44 Integrating Access Manager with SAP NetWeaver Enterprise Portal
This chapter describes the integration of Access Manager 11.1.2 with SAP NetWeaver Enterprise Portal.
This chapter covers the following topics:
44.1 What is Supported in This Release?
Versions 7.0.x and 7.4.x of SAP NetWeaver Enterprise Portal are supported in this release.
Access Manager supports SAP NetWeaver Enterprise Portal v7.4.x with the following caveats:
-
Apache 2.2.x and 2.0.x (from Apache.org) are supported Web servers with this release.
-
MySAP is not certified.
Access Manager supports SAP NetWeaver Enterprise Portal v6.0 and v7.0.x with the following caveats:
-
Apache 2.0 (from Apache.org) is supported as a Web server with this release.
-
MySAP is not certified.
44.2 Supported Versions and Platforms
Access Manager supports the versions and platforms described on the following site:
http://www.oracle.com/technetwork/middleware/ias/downloads/fusion-certification-100350.html44.3 Integration Architecture
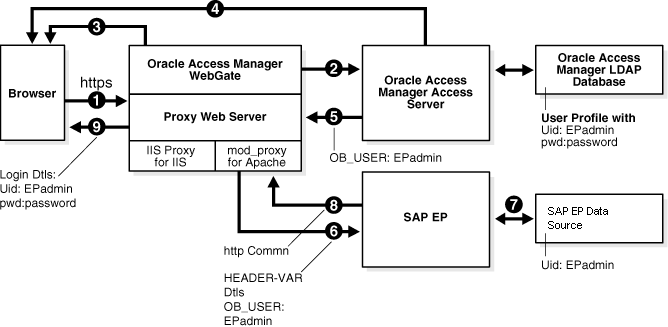
The following diagram illustrates the integration between Access Manager and SAP NetWeaver Enterprise Portal.
44.3.1 Process Overview: Integration with SAP NetWeaver Enterprise Portal
Here is an overview of the integration process with SAP NetWeaver Enterprise Portal.
-
A user attempts to access content via the SAP NetWeaver Enterprise Portal.
For example, the user may enter the following URL to access an HR application through a proxy server:
https://host:port/irj -
The WebGate intercepts the request and queries the Access Server for the security policy that determines if the resource is protected.
The security policy consists of an authentication scheme, authorization rules, and allowed operations. Based on the authentication and authorization success or failure, specified actions are performed.
The Access System security policy for the SAP
/irjlogin URL is applicable to all resources accessed using thehttps://host:port/irjURL.Note that the SAP NetWeaver Enterprise Portal has its own authorization system that can be configured to set user access to iViews.
-
If the resource is protected, the WebGate prompts the user for authentication credentials.
The credentials that the WebGate requests depend on the authentication scheme configured in the Access System, for example, Basic over LDAP or Form-based authentication.
-
If the credentials are validated, the Access System authenticates the user and sets an encrypted ObSSOCookie in the user's browser.
-
After authenticating, the authorization rules defined in the Access System are applied based on the security policy.
Specific actions are performed based on the authorization rules. If the user is authorized, access to the SAP Portal login (the requested content) is allowed. For SAP Enterprise Portal header variable integration, the Access Server sets the authenticated user ID in a header variable.
If the user is not authenticated or authorized, he or she is denied access and redirected to another URL, as determined by the administrator. For example, the user may be redirected to an "invalid credentials" page.
-
For the integration with SAP NetWeaver Enterprise Portal, the proxy Web server redirects the request to the SAP NetWeaver Enterprise Portal internal Web server that contains the header variable details.
-
The SAP NetWeaver Enterprise Portal uses the header variable value to check the mapping of the user ID against the configured data source in the portal.
Both the Access Manager and SAP NetWeaver Enterprise Portal data source must contain the same user ID value.
Upon successful mapping, SAP NetWeaver Enterprise Portal allows the user to access the requested resource.
SAP NetWeaver Enterprise Portal sends a response to the proxy, and the proxy redirects to the client browser.
-
All interaction with the SAP Enterprise Portal takes place through the proxy server.
