2 Creating an Application by Using the Connector
Learn about onboarding applications using the connector and the prerequisites for doing so.
2.1 Process Flow for Creating an Application By Using the Connector
From Oracle Identity Governance release 12.2.1.3.0 onward, connector deployment is handled using the application onboarding capability of Identity Self Service.
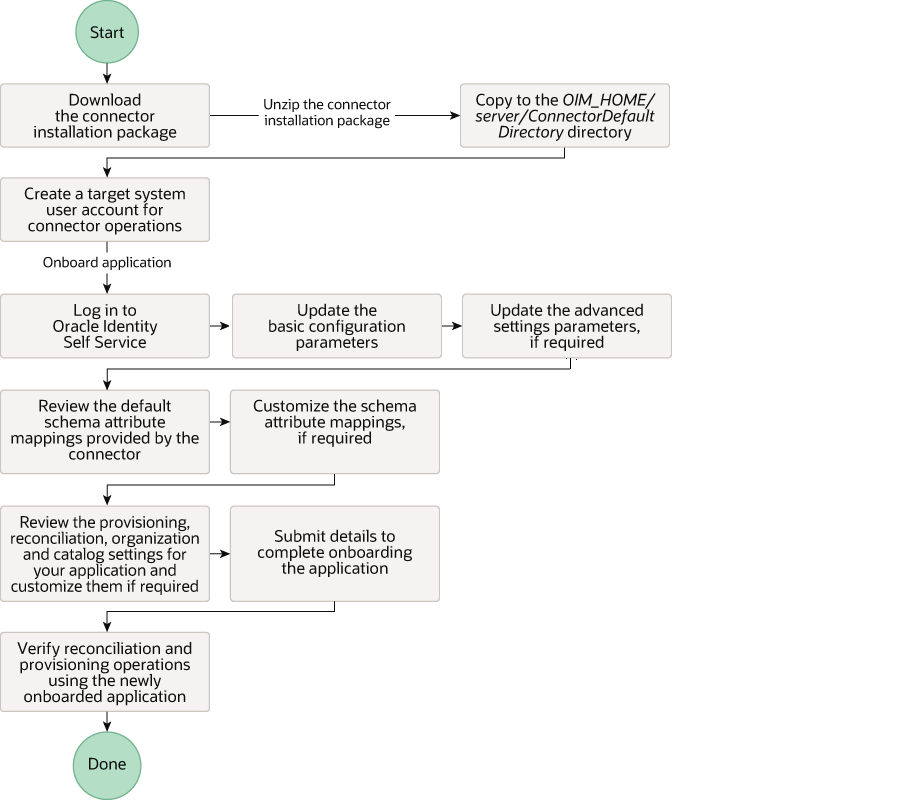
Figure 2-1 is a flowchart depicting high-level steps for creating an application in Oracle Identity Governance by using the connector installation package.
Figure 2-1 Overall Flow of the Process for Creating an Application By Using the Connector
2.2 Downloading the Connector Installation Package
You can obtain the installation package for your connector on the Oracle Technology Network (OTN) website.
2.3 Downloading and Copying Third-Party Jar Libraries
You can either use third-party jars from the
AmazonWebServices-12.2.1.3.0 /lib folder shipped with the connector
package or download any latest, stable, and secure version. Please follow the below
procedure to include third-party jars:
Note:
If you are using Connector Server, copy Amazon Web Services Apps third-party libraries to theCONNECTOR_SERVER_HOME/lib directory.
If you are looking for latest third party jar libraries, use the following link to download them:
Table 2-1 Third-Party Jars
2.4 Creating an Application By Using the Amazon Webservice Connector
You can onboard an application into Oracle Identity Governance from the connector package by creating a Target application. To do so, you must log in to Identity Self Service and then choose the Applications box on the Manage tab.
Note:
For detailed information on each of the steps in this procedure, see Creating Applications of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
- Create an application in Identity Self Service. The high-level steps are as follows:
- Verify reconciliation and provisioning operations on the newly created application.
See Also:
-
Configuring the Connector for details on basic configuration and advanced settings parameters, default user account attribute mappings, default correlation rules, and reconciliation jobs that are predefined for this connector
-
Configuring Oracle Identity Governance for details on creating a new form and associating it with your application, if you chose not to create the default form
2.5 Creating a Target System User Account for the AWS Target
The following topics describe the procedures to create a target system user account for the AWS target:
2.5.1 Signing in with Root User Credentials
To sign in to an AWS account as the root user, perform the following steps:
Note:
To sign in to an AWS account as a root user, ensure you know the email address used to create the AWS account and the password for the root user.- Open https://console.aws.amazon.com/.
- If you have not signed in previously using this browser, select Root user, enter the email address associated with your account, click Next, enter the password and choose Sign in.
- If you have signed in as a root user previously using this browser, your browser might remember the email address for the AWS account. If so, you just need to enter password and select Sign in.
2.5.2 Creating an IAM user in the AWS account
To create an IAM user in the AWS account, perform the following steps:
2.5.3 Adding Inline Policy to an IAM User
To add inline policies to IAM users, perform the following steps: