click Load Balancers.
- Click the load balancer. For example: ldap_loadbalancer.
- Click on the Listeners tab.
- To edit the listener, click the three dots next to the name, and then click Edit.
- Set the host name to the host name you created earlier. For example: idstore. See Creating Host Names.
- Click Save changes.
Parent topic: Creating an LDAP Load Balancer
Creating a Database
You must create a database to store all the schema information for Oracle Identity Management.
There are several different databases that you can create in OCI. For this example, a bare metal RAC database will be created. You may need to create one or more databases.
See Preparing the Database for an Enterprise Deployment for details on the databases and services you should create. This section shows an example of creating one of these databases in OCI.
Creating the Database
After establishing the network, you can now create the database.
Note:
After the database is created, OCI adds a suffix to the database name. Ensure that you use the complete name including this suffix when configuring the database as described in Preparing the Database for an Enterprise Deployment.Parent topic: Creating a Database
Creating a Secondary Pluggable Database
When you create the database, it creates a single pluggable database (PDB). A single PDB may be sufficient for your needs.
However, if you require more PDBs so that OAM and OIG use different PDBs in the same database, you have to create additional PDBs. See Creating a PDB Using an Existing PDB as a Template.
You can do this either at the database level or, if you are using Oracle OCI, through the OCI console. For adding a PDB at the database level, see Creating a PDB Using an Existing PDB as a Template.
- Log in to the Oracle Cloud Infrastructure for your tenancy.
- Navigate to Oracle Database and click Oracle Base Database Service.
- Click the DB system hosting the database.
- Click on the Databases tab
- Click the Container Database Name from the list of displayed databases.
- Click the Pluggable Databases tab.
- Click Create.
- Add a name for the new pluggable database, for
example
oigpdb, and enter the TDE wallet password for the container database. This password may be the same as the database SYS password if you opt not to set an explicit value. - Click Create.
Parent topic: Creating a Database
Connecting to the Database Node
You can now connect to the database node using the following SSH command:
ssh -A opc@databaseNodeIPAdddressConnect to DB node 1 from the bastion node using the command:
ssh -A opc@dbnode1After you connect to DB node 1 as opc, connect to the oracle user using
the following command:
sudo su - oracleParent topic: Creating a Database
Configuring the Database
After you create the skeletal database, you should configure the database as described in Preparing the Database for an Enterprise Deployment.
Parent topic: Creating a Database
Creating a DNS Server
It is important that all host names are resolvable, including the load balancer virtual hosts. You can make them resolvable by adding entries to the local hosts files. However, in OCI, using a private DNS server is the simpler method.
By default, the compute hosts are configured to use a private DNS server. You have to add the entries only for the local hosts.
Creating DNS Records
After you create the zone, you can create records in the zone for each host. There are two types of DNS records that have to be created:
- A Record: This is an IP address association with a host name.
- CNAME: This is an alias for the A Record.
If you have multiple hosts using the same IP address, Oracle recommends you to create one 'A Record' and multiple 'CNAME' records.
To create a record:
Parent topic: Creating a DNS Server
Validating Your Environment
Perform checks to ensure that your environment is ready for a deployment.
For the bastion node
- Check the network
connectivity:
ping webhost1.example.comping webhost2.example.com - Resolve the public address of the load
balancer:
ping login.example.comping oig.example.com - Verify DNS is working by issuing the
command:
Verify that the IP address returned is that of your LDAP load balancer.nslookup idstore.example.com
From the Web Tiers
-
Verify that the web tiers can communicate with the Application compute instances, which includes the port that you communicate on.
Use the following command to check network connectivity:
or:nc -zv OAMHOSTn <PORT>nc -zv OIGHOSTn <PORT>For example, if your OAM Administration Server for OAMHOST1 is using port 9002 then the command is as follows:
nc -zv oamhost1.example.com 9002This will check that WEBHOSTn can communicate with the OAMHOST1 on port 9002 which is the secure mode port of the OAM Administration Server.
The output will be similar to the following:Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Connection refused.The Connection refused message is expected because you have not yet configured the OAM Admin Server. If the command hangs then this means that there is no pathway between the WEBHOST and the OAMHOST using port 9002. This indicates an issue with your security rules.
-
Resolve the public address of the load balancer
ping login.example.com