2 Creating an Application by Using the Connector
Learn about onboarding applications using the connector and the prerequisites for doing so
Topics
- Process Flow for Creating an Application By Using the Connector
- Downloading the Connector Installation Package
- Copying Third-Party Jar Libraries
- Creating an Application By Using the SAP S/4HANA Cloud Connector
- Creating a Target System User Account for the SAP S/4HANA Cloud Target
- Create System Account for SAP Identity Authentication Service (IAS)
- Application Post Configuration
- Creating an Application By Using the Connector Server
Process Flow for Creating an Application By Using the Connector
From Oracle Identity Governance release 12.2.1.3.0 onward, connector deployment is handled using the application onboarding capability of Identity Self Service.
Figure 2-1 is a flowchart depicting high-level steps for creating an application in Oracle Identity Governance by using the connector installation package.
Figure 2-1 Overall Flow of the Process for Creating an Application By Using the Connector
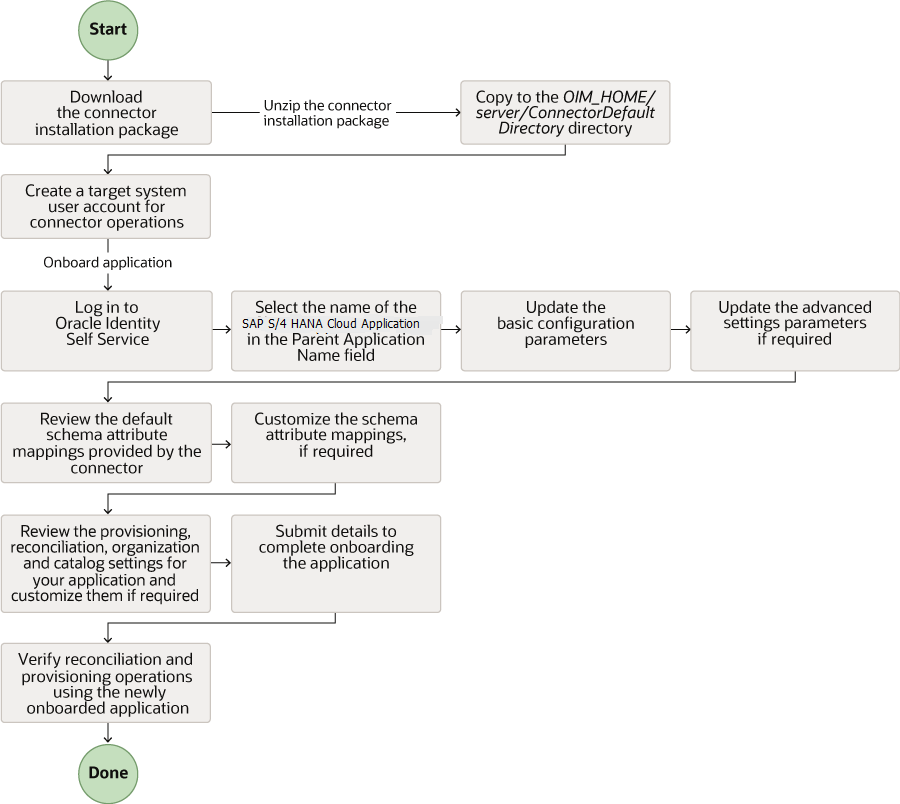
Description of "Figure 2-1 Overall Flow of the Process for Creating an Application By Using the Connector"
Downloading the Connector Installation Package
You can obtain the installation package for your connector on the Oracle Technology Network (OTN) website.
Copying Third-Party Jar Libraries
You can either use third-party jars from the S4HANA-12.2.1.3.0 /lib folder shipped with the connector package or download any latest, stable, and secure version. Please follow the below procedure to include third-party jars:
Creating an Application By Using the SAP S/4HANA Cloud Connector
You can onboard an application into Oracle Identity Governance from the connector package by creating a Target application. To do so, you must log in to Identity Self Service and then choose the Applications box on the Manage tab.
