14 Managing Identity Audit
This chapter describes about the Identity Audit feature in the following topics:
14.1 About Identity Audit
The identity audit feature detects SoD violation or identity audit policy violation, which is a violation whereby a user has been assigned privileges that should not be held individually or in combination.
Identity audit enables the creation of rules and policies that detect potentially dangerous combinations of privileges held by users or roles that can lead to access violation, and determines policy violations and policy violation causes.
This feature can be enabled or disabled by setting the value of the Identity Audit system property to true or false respectively. See Managing System Properties in Administering Oracle Identity Governance for information about this system property. Also, in an upgraded deployment of Oracle Identity Manager, you must manually set the value of the Workflows policies enabled system property in order to use the identity audit and role lifecycle management features.
14.2 Understanding Identity Audit Concepts
Key concepts related to identity audit are detection mechanism, identity audit rules, rule conditions, identity audit policies, scan definitions, scan jobs, policy violations, remediators, policy violation remediation, and policy violation reports.
The concepts related to Identity Audit are described in the following topics.
14.2.1 About Modes of Detection
Identity audit uses detective mode or preventive mode for detecting policy violations.
You can use Identity Audit to detect SoD violations. The detection mechanism of Identity Audit monitors users' actual access to resources, and captures any violations on a continuous basis. This can be one of the following types:
-
Detective mode: In a detective mode, the entire identity warehouse of users can be monitored for anomalies or toxic combinations of user access rights.
-
Preventive mode: In preventative mode, any access that is requested via the access catalog in real-time can be automatically detected as an Identity Audit policy violation, and preventative action can be taken.
There may be multiple audit policies defined. A single audit policy detects a specific violation on users. An audit policy is composed of one or more audit rules, and each rule detects a cause of the violation. User profiles as well as their associated roles, accounts, entitlements, and organizations are then scanned for identity audit policy violations. User accounts (including entitlements), user attributes, and roles/access policies that violate an identity audit policy are flagged and tracked until the violation is resolved. The solution also maintains a comprehensive history of audit scans.
14.2.2 About Identity Audit Rules
An identity audit rule consists of a rule condition. These rules can be simple or complex based on the entities and user access privileges. You can define complex rules with nested conditions on the basis of user information, catalog metadata associated to applications, entitlements, roles, and organization metadata.
An identity audit rule can be associated with multiple policies. When a rule condition is modified, all policies associated with this rule are impacted. If the modified rule is the cause of any existing open violations in the system, then the cause and the associated violation are impacted by the change in condition.
A rule can be specified by entering an IF condition, and then return values when the condition matches.
Rules are associated with policies. When entities associated with an impacted violation are scanned against the policies associated with the rule, Oracle Identity Manager takes the following actions on the violation:
-
Oracle Identity Manager checks whether the modified condition still causes an exception.
-
If the rule condition still results in an exception, then Oracle Identity Manager sets the violation cause status to Active. Otherwise, the violation cause status is set to Inactive.
Identity audit rules must be owned by a user. Any user can be a rule owner irrespective of the admin role privileges of the user.
Note:
-
See Managing Administration Roles for information about admin roles and admin role capabilities.
-
The following admin role capabilities related to identity audit policies cannot be used from Identity Self Service, but can be used through APIs:
-
Identity Audit Policy - Assign Rule
-
Identity Audit Policy - Unassign Rule
-
Identity Audit Policy - Disable
-
Identity Audit Policy - Enable
-
Identity Audit Policy - Assign Rule
-
Identity Audit Policy - Unassign Rule
-
Identity Audit Rule - Enable
-
Identity Audit Rule - Disable
-
Identity Audit Scan Run - Delete
For information about using APIs, see Using APIs in the Developing and Customizing Applications for Oracle Identity Governance and Java API Reference for Oracle Identity Governance.
-
You can add new rules to an existing policy. However, this change can impact some existing unresolved violations. The next time the modified policy is scanned, existing open violations that are impacted by this change are updated and new ones are created if the new rules have caused exceptions.
14.2.3 About Rule Condition
A rule has a single condition. A rule's condition is the IF portion of the rule and is evaluated to be either true or false against the input values passed to the rule at policy evaluation time.
A condition is a set of one or more criteria, which can be logically conjugated together with AND or OR operators. The criteria can be grouped, and the groups can be logically conjugated together with AND or OR operators. This allows for complex nested Boolean expressions. A condition criterion consists of an attribute, operators, and value, as shown:
Condition criterion = ATTRIBUTE OPERATOR VALUE
14.2.4 About Identity Audit Policies
An identity audit policy is a collection of audit rules that together enforce SoD business policies. Identity audit policies consist of metadata, such as the identity audit policy name, description, severity, creation date, and update data. Identity audit policies have designated policy owners and policy remediators.
An identity audit policy must be owned by any user. The policy owner can create, search, view, modify, or delete policies.
By default, policies will report a violation if any of its rules evaluate to true.
An identity audit policy owner is responsible for the definition of the policy. However, it is the remediator's responsibility to take action on an identity audit policy violation and fix the violation.
14.2.5 About Scan Definitions
An identity audit scan is the action of executing an identity audit policy along with its associated rules against a given population of entities (users). A scan definition specifies a particular identity audit scanning ‘recipe’ that can be used by a scheduled task to run and repeat the desired scan in the future.
Scan definitions contain a base selection of users or organizations to scan, and a collection of one or more policies to evaluate when scanning. In addition, other configuration settings can also be specified in a scan definition.
Scan definitions act as templates that configure a scheduled task (scan job) with audit scan parameters. Scan definitions themselves contain no scheduling information.
Identity Audit scan can be of the following types:
-
Detective scan: A scheduled job that performs an Identity Audit scan according to a specified Identity Audit scan definition, and generates a persistent policy violation for each user SoD conflict that it detects. This type of scan is used to find latent problems in access privileges.
A detective scan is the process of applying a scan definition to a user population and generating Identity Audit policy violations. A scan definition consists of policies and user-selection criteria. Each policy contains rules that define the combination of access privileges that will result in a violation being detected by the scan. Detective scans are run as Oracle Identity Manager scheduled jobs. Detected violations are persisted to the data store if they are new and updated if they already exist. You can also use the capability of running a detective scan on-demand for a single policy in a "preview" mode. In preview mode, the scan returns a collection of preview violations that it has detected, but these violations are not actionable and can only be saved temporarily.
-
Preventive scan: A synchronous (not scheduled) Identity Audit scan that reports a list of violations. This type of scan is used to detect hypothetical policy violations that might be introduced as a direct result of a particular access grant during the request process.
A preventive scan is a synchronous IDA scan that returns a list of potential violations against a specified set of IDA policies, initiated as part of access request processes. This type of scan is used to detect potential policy violations that would be introduced if a particular request is submitted by a requestor. The preventive scan violation results may be discarded, or the requestor can be stopped from submitting the request. OIG IDA provides APIs for invoking preventive scans and for managing their results. The IDA Policies included in a preventive scan are those policies marked with the Evaluate flag during access request.
14.2.6 About Scan Jobs
You can save an identity audit scan as a scheduled task. This scheduled task is called scan job that you can run to perform an audit scan.
An identity audit scan can be effectively saved as a scheduled task (a scan job) in the Oracle Identity System Administration that performs an audit scan, using selection criteria from its scan definition with a preface of Identity Audit_ScanDefinitionName, and can be scheduled by an administrator with a given date and time, or on a repeated basis.
Multiple scan jobs can exist, allowing individual scans to be performed on their own schedule. Multiple scan jobs can run concurrently.
14.2.7 About Policy Violations
An identity audit policy violation occurs if one or more rules associated with an identity audit policy is broken by a user account (including entitlements within the account), a user attribute, or a user role.
The goal here is for the solution to track the violation until it is resolved. The solution must display a unique violation per policy and the objects, such as users, roles, entitlements, and accounts, that have been violated within the policy. By default, a policy violation occurs when one or more rules associated with a policy is matched by a user account including entitlements within the account, a user attribute, or a user role.
14.2.8 About Remediators
An identity audit policy must have one or more remediators. A remediator can be a role, a manager, or any user with or without any particular role associated.
You cannot assign multiple users as remediator. Assigning multiple users as remediator can be achieved only by assigning any role as the remediator. A remediator is responsible for fixing an identity audit policy violation or for reassigning the violation to another eligible remediator.
Identity Audit policies have designated remediators who are responsible for taking action when violations are discovered. Notification for policy violations are sent to the Inbox of the remediators. When a policy detects a violation during a scan, the violation is assigned to the remediator(s) designated by the policy. Remediators are notified when they have been assigned a new policy violation. The remediator role allows remediators to view and edit their assigned policy violations.
A remediator may reassign a policy violation to another eligible remediator, after which the original remediator is no longer responsible for the policy violation and can take no further action on it or reclaim it.
14.2.9 Understanding Policy Violation Remediation
Policy violation remediation involves generation of policy violation tasks based on the policy violation causes. A policy violation transitions through a sequence of states during the remediaton process.
This section describes about policy violation remediation in the following topics:
14.2.9.1 About Policy Violation Remediation
An Identity Audit scan creates a Policy Violation when the scan detects a target entity (for example, a User) matching one or more rules specified in the policy set referenced by the scan definition. The Policy Violation comprises a set of attributes including the violation target, the policy violated, a violation count, along with a collection of (Policy Rule) Violation Causes. Violation Causes are included to give remediators specific information about the rule conditions that produced the Segregation of Duties conflict. A remediation task is created and assigned to the remediator(s) designated by the policy to initiate the remediation workflow.
14.2.9.2 About Violation Causes
Each violation cause includes the rule, condition, and attributes resulting in the violation.
