7 Extending the Functionality of the Oracle Internet Directory Connector
You can extend the functionality of the connector to address your specific business requirements.
This chapter discusses the following sections:
Adding New Multivalued Fields for Target Resource Reconciliation
You can add new multivalued fields for target resource reconciliation of users, groups, organizational units, and roles.
Adding New Multivalued Fields for Reconciling Users from a Target Application
By default, the multivalued fields listed on the Schema page for your application in Identity Self Server are mapped for reconciliation between Oracle Identity Governance and the target system. If required, you can add new multivalued fields for target resource reconciliation.
- Log in to Oracle Identity System Administration and create a lookup that can hold the list of values for the multivalued field that you want to add.
- Create a child form and add attributes as follows:
- Log in to Identity System Administration, create a new form and associate it with your application.
See Also:
-
Creating a Lookup Type in Oracle Fusion Middleware Administering Oracle Identity Governance for details about create lookups for your multivalued fields
-
Adding Child Forms in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance for information about creating a child form and adding attributes
-
Configuring Oracle Identity Governance for information about creating a new form and associating it with your application
Adding New Multivalued Fields for Target Resource Reconciliation of Groups, Organizational Units, and Roles
By default, the multivalued fields listed in the respective lookup definitions are mapped for reconciliation between Oracle Identity Governance and the target system. If required, you can add new multivalued fields for target resource reconciliation of groups, organizational units, and roles.
Note:
-
This section describes an optional procedure. Perform this procedure only if you want to add multivalued fields for target resource reconciliation.
-
You can apply this procedure to add group, organizational unit, or role fields.
-
You must ensure that new fields you add for reconciliation contain only string-format data. Binary fields must not be brought into Oracle Identity Governance natively.
To add a new multivalued field for target resource reconciliation, perform the following procedures:
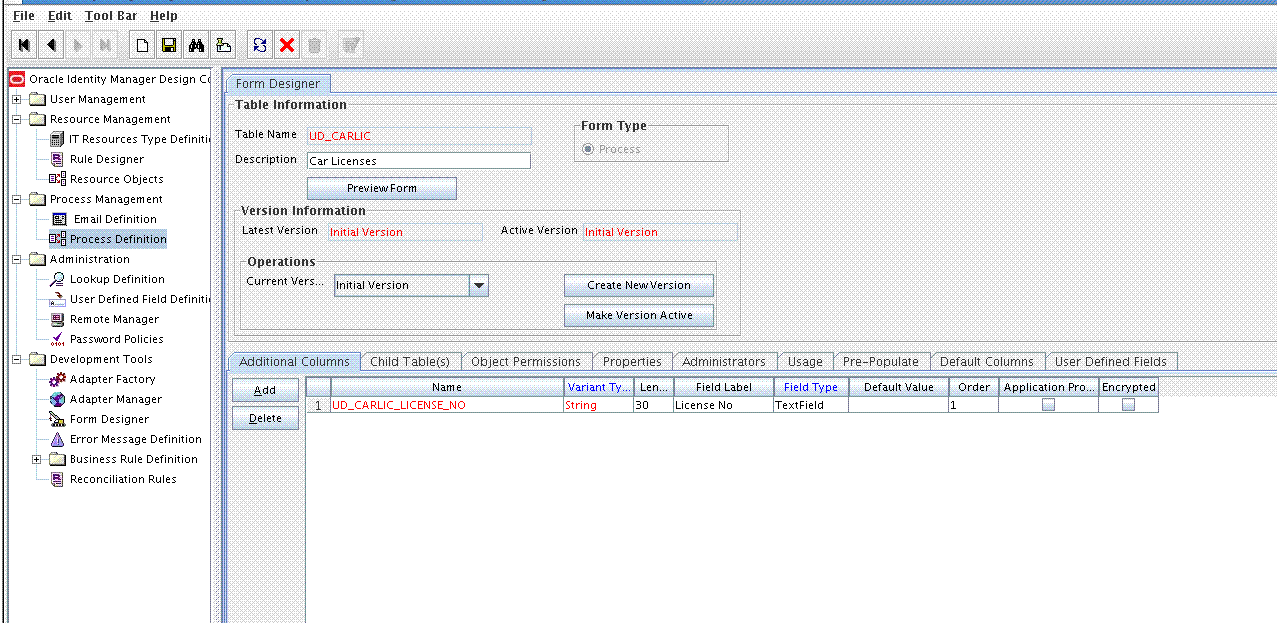
