4 Performing Postconfiguration Tasks for the SAP User Management Connector
These are the tasks that you can perform after creating an application in Oracle Identity Governance.
-
Configuring the Target System to Enable Propagation of User Password Changes
-
Setting Up the Advanced Configuration Values in Oracle Identity Governance
-
Configuring the Access Request Management Feature of the Connector
-
Configuring SNC to Secure Communication Between Oracle Identity Governance and the Target System
-
Synchronizing the SAPUM Process Form Field Length Needs with the Target Field Length
Configuring Ports on the Target System
You can configure ports to enable communication between the target system and Oracle Identity Governance.
To enable communication between the target system and Oracle Identity Governance, you must ensure that the ports listed in Table 4-1 are open.
Table 4-1 Ports for SAP Services
| Service | Port Number Format | Default Port |
|---|---|---|
|
Dispatcher |
32SYSTEM_NUMBER |
3200 |
|
Gateway (for non-SNC communication) |
33SYSTEM_NUMBER |
3300 |
|
Gateway (for SNC communication) |
48SYSTEM_NUMBER |
4800 |
|
Message server |
36SYSTEM_NUMBER |
3600 |
To check if these ports are open, you can, for example, try to establish a Telnet connection from Oracle Identity Governance to these ports.
Configuring the Target System to Enable Propagation of User Password Changes
This section describes the procedures involved in configuring the target system to enable propagation of user password changes from the SAP CUA parent system to its child systems. You may need the assistance of the SAP Basis administrator to perform some of these procedures.
Configuring the target system involves the following tasks:
Gathering Required Information
The following information is required to configure the target system:
Note:
During SAP installation, a system number and client number are assigned to the server on which the installation is carried out. These items are mentioned in the following list.
-
Login details of an admin user having the permissions required to import requests
-
Client number of the server on which the request is to be imported
-
System number
-
Server IP address
-
Server name
-
User ID of the account to be used for connecting to the SAP application server
-
Password of the account to be used for connecting to the SAP application server
Creating an Entry in the BAPIF4T Table
The User Group field is one of the fields that holds user data in SAP. F4 values are values of a field that you can view and select from a list. To view F4 values of the User Group field, you must create an entry in the BAPIF4T table by running the SM30 transaction. Ensure that the entry in the table includes XUCLASS as the data element and ZXL_PARTNER_BAPI_F4_AUTHORITY as the function name.
Importing the Request
You must import the request to create the following custom objects in the SAP system.
| Object Type | Object Name |
|---|---|
|
Package |
ZXLC |
|
Function Group |
ZXLCGRP ZXLCHLPVALUES ZXLCPRF ZXLCRL ZXLCUSR |
|
Message class |
ZXLCBAPI |
|
Program |
ZLCF4HLP_DATA_DEFINITIONS ZLCMS01CTCO ZLCMS01CTCO1 ZLCMS01CTP2 ZXLCGRP ZXLCHLPVALUES ZXLCPRF ZXLCRL ZXLCUSR |
|
Search Help |
ZXLC_ROLE ZXLC_SYS |
|
Business object types |
ZXLCGRP ZXLCHLP ZXLCPRF ZXLCRL ZXLCUSR |
|
Table |
ZXLCBAPIMODE ZXLCBAPIMODM ZXLCGROUPS ZXLCPRF ZXLCROLE ZXLCSTRING ZXLCSYSNAME |
The xlsapcar.sar file contains the definitions for these objects. When you import the request represented by the contents of the xlsapcar.sar file, these objects are automatically created in SAP. This procedure does not result in any change in the existing configuration of SAP.
Importing the request into SAP involves extracting the request files and performing the request import operation as follows:
Configuring Oracle Identity Governance
During application creation, if you did not choose to create a default form, then you must create a UI form for the application that you created by using the connector.
Note:
Perform the procedures described in this section only if you did not choose to create the default form during creating the application.Creating and Activating a Sandbox
You must create and activate a sandbox to begin using the customization and form management features. You can then publish the sandbox to make the customizations available to other users.
See Creating a Sandbox and Activating a Sandbox in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance.
Creating a New UI Form
You can use Form Designer in Oracle Identity System Administration to create and manage application instance forms.
See Creating Forms By Using the Form Designer in Oracle Fusion Middleware Administering Oracle Identity Governance.
While creating the UI form, ensure that you select the resource object corresponding to the newly created application that you want to associate the form with. In addition, select the Generate Entitlement Forms check box.
Publishing a Sandbox
Before publishing a sandbox, perform this procedure as a best practice to validate all sandbox changes made till this stage as it is difficult to revert the changes after a sandbox is published.
-
In Identity System Administration, deactivate the sandbox.
-
Log out of Identity System Administration.
-
Log in to Identity Self Service using the xelsysadm user credentials and then activate the sandbox that you deactivated in Step 1.
-
In the Catalog, ensure that the application instance form for your resource appears with correct fields.
-
Publish the sandbox. See Publishing a Sandbox in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance.
Updating an Existing Application Instance with a New Form
For any changes that you do in the schema of your application in Identity Self Service, you must create a new UI form and update the changes in an application instance.
To update an existing application instance with a new form:
-
Create and activate a sandbox.
-
Create a new UI form for the resource.
-
Open the existing application instance.
-
In the Form field, select the new UI form that you created.
-
Save the application instance.
-
Publish the sandbox.
See Also:
-
Creating a Sandbox and Activating a Sandbox in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance
-
Creating Forms By Using the Form Designer in Oracle Fusion Middleware Administering Oracle Identity Governance
-
Publishing a Sandbox in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance
Harvesting Entitlements and Sync Catalog
To harvest entitlements and sync catalog:
- Run the scheduled jobs for lookup field synchronization.
- Run the Entitlement List scheduled job to populate Entitlement Assignment schema from child process form table.
- Run the Catalog Synchronization Job scheduled job.
See Also:
-
Reconciliation Jobs for a list of jobs for entitlements (lookup field synchronization)
-
Predefined Scheduled Tasks in Oracle Fusion Middleware Administering Oracle Identity Governance for information about the Entitlement List and Catalog Synchronization Job scheduled jobs
Setting Up the Advanced Configuration Values in Oracle Identity Governance
The Advanced Configuration settings are entered in Oracle Identity Governance when you create an application.
The following sections provide information on the entries in Advanced Configuration:
Linking of SAP HRMS and SAP ERP or SAP CUA Accounts
An SAP HRMS account created for a particular user can be linked with the SAP ERP or SAP CUA account created for the same user. For a particular user, an attribute of SAP HRMS holds the user ID of the corresponding SAP ERP or SAP CUA account.
You can duplicate this link in Oracle Identity Governance by using the following parameters of the Advanced Settings section:
-
validatePERNR: You enter
yesas the value if your operating environment contains multiple SAP HRMS installations. If there is only one SAP HRMS installation, then enter no. -
overwriteLink: You enter
yesas the value if you want existing links in SAP to be overwritten by the ones set up through provisioning operations.
The following topics provide detailed information about the linking process:
About the Linking Process
An SAP HRMS account created for a particular user can be linked with the SAP R/3 or SAP CUA account created for the same user. For a particular user, an attribute of SAP HRMS holds the user ID of the corresponding SAP R/3 or SAP CUA account.
The following example describes the manner in which the linking process is performed:
-
An OIM User record is created for user John Doe through trusted source reconciliation with SAP HRMS. During creation, the user ID value is put in the User ID and Personnel Number attributes of the record.
Note:
The Personnel Number field is a hidden UDF on the OIM User form.
-
To provision an SAP R/3 or SAP CUA account for John, you enter and submit the required data on Oracle Identity System Administration.
-
The connector looks for the user's SAP HRMS account. If you entered
yesas the value of validatePERNR attribute, then the connector checks for a match for the Personnel Number attribute on SAP HRMS. -
After a match is found with an existing SAP HRMS account, the connector performs one of the following steps:
-
If the value of overwriteLink advanced settings parameter is
yes, then the connector posts the User ID value of the SAP R/3 or SAP CUA account into the 0001 subtype in the Communication (0105) infotype of the SAP HRMS account. This is regardless of whether that infotype contains a value. -
If the value of overwriteLink advanced settings parameter is
no, then the connector posts the User ID value of the SAP R/3 or SAP CUA account into the 0001 subtype in the Communication (0105) infotype of the SAP HRMS account only if that subtype does not hold a value.