44.4 Configuring Oracle Access Management and NetWeaver Enterprise Portal 7.0.x
You can configure Access Manager and SAP NetWeaver Enterprise Portal 7.0.x to work together.
This section contains the following tasks:
44.4.1 Before You Begin Configuring OAM and NetWeaver Enterprise Portal 7.0.x
-
Install SAP NetWeaver Enterprise Portal before completing the steps in this section.
-
Install the Apache HTTP Server by following the installation steps provided by apache.org.
-
Install and configure a WebGate on each Apache HTTP Server instance that supports the proxy connection to the SAP Enterprise Portal instance. See Installing Webgates for Oracle Access Manager for details.
-
Install Access Manager before completing the steps in Configuring Access Manager for SAP Enterprise Portal. See the Installing and Configuring Oracle Identity and Access Management for details.
-
Synchronize the time on all servers where SAP NetWeaver Enterprise Portal and Access Manager components are installed.
-
Ensure that the users exist in the Access Manager LDAP directory as well as on the SAP R3 system database.
The user ID in Access Manager and the SAP database must be the same or be mapped to each other. Any attribute in a user's profile can be configured as the SAP ID and passed directly to SAP. Alternatively, SAP can be configured to map the SAP ID to any user attribute that it receives from Access Manager.
-
Verify that the Web browser is configured to allow cookies.
Note:
Oracle suggests reviewing the following topics prior to integrating Access Manager with SAP NetWeaver Enterprise Portal.
-
Managing Data Sources to understand how to add and configure data sources in Access Manager.
-
Managing Authentication and Shared Policy Components to understand how to configure Form and Basic mode authentication in Access Manager.
-
Configuring Cert Mode Communication for Access Manager to understand how to configure Cert mode for Access Manager.
44.4.2 Configuring the Apache HTTP Server as a Proxy
You can configure a proxy (Apache HTTP Server 2.0.x) to access SAP NetWeaver Enterprise Portal.
To configure Apache HTTP Server 2.0.x
44.4.3 Configuring SAP NetWeaver Enterprise Portal for External Authentication
You can enable external authentication in SAP Enterprise Portal using the OB_USER header variable.
For more information about configuring authentication schemes for SAP Enterprise Portal, see the SAP documentation.
To configure the header variable
-
Stop the SAP J2EE dispatcher and server.
-
Browse to the following directory:
SAP_J2EE_engine_install_dir
\ume -
Back up the file
authschemes.xml.bakto another directory. -
Rename
authschemes.xml.baktoauthschemes.xml. -
Open
authschemes.xmlin an editor and change the reference of the default authentication scheme to the authentication scheme header as follows:<authscheme-refs> <authscheme-ref name="default"> <authscheme>header</authscheme> <authscheme>uidpwdlogon</authscheme> </authscheme-ref> </authscheme-refs> -
In the authentication scheme header of
authschemes.xml, specify the name of the HTTP header variable where the Access System provides the user ID.As described in "Configuring Access Manager for SAP Enterprise Portal", this is the
OB_USERheader variable. You configure this header variable as follows:<authscheme name="header"> <loginmodule> <loginModuleName> com.sap.security.core.logon.imp.HeaderVariableLoginModule </loginModuleName> <controlFlag>REQUISITE</controlFlag> <options>Header=OB_USER</options> </loginmodule> <priority>5</priority> <frontEndType>2</frontEndType> <frontEndTarget>com.sap.portal.runtime.logon.header</frontEndTarget> </authscheme>The control flag value
REQUISITEmeans the login module must succeed. If login succeeds, authentication continues through the list of login modules. If it fails, control immediately returns to the application and authentication does not continue through the list of login modules. -
Restart the portal server and J2EE engine.
The modified
authschemes.xmlfile will be loaded into the Portal Content Directory (PCD). SAP Enterprise Portal will rename it asauthschemes.xml.bak.
To Configure Logout
44.4.4 Adjusting the Login Module Stacks for using Header Variables
Add the HeaderVariableLoginModule to the appropriate login module stack or template and configure the options.