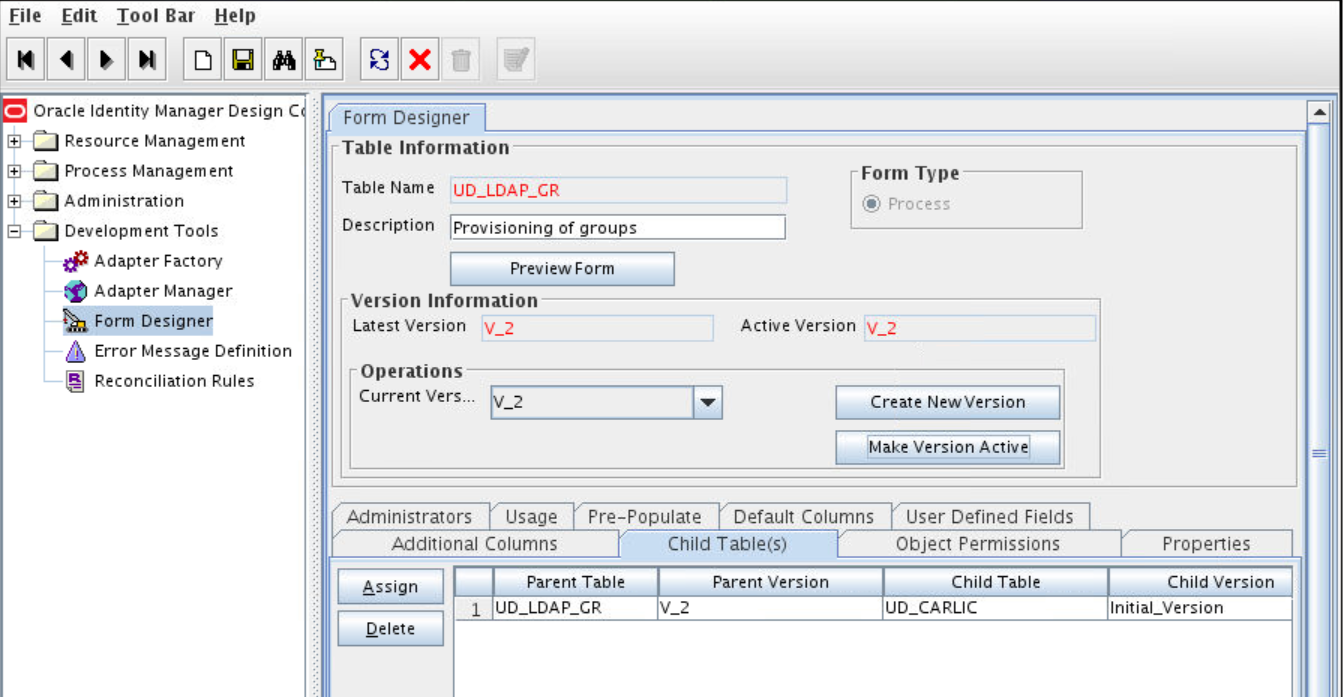
Adding the Form as a Child Form of the Process Form
Add the form created for the multivalued field as a child form of the process form.
Associating a New Form With the Application Instance
If you are using Oracle Identity Manager release 11.1.2.x or later, then all changes made to the Form Designer of the Design Console must be done in a new UI form.
- Log in to Oracle Identity System Administration.
- Create and active a sandbox.
- Create a new UI form to view the newly added field along with the rest of the fields.
- Associate the newly created UI form with the application instance of your target system. To do so, open the existing application instance for your resource, from the Form field, select the form (created in Step 4.c), and then save the application instance.
- Publish the sandbox.
See Also:
-
Creating a Sandbox and Activating a Sandbox in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance
-
Creating Forms By Using the Form Designer in Oracle Fusion Middleware Administering Oracle Identity Governance
-
Publishing a Sandbox in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance
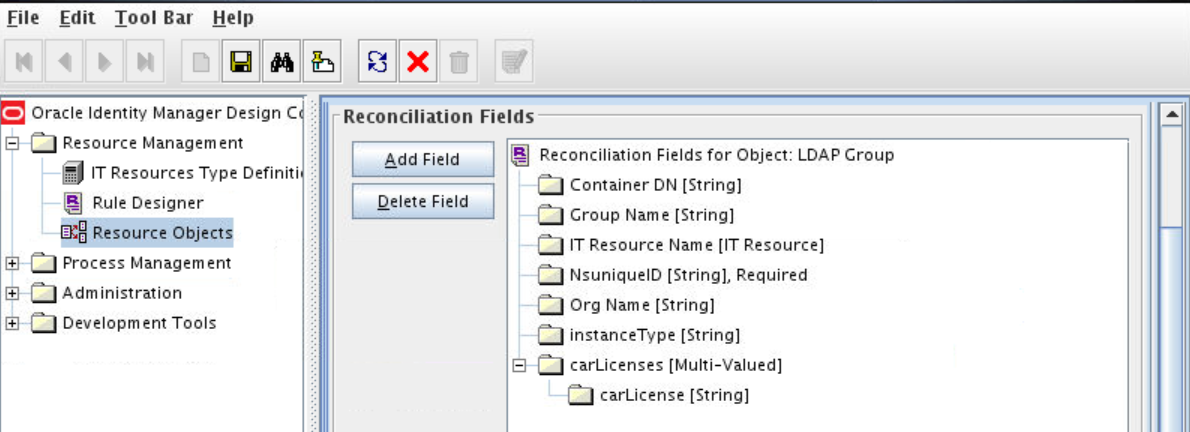