-
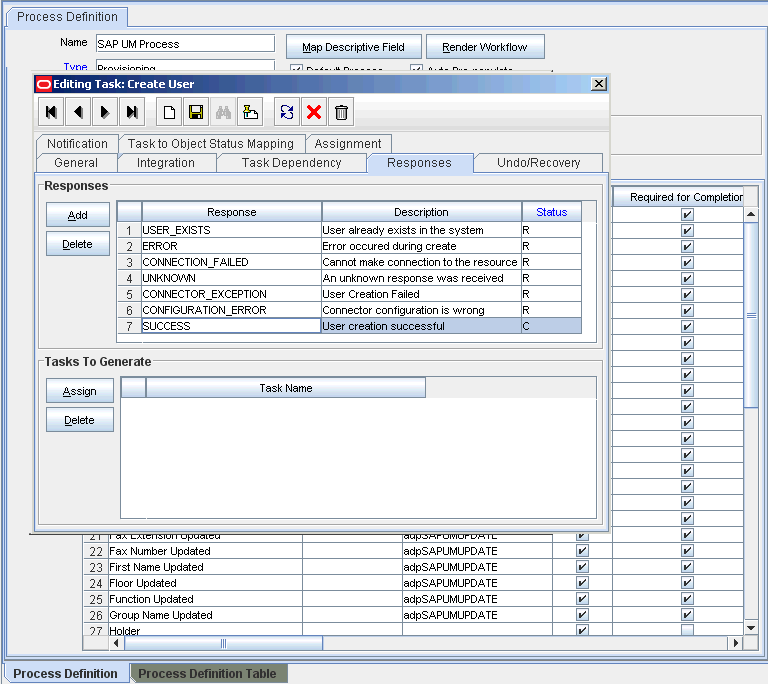
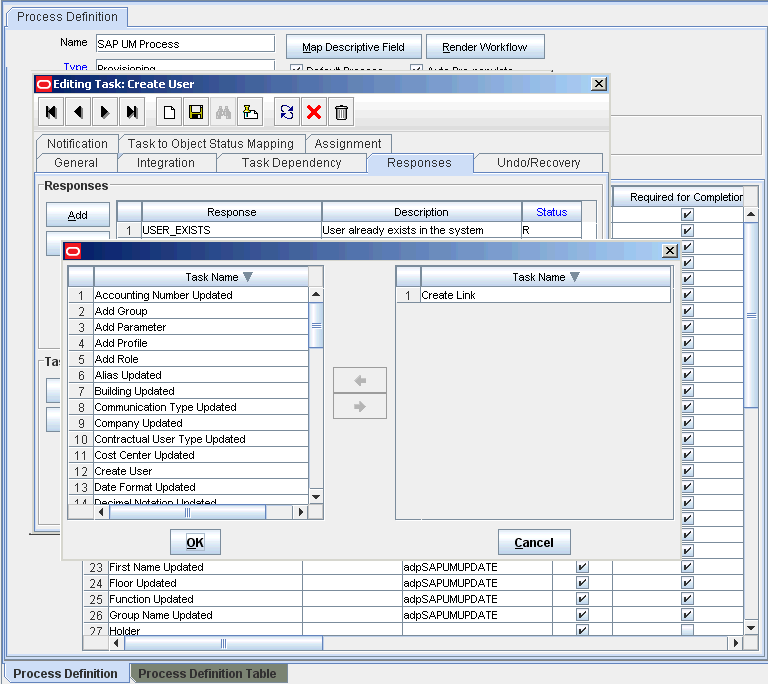
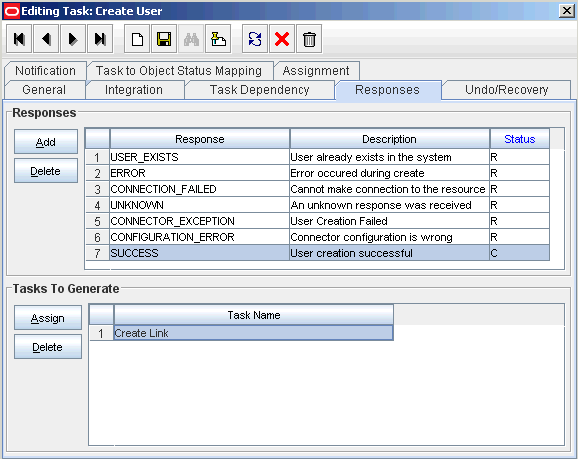
The Create Link task is one of the tasks that are run during the Create User provisioning operation. You can, if required, remove this task so that it is not displayed in the list of tasks that are run. Use the Design Console for this operation.
Configuring Password Changes for Newly Created Accounts
For information about configuring password changes for newly created accounts, see Configuring Password Changes for Newly Created Accounts.
Managing Logging for the SAP UM Connector
Oracle Identity Governance uses the Oracle Diagnostic Logging (ODL) logging service for recording all types of events pertaining to the connector.
The following topics provide detailed information about logging:
Understanding Log Levels
When you enable logging, Oracle Identity Governance automatically stores in a log file information about events that occur during the course of provisioning and reconciliation operations.
ODL is the principle logging service used by Oracle Identity Governance and is based on java.util.logger. To specify the type of event for which you want logging to take place, you can set the log level to one of the following:
-
SEVERE.intValue()+100
This level enables logging of information about fatal errors.
-
SEVERE
This level enables logging of information about errors that might allow Oracle Identity Governance to continue running.
-
WARNING
This level enables logging of information about potentially harmful situations.
-
INFO
This level enables logging of messages that highlight the progress of the application.
-
CONFIG
This level enables logging of information about fine-grained events that are useful for debugging.
-
FINE, FINER, FINEST
These levels enable logging of information about fine-grained events, where FINEST logs information about all events.
These message types are mapped to ODL message type and level combinations as shown in Table 4-2.
Table 4-2 Log Levels and ODL Message Type:Level Combinations
| Java Level | ODL Message Type:Level |
|---|---|
|
SEVERE.intValue()+100 |
INCIDENT_ERROR:1 |
|
SEVERE |
ERROR:1 |
|
WARNING |
WARNING:1 |
|
INFO |
NOTIFICATION:1 |
|
CONFIG |
NOTIFICATION:16 |
|
FINE |
TRACE:1 |
|
FINER |
TRACE:16 |
|
FINEST |
TRACE:32 |
The configuration file for OJDL is logging.xml, which is located at the following path:
DOMAIN_HOME/config/fmwconfig/servers/OIM_SERVER/logging.xml
Here, DOMAIN_HOME and OIM_SEVER are the domain name and server name specified during the installation of Oracle Identity Governance.
Enabling Logging
To enable logging in Oracle WebLogic Server:
-
Edit the logging.xml file as follows:
-
Add the following blocks in the file:
<log_handler name='sap-handler' level='[LOG_LEVEL]' class='oracle.core.ojdl.logging.ODLHandlerFactory'> <property name='logreader:' value='off'/> <property name='path' value='[FILE_NAME]'/> <property name='format' value='ODL-Text'/> <property name='useThreadName' value='true'/> <property name='locale' value='en'/> <property name='maxFileSize' value='5242880'/> <property name='maxLogSize' value='52428800'/> <property name='encoding' value='UTF-8'/> </log_handler>
<logger name="ORG.IDENTITYCONNECTORS.SAP" level="[LOG_LEVEL]" useParentHandlers="false"> <handler name="sap-handler"/> <handler name="console-handler"/> </logger>If you are using SAP GRC, then add the following block:
<logger name="ORG.IDENTITYCONNECTORS.SAPAC" level="[Log_LEVEL]" useParentHandlers="false"> <handler name="sap-handler"/> <handler name="console-handler"/> </logger>If you are using Application onboarding, then add the following block:
<logger name='oracle.iam.application' level="[Log_LEVEL]" useParentHandlers='false'> <handler name='sap-handler'/> <handler name='console-handler'/> </logger> -
Replace both occurrences of [LOG_LEVEL] with the ODL message type and level combination that you require. Table 4-2 lists the supported message type and level combinations.
Similarly, replace [FILE_NAME] with the full path and name of the log file in which you want log messages to be recorded.
The following blocks show sample values for [LOG_LEVEL] and [FILE_NAME]:
<log_handler name='sap-handler' level='NOTIFICATION:1' class='oracle.core.ojdl.logging.ODLHandlerFactory'> <property name='logreader:' value='off'/> <property name='path' value='F:\MyMachine\middleware\user_projects\domains\base_domain1\servers\oim_server1\logs\oim_server1-diagnostic-1.log'/> <property name='format' value='ODL-Text'/> <property name='useThreadName' value='true'/> <property name='locale' value='en'/> <property name='maxFileSize' value='5242880'/> <property name='maxLogSize' value='52428800'/> <property name='encoding' value='UTF-8'/> </log_handler>
<logger name="ORG.IDENTITYCONNECTORS.SAP" level="NOTIFICATION:1" useParentHandlers="false"> <handler name="sap-handler"/> <handler name="console-handler"/> </logger>If you are using SAP GRC, then add the following block:
<logger name="ORG.IDENTITYCONNECTORS.SAPAC" level="NOTIFICATION:1" useParentHandlers="false"> <handler name="sap-handler"/> <handler name="console-handler"/> </logger>If you are using Application Onboarding, then add the following block:
<logger name='oracle.iam.application' level="NOTIFICATION:1" useParentHandlers='false'> <handler name='sap-handler'/> <handler name='console-handler'/> </logger> </logger>With these sample values, when you use Oracle Identity Governance, all messages generated for this connector that are of a log level equal to or higher than the NOTIFICATION:1 level are recorded in the specified file.
-
-
Save and close the file.
-
Set the following environment variable to redirect the server logs to a file:
For Microsoft Windows:
set WLS_REDIRECT_LOG=FILENAMEFor UNIX:
export WLS_REDIRECT_LOG=FILENAMEReplace FILENAME with the location and name of the file to which you want to redirect the output.
-
Restart the application server.
Note:
In an Oracle Identity Governance cluster, perform this step on each node of the cluster.Configuring the Access Request Management Feature of the Connector
Access Request Management is a module in the SAP GRC suite. In an SAP environment, you can set up Access Request Management as the front end for receiving account creation and modification provisioning requests. In Access Request Management, workflows for processing these requests can be configured and users designated as approvers act upon these requests.
Oracle Identity Governance can be configured as the medium for sending provisioning requests to SAP GRC Access Request Management. A request from Oracle Identity Governance is sent to Access Request Management, which forwards the provisioning data contained within the request to the target system (SAP ERP or SAP CUA). The outcome is the creation of or modification to the user's account on the target system.
Note:
Before you configure the Access Request Management feature, it is recommended that you read the guidelines described in Guidelines on Using a Deployment Configuration
See Configuring Request Types and Workflows on SAP GRC Access Request Management for more information about configuring the Access Request Management feature.
Configuring SoD (Segregation of Duties)
SoD is a process that ensures that every individual is given access to only one module of a business process and will not be able to access other modules to reduce risk of fraud and error.
This section provides information on the following procedures:
-
Verifying Entries Created in the Lookup.SAPABAP.System Lookup Definition
-
Specifying a Value for the TopologyName of Basic Configuration Parameter
Note:
The ALL USERS group has INSERT, UPDATE, and DELETE permissions on the UD_SAP, UD_SAPRL, and UD_SPUM_PRO process forms. This is required to enable the following process:
During SoD validation of an entitlement request, data first moves from a dummy object form to a dummy process form. From there data is sent to the SoD engine for validation. If the request clears the SoD validation, then data is moved from the dummy process form to the actual process form. Because the data is moved to the actual process forms through APIs, the ALL USERS group must have INSERT, UPDATE, and DELETE permissions on the three process forms.
Specifying Values for the GRC-ITRes IT Resource
The GRC-ITRes IT resource holds information that is used during communication with SAP GRC Access Request Management. To set values for the parameters of this IT resource:
-
For Oracle Identity Governance 12.2.1.3.0, log in to Oracle Identity System Administration.
-
In the left pane under Configuration, click IT Resource.
-
In the IT Resource Name field on the Manage IT Resource page, enter
GRC-ITResand then click Search. -
Click the edit icon for the IT resource.
-
From the list at the top of the page, select Details and Parameters.
-
Specify values for the parameters of the IT resource.
Table 4-3 lists the parameters of the GRC-ITRes IT resource.
Table 4-3 Parameters of the GRC-ITRes IT Resource
Parameter Description language
Enter the two-letter code for the language set on the target system.
Sample value:
ENConnector Server Name
Name of the IT resource of the type "Connector Server." You create an IT resource for the
Connector Server in Configuring the IT Resource for the Connector Server.
Note: Enter a value for this parameter only if you have deployed the SAP User Management connector in the Connector Server.
password
Enter the password of the account created on Access Request Management system.
port
Enter the number of the port at which Access Request Management system is listening.
Sample value:
8090server
Enter the IP address of the host computer on which Access Request Management system is listening.
Sample value:
10.231.231.231username
Enter the user name of an account created on Access Request Management system. This account is used to call Access Request Management system APIs that are used during request validation.
Sample value:
jdoe -
To save the values, click Update.
Configuring SAP GRC to Act As the SoD Engine
To configure SAP GRC to act as the SoD engine, see Using Segregation of Duties in Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager at for 11g Release 1 (11.1.2).
Verifying Entries Created in the Lookup.SAPABAP.System Lookup Definition
The Lookup.SAPABAP.System lookup definition is automatically populated with system names when you run lookup field synchronization. After synchronization, you must open this lookup definition and ensure that only entries for systems that you want to use for the SoD validation process are retained in this table.
Specifying a Value for the TopologyName of Basic Configuration Parameter
The TopologyName IT resource parameter holds the name of the combination of the following elements that you want to use for SoD validation:
-
Oracle Identity Governance installation
-
SAP GRC installation
-
SAP ERP installation
Enter sodgrc as the value of the TopologyName parameter.
For more inofmration about this element, see Using Segregation of Duties in Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager for 11g Release 1 (11.1.2.0).
See Basic Configuration Parameters for information about specifying values for parameters of Basic Configuration.
Disabling and Enabling SoD
This section describes the procedure to disable and enable SoD on Oracle Identity Governance.
Disabling SoD on Oracle Identity Governance
To disable SoD:
-
For Oracle Identity Governance release 12.2.1.3.0, log in to Oracle Identity System Administration.
-
In the left pane, under System Management, click System Configuration.
-
In the Search System Configuration box, enter
XL.SoDCheckRequiredand then click Search.A list that matches your search criteria is displayed in the search results table.
-
Click the XL.SoDCheckRequired property name.
System properties for SoD are displayed on the right pane.
-
In the Value box, enter
FALSEto disable SoD. -
Click Save.
-
Restart Oracle Identity Governance.
Enabling SoD on Oracle Identity Governance
To enable SoD:
-
For Oracle Identity Governance release 12.2.1.3.0, log in to Oracle Identity System Administration.
-
In the left pane, under System Management, click System Configuration.
-
In the Search System Configuration box, enter
XL.SoDCheckRequiredand then click Search.A list that matches your search criteria is displayed in the search results table.
-
Click the XL.SoDCheckRequired property name.
System properties for SoD are displayed on the right pane.
-
In the Value box, enter
TRUEto enable SoD. -
Click Save.
-
Restart Oracle Identity Governance.
Configuring SNC to Secure Communication Between Oracle Identity Governance and the Target System
Oracle Identity Governance uses a Java application server. To connect to the SAP system application server, this Java application server uses the SAP Java connector (JCo). If required, you can use Secure Network Communication (SNC) to secure communication between Oracle Identity Governance and the SAP system.