14.2.9.2.1 About Violation Cause Actions
The remediator can take one of the following actions:
-
Request for Remediation (remediate): This action is available for causes that involve catalog items, such as user role, account, and entitlements, within the account. The remediator requests revocation of the catalog item mentioned as a cause of the violation.
-
Close As Fixed: The remediator has taken an action independent of the provisioning system to fix the violation cause.
-
Close As Risk Accepted: This action indicates that the violation cause condition should be ignored in subsequent policy re-evaluations for a limited time.
14.2.9.2.2 About Violation Cause States
An Identity Audit policy violation transitions through a sequence of states during the remediaton process. The possible states of an Identity Audit policy violation are:
-
Active: The initial state of a violation cause. This state indicates that the rule condition still matches.
-
Risk Accepted: The state after the remediator temporarily disables a rule condition by selecting the Risk Accepted action. This state expires when the specified time limit is reached, and the rule condition is evaluated at the subsequent scan.
-
Manually Fixed: The state after the remediator takes the Close as Fixed action.
-
Remediation Requested: The state after the remediator takes the Request Remediation action.
-
Resolved: This state is set by system when a scan detects that a violation cause condition no longer matches the target entity. Typically, resolved state is reached when a remediator's action has been applied and an identity audit scan confirms it. However, an external change to the remediation can also resolve a violation cause.
Remediators take action on violation causes to resolve the identity audit policy violation so that it no longer matches any rule of the violated policy. Subsequent scans re-evaluate the policy (re-apply the rules to the target entity) and confirms if the violation cause has been resolved and update the violation cause statuses accordingly. The remediator can also indicate that a violation cause can be accepted (ignored) for a limited time.
14.2.9.3 About Policy Violation States
An Identity Audit policy violation transitions through a sequence of states during the remediaton process. The possible states of an Identity Audit policy violation are:
-
Open: The initial state of Policy Violation, before it is assigned to the remediator(s) designated by the policy.
-
Assigned: The state after an Identity Audit Policy Violation has been assigned to a remediator.
-
Remediation In Progress: The state after the first remediator action and until the remediator completes the remediation.
-
Remediation Under Review: Policy Violation state is moved to this state if the remediation has overseers. The Policy Violation remains in this state until the last reviewer action.
-
Remediation Completed: The state after the remediation (and review, if required). From this state, an Identity Audit Scan either closes or re-opens the Policy Violation.
-
Closed: The state after an Identity Audit Policy Violation is evaluated and no outstanding violations are detected. An administrator can also force the Policy Violation into this state by invoking the Close action.
14.2.10 About Policy Violation Reports
Oracle Business Intelligence Publisher is used for Identity Audit Policy Violation Reports. Reports are available in BI Publisher RTF template format.
BI Publisher uses the appropriate SQL queries (defined in the data model) to query Oracle Identity Manager database (specifically IDA tables) for the violation data.
Identity Audit Policy Violation Reports are available for download from Reports link in the Compliance tab of Oracle Identity Self Service. An Identity Audit Policy Violation report can be generated for a Policy, Scan Stop Date, Manager, Remediator or selected users.
For information about generating identity audit policy violation reports, see Generating Identity Audit Policy Violation Reports.
For information about each type of identity audit policy violation report, see "Identity Audit Reports" in the Administering Oracle Identity Governance.
14.3 Enabling Identity Audit
By default, the Identity Audit feature is disabled in a Oracle Identity Manager deployment. As a result, the Compliance tab of the Identity Self Service is not available. You can enable Identity Audit by setting the value of the Identity Auditor Feature Set Availability system property to TRUE.
To enable Identity Audit:
14.4 Configuring Identity Audit
After enabling identity audit, you can configure the way identity audit will work. This involves setting the Identity Audit options, and configuring reminders, notifications, escalations, and expiry for identity audit.
This section describes how to configure Identity Audit after it is enabled. It contains the following topics:
14.4.1 Setting Identity Audit Options
After identity audit is enabled, you can configure the way identity audit will work by using the Configuration page in Identity Self Service.
To configure identity audit:
14.4.2 Understanding Configuring Reminders, Notifications, Escalations, and Expiry for Identity Audit
If email notifications is configured in SOA, then email notifications are sent by default when a policy violation is assigned to a user or when a policy violation is completed. You can optionally change this default configuration by using Oracle SOA Composer.
This section describes about configuring reminders, notifications, escalations, and expiry for identity audit in the following topics:
14.4.2.1 Understanding Email Notification and Reminders for Identity Audit
If email notifications is configured in SOA, as described in "Configuring SOA Email Notification" in the Administering Oracle Identity Governance, then email notifications are sent by default in the following scenarios:
-
when a policy violation is assigned to a user
-
when a policy violation is completed
By default, two reminders are sent one day after and two days after the policy violation task has been created. There is no escalation or expiry set for the policy violations by default.
