5 Using the Connector
You can use the connector for performing reconciliation and provisioning operations after configuring your application to meet your requirements.
5.1 Configuring Reconciliation
You can configure the connector to specify the type of reconciliation and its schedule.
This section discusses the following topics related to configuring reconciliation:
5.1.1 Performing Full Reconciliation and Incremental Reconciliation
Full reconciliation involves reconciling all existing user records from the target system into Oracle Identity Governance. After you create the application, you must first perform full reconciliation. .
To perform a full reconciliation run, remove (delete) any value currently assigned to the Latest Token and Filter suffix parameters and run one of the reconciliation jobs listed in the Reconciliation Jobs section.
In the Azure AD connector, the incremental reconciliation option is not enabled by default. The connector supports incremental reconciliation only if the target system contains an attribute that holds the timestamp at which an object is created or modified.
Configuring Incremental Reconciliation
If you want to perform incremental reconciliation runs, then configure incremental reconciliation as follows:Note:
In the Azure AD connector, the incremental reconciliation option is not enabled by default. The connector supports incremental reconciliation only if the target system contains an attribute that holds the timestamp at which an object is created or modified.
For example, consider lastDirSyncTime as a sample
Incremental Recon Attribute that
you specify for the AzureAD User Reconciliation
Scheduled job. After the first full reconciliation
run, the connector populates the Latest
Token parameter with a timestamp. In
subsequent reconciliation runs, the connector
fetches only the user records that are created or
updated after the Latest Token
timestamp.
- Before running an incremental reconciliation job, first run a full Trusted/Target User Reconciliation job and configure the value of
Incremental Recon AttributeaslastDirSyncTime.Note:
ThelastDirSyncTimeis a sample attribute. This attribute name may be different in your production instance. -
After a successful reconciliation job run, the
Latest Tokenattribute gets updated.Sample latest token value:
<String>2020-05-06T17:27:34Z</String> -
Open Identity Self-Service application.
-
Click Manage.
-
Click Application.
-
Search and open the application you have created.
-
Expand the Advanced Settings option and modify the value of
relURIsas per your requirement. -
To use both User and Group Reconciliation jobs, modify relURIs as follows:
-
For Authoritative Application, modify
relURIsas:"__ACCOUNT__.CREATEOP=/$(api_version)$/users?","__ACCOUNT__.UPDATEOP=/$(api_version)$/users/$(__UID__)$","__ACCOUNT__.SEARCHOP=/$(api_version)$/users?$filter=$(Incremental Recon Attribute)$+ge+$(Latest Token)$&$select=assignedLicenses,displayName,userType,givenName,userPrincipalName,id,$(Incremental Recon Attribute)$,city,usageLocation,accountEnabled,mailNickname,country&$top=$(PAGE_SIZE)$&$skiptoken=$(PAGE_TOKEN)$","__ACCOUNT__=/$(api_version)$/users/$(__UID__)$?$select=displayName,givenName,userPrincipalName,id,preferredLanguage,usageLocation,accountEnabled,surname,country","__ACCOUNT__.manager.SEARCHOP=/$(api_version)$/users/$(__UID__)$/manager","__ACCOUNT__.manager=/$(api_version)$/users/$(__UID__)$/manager/$ref" - For Target Application, modify
relURIsas:"__ACCOUNT__.CREATEOP=/$(api_version)$/users?","__ACCOUNT__.UPDATEOP=/$(api_version)$/users/$(__UID__)$","__ACCOUNT__.SEARCHOP=/$(api_version)$/users?$filter=$(Incremental Recon Attribute)$+ge+$(Latest Token)$&$select=assignedLicenses,displayName,userType,givenName,userPrincipalName,id,$(Incremental Recon Attribute)$,city,usageLocation,accountEnabled,mailNickname,country&$top=$(PAGE_SIZE)$&$skiptoken=$(PAGE_TOKEN)$","__ACCOUNT__=/$(api_version)$/users/$(__UID__)$?$select=assignedLicenses,displayName,givenName,userPrincipalName,id,createdDateTime,city,usageLocation,accountEnabled,mailNickname,country","__ACCOUNT__.manager.SEARCHOP=/$(api_version)$/users/$(__UID__)$/manager","__ACCOUNT__.manager=/$(api_version)$/users/$(__UID__)$/manager/$ref","__ACCOUNT__.__GROUP__.SEARCHOP=/$(api_version)$/users/$(__UID__)$/memberOf?&$top=$(PAGE_SIZE)$&$skiptoken=$(PAGE_TOKEN)$","__ACCOUNT__.__GROUP__.DELETEOP=/$(api_version)$/groups/$(__GROUP__.id)$/members/$(__UID__)$/$ref","__ACCOUNT__.__GROUP__=/$(api_version)$/groups/$(__GROUP__.id)$/members/$ref","__GROUP__.CREATEOP=/$(api_version)$/groups","__GROUP__.UPDATEOP=/$(api_version)$/groups/$(__UID__)$","__GROUP__.SEARCHOP=/$(api_version)$/groups?&$filter=securityEnabled+eq+true+and+(Incremental Recon Attribute)$+ge+$(Latest Token)$&$top=$(PAGE_SIZE)$&$skiptoken=$(PAGE_TOKEN)$","__OFFICEGROUP__.SEARCHOP=/$(api_version)$/groups?&$filter=securityEnabled+eq+false+and+(Incremental Recon Attribute)$+ge+$(Latest Token)$&$top=$(PAGE_SIZE)$&$skiptoken=$(PAGE_TOKEN)$","__GROUP__=/$(api_version)$/groups/$(__UID__)$","__GROUP__.member=/$(api_version)$/groups/$(__UID__)$/members/$ref?","__ROLE__.SEARCHOP=/$(api_version)$/directoryRoles?/$(Filter Suffix)$","__ACCOUNT__.__ROLE__=/$(api_version)$/directoryRoles/$(__ROLE__.id)$/members/$ref","__ACCOUNT__.__ROLE__.DELETEOP=/$(api_version)$/directoryRoles/$(__ROLE__.id)$/members/$(__UID__)$/$ref","__ROLE__.member=/$(api_version)$/directoryRoles/$(__UID__)$/members/$ref","__ACCOUNT__.__ROLE__.SEARCHOP=/$(api_version)$/users/$(__UID__)$/memberOf?&$top=$(PAGE_SIZE)$&$skiptoken=$(PAGE_TOKEN)$","assignedLicenses.SEARCHOP=/$(api_version)$/subscribedSkus?/$(Filter Suffix)$","__ACCOUNT__.assignedLicenses.ADDATTRIBUTE=/$(api_version)$/users/$(__UID__)$/assignLicense","__ACCOUNT__.assignedLicenses.REMOVEATTRIBUTE=/$(api_version)$/users/$(__UID__)$/assignLicense","__ACCOUNT__.__OFFICEGROUP__=/$(api_version)$/groups/$(__OFFICEGROUP__.id)$/members/$ref","__ACCOUNT__.__OFFICEGROUP__.DELETEOP=/$(api_version)$/groups/$(__OFFICEGROUP__.id)$/members/$(__UID__)$/$ref","__ACCOUNT__.__OFFICEGROUP__.SEARCHOP=/$(api_version)$/users/$(__UID__)$/memberOf?&$top=$(PAGE_SIZE)$&$skiptoken=$(PAGE_TOKEN)$"
-
-
To use only User Reconciliation jobs, modify relURIs as follows:
-
For Authoritative Application, modify
relURIsas::"__ACCOUNT__.CREATEOP=/$(api_version)$/users?","__ACCOUNT__.UPDATEOP=/$(api_version)$/users/$(__UID__)$","__ACCOUNT__.SEARCHOP=/$(api_version)$/users?$filter=$(Incremental Recon Attribute)$+ge+$(Latest Token)$&$select=assignedLicenses,displayName,userType,givenName,userPrincipalName,id,$(Incremental Recon Attribute)$,city,usageLocation,accountEnabled,mailNickname,country&$top=$(PAGE_SIZE)$&$skiptoken=$(PAGE_TOKEN)$","__ACCOUNT__=/$(api_version)$/users/$(__UID__)$?$select=displayName,givenName,userPrincipalName,id,preferredLanguage,usage -