This section provides information on the following topics:
Prerequisites for Configuring the Connector to Use SNC
The following are prerequisites for configuring the connector to use SNC:
-
SNC must be activated on the SAP application server.
-
You must be familiar with the SNC infrastructure. You must know which Personal Security Environment (PSE) the application server uses for SNC.
Installing the Security Package
To install the security package on the Java application server used by Oracle Identity Governance:
Configuring SNC
To configure SNC:
-
Either create a PSE or copy the SNC PSE of the SAP application server to the SECUDIR directory. To create the SNC PSE for the Java application server, use the sapgenpse.exe command-line tool as follows:
-
To determine the location of the SECUDIR directory, run the sapgenpse command without specifying any command options. The program displays information such as the library version and the location of the SECUDIR directory.
-
Enter a command similar to the following to create the PSE:
sapgenpse get_pse -p PSE_Name -x PIN Distinguished_Name
The following is a sample distinguished name:
CN=SAPJ2EE, O=MyCompany, C=US
The sapgenpse command creates a PSE in the SECUDIR directory.
-
-
Create credentials for the Java application server.
The Java application server must have active credentials at run time to be able to access its PSE. To check whether or not this condition is met, enter the following command in the parent directory of the SECUDIR directory:
Sapgenpse seclogin
Then, enter the following command to open the PSE of the server and create the credentials.sapgenpse file:
seclogin -p PSE_Name -x PIN -O [NT_Domain\]user_ID
The
user_IDthat you specify must have administrator rights.PSE_NAMEis the name of the PSE file.The credentials file, cred_v2, for the user specified with the
-Ooption is created in the SECUDIR directory. -
Exchange the public key certificates of the two servers as follows:
Note:
If you are using individual PSEs for each certificate of the SAP server, then you must perform this procedure once for each SAP server certificate. This means that the number of times you must perform this procedure is equal to the number of PSEs.
-
Export the Oracle Identity Governance certificate by entering the following command:
sapgenpse export_own_cert -o filename.crt -p PSE_Name -x PIN
-
Import the Oracle Identity Governance certificate into the SAP application server. You may require the SAP administrator's assistance to perform this step.
Use one of the following ways to set up SNC on the SAP application server:- Certificate or User Mapping
- Rule based Certificate Mapping
If you do not want to map each user with the certificate and use batch processing, define a general rule-based certificate mapping to enable NetWeaver map user certificates automatically.
-
Export the certificate of the SAP application server. You may require the SAP administrator's assistance to perform this step.
-
Import the SAP application server certificate into Oracle Identity Governance by entering the following command:
sapgenpse maintain_pk -a serverCertificatefile.crt -p PSE_Name -x PIN
-
-
Configure the following parameters in the SAP UM ITResource IT resource object:
-
SAP lib
-
SAP mode
-
SAP myname
-
SAP partnername
-
SAP qop
-
Configuring the IT Resource for the Connector Server
If you have used the Connector Server, then you must configure values for the parameters of the Connector Server IT resource.
Table 4-4 Parameters of the IT Resource for the SAP UM Connector Server
| Parameter | Description |
|---|---|
|
Host |
Enter the host name or IP address of the computer hosting the Connector Server. Sample value: |
|
Key |
Enter the key for the Connector Server. |
|
Port |
Enter the number of the port at which the Connector Server is listening. Default value: |
|
Timeout |
Enter an integer value which specifies the number of milliseconds after which the connection between the Connector Server and Oracle Identity Governance times out. If the value is zero or if no value is specified, the timeout is unlimited. Recommended value: |
|
UseSSL |
Enter Default value: Note: It is recommended that you configure SSL to secure communication with the connector server. To configure SSL, see Configuring SSL for Java Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance. |
Downloading WSDL files from SAP GRC
In SAP GRC 10 or later, you need to download the WSDL files from SAP GRC before configuring the web services.
Since the connector only supports basic authentication, select the User ID/Password check box for the following web services supported from OIG:
| WSDL | Description |
|---|---|
|
GRAC_AUDIT_LOGS_WS |
Audit log web service |
|
GRAC_LOOKUP_WS |
Lookup service |
|
GRAC_REQUEST_STATUS_WS |
Request status web service |
|
GRAC _RISK_ANALYSIS_WOUT_NO_WS |
Risk analysis without request number. Note: For this WSDL, ReportFormat is a mandatory field from SP17. |
|
GRAC_SELECT_APPL_WS |
Select application web service |
|
GRAC_USER_ACCES_WS |
User access request service |
|
GRAC_SEARCH_ROLES_W |
Search role web service |
When you download the WSDL file, ensure to save it with the same name as mentioned in the SOA Management page. In addition, ensure that the folder containing WSDL files have read permission.
Localizing Field Labels in UI Forms
You can localize UI form field labels by using the resource bundle corresponding to the language you want to use. The resource bundles are available in the connector installation media.
To localize field label that is added to the UI forms:
-
Log in to Oracle Enterprise Manager.
-
In the left pane, expand Application Deployments and then select oracle.iam.console.identity.sysadmin.ear.
-
In the right pane, from the Application Deployment list, select MDS Configuration.
-
On the MDS Configuration page, click Export and save the archive (oracle.iam.console.identity.sysadmin.ear_V2.0_metadata.zip) to the local computer.
-
Extract the contents of the archive, and open one of the following files in a text editor:
SAVED_LOCATION\xliffBundles\oracle\iam\ui\runtime\BizEditorBundle_en.xlf
Note:
You will not be able to view the BizEditorBundle.xlf unless you complete creating the application for your target system or perform any customization such as creating a UDF. -
Edit the BizEditorBundle.xlf file in the following manner:
-
Search for the following text:
<file source-language="en" original="/xliffBundles/oracle/iam/ui/runtime/BizEditorBundle.xlf" datatype="x-oracle-adf">
-
Replace with the following text:
<file source-language="en" target-language="LANG_CODE" original="/xliffBundles/oracle/iam/ui/runtime/BizEditorBundle.xlf" datatype="x-oracle-adf">In this text, replace LANG_CODE with the code of the language that you want to localize the form field labels. The following is a sample value for localizing the form field labels in Japanese:
<file source-language="en" target-language="ja" original="/xliffBundles/oracle/iam/ui/runtime/BizEditorBundle.xlf" datatype="x-oracle-adf">
-
Search for the application instance code. This procedure shows a sample edit for SAP User Management application instance. The original code is:
<trans-unit id="${adfBundle['oracle.adf.businesseditor.model.util.BaseRuntimeResourceBundle']['persdef.sessiondef.oracle.iam.ui.runtime.form.model.user.entity.userEO.UD_SAP_TITLE__c_description']}"> <source>Title</source> </target> </trans-unit> <trans-unit id="sessiondef.oracle.iam.ui.runtime.form.model.umform.entity.umformEO.UD_SAP_TITLE__c_LABEL"> <source>Title</source> </target> </trans-unit> -
Open the resource file from the connector package, for example SAPUM_ja.properties, and get the value of the attribute from the file, for example, global.udf. UD_SAP_TITLE = \u5F79\u8077.
-
Replace the original code shown in Step 6.b with the following:
<trans-unit id="${adfBundle['oracle.adf.businesseditor.model.util.BaseRuntimeResourceBundle']['persdef.sessiondef.oracle.iam.ui.runtime.form.model.user.entity.userEO.UD_SAP_TITLE__c_description']}"> <source>Title</source> <target>\u5F79\u8077</target> </trans-unit> <trans-unit id="sessiondef.oracle.iam.ui.runtime.form.model.umform.entity.umformEO.UD_SAP_TITLE__c_LABEL"> <source>Title</source> <target>\u5F79\u8077</target> </trans-unit> -
Repeat Steps 6.a through 6.d for all attributes of the process form.
-
Save the file as BizEditorBundle_LANG_CODE.xlf. In this file name, replace LANG_CODE with the code of the language to which you are localizing.
Sample file name: BizEditorBundle_ja.xlf.
-
-
Repackage the ZIP file and import it into MDS.
See Also:
Deploying and Undeploying Customizations in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager, for more information about exporting and importing metadata files
-
Log out of and log in to Oracle Identity Governance.