Table 44-1 Login Module Stacks for using Header Variables
| Login Modules | Flag | Options |
|---|---|---|
|
EvaluateTicketLoginModule |
SUFFICIENT |
{ume.configuration.active=true |
|
HeaderVariableLoginModule |
OPTIONAL |
{ume.configuration.active=true, Header=<header_name>} |
|
CreateTicketLoginModule |
SUFFICIENT |
{ume.configuration.active=true} |
|
BasicPasswordLoginModule |
REQUISITE |
{} |
|
CreateTicketLoginModule |
OPTIONAL |
{ume.configuration.active=true} |
To adjust the Login Module Stacks for using Header Variables
44.5 Configuring Oracle Access Management and NetWeaver Enterprise Portal 7.4.x
This section contains the following tasks.
44.5.1 Before You Begin Configuring OAM and NetWeaver Enterprise Portal 7.4.x
-
Install SAP NetWeaver Enterprise Portal version 7.4.x before completing the steps in this section.
-
Install Access Manager as described in the Installing and Configuring Oracle Identity and Access Management.
-
Install Apache HTTP Server 2.0.x or 2.2.x by following the installation steps provided by apache.org.
-
Install and configure an OAM WebGate on each Apache HTTP Server instance that supports the proxy connection to the SAP Enterprise Portal 7.4 instance. See Installing Webgates for Oracle Access Manager for details.
-
Synchronize the time on all servers where SAP NetWeaver Enterprise Portal and Access Manager components are installed.
-
Ensure that the users exist in the Access Manager LDAP directory as well as on the SAP R3 system database.
The user ID in Access Manager and the SAP database must be the same or be mapped to each other. Any attribute in a user's profile can be configured as the SAP ID and passed directly to SAP. Alternatively, SAP can be configured to map the SAP ID to any user attribute that it receives from Access Manager.
-
Verify that your Web browser is configured to allow cookies.
Note:
Oracle suggests reviewing the following topics prior to integrating Access Manager with SAP NetWeaver Enterprise Portal.
-
Managing Data Sources to understand how to add and configure data sources in Access Manager.
-
Managing Authentication and Shared Policy Components to understand how to configure Form and Basic mode authentication in Access Manager.
-
Configuring Cert Mode Communication for Access Manager to understand how to configure Cert mode for Access Manager.
44.5.2 Configuring Access Manager for SAP NetWeaver Enterprise Portal 7.4.x
You can configure the Access Manager security policy that protects SAP NetWeaver Enterprise Portal log-ins.
To configure:
-
In to the Oracle Access Management Console, click Application Security at the top of the window.
-
In the Launch Pad tab, select Create Application Domain from the Create (+) drop-down menu in the Access Manager section.
-
Complete the form to create a WebGate for this integration. For example:
Name—Type a meaningful name, for example, SAP_AG. Do not include spaces in the name.
Version - select OAM from the drop-down menu.
Access Client Password—Enter a password to be used during the installation of the WebGate.
Security—Choose the type of communication that should occur between the WebGate and the OAM server.
Click Apply.
A confirmation page opens.
-
At the bottom of the confirmation page, in the Server Lists section, associate the WebGate with a defined Access Server.
Click Apply.
-
On the Launch Pad page, go to the Access Manager section and click Host Identifiers.
Click Search, then click the WebGate in the search results.
Configure the host identifiers using the fully qualified proxy machine name and port for the Apache proxy.
-
Click Application Domains and search for the application domain name that you used to create the WebGate (for example, SAP_WG).
Click the application domain name in the search results to open it
-
Click the Resources tab and search for the resource that the WebGates should protect. Select the resource in the search results then click the Create button.
Complete the form and click Apply.
Type - HTTP
Resource URL -
/irjProtection Level - Protected
Authentication Policy - Protected Resource Policy
Authorization Policy - Protected Resource Policy
-
Click the Authentication Policies tab, then click Protected Resource Policy.
Choose the appropriate authentication scheme from the Authentication Scheme drop-down that you want to configure for this particular domain. For example, for a form-based authentication policy (FAAuthScheme), enter the following:
Name - Protected Resource Policy
Authentication Scheme - FAAuthScheme
Note:
Select either basic-over-LDAP or form-based authentication.