For Target Application, modify
relURIsas:"__ACCOUNT__.CREATEOP=/$(api_version)$/users?","__ACCOUNT__.UPDATEOP=/$(api_version)$/users/$(__UID__)$","__ACCOUNT__.SEARCHOP=/$(api_version)$/users?$filter=$(Incremental Recon Attribute)$+ge+$(Latest Token)$&$select=assignedLicenses,displayName,userType,givenName,userPrincipalName,id,city,$(Incremental Recon Attribute)$,usageLocation,accountEnabled,mailNickname,country&$top=$(PAGE_SIZE)$&$skiptoken=$(PAGE_TOKEN)$","__ACCOUNT__=/$(api_version)$/users/$(__UID__)$?$select=assignedLicenses,displayName,givenName,userPrincipalName,id,city,createdDateTime,usageLocation,accountEnabled,mailNickname,country","__ACCOUNT__.manager.SEARCHOP=/$(api_version)$/users/$(__UID__)$/manager","__ACCOUNT__.manager=/$(api_version)$/users/$(__UID__)$/manager/$ref","__ACCOUNT__.__GROUP__.SEARCHOP=/$(api_version)$/users/$(__UID__)$/memberOf?&$top=$(PAGE_SIZE)$&$skiptoken=$(PAGE_TOKEN)$","__ACCOUNT__.__GROUP__.DELETEOP=/$(api_version)$/groups/$(__GROUP__.id)$/members/$(__UID__)$/$ref","__ACCOUNT__.__GROUP__=/$(api_version)$/groups/$(__GROUP__.id)$/members/$ref","__GROUP__.CREATEOP=/$(api_version)$/groups","__GROUP__.UPDATEOP=/$(api_version)$/groups/$(__UID__)$","__GROUP__.SEARCHOP=/$(api_version)$/groups?&$filter=securityEnabled+eq+true&$top=$(PAGE_SIZE)$&$skiptoken=$(PAGE_TOKEN)$","__OFFICEGROUP__.SEARCHOP=/$(api_version)$/groups?&$filter=securityEnabled+eq+false&$top=$(PAGE_SIZE)$&$skiptoken=$(PAGE_TOKEN)$","__GROUP__=/$(api_version)$/groups/$(__UID__)$","__GROUP__.member=/$(api_version)$/groups/$(__UID__)$/members/$ref?","__ROLE__.SEARCHOP=/$(api_version)$/directoryRoles?/$(Filter Suffix)$","__ACCOUNT__.__ROLE__=/$(api_version)$/directoryRoles/$(__ROLE__.id)$/members/$ref","__ACCOUNT__.__ROLE__.DELETEOP=/$(api_version)$/directoryRoles/$(__ROLE__.id)$/members/$(__UID__)$/$ref","__ROLE__.member=/$(api_version)$/directoryRoles/$(__UID__)$/members/$ref","__ACCOUNT__.__ROLE__.SEARCHOP=/$(api_version)$/users/$(__UID__)$/memberOf?&$top=$(PAGE_SIZE)$&$skiptoken=$(PAGE_TOKEN)$","assignedLicenses.SEARCHOP=/$(api_version)$/subscribedSkus?/$(Filter Suffix)$","__ACCOUNT__.assignedLicenses.ADDATTRIBUTE=/$(api_version)$/users/$(__UID__)$/assignLicense","__ACCOUNT__.assignedLicenses.REMOVEATTRIBUTE=/$(api_version)$/users/$(__UID__)$/assignLicense","__ACCOUNT__.__OFFICEGROUP__=/$(api_version)$/groups/$(__OFFICEGROUP__.id)$/members/$ref","__ACCOUNT__.__OFFICEGROUP__.DELETEOP=/$(api_version)$/groups/$(__OFFICEGROUP__.id)$/members/$(__UID__)$/$ref","__ACCOUNT__.__OFFICEGROUP__.SEARCHOP=/$(api_version)$/users/$(__UID__)$/memberOf?&$top=$(PAGE_SIZE)$&$skiptoken=$(PAGE_TOKEN)$" Location,accountEnabled,surname,country","__ACCOUNT__.manager.SEARCHOP=/$(api_version)$/users/$(__UID__)$/manager","__ACCOUNT__.manager=/$(api_version)$/users/$(__UID__)$/manager/$ref"
-
- Run the user reconciliation scheduled job to perform incremental reconciliation. The connector only fetches records created or modified after the time stamp (populated in the Latest Token attribute).