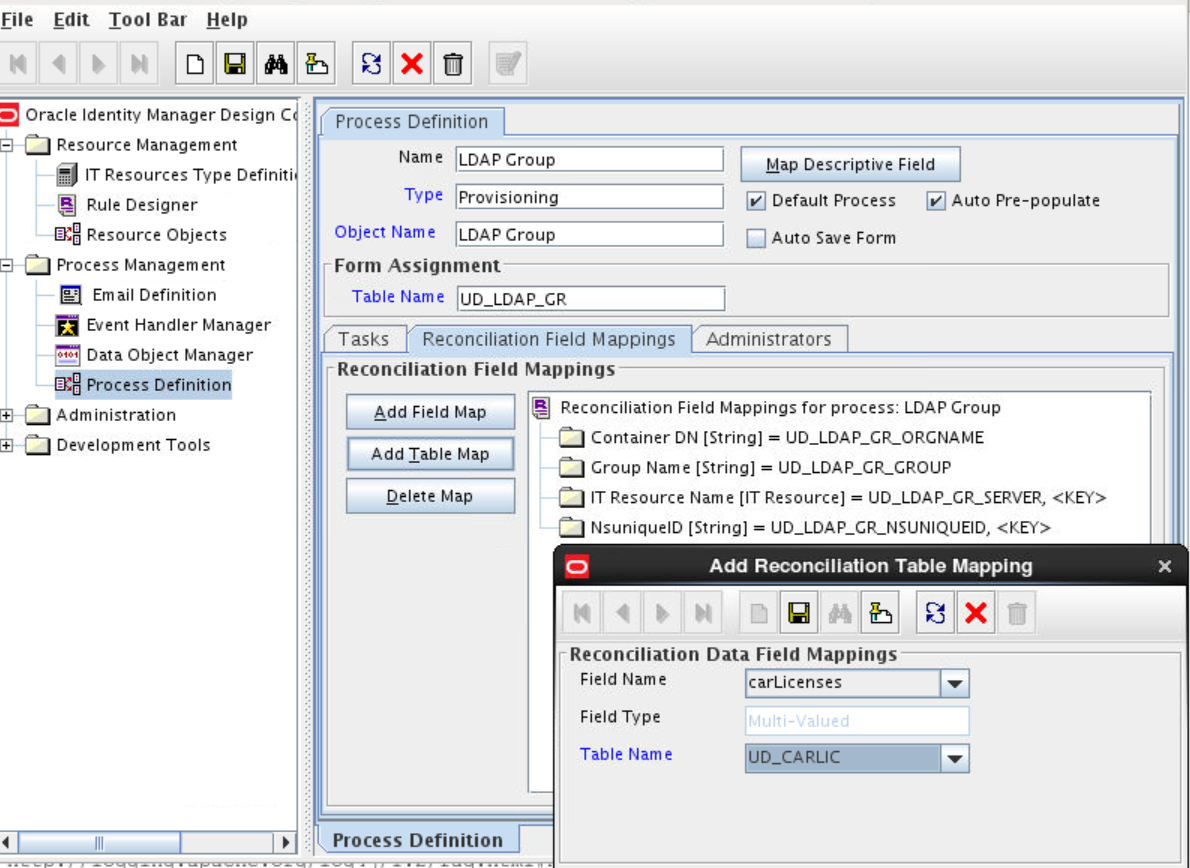
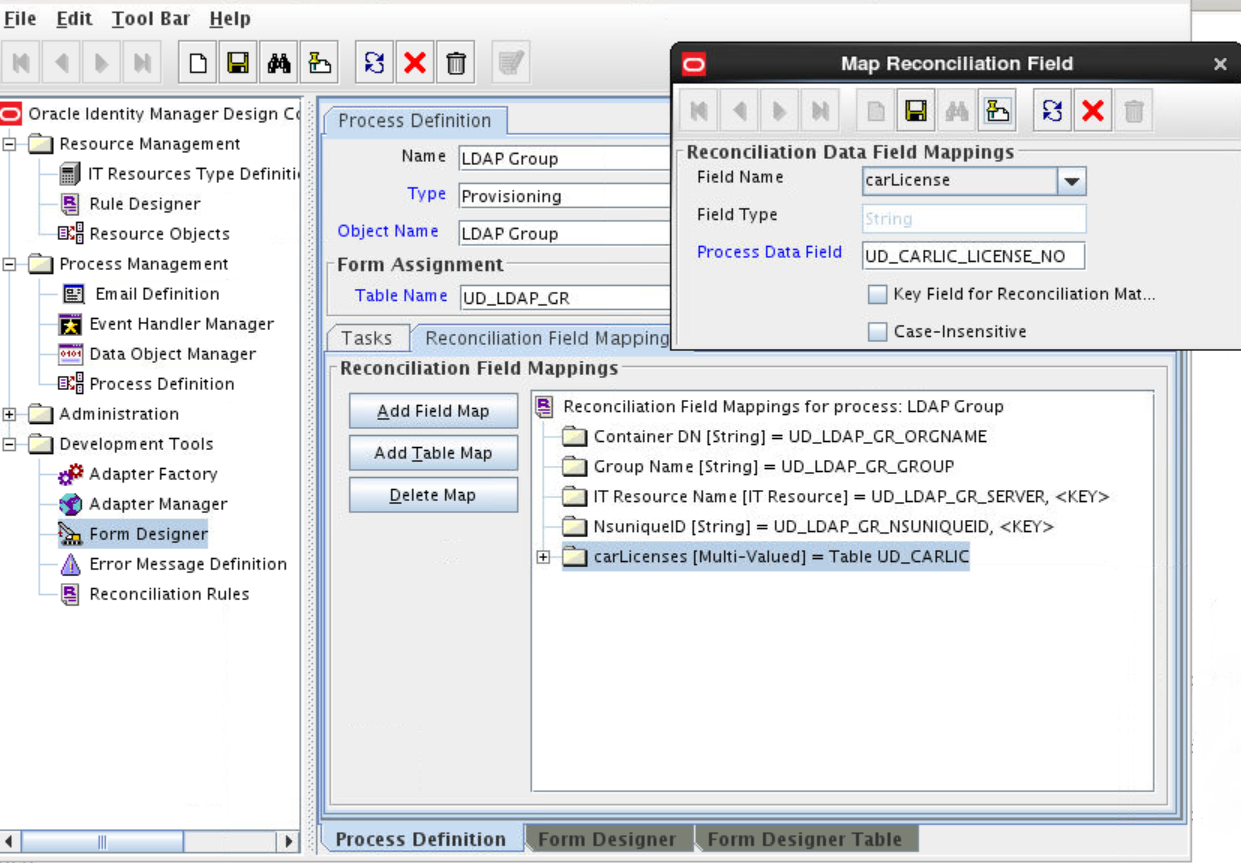
Adding the New Multivalued Field to the Resource Object Reconciliation Fields
Add the new multivalued field to the list of reconciliation fields in the resource object.
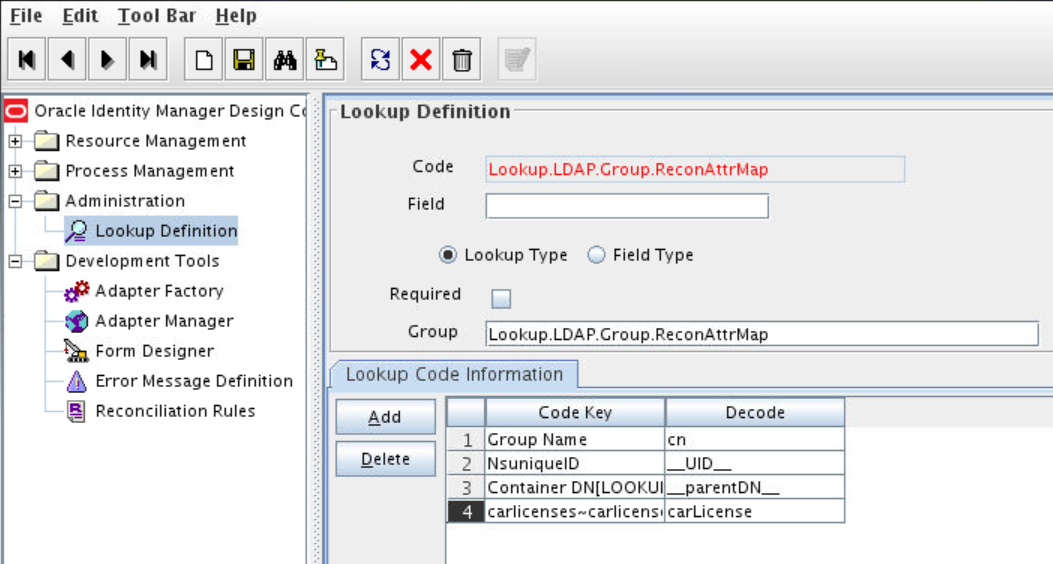
Creating an Entry for the Field in the Lookup Definition for Reconciliation
Create an entry for the newly added field in the lookup definition for reconciliation.
Adding New Multivalued Fields for Provisioning
You can add new multivalued fields for provisioning of users, groups, organizational units, and roles.
Adding New Multivalued Fields for User Provisioning
By default, the multivalued fields listed on the Schema page for your application in Identity Self Server are mapped for provisioning between Oracle Identity Governance and the target system. If required, you can add new multivalued fields for provisioning.
- Log in to Oracle Identity System Administration and create a lookup that can hold the list of values for the multivalued field that you want to add.
- Create a child form and add attributes as follows:
- Log in to Identity System Administration, create a new form and associate it with your application.