14.4.2.2 Configuring Reminders, Notifications, Escalations, and Expiry for Identity Audit (Optional)
To change the default configuration for identity audit:
-
Login to Oracle SOA Composer with Admin credentials, such as weblogic, by navigating to the following URL:
http://HOST_NAME:PORT_NUMBER/soa/composer
-
Expand the composites, click Default, and select IdentityAuditRemidiation. The Event Driven Configuration page is displayed.
-
In the Notification Settings section, perform the following:
-
The assignees of the task are selected as recipients of the notification for Assign and Complete tasks. To change the default setting, you can select the task status in the Task Status column, and select the notification recipient in the Recipient column. You can click the pencil icon for each task to edit the default notification message, and click OK.
-
In the drop-down below, change the default setting for reminders.
-
-
In the Expiry and Escalation Policy section, you can change the default value for escalation and expiry.
-
Click Publish to save the changes.
14.5 Managing Identity Audit Rules
Managing identity audit rules involves searching identity audit rules, creating rules using rule expressions, and modifying, duplicating, and deleting identity audit rules.
This section describes how to create and manage Identity Audit rules. It contains the following sections:
14.5.1 Searching Identity Audit Rules
You can perform basic and advanced search for identity audit rules in the Rules page of Identity Self Service.
This section describes how to perform basic search and advanced search for rules:
14.5.1.1 Performing Basic Search for Identity Audit Rules
To perform a basic search for Identity Audit rules:
- In Identity Self Service, click the Compliance tab.
- Click the Identity Audit box, and select Rules. The Rules page is displayed.
- If fields for advanced search is displayed, then click Basic. Otherwise, ignore this step and continue with step 4.
- From the Search list, select an attribute based on which you can search the rules. The attributes are Rule Name, Description, Created Date, and Owner Login.
- In the Search box, enter a value of the selected attribute as the search criterion.
- Click the Search icon. The search result is displayed in a tabular format.
14.5.2 Creating Identity Audit Rules
You can create identity audit rules by using the Create option from the Rules page of Identity Self Service, and specifying the rule conditions in the Condition Builder.
To create Identity Audit rules:
-
In Identity Self Service, click the Compliance tab.
-
Click the Identity Audit box, and select Rules. The Rules page is displayed.
-
From the Actions menu, select Create. Alternatively, click Create on the toolbar. The Create Rule page is displayed.
-
In the Name box, enter a name of the rule. This is a mandatory field.
-
In the Description box, enter a description for the rule.
-
Click the search icon adjacent to the Owner box, and search and select a user.
-
Verify that Enabled is selected in the Status list so that the rule you create is in enabled state. By default, rules are in enabled state. To disable the rule, you can select Disabled from the Status list.
-
In the Condition Builder section, click the icon to the right of the Condition field to open the Condition Builder dialog box to start building your condition. The Condition Builder dialog box enables you to search and navigate through all the attributes so that you can select them to include in your rule condition.
-
Search for an entity type based on which you want to specify the condition, for example User.
-
Click User. The user attributes are displayed.
-
Search for the user attribute that you want to include in the rule condition, for example, Manager Display Name. Alternatively, you can navigate through the user attributes by clicking the page number icons, and then select the attribute.
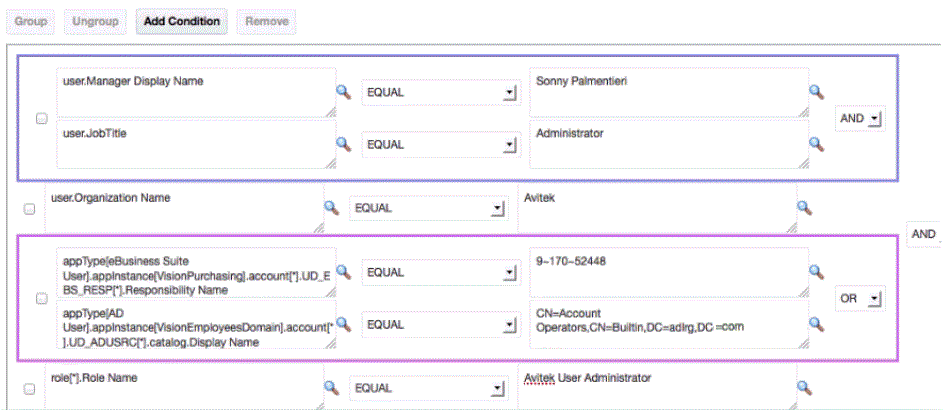
Click OK. The following expression is added in the Condition field:
user.Manager Display Name
-
From the list of operators, select an operator, such as EQUAL.
-
In the right hand side field, enter the Manager Display Name, for example, Sony Palmentieri. Alternatively, you can click the icon adjacent to the field to open the Condition Builder dialog box. To specify the Manager Display Name, select any one of the following:
-
Value: Selecting this option enables you to select a specific value for the attribute.
Note:
If you select value, based on the left hand side, only the values for that field are displayed. However, the values are not displayed for all attributes. For some attributes, the value must be entered.