5.1.2 Performing Limited Reconciliation
Limited or filtered reconciliation is the process of limiting the number of records being reconciled based on a set filter criteria.
By default, all target system records that are added or modified after the last reconciliation run are reconciled during the current reconciliation run. You can customize this process by specifying the subset of added or modified target system records that must be reconciled. You do this by creating filters for the reconciliation module.
You can perform limited reconciliation by creating filters for the reconciliation module. An example Filter Suffix value that is valid in the API version 1.6 is as follows:
Filter Suffix value : &$filter=startswith(displayName,'john.doe')
This connector provides a Filter Suffix attribute (a scheduled task attribute) that allows you to use any of the attributes of the target system to filter target system records. You specify a value for the Filter Suffix attribute while configuring the user reconciliation scheduled job.
Note:
Specify a value for the Filter Suffix attribute in a format that is supported by the Azure AD APIs you are using. For example:-
If you have configured incremental reconciliation and you are using version 1.6 of the API, then set a value for the Filter Suffix attribute in the following format:
Sample Filter Suffix for API version 1.6: %20and%20startswith(displayName,'user1')
-
If you have not configured incremental reconciliation and you are using version 1.6 of the API, then set a value for the Filter Suffix attribute in the following format:
Sample Filter Suffix for API version 1.6: &$filter=startswith(displayName,'user1')
5.2 Configuring Reconciliation Jobs
Configure reconciliation jobs to perform reconciliation runs that check for new information on your target system periodically and replicates the data in Oracle Identity Governance.
You can apply this procedure to configure the reconciliation jobs for users and entitlements.
5.3 Configuring Provisioning
You can configure the provisioning operation for the Azure AD connector.
5.3.1 Guidelines on Performing Provisioning Operations
These are the guidelines that you must apply while performing provisioning operations.
-
For a Create User provisioning operation, you must specify a value for the User Principal Name field along with the domain name. For example, jdoe@example.com, it is mandatory field, other mandatory fields are Display Name, Password, MailNickname, and Usage Location.
-
During a group provisioning operation you must enter a value for the DisplayName and MailNickname fields. The value in the MailNickname field should not include spaces.
5.3.2 Performing Provisioning Operations
You create a new user in Identity Self Service by using the Create User page. You provision or request for accounts on the Accounts tab of the User Details page.
To perform provisioning operations in Oracle Identity Governance:
- Log in to Identity Self Service.
- Create a user as follows:
- In Identity Self Service, click Manage. The Home tab displays the different Manage option. Click Users. The Manage Users page is displayed.
- From the Actions menu, select Create. Alternatively, you can click Create on the toolbar. The Create User page is displayed with input fields for user profile attributes.
- Enter details of the user in the Create User page.
- On the Account tab, click Request Accounts.
- In the Catalog page, search for and add to cart the application instance for the connector that you configured earlier, and then click Checkout.
- Specify value for fields in the application form and then click Ready to Submit.
- Click Submit.
See Also:
Creating a User in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance for details about the fields on the Create User page5.4 Connector Objects Used for Groups Management
Learn about the objects that are used by the connector to perform group management operations such as create and delete.