See Also:
-
Creating a Lookup Type in Oracle Fusion Middleware Administering Oracle Identity Governance for details about create lookups for your multivalued fields
-
Adding Child Forms in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance for information about creating a child form and adding attributes
-
Configuring Oracle Identity Governance for information about creating a new form and associating it with your application
Adding New Multivalued Fields for Groups, Organizational Units, and Roles Provisioning
By default, the multivalued fields listed in the respective lookup definitions are mapped for provisioning between Oracle Identity Governance and the target system. If required, you can add new multivalued fields for provisioning of groups, organizational units, and roles.
Note:
This section describes an optional procedure. Perform this procedure only if you want to add multivalued fields for provisioning of Groups, Organizational Units, or Roles.
Before starting the following procedure, perform the procedures described in Creating a Form for the Multivalued Field through Associating a New Form With the Application Instance. If these steps have been performed while adding new multivalued fields for target resource reconciliation, then you need not repeat the steps.
To add new multivalued fields for provisioning, perform the following procedures:
-
Creating an Entry for the Field in the Lookup Definition for Provisioning
-
Adding the Task for Provisioning Multivalued Attributes in the Process Definition
-
Running the PurgeCache Utility and Importing the Request Dataset Definition to MDS
Note:
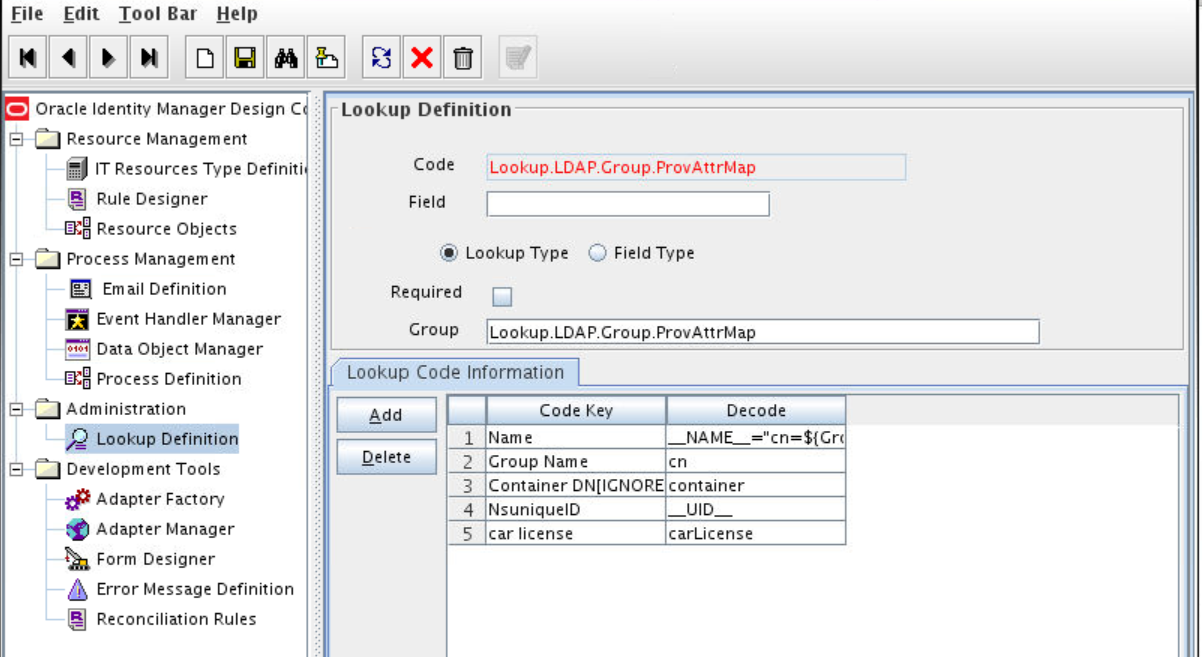
Creating an Entry for the Field in the Lookup Definition for Provisioning
Create an entry for the field in the lookup definition for provisioning as follows:
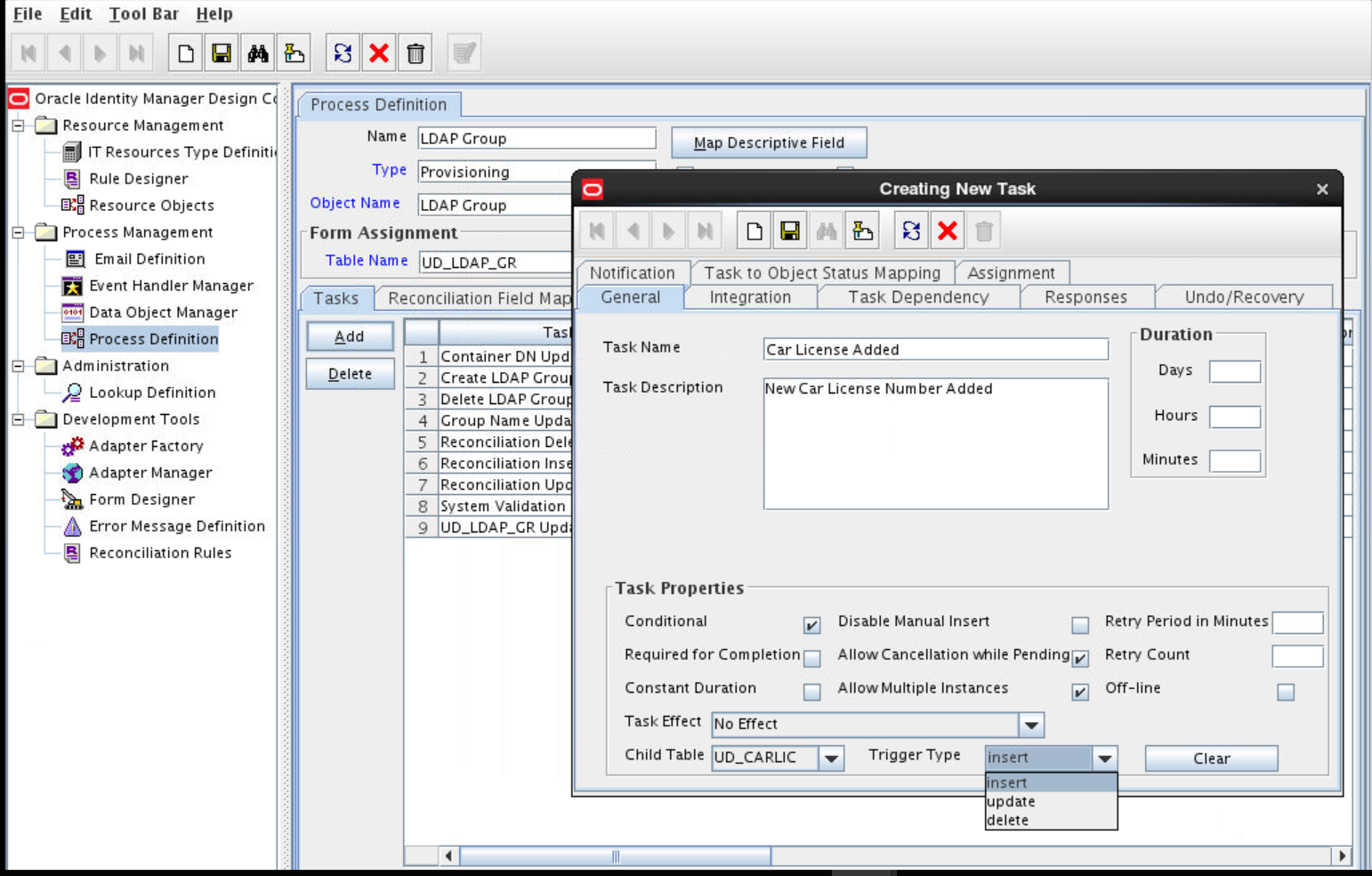
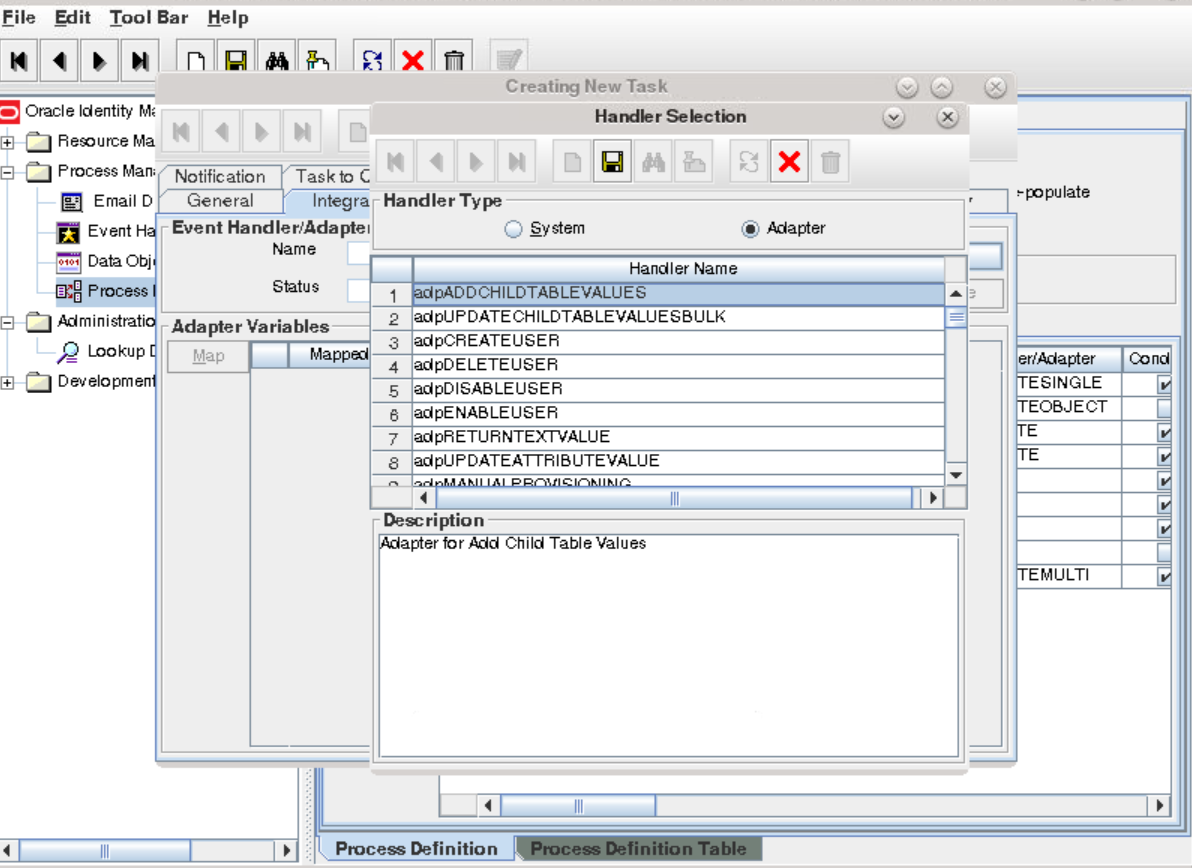
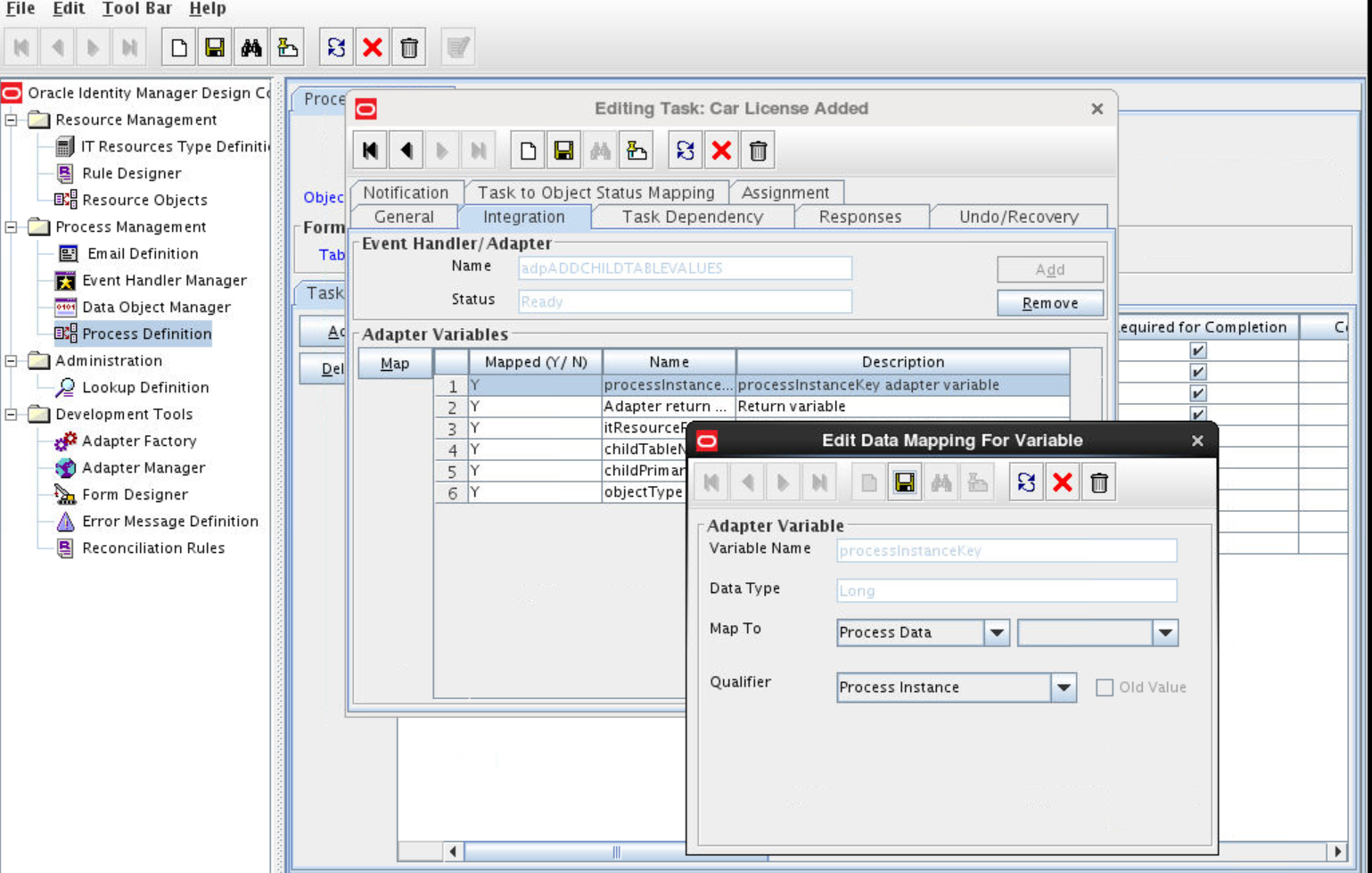
Adding the Task for Provisioning Multivalued Attributes in the Process Definition
To add the task for provisioning multivalued attributes in the process definition, perform the following procedures:
Updating the Process Definition
In the process definition, add the task for provisioning multivalued attributes as follows:
Updating the Request Dataset
Update the request dataset.