Note:
For detailed information on the steps in this procedure, see Creating a Target Application of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.- Create an application in Identity Self Service. The high-level steps are as follows:
- Verify reconciliation and provisioning operations on the newly created application.
See Also:
-
Configuring the Connector for details on basic configuration and advanced settings parameters, default user account attribute mappings, default correlation rules, and reconciliation jobs that are predefined for this connector
-
Configuring Oracle Identity Governance for details on creating a new form and associating it with your application, if you chose not to create the default form
Creating a Target System User Account for the SAP S/4HANA Cloud Target
The following topics describe the procedures to create a target system user account for the SAP S/4HANA Cloud target:
Create a Communication User
- Log in to SAP S/4HANA Cloud application with administrator credentials.
- Under Communication Management, click Maintain Communication Users.
- Click New to create a new communication user.
The Create Communication User page appears.
- Enter User Name, Description, and password.
- Click Propose Password to get a system-generated password.
Note:
Keep a note of the User Name and password for your communication user. - Click Create.
Create a Communication System
Perform the following steps to create a communication system and assign a communication user to the communication system.
- Log in to the SAP S/4HANA Cloud application with administrator credentials.
- Under Communication Management, click Communication Systems.
- Click New to create a new communication system.
- Enter System ID and System Name, then click Create.
- Under Technical Data, enter the Host Name of your SAP S/4HANA Cloud tenant in the following format:
<tenant ID>.s4hana.ondemand.com - Click User for Inbound Communication tab, then click the add (+) icon.
- Assign the communication user you create and select the authentication method as User ID and Password.
- Click Save.
Create a Communication Arrangement
- Log in to SAP S/4HANA Cloud application with administrator credentials.
- Under Communication Management, click Communication Arrangements.
- Click New to create a new communication arrangement.
- Select communication scenario SAP_COM_0193, enter an arrangement name, and click Create.
- Select Communication Arrangement in the list.
The inbound communication user is automatically assigned.
- Under Inbound Services, the endpoint URLs to call the SOAP service is found in the following format:
- https://<S4HANA tenant ID>-api.s4hana.ondemand.com/sap/bc/srt/scs_ext/sap/managebusinessuserin
- https://<S4HANA tenant ID>-api.s4hana.ondemand.com/sap/bc/srt/scs_ext/sap/querybusinessuserin
- https://<S4HANA tenant ID>-api.s4hana.ondemand.com/sap/bc/srt/scs_ext/sap/querybusinessusermetadatain
- Click Save.
WSDLs can be downloaded from this arrangement once saved.
The same SAP S/4HANA user can be used as a communication user in Oracle Identity Governance to perform all the connector operations.
Create System Account for SAP Identity Authentication Service (IAS)
This account is used to connect to SAP IAS to verify user existence. The User ID must exist here to provision it to S4/HANA Cloud and manage users credential. For more information refer to, Add System as Administrator under SAP Cloud Identity Services - Identity Authentication in SAP Help Portal.
To add a person as a new tenant administrator, proceed as follows:
- Access the tenant's administration console for Identity Authentication by using the console's URL.
- Choose the Administrators tile.
Note:
The URL has the following pattern:https://<tenant ID>.accounts.ondemand.com/admin
Tenant ID is an automatically generated ID by the system. The first administrator created for the tenant receives an activation e-mail with a URL in it. This URL contains the tenant ID. For more information about your tenants refer to Viewing Assigned Tenants and Administrators under SAP Cloud Identity Services - Identity Authentication in SAP Help Portal.
If you have a configured custom domain, the URL pattern is: <your custom domain>/admin.
This operation opens a list of all administrators in alphabetical order.Note:
The list also includes the SAP BTP system, which by default has authorizations to set up the trust with Identity Authentication. - Press the +Add button on the left-hand panel to add a new administrator to the list.
- Choose Add User.
- Make the appropriate entries in the Email, First Name, and Last Name fields for the user you want to add as an administrator.
The E-mail must be unique for the tenant.
