2 Product Architecture of Oracle Identity Governance
This chapter provides an overview of Oracle Identity Governance product architecture. It consists of the following topics:
2.1 Oracle Identity Governance Components
Oracle Identity Governance is a J2EE web application. The J2EE platforms consists of a set of industry-standard services, APIs, and protocols that provide the functionality for developing multi-tiered and web-based enterprise applications.
Figure 2-1 shows the various components of Oracle Identity Governance.
Figure 2-1 Oracle Identity Governance Components
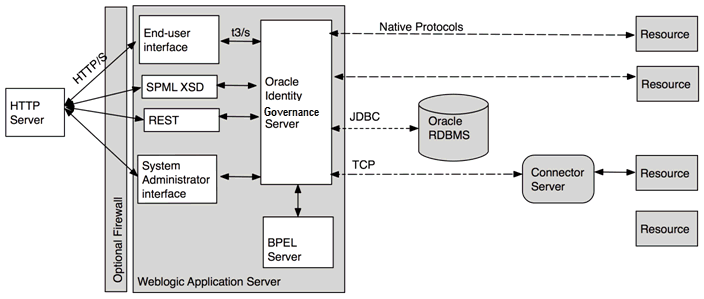
Description of "Figure 2-1 Oracle Identity Governance Components"
2.2 Multi-tiered Architecture of Oracle Identity Governance
The system architecture of Oracle Identity Governance is distributed across logical tiers, namely user interface tier, application tier, database tier, and connector tier.
This section contains the following topics:
2.2.1 About the User Interface Tier
The user-interface tier (or the user tier) consists of administrators and end-users who interact with Oracle Identity Governance through one of the user interfaces.
The main user interface for Oracle Identity Manager is web-based, which communicates with Oracle Identity Manager over HTTP/S. There are two browser-based UIs, the end-user facing Oracle Identity Self Service and the administrator facing Oracle Identity System Administration. These UIs are developed by using the Oracle Application Development Framework (ADF).
Identity Self Service can be customized via the web browser, by system administrators who can add links, add business logic to show/hide form fields, extend shipped forms, and perform several other common UI customization tasks. Administrators perform UI customization tasks in UI sandboxes. These sandboxes can be exported and imported into higher environments. The use of Oracle ADF and UI customization framework allows administrators to customize Identity Self Service in an upgrade-safe manner.
Identity System Administration allows administrators to perform typical system administration functions including scheduling jobs, onboarding applications, and managing schemas. This UI is not customizable.
Developers can use the Design Console to create provisioning workflows and Oracle JDeveloper to create BPEL workflows for manual fulfillment, approval, identity certification, and identity audit.
2.2.2 About the Application Tier
Oracle Identity Manager Server is a J2EE application. It is deployed on Oracle WebLogic Server. The server consists of the Identity Self Service and Identity System Administration web applications, SPML XSD, and REST services, and the EJBs and related Java classes that provide the core functionality. Connectors, which interact with other IT systems, are deployed on the Oracle Identity Manager Server.
Note:
Oracle recommends that you use REST services instead of SPML.
The server comprises of the following functional components:
-
Identity administration
This includes self-registration, lost password and forgotten user ID, user, role, and organization management, and password management.
The user management engine allows administrators to manage users; reset their passwords and grant/revoke/modify access. When integrated with Oracle Access Manager (OAM), the changes in the user profile are synchronized with the LDAP directory used by OAM using a feature called LDAP synchronization.
The role management engine allows business users and administrators to create static and dynamic roles, associate access via access policies, and make the role available to various organizations. These operations can go through approval. After approval, the changes are committed to the Oracle Identity Manager repository. This feature is known as role lifecycle management.
The organization management engine allows administrators to create and manage static or rule-based dynamic organizations. Administrators can define password policies and associate them with organizations, which allows different user communities to have different password policies.
-
Authorization
The authorization engine in Oracle Identity Manager allows granular delegated administration by allowing administrators to define admin roles and associate them with functional capabilities. The authorization engine enforces the policies, which in turn leverage the admin role memberships of the user. Administrators can also define attribute-level permissions for users and specify who can see and modify user attributes.
-
Provisioning
Oracle Identity Manager provides a highly scalable provisioning engine that provides account management and account password management capabilities. Oracle Identity Manager allows administrators to manage accounts and grant/revoke/modify additional access (entitlements). Administrators and end-users can also reset account passwords or configure Oracle Identity Manager so that the user password is synchronized with the accounts provisioned to a user. The provisioning engine supports two types of provisioning, connected provisioning using connectors and disconnected provisioning (or manual fulfillment) where a user has to take some action.
You can use Oracle Identity Governance to create, maintain, and delete users on target systems. In this configuration, Oracle Identity Governance acts as the front-end entry point for managing user data on the target systems. After accounts are provisioned, the users for whom the accounts have been provisioned can access the target systems without any interaction with Oracle Identity Governance. This is the provisioning configuration of Oracle Identity Governance.
A provisioning operation can be started through any of the following ways:
-
Request-Based Provisioning: In request-based provisioning, an individual creates a request for a target system account. The provisioning process is completed when an Oracle Identity Governance User with the required privileges approves the request and provisions the target system account to the requester.
-
Policy-Based Provisioning: This type of provisioning refers to resources being granted to users automatically through access policies. Access policies are used to define the association between user groups (or roles) and target resources.
-
Direct Provisioning: This type of provisioning is a special administrator-only function in which an Oracle Identity Governance administrator provisions a resource to an OIG User. The workflow for this form of provisioning does not include the request and approval steps. You perform direct provisioning by using the Oracle Identity Self Service interface.
-
Automate and Manual Provisioning: Oracle Identity Governance provides automated provisioning to managed applications and target systems upon access grant for both standard and privileged access, using a robust set of connectors. If these grants need to be revoked as a result of monitoring controls, then they can be automatically deprovisioned by using the same connectors, while providing a comprehensive audit trail.
Some of the provisioning actions can be automated if a provisioning connector is deployed for the specific target system and others can be completed manually. For manual fulfillment, an administrator will be assigned a provisioning task, make the appropriate changes in the target system, and then mark the task as ‘completed’ in Oracle Identity Governance. As approval needs can change over the period of time, policy owners can change the approval routing logic using the Identity Self Service interface.
-
Role-Based Provisioning: Any organization that implements a role-based platform for automated provisioning and a personalized portal must first implement an integrated identity-management platform to manage risk, protect sensitive information assets, and improve business performance. An identity management suite also can be used to integrate information portals, providing a sophisticated solution for access management, provisioning, and role management.
A solution that implements role-based provisioning should include four key components:
-
Provisioning platform: The provisioning platform pulls identities from a trusted source (often an HR system) and facilitates provisioning by automatically creating accounts on a target system. It is responsible for synchronizing user data between the HR system and target systems where there are changes to user data, such as new-hires, job role changes, or employee termination. When a user is removed from a role and no longer requires access, the provisioning platform automatically deletes the user privileges from the target system.
-
Role management: Role management organizes user-access rights based on similar responsibilities across the enterprise. For instance, a company might formalize job codes or responsibilities into particular roles that carry their own specific system-access rights and security levels. As a user's role changes, so do the user's access permissions. Oracle Identity Governance pushes these changes to the role manager, which derives user role membership and access information based on the user profile sent from the trusted resource. The provisioning platform and role manager should work in tandem to ensure that provisioning events are based on roles.
-
Access management: An access management platform allows users of applications or IT systems to log in once and gain access to IT resources across the enterprise. This allows the organization to create a centralized and automated single sign-on (SSO) solution for managing who has access to what information across the IT infrastructure.
-
Portal: Portals provide unified access to enterprise information in a personalized fashion. Portals can leverage the access-management platform to authenticate and authorize users. Once the user is authenticated and authorized, the portal presents an interface that can be personalized for each user to display only the data and applications that user has access to.
-
-
-
Reconciliation
The reconciliation engine allows changes in target applications to be detected and synchronized with Oracle Identity Manager. It can retrieve changes from an authoritative source or from a target resource.The reconciliation engine allows changes in target applications to be detected and synchronized with Oracle Identity Manager. It can retrieve changes from an authoritative source or from a target resource. In the former scenario, changes are synchronized with the user, while in the latter, with the account.
-
Access request and approvals
The request engine allows end-users to submit requests for new and modified access, either for themselves or for others. They can use the access catalog to search and browse in a manner similar to online shopping and submit their requests. The requests are routed to the appropriate approvers and fulfilled either in an automated manner by using connectors, or manually by using disconnected provisioning.
-
Identity certification
The identity certification engine allows administrators to define certification campaigns. These campaigns allow managers and authorized users to review and certify the access granted to users. They can delegate certain users or process them themselves. They can reject a user's access, which can trigger a provisioning action to revoke the access. This is called closed-loop remediation.
-
Identity audit or Segregation of Duties (SoD)
The SoD engine allows administrators to define rules and group them into policies. These rules and policies, known as identity audit rules and policies, allow Oracle Identity Manager to detect access that violates compliance rules. Administrators can specify which policies should be enforced during access request, while allowing other policies to be enforced retroactively. When a policy violation is found, the engine assigns the violation to a user for remediation.
-
Auditing
The auditing engine audits (or logs) various actions in Oracle Identity Manager. Administrators can also add custom audit events. The audit data can be reported on using the reporting capabilities of Oracle Identity Manager.
-
Embedded reporting server
The embedded reporting server, based on Oracle BI Publisher, provides operational and historical reports. Administrators can also use standalone BI Publisher or use the schema information to create reports using any other reporting tool.
-
BPEL workflow engine
Oracle Identity Manager uses BPEL to provide workflow orchestration for approval, manual fulfillment, identity certification, and identity audit. Administrators or developers can define BPEL workflows or SOA composites and use workflow rules to dynamically invoke these workflows. BPEL provides data-driven approver resolution, task expiration, and escalation and email-based actionable notification. Oracle JDeveloper can be used to create new workflows and register them in Oracle Identity Manager.
2.2.3 About the Database Tier
Oracle Identity Manager stores all its information in the Oracle Identity Manager repository. The repository is comprised of tables that store the configuration, state, and other data.
Oracle Identity Manager keeps a copy of the account and entitlement data that is provisioned to the user, allowing it to be the source of truth for identity and account data.
Oracle Identity Manager also makes use of other schemas to store metadata about the workflows, approvals, configuration, and authorization policies.
Because Oracle Identity Manager can accumulate state data, it provides archival and purge utilities to manage data growth. Administrators must follow the product recommendations to manage data growth for optimal performance.
2.2.4 About the Connector Tier
The connector tier consists of applications and IT systems to which you provision and deprovision user accounts, change the account password, and grant/revoke entitlements.
The connector tier also includes the connector server, which is a lightweight application that allows Oracle Identity Manager to manage applications that do not provide remote APIs or require native integration.
Typically, Oracle Identity Manager connectors are developed by using the Identity Connector Framework and are deployed with the server. In some cases, where a connector server is required, they are deployed on the connector server.
You can create your own connectors by using the Identity Connector Framework, a lightweight and easy to use framework for developing connectors.