Note:
Perform the steps in this section and Running the PurgeCache Utility and Importing the Request Dataset Definition to MDS only if you enabled request-based provisioning.
When you add an attribute on the process form, you also update the XML file containing the request dataset definitions. To update a request dataset:
Running the PurgeCache Utility and Importing the Request Dataset Definition to MDS
Run the PurgeCache utility to clear content related to request datasets from the server cache.
See Purging Cache in Oracle Fusion Middleware Administering Oracle Identity Governance for more information about the PurgeCache utility.
Import into MDS the request dataset definitions in XML format.
Configuring Transformation and Validation of Data
Configure transformation and validation of user account data by writing Groovy script logic while creating your application.
You can configure transformation of reconciled single-valued user data according to your requirements. For example, you can use First Name and Last Name values to create a value for the Full Name field in Oracle Identity Governance.
Similarly, you can configure validation of reconciled and provisioned single-valued data according to your requirements. For example, you can validate data fetched from the First Name attribute to ensure that it does not contain the number sign (#). In addition, you can validate data entered in the First Name field on the process form so that the number sign (#) is not sent to the target system during provisioning operations.
To configure transformation or validation of user account data, you must write Groovy scripts while creating your application. For more information about writing Groovy script-based validation and transformation logic, see Validation and Transformation of Provisioning and Reconciliation Attributes of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Configuring the Connector for User-Defined Object Classes
By default, depending on the target system that you are using, the connector supports the Users, Groups, Organizational Units, or Roles object class. You can configure the connector for user-defined or custom object classes for connector operations.
Note:
This section describes an optional procedure. Perform this procedure only if you want to configure the connector for user-defined object classes.
To configure the connector for user-defined object classes:
Configuring the Connector for Multiple Trusted Source Reconciliation
You can configure this connector for multiple installations of the target system by cloning applications which copies all configurations of the base application into the cloned application or by creating instance applications which shares the configurations as the base application.
For more information about these configurations, see Cloning Applications and Creating Instance Applications in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Note:
Perform this procedure only if you want to configure the connector for multiple trusted source reconciliation.
The following are examples of scenarios in which there is more than one trusted source for user data in an organization:
-
One of the target systems is a trusted source for data about employees. The second target system is a trusted source for data about contractors. The third target system is a trusted source for data about interns.
-
One target system holds the data of some of the identity fields that constitute an OIG User. Two other systems hold data for the remaining identity fields. In other words, to create an OIM User, data from all three systems would need to be reconciled.
If the operating environment of your organization is similar to that described in either one of these scenarios, then this connector enables you to use the target system as one of the trusted sources of user data in your organization.
Configuring the Connector to Support POSIX Groups and Accounts
You can configure the connector to support POSIX groups (posixGroups) and POSIX accounts (posixAccounts).
Note:
You can perform this procedure only for a Target application.After you complete this configuration:
-
The connector will support POSIX groups.
-
The sync reconciliation operation will not return the POSIX group membership changes. You must use the full search reconciliation task to get these changes.
To configure the connector to support POSIX groups and accounts:
-
Log in to Identity Self Service.
-
Search for and open the application you created for the connector for editing.
-
In the Advanced Settings section for your application:
-
Set the value of the maintainPosixGroupMembership parameter to true.
-
Update the accountObjectClasses parameter to include "posixGroup","posixAccount".
-
Update the objectClassesToSynchronize parameter to include "posixGroup","posixAccount".
-
Set the value of the readSchema parameter to
true.
-
-
On the Schema page, update the table under the UserGroup section as follows:
-
In the Target Attribute column, replace the ldapGroups value with posixGroups.
-
Update the table to include the following values:
Display Name Target Attribute Data Type Mandatory Provisioning Property? Recon Field? Key Field? Case Insensitive? GID NUMBER
gidNumber
String
Yes
Yes
No
No
UID NUMBER
uidNumber
String
Yes
Yes
No
No
HOME DIRECTORY
homedirectory
String
Yes
Yes
No
No
-
Save your changes.
-
-
Log in to Oracle Identity Design Console.
-
In the Lookup.LDAP.Group.ProvAttrMap and Lookup.LDAP.Group.ReconAttrMap lookup definitions, add the following mapping as a String:
GID NUMBER to gidNumber
For OID, update the Lookup.OID.Group.ProvAttrMap and Lookup.OID.Group.ReconAttrMap lookup definitions.
-
In the LDAP Group, OID Group, or eDirectory Group resource object, add the GID NUMBER field as follows:
Select the group (LDAP Group, OID Group), Object Reconciliation, Add Field, and then add GID NUMBER.
-
In the LDAP Group, OID Group, process form, add the GID NUMBER field.
-
In the LDAP Group, OID Group, process definition, add the mapping as a String for GID Number.
-
After you are finished, click Create Reconciliation Profile.