The First Name, and Last Name fields are pre-filled automatically for users who already exist in system.
Note:
Once the administrator is created, the First Name, Last Name, and Email fields are not editable from the administrator section. If you want to change the information you must go to the User Management section. For more information refer to List and Edit User Details under SAP Cloud Identity Services - Identity Authentication in SAP Help Portal. - Assign the required administrator roles for the user. To be a tenant administrator, a user must be assigned at least one of the following roles.
Table 2-2 Administrator Roles
Authorization Description Manage Applications This role gives the tenant administrator permission to configure the applications via the administration console. Manage Corporate Identity Providers This role gives the tenant administrator permission to configure the identity providers via the administration console. Manage Users This role gives the tenant administrator permission to manage, import, and export users via the administration console. Read Users This role gives the tenant administrator permission to retrieve user data and import users via the administration console and the SCIM REST API of Identity Authentication. Manage Groups This role gives the tenant administrator permission to create, edit, and delete user groups via the administration console. Manage Tenant Configuration This role gives the tenant administrator permission to manage tenant configuration and authorization assignment to users. Tenant administrators with that role can add additional roles to themselves or to other administrators. Note:
By default, all administrator roles are assigned. - Configure the method for authentication when the system is used.
- Set Password
Note:
You must set password for basic authentication when Identity Authentication is used. The client ID is in the universally unique identifier (UUID) format and will be automatically generated. For example, 1ab7c243-5de5-4530-8g14-1234h26373ab. The password must meet the following conditions:- Minimum length of 8 characters.
- Characters from at least three of the following groups:
- Lower-case Latin characters (a-z)
- Upper-case Latin characters (A-Z)
- Base 10 digits (0-9)
- Non-alphabetic characters (!@#$...)
- Must not include space and the %, +, \, !, #, $, &, ‘, (, ), *, ,, ;, <, >, ^, `, {, |, and } characters.
- The password is locked for 60 min after 5 failed attempts with wrong value.
- Set Password
- Save your changes.
Application Post Configuration
Post the configuration of application, it is a must to add business roles to OIG.
Note:
This step is not appliable if you are using S4HANA-12.2.1.3.0A or a later version.- Login to S/4 HANA cloud tenant.
- Search for Maintain Business Roles.
- Select Business Role ID.
- Click Download Business Roles.
Lookup.S4HANA.Roles. Do the following:
- Login to OIG Identity System Administration console as sysadmin.
- Navigate to System Configuration>Lookups
- Search for Lookup.S4HANA.Roles.
- Click Actions.
- Select Edit.
- Add entries as shown in the following example.
Table 2-3 Example Data Table
Code Decode/Meaning 5~BR_GRANT_RESPONSIBLES4HANA1~Grant Responsible 5~BR_GRANT_SPECIALISTS4HANA1~Grant Specialist
Note:
- The code
<IT Resource Key>~<Business Role ID>Decode/Meaning:<Application Name>~<Business Role Description>. - IT Resource Key is provided using
svr table,andsvr_key column data. - The above steps are applicable for all S4HANA OIG Applications. You must also run the entitlement list for scheduled job.
Creating an Application By Using the Connector Server
Note:
- If you are using Java Connector Server 12.2.1.3.1 version, then all the steps are applicable.
- If you are using Java Connector Server 12.2.1.3.0 version, then step 1 and 6 are only applicable.
- Copy connector bundle jar to the bundles directory of connector server.
- Copy the
jakarta.xml.soap-api-1.4.2.jar from <Middleware_Home>/oracle_common/modules/to the lib directory of connector server. - Copy the
jakarta.activation-1.2.2.jar from <Middleware_Home>/oracle_common/modules/to the lib directory of connector server. - Copy the
stax-ex-1.8.3.jar from <Middleware_Home>/oracle_common/modules/to the lib directory of connector server. - Copy the
saaj-impl-1.5.3.jar from <Middleware_Home>/oracle_common/modules/to the lib directory of connector server. - Restart Connector Server.