-
Expression: Selecting this option enables you to specify an expression based on the selected attribute, for example
$(user.Country).
Search and select the desired value, and click OK. The value is added to the right hand side field, and adding the first line of the rule condition is complete.
Note:
You can enter an expression in the rule condition fields instead of searching and selecting the values.
-
-
To add another line to the rule condition, click Add Condition.
To remove a line from the rule condition, you can select the checkbox to the left of the line, and then click Remove. You can select multiple checkboxes to remove those lines at a time.
-
From the operators list to the right of the first line, select AND. This is to specify that both the first and second lines must be true.
-
In the left hand side field, enter the expression or search and select the attribute. For the purpose of this example, specify
user.Job Title. Select theEQUALoperator, and specify a value for the Job Title attribute in the right hand side field, for example, Administrator. -
Add another line and specify the following:
user.Organization Name EQUAL Avitek
-
To group the first two lines together, select the checkboxes adjacent to the first two lines, and click Group.
You can ungroup the lines by selecting the checkboxes adjacent to the lines and clicking Ungroup.
Note:
You can group only two conditions at a time. If you select more than two conditions, then the Group button is disabled. Alternatively, the Ungroup button is enabled only when you select one of the conditions that is grouped, but it is disabled when you select more than one group.
-
Add the fourth line, and click the icon to the right of the condition field to open the Condition Builder dialog box.
-
To add an entitlement, make the following selections:
-
Select Application. The application types are displayed.
-
Then select the resource, for example eBusiness Suite User. click appinstance.
-
Select Vision Purchasing as the application instance.
-
Select account as you are selecting an entitlement, and select wildcard character * to specify all accounts.
Click the arrow in the first row to go back, and then select UD_EBS_RESP as the entitlement, and select wildcard character * to specify all responsibilities.
Note:
For application instances, there is no mechanism to filter out the attributes. All the attributes for application instances are displayed in the Condition Builder with which a rule can be written.
For roles, select the role name to display the list of attributes for the role entities. You can select the asterisk (*) wildcard character to display the list of attributes.
-
Select Responsibility Name.
Note that the selection is displayed at the top of the dialog box, as follows:
Home > appType[eBusiness Suite User].appinstance[Vision Purchasing].account[*].UD_EBS_RESP[*].Responsibility Name
-
Click OK. The expression is added in the condition field.
-
Select EQUAL and specify a value for the Responsibility Name, such as
9~170~52448.
-
-
Add another line, and add an expression for the entitlement of the AD User resource in the condition field. The expression can look similar to the following:
appType[AD User].appinstance[VisionEmployeesDomain].account[*].UD_ADUSRC[*].catalog.Display Name
-
Select EQUAL and specify a value for the Display Name, such as CN=Account Operators,CN=Builtin,DC=adlrg,DC=us,DC=mydomain,DC=com.
-
Group the fourth and fifth lines and specify OR operator between them. If you do not specify an operator, then it is taken to be AND by default.
-
Join the first and second groups with an AND operator.
Note:
A maximum of two conditions can be grouped together. Therefore, if you create a rule with four conditions that are grouped together with the AND operator, then the conditions are grouped into two sets. But if one of the conditions are grouped with the OR operator, then rule is updated correctly.
-
Click Create. The rule is created and the Rules page is displayed. To display the rule you created in the search result of the Rules page, you can click Refresh.
Note:
When Risk attributes are used to define the conditions in a rule, for the rule to be evaluated correctly, the Risk Aggregation Job scheduled job must be run before the request is made.
14.5.3 Understanding Identity Audit Rule Expressions
Some sample identity audit rules include rules for testing the group name attribute, finding conflicting attribute values within a single entitlement in a single account, and finding conflicting attribute values within the same account.
This section describes the following sample Identity Audit rules:
-
There are restrictions on how rules can be written when their conditions involve account entitlements. Identity Audit rules that use catalog-based conditions do not produce matches if the entitlements are being requested as child form data in a new/modify account request. For example, if a user requests an ActiveDirectory group entitlement as part of an account request in the AD Group form, then the following rule operand does not match the name of the AD group:
appType[AD User].appInstance[VisionADAppInst].account[*].UD_ADUSRC[*].catalog.Display Name
To work around this restriction, the operand must be testing for the group name attribute (Group Name) directly, as shown:
appType[AD User].appInstance[VisionADAppInst].account[*].UD_ADUSRC[*].Group Name
-
The following rule shows how to find conflicting attribute values within a single entitlement in a single account by using the discriminator character
#:appType[*].appInstance[*].account[#x].UD_VISDUMC[#x].VISDUM lookup == 8~CN=VISDUM1,DC=abc,DC=com AND appType[*].appInstance[*].account[#x].UD_VISDUMC[#x].ss == admin
In this example, both the rule conditions reference the same entitlement (in bold).
-
The following rule shows how to find conflicting attribute values within the same account by using the discriminator to pin the account instance:
appType[AD User].appInstance[VisionADAppInst].account[#x].Organization Name == 6~OU=Vision,DC=oia,DC=mydomain,DC=com AND appType[AD User].appInstance[VisionADAppInst].account[#x].Department == avitek
14.5.4 Modifying Identity Audit Rules
Modifying identity audit rules involves searching and opening the rule, and then using the Condition Builder to edit the rule conditions.
To modify a rule:
14.5.5 Duplicating Identity Audit Rules
You can use the rule conditions specified for a rule in another rule by duplicating the rule.
To duplicate a rule:
14.6 Managing Identity Audit Policies
Managing identity audit policies involves searching, creating, modifying, duplicating, and deleting identity audit policies, and previewing the results of identity audit policies.
This section describes how to create and manage identity audit policies. It contains the following sections:
14.6.1 Searching Identity Audit Policies
You can perform basic and advanced search for identity audit policies in the Policies page of Identity Self Service.
This section describes how to perform basic search and advanced search for identity audit policies:
14.6.1.1 Performing Basic Search for Identity Audit Policies
To perform a basic search for Identity Audit policies:
- In Identity Self Service, click the Compliance tab.
- Click the Identity Audit box, and select Policies. The Policies page is displayed.
- If fields for advanced search is displayed, then click Basic. Otherwise, ignore this step and continue with step 4.
- From the Search list, select an attribute based on which you can search the policies.
- In the Search box, enter a value of the selected attribute as the search criterion.
- Click the Search icon. The search result is displayed in a tabular format.
14.6.2 Creating Identity Audit Policies
You can create identity audit policies by using the Create option from the Policies page of Identity Self Service, and specifying values for the policy attributes and adding one or more rules to the policy.
To create Identity Audit policies:
-
In Identity Self Service, click the Compliance tab.
-
Click the Identity Audit box, and select Policies. The Policies page is displayed.
-
From the Actions menu, select Create. Alternatively, click Create on the toolbar. The Create Policy page is displayed.
-
Enter values in the fields of the Create Policy page, as described in Table 14-2.
Table 14-2 Fields in the Create Policy Page
Field Description Name
The Identity Audit policy name.
Description
The description for the Identity Audit policy.
Status
The status of the Identity Audit policy, which is Enabled by default.
Owner
The display name of the policy owner. Click the search icon adjacent to this field to search and select a policy owner.
Type
The policy type is Identity Audit by default. This value cannot be modified because only policies of type Identity Audit can be created from the Create Policies page.
Severity
Select a severity level, such as High, Medium, or Low, which will be associated with the policy violations generated by this policy.
Evaluate during Requests
Select this option to display the policy violation during user's access request. User can either cancel the request or submit the request with violation.
Disable Close as Risk Accepted Action Select this option to disable the Close As Risk Accepted action for any violation corresponding to the policy.
Workflow Name
The workflow name that will be invoked during a user's access, if you select the Evaluate during Requests option. By default, the
default/Identity/AuditRemediationworkflow is selected.Remediator
Specify a remediator for violations generated by the policy. To do so, select any one of the following:
-
User: Select this option to specify a user as the remediator. Search and select the user by clicking the Search icon.
-
Manager: Select this option if you want the manager of the user for whom the violation is generated to be the remediator.
-
Role: Select this option if you want to specify the members of a certain role to be the remediator. Search and select the role by clicking the Search icon.
-
-
To add one or more rules to the policy:
-
Click Add. The Add Rule dialog box is displayed.
-
Search for the rule or rules that you want to add to the policy. To do so, select a rule attribute name from the search list, enter a search criterion on the search field, and click the Search icon. The rules that match the search criterion are listed in the Results table.
-
Select one or more rules that you want to add to the policy, and click Add Selected. To select all rules, you can click Add All. The selected rules are added in the Selected Rules table.
-
Click Select. The selected rules are added to the table in the Create Policy page.
-
(Optional) To remove any rule from the table in the Create Policy page, select the rule, and click Remove.
-
-
Click Create. The policy is created. The policy is listed in the Policies page. You can now run a preview of the policy.
14.6.3 Modifying Identity Audit Policies
Modifying identity audit policies involves searching and opening the policy, and then modifying the values of the policy attributes and adding or removing the rules.
To modify Identity Audit policies:
14.6.4 Duplicating Identity Audit Policies
You can use the rules specified for a policy in another policy by duplicating the policy.
To duplicate a rule:
14.6.5 Deleting Identity Audit Policies
You can delete a rule if no policies or policy violations are associated with the rule.
To delete a rule:
14.6.6 Previewing the Results of Identity Audit Policies
You can preview results of the Identity Audit policies to understand the policy violations that will be generated as a result of a scan. When you preview a policy, the policy violations are displayed, but the violations are not assigned to the remediators.
To preview the results of an Identity Audit policy:
-
In Identity Self Service, click the Compliance tab.
-
Click the Identity Audit box, and select Policies. The Policies page is displayed.
-
Search for the policy that you want to modify. See Searching Identity Audit Policies for information about searching policies.
-
Select the policy that you want to preview.
-
From the Actions menu, select Preview. Alternatively, click Preview on the toolbar. The Base Selection page is displayed.
-
Select a set of users that you want to scan by selecting any of the following options:
-
All Organizations: To specify that all organizations will be scanned.
-
Selected Organizations: To specify one or more organizations that will be scanned. After selecting this option, click Add Organizations, search and select one or more organizations, and then click Select.
-
All Users: To specify that all users will be scanned.
-
User Criteria: To specify criteria parameters so that users that match the criteria will be scanned. To specify the user criteria:
-
Under the Criteria Parameters section, select any one of the following:
All: To specify that all the parameters must match.
Any: To specify that any one parameter must match.
-
Enter values in the Manager and Organizations fields.
-
Optionally, you can click Advanced to include more attributes in the criteria.
-
Click Update and Preview Results. The selected criteria is added to the Criteria String section.
-
-
Selected Users: To specify one or more users that will be scanned. After selecting this option, click Add Users, search and select one or more users, and then click Select.
-
-
Click Submit. The scan is submitted.
-
To view the policy violations detected by the scan, select the policy in the Policies page, and click View Scans. Alternatively, from the Actions menu, select View Scans.
The Scans page is displayed with the results of the scan. The scan name, status of the scan, start time, end time, the number of users scanned, and number of violations are displayed in a table.
-
Click the scan name. Alternatively, click Open. The Policy Violations page is displayed with a list of all the policy violations.
The remediator will get the policy violations in the Policy Violations of the Self Service after the scan is run.
-
You can click each policy name to view the policy violation details in the Violation details page. This page has the following sections:
-
Violation Details: Displays the details of the policy violation, such as the policy attributes, status, detection count, and the user name for which the violation is generated.
-
Access Details: Displays the cause of the violation, the rules that have been violated, the status and attributes of the violation, and comments, if any.
-
14.7 Managing Scan Definitions
Managing scan definitions involves searching, creating, and modifying scan definitions, and running and viewing scans.
This section describes how to create and manage scan definitions. It contains the following topics:
14.7.1 Searching Scan Definitions
You can perform basic and advanced search for scan definitions in the Scan Definitions page of Identity Self Service.
This section describes how to perform basic search and advanced search for scan definitions:
14.7.1.1 Performing Basic Search for Scan Definitions
To perform a basic search for scan definitions:
- In Identity Self Service, click the Compliance tab.
- Click the Identity Audit box, and select Scan Definitions. The Scan Definitions page is displayed.
- If fields for advanced search is displayed, then click Basic. Otherwise, ignore this step and continue with step 4.
- From the Search list, select an attribute based on which you can search the scan definitions.
- In the Search box, enter a value of the selected attribute as the search criterion.
- Click the Search icon. The search result is displayed in a tabular format.
14.7.2 Creating Scan Definitions
You can create scan definitions by using the Create option from the Scan Definitions page of Identity Self Service, and specifying values, policy selection strategy, base selection, and configuration parameters for the scan definition.
To create scan definitions:
-
In Identity Self Service, click the Compliance tab.
-
Click the Identity Audit box, and select Scan Definitions. The Scan Definitions page is displayed.
-
From the Actions menu, select Create. Alternatively, click Create on the toolbar. The Attributes page of the Create Scan Definitions wizard is displayed.
-
In the General Policy Information section, enter the scan definition name in the Name box. This is a mandatory field.
-
In the Description box, enter a description for the scan definition.
-
In the Owner box, specify the user name of the owner of the scan definition. You can click the Search icon, and search and select a user as the owner. This is a mandatory field.
-
Click Next. The Select Policy page of the Create Scan Definitions wizard is displayed.
-
From the Policy Selection Strategy list, select any one of the following options:
-
All Policies: Select this option to associate all the Identity Audit policies with the scan definition.
-
Selected Policies: Select this option to associate the policies you select to associate them with the scan definition. To do so, click Add Policies, and search and select a policy.
-
Policy Criteria: Select this option to specify criteria parameters based on which the policies will be dynamically associated with the scan definition. To do so:
-
Select any one of the following options:
All: To specify that all parameters must match.
Any: To specify that any one parameter must match.
-
Enter values in the Policy Name and Description fields.
-
Optionally, you can click Advanced to include more attributes in the criteria.
-
Click Update and Preview Results. The selected criteria is added to the Criteria String section.
-
-
-
Click Next. The Base Selection page of the Create Scan Definitions wizard is displayed.
-
In the Base Selection section, specify the users that you want to scan by using this scan definition. Select a set of users that you want to scan by selecting any of the following options:
-
All Organizations: To specify that all organizations will be scanned.
-
Selected Organizations: To specify one or more organizations that will be scanned. After selecting this option, click Add Organizations, search and select one or more organizations, and then click Select.