Oracle recommends that you use a form-based authentication scheme. If you use the basic authentication scheme, also set the Challenge Redirect field to another WebGate to ensure that the
ObSSOCookieis set.Click Apply to save your changes.
-
Click the Authorization Policies tab, then click Protected Resource Policy.
Click the Responses tab and add the following:
Type - Header
Name - OAM_REMOTE_USER
Value - Same account name
The other tabs in Authorization Policies include conditions and rules:
Condition - Creates a list of users and puts them in a group.
Rule - Allows or denies access to the group of users created in the conditions tab.
Click Apply to save your changes.
-
-
If you configured a form-based authentication scheme, ensure that a
login.htmlpage is configured in the proxy server document root.Also, ensure that a
logout.htmlpage is present on the proxy Web server document root. You can create a custom logout page using HTML, a JSP file, or a CGI protocol.The default logout page (
logout.html) is located here:WebGate_install_dir/webgate/apache/oamsso/logout.htmlWhere:
WebGate_install_diris the directory where the WebGate is installed. Ensure that the name of the logout page contains the stringlogout. -
Ensure that the user ID that is returned by the
OAM_REMOTE_USERheader variable exists in the user management data sources for SAP Enterprise 7.4. -
On the Launch Pad page, go to the Access Manager section and click Authentication Schemes.
Choose the authentication scheme to use. This is the scheme that you selected inside the application domain of the WebGate.
44.5.3 Configuring Apache Web Server 2.0.x or 2.2.x
You can configure a proxy to access SAP Enterprise Portal 7.4.
To configure:
44.5.4 Configuring SAP Enterprise Portal 7.4 for External Authentication
You can enable external authentication in SAP Enterprise Portal 7.4 using the OAM_REMOTE_USER header variable.
See the SAP Enterprise Portal 7.4 Enterprise Postal Security Guide for more information about configuring authentication schemes for SAP Enterprise Portal.
44.5.5 Adjusting the Login Module Stacks for Using Header Variables
You can use the NetWeaver Admin console to add the HeaderVariableLoginModule to the appropriate login module stack or template and configure the options.
In the console, choose Configuration > Authentication and Single Sign-On. Click Login Modules under the Authentication tab. Create the HeaderVariableLoginModule login module, with the display name as HeaderVariableLoginModule and class name as com.sap.security.core.server.jaas.HeaderVariableLoginModule. Choose Component > ticket from the Login Module Use tab, and add the login module HeaderVariableLoginModule to the login module stack for each template or application that is to support header variable authentication.
Table 44-2 Login Module Stacks for using Header Variables
| Login Modules | Flag | Options |
|---|---|---|
|
EvaluateTicketLoginModule |
SUFFICIENT |
{ume.configuration.active=true |
|
HeaderVariableLoginModule |
OPTIONAL |
{ume.configuration.active=true, Header=<header_name>} |
|
CreateTicketLoginModule |
SUFFICIENT |
{ume.configuration.active=true} |
|
BasicPasswordLoginModule |
REQUISITE |
{} |
|
CreateTicketLoginModule |
OPTIONAL |
{ume.configuration.active=true} |
44.6 Testing the Integration
You can validate the front-end and back-end integrations. using web browser.
Front-End Integration Test Procedure
Follow these steps to test the integration using a Web browser.
-
Open a protected URL. For example:
https://host:port/irjAccess Manager should prompt for authentication (either form based, or basic authentication over LDAP, or Cert Mode authentication).
-
Enter the correct user credentials.
If the credentials are correct, you will be logged into the SAP NetWeaver Enterprise Portal system.
Back-End Integration Test Procedure
To use these steps, download and install a plug-in for your Web browser that displays the HTTP requests and responses that happen when your browser requests a resource. Live HTTP Headers for Firefox, or ieHTTPHeaders for Internet Explorer are two such plug-ins.
44.7 Troubleshooting the Integration
You can troubleshoot issues with this integration.
Problem: The browser has problems displaying the SAP 7.0.x administration interface through the proxy server. You may receive an "object not found" error and related JavaScript errors.
Solution: See the following SAP document for a list of supported browsers, "SAP NetWeaver 7.0.x Product Availability Matrix."