5.4.1 Lookup Definitions for Groups Management
The lookup definitions for Groups are automatically created in Oracle Identity Governance after you create the application by using the connector.
5.4.1.1 Lookup.AzureAD.GM.Configuration
The Lookup.AzureAD.GM.Configuration lookup definition holds configuration entries that are specific to the group object type. This lookup definition is used during group management operations when your target system is configured as a target resource.
Table 5-1 Entries in the Lookup.AzureAD.GM.Configuration Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Provisioning Attribute Map |
Lookup.AzureAD.GM.ProvAttrMap |
This entry holds the name of the lookup definition that stores attribute mappings between Oracle Identity Governance and the target system. This lookup definition is used during provisioning operations. |
|
Recon Attribute Map |
Lookup.AzureAD.GM.ReconAttrMap |
This entry holds the name of the lookup definition that stores attribute mappings between Oracle Identity Governance and the target system. This lookup definition is used during reconciliation. |
5.4.1.2 Lookup.AzureAD.GM.ProvAttrMap
Lookup.AzureAD.GM.ProvAttrMap lookup definition holds mappings between process form fields (Code Key values) and target system attributes (Decode). This lookup definition is preconfigured and is used during group provisioning operations.
Table 5-2 Entries in the Lookup.AzureAD.GM.ProvAttrMap Lookup Definition
| Group Field on Oracle Identity Governance | AzureAD Field |
|---|---|
|
ObjectId |
__UID__ |
|
Description |
description |
|
Mail Enabled |
mailEnabled |
|
Mail Nickname |
mailNickname |
|
Display Name |
__NAME__ |
|
Security Enabled |
securityEnabled |
5.4.1.3 Lookup.AzureAD.GM.ReconAttrMap
The Lookup.AzureAD.GM.ReconAttrMap lookup definition holds mappings between resource object fields (Code Key values) and target system attributes (Decode). This lookup definition is preconfigured and is used during target resource group reconciliation runs.
Table 5-3 Entries in the Lookup.AzureAD.GM.ReconAttrMap Lookup Definition
| Group Field on Oracle Identity Governance | AzureAD Field |
|---|---|
|
ObjectId |
__UID__ |
|
Description |
description |
|
Mail Enabled |
mailEnabled=”${mailEnabled}” |
|
Mail Nickname |
mailNickname |
|
Display Name |
__NAME__ |
|
Security Enabled |
securityEnabled="${securityEnabled}" |
|
OIM Org Name |
OIM Organization Name Note: This is a connector attribute. The value of this attribute is used internally by the connector to specify the organization of the groups in Oracle Identity Governance. |
5.4.2 Reconciliation Rules and Action Rules for Groups Management
Reconciliation rules are used by the reconciliation engine to determine the identity to which Oracle Identity Governance must assign a newly discovered account on the target system. Reconciliation action rules define that actions the connector must perform based on the reconciliation rules.
5.4.2.1 Reconciliation Rule for Groups
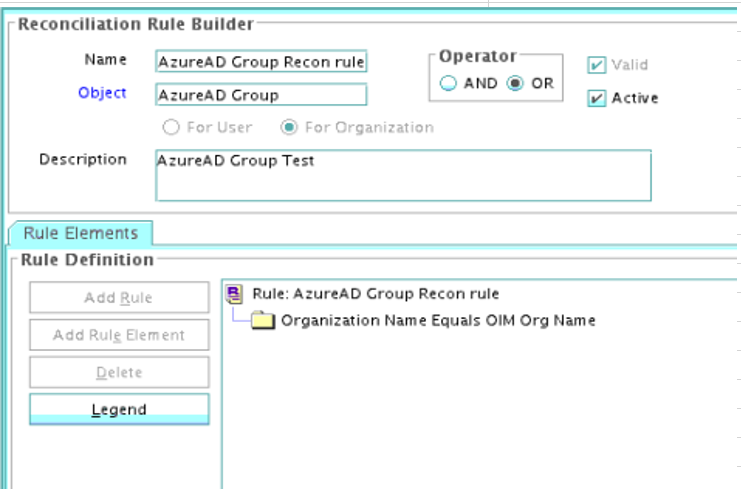
The following is the process-matching rule for groups:
Rule name: AzureAD Groups Recon Rule
Rule element: Organization Name Equals OIM Org Name
In this rule element:
-
Organization Name is the Organization Name field of the OIM User form.
-
OIM Org Name is the organization name of the groups in Oracle Identity Governance. OIM Org Name is the value specified in the Organization Name attribute of the AzureAD Group Recon scheduled job.
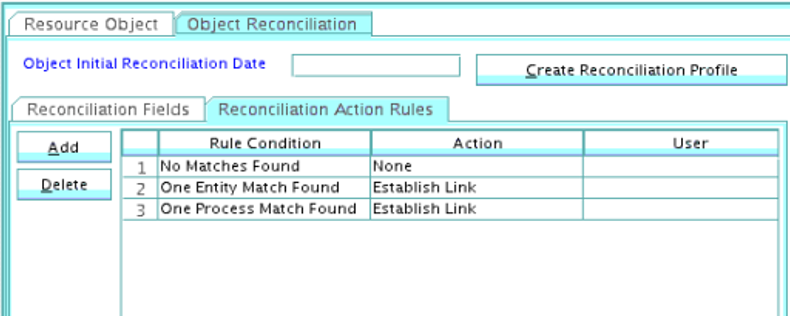
5.4.2.2 Reconciliation Action Rules for Groups
Table 5-4 lists the action rules for groups reconciliation.
Table 5-4 Action Rules for Groups Reconciliation
| Rule Condition | Action |
|---|---|
|
No Matches Found |
None |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
5.4.3 Reconciliation Scheduled Jobs for Groups Management
After you create an application, reconciliation scheduled jobs are automatically created in Oracle Identity Governance. You must configure these scheduled jobs to suit your requirements by specifying values for its attributes.
Table 5-5 Attributes of the AzureAD Group Reconciliation Job
| Attribute | Description |
|---|---|
|
Filter Suffix |
Enter the search filter for fetching user records from the target system during a reconciliation run. See Performing Limited Reconciliation for more information about this attribute. |
|
Object Type |
This attribute holds the name of the object type for the reconciliation run. Default value: Group Note: Do not change the default value. |
|
Incremental Recon Attribute |
Attribute that holds the timestamp at which the token record was modified. |
|
OIM Organization Name |
Enter the name of the Oracle Identity Governance organization in which reconciled groups must be created or updated. |
|
IT Resource Name |
Enter the name of the IT resource for the target system installation from which you want to reconcile user records. Default value: AzureAD |
|
Resource Object Name |
This attribute holds the name of the resource object used for reconciliation. Default value: AzureAD Group Note: Do not change the default value. |
|
Scheduled Task Name |
Name of the scheduled task used for reconciliation. Default value: Azure Group Recon Do not modify the value of this attribute. |
5.5 Uninstalling the Connector
Uninstalling the Azure AD connector deletes all the account-related data associated with its resource objects.
If you want to uninstall the connector for any reason, then run the Uninstall Connector utility. Before you run this utility, ensure that you set values for ObjectType and ObjectValues properties in the ConnectorUninstall.properties file. For example, if you want to delete resource objects, scheduled tasks, and scheduled jobs associated with the connector, then enter "ResourceObject", "ScheduleTask", "ScheduleJob" as the value of the ObjectType property and a semicolon-separated list of object values corresponding to your connector as the value of the ObjectValues property.
For example: AzureAD User; AzureAD Group
Note:
If you set values for theConnectorName and Release properties along with the ObjectType and ObjectValue properties, then the deletion of objects listed in the ObjectValues property is performed by the utility and the Connector information is skipped.
For more information, see Uninstalling Connectors in Oracle Fusion Middleware Administering Oracle Identity Governance.