-
All Users: To specify that all users will be scanned.
-
User Criteria: To specify criteria parameters so that users that match the criteria will be scanned. To specify the user criteria:
-
Under the Criteria Parameters section, select any one of the following:
All: To specify that all the parameters must match.
Any: To specify that any one parameter must match.
-
Enter values in the Manager and Organizations fields.
-
Optionally, you can click Advanced to include more attributes in the criteria.
-
Click Update and Preview Results. The selected criteria is added to the Criteria String section.
-
-
Selected Users: To specify one or more users that will be scanned. After selecting this option, click Add Users, search and select one or more users, and then click Select.
-
-
Click Next. The Configuration page of the Create Scan Definitions wizard is displayed.
-
(Optional) Select the Prevent Self Remediation option if you want to prevent the owner of the scan definition to take remediation action. Then you must specify a different user as the remediator by selecting any one of the following options from the Alternate remediator ID list:
-
User Manager: To specify the manager of the user for whom the policy violation has been detected as the remediator.
-
Selected User: To specify a user that you select as the remediator. To do so, click the Search icon, and search and select a user.
-
-
If you do not want to prevent self remediation, then accept the default settings, and click Next. The Summary page of the Create Scan Definitions wizard is displayed.
-
Review the attributes, policies, base selection, and configuration that you specified, and then click Finish. The scan definition is created.
After a scan definition is created, when it is run for the first time, a scheduled job is created that can be configured to run periodically.
14.7.3 Modifying Scan Definitions
Modifying scan definitions involves searching and opening the scan definition, and then modifying the values of the scan definition attributes, policies, base selection, and configuration.
To modify scan definitions:
14.7.4 Running and Viewing Scans
Running a scan can be performed either using the Scheduler section of Identity System Administration or by using the Scan Definitions page of Identity Self Service.
Running a scan can be performed in any one of the following ways:
-
From the Scheduler section of Identity System Administration, run the scheduled job that is generated when the scan definition is created. See "Managing the Scheduler" in the Administering Oracle Identity Governance for information about scheduled jobs.
-
From the Scan Definitions page of the Identity Self Service, as described in this section.
To run a scan based on a scan definition and view the scan:
14.8 Managing Policy Violations
Managing policy violations involves searching, opening, completing, and closing policy violations, remediating or closing policy violation causes, and generating policy violation reports.
This section describes how to manage identity audit policy violations from the Policy Violations page. It contains the following topics:
14.8.1 Introducing Identity Audit Policy Violation Page in Identity Self Service
You can manage identity audit policy violations either by using the Pending Violations page or by using the Policy Violations page of Identity Self Service.
Identity audit policy violations can be managed from the following sections of Identity Self Service:
Pending Violations page: As a remediator of identity audit policy violations that are assigned to you, you can access the pending violations and take action on them by using the Pending Violations page. See Managing Pending Violations for details.
Policy Violations page: You can view and take actions on the identity audit policy violations for administrative purpose by using the Policy Violations page, which you can open from the Compliance tab of the Identity Self Service.
14.8.2 Searching Policy Violations
You can perform basic and advanced search for policy violations in the Policy Violations page of Identity Self Service.
This section describes how to perform basic search and advanced search for policy violations:
14.8.2.1 Performing Basic Search for Policy Violations
To perform a basic search for policy violations:
- In Identity Self Service, click the Compliance tab.
- Click the Identity Audit box, and select Policy Violations. The Policy Violations page is displayed.
- If fields for advanced search is displayed, then click Basic. Otherwise, ignore this step and continue with step 4.
- From the Search list, select an attribute based on which you can search the policy violations.
- In the Search box, enter a value of the selected attribute as the search criterion.
- Click the Search icon. The search result is displayed in a tabular format.
14.8.3 Opening Policy Violation Details
Before taking action on policy violations, the remediator must open the policy violation and review the details.
To open a policy violation:
14.8.4 Completing Policy Violations
Completing policy violations include searching and selecting the policy violations and clicking Complete.
To complete policy violations:
- Open the Policy Violations page, as described in Opening Policy Violation Details.
- Search for the policy violation you want to complete. See Searching Policy Violations for information about searching policy violations.
- Select the policy violation you want to complete.
- To complete a policy violation, open the policy violation details by clicking the policy name, and then click Complete in the Details tab.
14.8.5 Closing Policy Violations
Closing policy violations include searching and selecting the policy violations and clicking Close.
To close policy violations:
- Open the Policy Violations page, as described in Opening Policy Violation Details.
- Search for the policy violation you want to close.
- Select the policy violation you want to close.
- From the Actions menu, select Close. Alternatively, click Close on the toolbar.
14.8.6 Remediating or Closing Policy Violations Causes
Remediating or closing policy violation causes involves three options: Remediate, Close as Fixed, and Close as Risk Accepted.
To remediate or close policy violation causes: