Configure Oracle Unified Directory for Oracle Access Management 12c
Introduction
This tutorial shows you how to install and configure Oracle Unified Directory (OUD) for use with Oracle Access Management 12c.
This is the seventh tutorial in the series Getting Started with Oracle Access Management 12c. Read them sequentially.
- Getting Started with Oracle Access Management 12c Series - Overview
- Install Oracle Database for Oracle Access Management 12c
- Create an Oracle Database for Oracle Access Management 12c
- Install Oracle Access Management 12c
- Configure Oracle Access Management 12c
- Configure SSL for Oracle Access Management 12c
- Configure Oracle Unified Directory for Oracle Access Management 12c
- Install and Configure Oracle HTTP Server for Oracle Access Management 12c
- Create and Configure a WebGate
- Protect an Application Deployed in WebLogic Server with Oracle Access Management 12c
Objective
To configure Oracle Unified Directory for use with Oracle Access Management 12c.
By default Oracle Access Management 12c uses the WLS Embedded LDAP server to store identity information such as users and groups. Alternatively you can store this identity information in another LDAP Server such as Oracle Unified Directory. If you prefer to use the WLS Embedded LDAP server then skip this tutorial.
Prerequisites
To have followed Configure SSL for Oracle Access Management 12c.
Download the Oracle Unified Directory Software
- Launch your browser and navigate to Identity & Access Management Downloads.
- Under Identity Management 12cPS4 (12.2.1.4.0), click Oracle Unified Directory 12cPS4.
- In the Oracle Software Delivery Cloud page, select
Linux x86-64from the Platforms drop down list. - Click on V983402-01.zip - Oracle Fusion Middleware 12c (12.2.1.4.0) Unified Directory for (Linux x86-64). The download will begin.
- After the download is complete, move the zip file to a staging directory, for example:
/stage/OUD12cand unzip it.
Install Oracle Unified Directory in Standalone Mode
-
Launch a terminal window as oracle and run the following commands:
cd /stage/OUD12c java -jar fmw_12.2.1.4.0_oud.jar -
Follow the table below to guide you through the installation screens:
Step Window Description Choice or Values 1 Welcome Click Next 2 Auto Updates Skip Auto Updates 3 Installation Location Oracle Home: /u01/app/oracle/product/middleware/oud4 Installation Type Standalone Oracle Unified Directory Server (Managed independently of WebLogic Server) 5 Prerequisite Checks Click Next 6 Installation Summary Click Install 7 Installation Progress Click Next 8 Installation Complete Click Finish
Configure Oracle Unified Directory
-
Launch a terminal window as
oracleand enter the following command:cd /u01/app/oracle/product/middleware/oud/oud ./oud-setup -
Follow the table below to guide you through the configuration screens:
Step Window Description Choice or Values 1 Welcome Click Next 2 Server Administration Settings Instance Path: /u01/app/oracle/product/middleware/oud/asinst_1/OUD
Host Name:oam.example.com
Password:<password>
Confirm Password:<password>3 Ports Select checkbox: LDAPS: Enable on Port
Check Enable StartTLS for LDAP
Certificate:Use an Existing Certificate
Key Store Type:JKS
Key Store Path:/u01/app/oracle/admin/domains/oam_domain/keystore/oam_keystore.jks
Key Store PIN:<password>
When you see an Error stating the Key Store contains multiple certificates, click OK and from the Alias drop down list selectserver_cert.4 Topology Options Select: This will be a standalone server 5 Directory Data Select: Leave Database Empty 6 Oracle Components Integration Click Next 7 Server Tuning Click Next 8 Review Click Finish 9 Finished Click Close Note: Oracle Unified Directory will automatically start after the configuration wizard has completed. For information on stopping and starting Oracle Unified Directory see: Starting and Stopping the Server.
Import Sample Identity Data
In this section you import sample identity data that contains example users and groups that will be used in later tutorials.
-
Download the example.ldif file and move the file to
/stage/OUD12c. -
Launch a terminal window as
oracleand run the following commands to populate the OUD directory server with sample data:cd /u01/app/oracle/product/middleware/oud/asinst_1/OUD/bin ./ldapmodify -p 1389 -D "cn=Directory Manager" -w <password> -a -c -f /stage/OUD12c/example.ldif
Import the CA certificate into the JAVA_HOME keystore
-
Run the following command to import the CA certificate into the Java keystore
cacertsfile:keytool -import -v -alias oam_ca -file /stage/ssl/ca.crt -noprompt -trustcacerts -keystore $JAVA_HOME/jre/lib/security/cacerts -storepass changeitThe output will look similar to the following:
Certificate was added to keystore [Storing /u01/app/oracle/product/jdk/jre/lib/security/cacerts]
Configure OUD as the Identity Store in OAM
-
Launch a browser and access the OAM Console
https://oam.example.com:7002/oamconsole. Login asweblogic/<password>. -
Click the Configuration tab (top right), then click User Identity Stores. Click Create in the OAM ID Stores section.
-
Specify the values as shown:
- Store Name:
OUDStore - Store Type:
OUD: Oracle Unified Directory - Location:
oam.example.com:1636 - Bind DN:
cn=Directory Manager - Password:
<password> - Login ID Attribute:
uid - User Password Attribute:
userPassword - User Search Base:
ou=People,dc=example,dc=com - Group Name Attribute:
cn - Group Search Base:
ou=Groups, dc=example, dc=com - Check Enable SSL
For example:
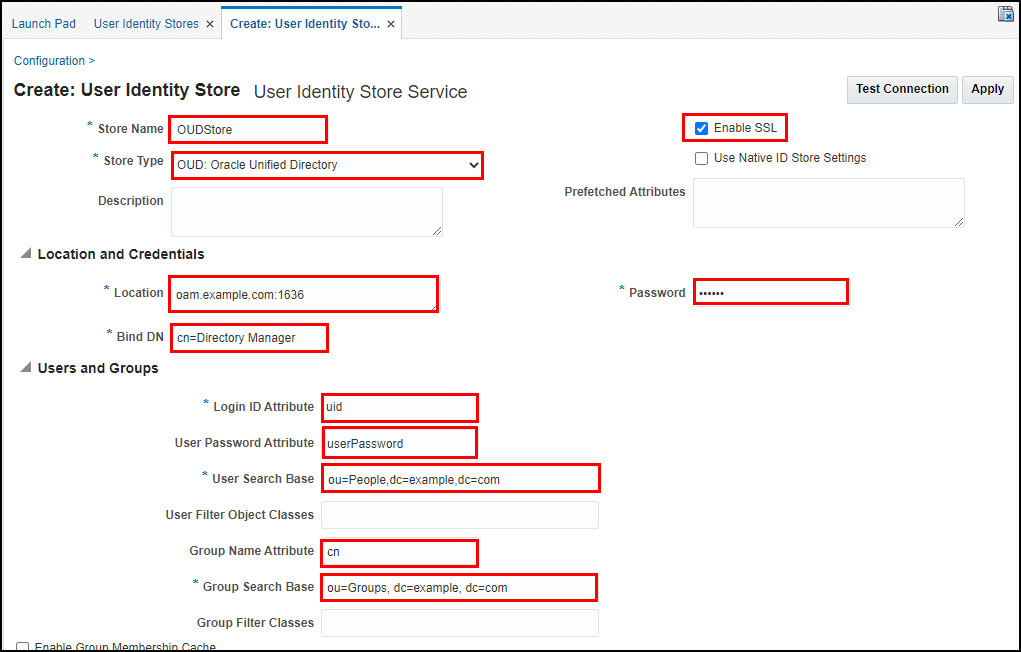
- Store Name:
-
Click Test Connection. Assuming the connection works, click OK in the Connection Status window.
-
Click Apply to save the definition.
-
Access the User Identity Stores tab, and set Default Store to
OUDStore, and then click Apply. -
Click Application Security, and then Authentication Modules under the Plug-ins tile.
-
Click Create > Create LDAP Authentication Module. Enter the following values and click Apply:
- Name:
LDAPOverOUD - User Identity Store:
OUDStore
- Name:
-
Click the Launch Pad tab, and click the Authentication Schemes link in the Access Manager tile. In the Search Authentication Schemes page, click Search. Select the LDAPScheme row in the search result and click Edit.
-
In the LDAPScheme, click Duplicate. It creates a new scheme with the name ‘Copy of LDAP Scheme’. Change this scheme as follows, and then click Apply.
- Name:
LDAPOUDScheme - Description:
LDAP Scheme Over OUD - Authentication Module:
LDAPOverOUD
- Name:
-
Click Set As Default and then click OK in the confirmation pop-up.
Update oam-config.xml to add TLS v1.2 support
To support the TLSv1.2 connection to the LDAP server, add the LDAP_SSL_PROTOCOL parameter with value TLSv1.2 after the LDAP_URL parameter in the oam-config.xml` file.
-
Launch a terminal window as
oracleand create adbschema.propertiesfile in/stagewith the following contents:oam.entityStore.ConnectString=jdbc:oracle:thin:@oam.example.com:1521/orcl.example.com oam.entityStore.schemaUser=DEV_OAM oam.entityStore.schemaPassword=<password> oam.importExportDirPath=/stage oam.frontending=params=host;port;protocol -
Export the configuration from the dbstore using
config-utility.jar:cd /u01/app/oracle/product/middleware/idm/oam/server/tools/config-utility java -cp /u01/app/oracle/product/middleware/idm/oam/server/tools/config-utility/config-utility.jar:/u01/app/oracle/product/middleware/oracle_common/modules/oracle.jdbc/ojdbc8.jar oracle.security.am.migrate.main.ConfigCommand /u01/app/oracle/admin/domains/oam_domain export /stage/dbschema.propertiesThe output will look similar to the following:
<DATE> oracle.security.am.migrate.main.command.CommandFactory getCommand INFO: executable operation: export oam.exportDirPath=/stage oam.exportedFile=oam-config.xml -
Edit the
/stage/oam-config.xmland locate the line:<Setting Name="LDAP_URL" Type="xsd:string">ldaps://oam.example.com:1636</Setting>Add the
LDAP_SSL_PROTOCOLparameter after theLDAP_URLentry and save the file:<Setting Name="LDAP_SSL_PROTOCOL" Type="xsd:string">TLSv1.2</Setting>For example:
<Setting Name="LDAP" Type="htf:map"> ... <Setting Name="LDAP_URL" Type="xsd:string">ldaps://oam.example.com:1636</Setting> <Setting Name="LDAP_SSL_PROTOCOL" Type="xsd:string">TLSv1.2</Setting> -
Import the updated configuration by running the following command:
java -cp /u01/app/oracle/product/middleware/idm/oam/server/tools/config-utility/config-utility.jar:/u01/app/oracle/product/middleware/oracle_common/modules/oracle.jdbc/ojdbc8.jar oracle.security.am.migrate.main.ConfigCommand /u01/app/oracle/admin/domains/oam_domain import /stage/dbschema.propertiesThe output will look similar to the following:
<DATE> oracle.security.am.migrate.main.command.CommandFactory getCommand INFO: executable operation: import <DATE> oracle.security.am.migrate.util.ConfigFileUtil replaceValue INFO: 64 will be replaced by 65 <DATE> oracle.security.am.migrate.operation.ImportConfigOperation invoke INFO: imported config file version to database:65 oam.importDirPath=/stage oam.importedFile=oam-config.xml oam.importedVersion=65 oam.operation.time=2186 -
Restart the
oam_server1server:cd /u01/app/oracle/admin/domains/oam_domain/bin ./stopManagedWebLogic.sh oam_server1 ./startManagedWebLogic.sh oam_server1
Next Tutorial
Install and Configure Oracle HTTP Server for Oracle Access Management 12c.
Feedback
To provide feedback on this tutorial, please contact idm_user_assistance_ww_grp@oracle.com.
Acknowledgements
- Author - Russ Hodgson
Configure Oracle Unified Directory for OAM 12c
E89982-02
June 2022
Copyright © 2022, Oracle and/or its affiliates.