4 Upgrading Oracle Identity Manager Highly Available Environments
Describes the process of upgrading an Oracle Identity Manager highly available environment from 11g Release 2 (11.1.2.3.0) to Oracle Identity Governance 12c (12.2.1.3.0).
Note:
The product Oracle Identity Manager is referred to as Oracle Identity Manager (OIM) and Oracle Identity Governance (OIG) interchangeably in the guide.
Topics
- About the Oracle Identity Manager Multinode Upgrade Process
Review the topology and the roadmap for an overview of the upgrade process for Oracle Identity Manager highly available environments. - Completing the Pre-Upgrade Tasks for Oracle Identity Manager
Complete the pre-upgrade tasks described in this section before you upgrade Oracle Identity Manager. - Creating 12c Oracle Home Folder on OIMHOST1 and OIMHOST2
Create a folder for 12c Oracle Home on both OIMHOST1 and OIMHOST2. - Installing Product Distributions on OIMHOST1 and OIMHOST2
Install the 12c binaries onto OIMHOST1 and OIMHOST2 or onto shared storage accessible by both. If you are using redundant binaries ensure you install into each of the redundant locations - Installing the Latest Stack Patch Bundle
After you install the product distributions, Oracle strongly recommends you to apply the latest IDM Stack Patch Bundle (SPB) 12.2.1.3.0 before proceeding with the upgrade process. You can apply the patch by using the Opatch tool. Applying the SPB helps eliminate most of the upgrade issues or workarounds. - Running a Pre-Upgrade Readiness Check
To identify potential issues with the upgrade, Oracle recommends that you run a readiness check before you start the upgrade process. Be aware that the readiness check may not be able to discover all potential issues with your upgrade. An upgrade may still fail, even if the readiness check reports success. - Creating the Required 12c Schemas Using RCU
When upgrading from 11g, you must create the required 12c schemas. If your setup is not SSL enabled, you can use the Upgrade Assistant to create schemas by using the default schema settings. In case of SSL enabled setup, you can use the Repository Creation Utility (RCU) to create customized schemas. This procedure describes how to create schemas using the RCU. Information about using the Upgrade Assistant to create schemas is covered in the upgrade procedures. - Stopping Servers and Processes
Before you run the Upgrade Assistant to upgrade your schemas and configurations, you must shut down all of the pre-upgrade processes and servers, including the Administration Server, Node manager, and any managed servers. - Upgrading Schemas on OIMHOST1
Upgrade all of the necessary schemas for Oracle Identity Manager, on OIMHOST1 by using the Upgrade Assistant. - Reconfiguring the Domain on OIMHOST1
Run the Reconfiguration Wizard on OIMHOST1 to reconfigure your domain component configurations to 12c (12.2.1.3.0). - Upgrading Domain Component Configurations on OIMHOST1
Use the Upgrade Assistant to upgrade the domain component’s configurations inside the domain to match the updated domain configuration. - Replicating the Domain Configurations on each OIMHOST
Replicate the domain configurations on OIMHOST2. This involves packing the upgraded domain on OIMHOST1 and unpacking it on OIMHOST2. - Starting the Servers for Initial Post-Upgrade Bootstrap Processing
After you upgrade Oracle Identity Manager, start the servers to bootstrap the domain configuration. - Fully Deploy the oracle.iam.ui.custom-dev-starter-pack.war
Validate that the Upgrade Assistant has automatically copied theoracle.iam.ui.custom-dev-starter-pack.warfile from the 11g MW_HOME to the 12c ORACLE_HOME on the AdminServer host. - Starting the Servers on OIMHOST1 and OIMHOST2
After you upgrade Oracle Identity Manager on both OIMHOST1 and OIMHOST2, start the servers. - Upgrading Oracle Identity Manager Design Console
Upgrade the Oracle Identity Manager Design Console after you upgrade the Oracle Identity Manager (OIM) domain component configurations. - Performing the Post-Patch Install Steps
After completing the upgrade, you have to perform the post-patch installation steps. - Completing the Post-Upgrade Tasks for SSL Enabled Setup
If you are upgrading an Oracle Identity Manager SSL enabled setup, you must perform the required post-upgrade tasks to complete the upgrade process. - Increasing the Maximum Message Size for WebLogic Server Session Replication
- Changing the JMS and TLOG Persistence Store After the Upgrade
- Installing Standalone Oracle BI Publisher
When you upgrade Oracle Identity Manager 11.1.2.3.0 to Oracle Identity Governance 12c (12.2.1.3.0), the embedded Oracle BI Publisher present in the 11.1.2.3.0 deployment, is removed. Therefore, you must install a new standalone Oracle BI Publisher 12c (12.2.1.3.0) post upgrade, for configuring the Oracle Identity Governance reports.
Parent topic: In-Place Upgrade of Oracle Identity Manager
About the Oracle Identity Manager Multinode Upgrade Process
Review the topology and the roadmap for an overview of the upgrade process for Oracle Identity Manager highly available environments.
The steps you take to upgrade your existing domain will vary depending on how your domain is configured and which components are being upgraded. Follow only those steps that are applicable to your deployment.
Upgrade Topology
Note:
As required, you can upgrade OHS independently of this OIM upgrade process.Figure 4-1 Oracle Identity Manager High Availability Upgrade Topology
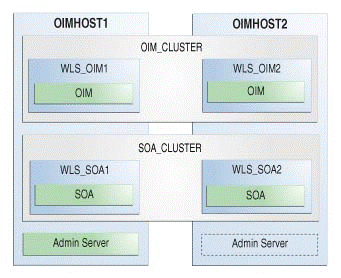
Description of "Figure 4-1 Oracle Identity Manager High Availability Upgrade Topology"
-
An Oracle Identity Manager instance has been installed in the WLS_OIM1 Managed Server and a SOA instance has been installed in the WLS_SOA1 Managed Server.
-
A WebLogic Server Administration Server has been installed. Under normal operations, this is the active Administration Server.
On OIMHOST2, the following installations have been performed:
-
An Oracle Identity Manager instance has been installed in the WLS_OIM2 Managed Server and a SOA instance has been installed in the WLS_SOA2 Managed Server.
-
A WebLogic Server Administration Server has been installed. Under normal operations, this is the passive Administration Server. You make this Administration Server active if the Administration Server on OIMHOST1 becomes unavailable.
The instances in the WLS_OIM1 and WLS_OIM2 Managed Servers on OIMHOST1 and OIMHOST2 are configured as the OIM_CLUSTER cluster.
The instances in the WLS_SOA1 and WLS_SOA2 Managed Servers on OIMHOST1 and OIMHOST2 are configured as the SOA_CLUSTER cluster.
Table 4-1 Tasks for Upgrading Oracle Identity Manager Highly Available Environments
| Task | Description |
|---|---|
|
Required If you have not done so already, review the introductory topics in this guide and complete the required pre-upgrade tasks. |
See: |
|
Required Complete the necessary pre-upgrade tasks specific to Oracle Identity Manager. |
See Completing the Pre-Upgrade Tasks for Oracle Identity Manager. |
|
Required Create the 12c Middleware Home Folder on both OIMHOST1 and OIMHOST2, so that you can use the location for installing the product distributions. |
See Creating 12c Middleware Home Folder on OIMHOST1 and OIMHOST2. |
|
Required Install Oracle SOA Suite12c (12.2.1.3.0) and Oracle Identity Manager12c (12.2.1.3.0) in the new Oracle home. |
See Installing Product Distributions on OIMHOST1 and OIMHOST2. |
|
Required Apply the latest bundle patches |
See Installing the Latest Stack Patch Bundle. |
|
Required Run a pre-upgrade readiness check. |
|
|
Required Start the Repository Creation Utility (RCU) to create the required 12c database schemas. Note: This step is not required for non-SSL setup, as the Upgrade Assistant creates the necessary 12c schemas during the upgrade process. For SSL enabled setup, you must run the RCU to create the necessary 12c schemas. |
The schemas you create will vary depending on your existing schema configuration. |
|
Required Shut down the 11g servers. This includes the Administration Server, Managed Servers, Node Manager, and system components like Oracle HTTP Server. Ensure that the Database is up during the upgrade. |
|
|
Required Upgrade the necessary schemas on OIMHOST1. |
|
|
Required Reconfigure the Oracle Identity Manager domain on OIMHOST1. |
|
|
Required Upgrade the Oracle Identity Manager configurations on both OIMHOST1, using the Upgrade Assistant. |
The Upgrade Assistant is used to update the reconfigured domain’s component configurations. See Upgrading Domain Component Configurations on OIMHOST1 and OIMHOST2. |
|
Required Replicate the domain configurations on OIMHOST2. |
This includes packing the domain on OIMHOST1 and unpacking it on OIMHOST2. |
|
Required Start the servers. |
See Starting the Servers for Initial Post-Upgrade Bootstrap Processing. |
|
Required Deploy the |
See Fully Deploy the oracle.iam.ui.custom-dev-starter-pack.war. |
|
Required Start the servers on OIMHOST1 and OIMHOST2. |
|
|
Required Upgrade the Oracle Identity Manager Design Console to 12c (12.2.1.3.0). |
|
|
Required Complete the post-patch install steps. |
|
|
Required Perform the post-upgrade tasks for SSL enabled setup. Note: This step is not required for non-SSL setup. |
See Completing the Post-Upgrade Tasks for SSL Enabled Setup. |
|
Required To replicate the session data across the nodes, increase the Maximum Message Size for WebLogic Server. |
See Increasing the Maximum Message Size for WebLogic Server Session Replication. |
|
Optional Change the JMS and TLOG persistence stores from files-based to database-based. |
See Changing the JMS and TLOG Persistence Store After the Upgrade |
|
Optional When you upgrade to Oracle Identity Governance 12c (12.2.1.3.0), the embedded Oracle BI Publisher present in the 11.1.2.3.0 deployment is removed. Therefore, you must install a new standalone Oracle BI Publisher 12c (12.2.1.3.0) on OIMHOST1 and OIMHOST2, post upgrade. After you install, integrate it with Oracle Identity Governance 12c (12.2.1.3.0) to configure the Oracle Identity Governance reports. |
Completing the Pre-Upgrade Tasks for Oracle Identity Manager
Complete the pre-upgrade tasks described in this section before you upgrade Oracle Identity Manager.
- Upgrading SOA Composites
If your starting point is Oracle Identity Manager 11.1.1.x.x, you must manually upgrade custom composites that you have built. - Updating Server Wallets to Remove MD5 Algorithm
OIM 12c (12.2.1.3.0) uses JDK 8, which does not support MD5 signing algorithm. If the existing keystore has a certificate which is invalid with JDK8 (that is, using disabled algorithm) used to install the 12c (12.2.1.3.0) binaries, you must generate the keystore and place it in theDOMAIN_HOME/config/fmwconfigdirectory. - Updating DB Wallets to Remove MD5 Algorithm (For SSL Enabled Setup)
If you have SSL enabled setup, update all of the DB wallets to remove any MD5 algorithms, as 12c (12.2.1.3.0) uses JDK 8 which does not support MD5 algorithm. - Verifying the Memory Settings
To avoid the memory issues for Oracle Identity Manager, ensure that the memory settings are updated as per the requirements. - Opening the Non-SSL Ports for SSL Enabled Setup
If you have an SSL enabled and non-SSL disabled setup, you must open the non-SSL ports for Servers and Database before you proceed with the Oracle Identity Manager upgrade. - Backing Up the metadata.mar File Manually
Upgrading SOA Composites
If your starting point is Oracle Identity Manager 11.1.1.x.x, you must manually upgrade custom composites that you have built.
- Open the SOA composite project in JDeveloper (Use Jdeveloper 11.1.1.9.0).
- Open
ApprovalTask.taskfile in designer mode. - Select General.
- Change Owner to Group, SYSTEM ADMINISTRATORS, STATIC.
- Select Outcomes lookup.
An Outcomes Dialog opens.
- Select Outcomes Requiring Comment.
- Select Reject and click OK.
- Click OK again.
- Select Notification.
- Click on the update icon under Notification.
Update any old URLs in notification with the corresponding new URL in 11.1.2.3.0.
Following is an example notification content:A <%/task:task/task:payload/task:RequestModel%> request has been assigned to you for approval. <BR><BR> Request ID: <%/task:task/task:payload/task:RequestID%> <BR> Request type: <%/task:task/task:payload/task:RequestModel%> <BR> <BR> Access this task in the <A style="text-decoration: none;" href=<%substring-before(/task:task/task:payload/task:url, "/workflowservice/CallbackService")%>/identity/faces/home?tf=approval_details > Identity Self Service </A> application or take direct action using the links below. Approvers are required to provide a justification when rejecting the request - Click Advanced.
- Deselect Show worklist/workspace URL in notifications.
Provide the URL to Pending Approvals in identity application as listed in the example in step 10.
- Repeat step 1 to step12 for other human tasks, if any, in the composite, and then save your work.
- Right click Project and select Deploy > Deploy to Application Server.
- Provide revision ID.
Select Mark revision as default and Overwrite any existing composite with same revision ID.
Note:
You can also deploy the composites with different revision ID. In that case, you have to modify all approval policies using this composite. - Select your application server connection, if it already exists, and click Next.
Create an application server connection if it does not exist.
- Click Next.
- Click Finish.
- Repeat the procedure for the remaining custom composites.
Updating Server Wallets to Remove MD5 Algorithm
OIM 12c (12.2.1.3.0) uses JDK 8, which does not support MD5 signing
algorithm. If the existing keystore has a certificate which is invalid with JDK8 (that is,
using disabled algorithm) used to install the 12c (12.2.1.3.0)
binaries, you must generate the keystore and place it in the
DOMAIN_HOME/config/fmwconfig directory.
If the default keystore has MD5 algorithm, then the upgrade readiness check and the examine phase of OIM configuration upgrade will fail.
To verify the validity of the certificate, do the following:
Note:
- For more information about using the keytool command, see keytool in the Java Platform, Standard Edition Tools Reference.
-
The procedure described in this section for regenerating the
default-keystore.jksor custom keystore includes self-signed certificates. If CA signed certificate is required, follow the standard process for the same, that is, generate the CSR and import the signed certificates in the keystore.During bootstrap process in OIM, the
default-keystore.jkskeystore will be configured in Keystore Service (KSS) out-of-the-box. In case of custom keystore,upload the given custom keystore to KSS after completing the upgrade. After you upload the given custom keystore to KSS, restart the servers.For more information about the Keystore Service commands, see OPSS Keystore Service Commands in WLST Command Reference for Infrastructure Security.
Updating DB Wallets to Remove MD5 Algorithm (For SSL Enabled Setup)
If you have SSL enabled setup, update all of the DB wallets to remove any MD5 algorithms, as 12c (12.2.1.3.0) uses JDK 8 which does not support MD5 algorithm.
Note:
All these steps in this procedure must performed on the Database server. That is, on the server where OIM database is installed.Verifying the Memory Settings
To avoid the memory issues for Oracle Identity Manager, ensure that the memory settings are updated as per the requirements.
root user, do the following:
Opening the Non-SSL Ports for SSL Enabled Setup
If you have an SSL enabled and non-SSL disabled setup, you must open the non-SSL ports for Servers and Database before you proceed with the Oracle Identity Manager upgrade.
- Log in to the WebLogic Server Administration Console.
- Click Environment > Servers > and select the required admin server.
- On the Settings for Server page, click the Configuration tab, and then click General.
- Click Lock & Edit.
- Select Listen Port Enabled. The default port is
14000. - Repeat the step 1 through step 5 for each required server in the domain.
Note:
After you complete the upgrade, you can undo these changes as required.For database: Ensure that database listener is listening on the same TCP port for database servers that you provided to upgrade assistant as parameters. For more information, see Enabling SSL for Oracle Identity Governance DB.
Creating 12c Oracle Home Folder on OIMHOST1 and OIMHOST2
Create a folder for 12c Oracle Home on both OIMHOST1 and OIMHOST2.
For example:
/home/Oracle/product/ORACLE_HOME
Installing Product Distributions on OIMHOST1 and OIMHOST2
Install the 12c binaries onto OIMHOST1 and OIMHOST2 or onto shared storage accessible by both. If you are using redundant binaries ensure you install into each of the redundant locations
-
Oracle Fusion Middleware Infrastructure 12c (12.2.1.3.0)
-
Oracle SOA Suite 12c (12.2.1.3.0)
-
Oracle Identity Manager 12c (12.2.1.3.0)
Note:
If you have redundantOracle_Home installations, then install the binaries into each of the redundant locations.
- Installing Product Distributions
Before beginning your upgrade, download Oracle Fusion Middleware Infrastructure, Oracle SOA Suite, and Oracle Identity Manager 12c (12.2.1.3.0) distributions on the target system and install them using Oracle Universal Installer.
Installing Product Distributions
Before beginning your upgrade, download Oracle Fusion Middleware Infrastructure, Oracle SOA Suite, and Oracle Identity Manager 12c (12.2.1.3.0) distributions on the target system and install them using Oracle Universal Installer.
Note:
The 12c binaries are installed in a different location from the previous 11g binaries. You can install 12c binaries before any planned downtime for upgrade.fmw_12.2.1.3.0_idmquickstart_generic.jar). The quick installer installs the Infrastructure, Oracle SOA Suite, and Oracle Identity Manager 12c (12.2.1.3.0) in one go.
Note:
If you are using Redundant binary locations, ensure that you install the software into each of those redundant locations.See Installing Oracle Identity Governance Using Quick Installer in the Installing and Configuring Oracle Identity and Access Management.
The other option is to install the required product distributions — Infrastructure, Oracle SOA Suite, and Oracle Identity Manager 12c (12.2.1.3.0) separately. To do this, complete the following steps:
Installing the Latest Stack Patch Bundle
After you install the product distributions, Oracle strongly recommends you to apply the latest IDM Stack Patch Bundle (SPB) 12.2.1.3.0 before proceeding with the upgrade process. You can apply the patch by using the Opatch tool. Applying the SPB helps eliminate most of the upgrade issues or workarounds.
- Initial Preparation: In this phase, you stage the software, read the
README.txtfile, and verify and/or update the Opatch tool to the appropriate versions. - Analysis Phase: In this phase, you run the
prestopcommand with the variables from theREADME.txtfile to determine if the system is ready for patching. - Patching Phase: In this phase, you backup MW_HOME and
DOMAIN_HOME, run the downtime command for OIG with the
variables from the
README.txtfile, and then clear any temporary files.
Note:
At this point, you will not restart the servers. There is currently no link between the schemas, the local configuration, and the new bits. The remainder of the patching process will happen after the bootstrap.config.xml for the
com.oracle.cie.comdev_7.8.2.0 and
com.oracle.cie.xmldh_3.4.2.0
libraries:<name>com.oracle.cie.comdev#3.0.0.0@7.8.2.0</name>
com.oracle.cie.comdev_7.8.2.0.jar<name>com.oracle.cie.xmldh#2.0.0.0@3.4.2.0</name>
com.oracle.cie.xmldh_3.4.2.0.jar<library>
<name>com.oracle.cie.comdev#3.0.0.0@7.8.2.0</name>
<target>oim_cluster</target>
<source-path><MW_HOME>/oracle_common/modules/com.oracle.cie.comdev_7.8.2.0.jar
</source-path>
<deployment-order>511</deployment-order>
<security-dd-model>DDOnly</security-dd-model>
<staging-mode>nostage</staging-mode>
</library>
<library>
<name>com.oracle.cie.xmldh#2.0.0.0@3.4.2.0</name>
<target>oim_cluster</target>
<source-path><MW_HOME>/oracle_common/modules/com.oracle.cie.xmldh_3.4.2.0.jar<
/source-path>
<deployment-order>511</deployment-order>
<security-dd-model>DDOnly</security-dd-model>
<staging-mode>nostage</staging-mode>
</library><library>
<name>com.oracle.cie.comdev#3.0.0.0@7.8.4.0</name>
<target>oim_cluster</target>
<source-path><MW_HOME>/oracle_common/modules/com.oracle.cie.comdev_7.8.4.0.jar
</source-path>
<deployment-order>511</deployment-order>
<security-dd-model>DDOnly</security-dd-model>
<staging-mode>nostage</staging-mode>
</library>
<library>
<name>com.oracle.cie.xmldh#2.0.0.0@3.4.4.0</name>
<target>oim_cluster</target>
<source-path><MW_HOME>/oracle_common/modules/com.oracle.cie.xmldh_3.4.4.0.jar<
/source-path>
<deployment-order>511</deployment-order>
<security-dd-model>DDOnly</security-dd-model>
<staging-mode>nostage</staging-mode>
</library>This update to the config.xml file changes the name of the libraries and
version of the jar file in each library to the one that will be used post the patching
process. Ensure that both nodes have the same settings.
For more information on the patching process, see Doc ID 2657920.1.
Note:
If you are using Windows or Solaris OS, download the individual Bundle Patches (BPs) from Doc ID 2457034.1.After completing the upgrade, you have to perform the post-patch install steps. See Performing the Post-Patch Install Steps.
Running a Pre-Upgrade Readiness Check
To identify potential issues with the upgrade, Oracle recommends that you run a readiness check before you start the upgrade process. Be aware that the readiness check may not be able to discover all potential issues with your upgrade. An upgrade may still fail, even if the readiness check reports success.
- About Running a Pre-Upgrade Readiness Check
You can run the Upgrade Assistant in-readinessmode to detect issues before you perform the actual upgrade. You can run the readiness check in GUI mode using the Upgrade Assistant or in silent mode using a response file. - Starting the Upgrade Assistant in Readiness Mode
Use the-readinessparameter to start the Upgrade Assistant in readiness mode. - Performing a Readiness Check with the Upgrade Assistant
Navigate through the screens in the Upgrade Assistant to complete the pre-upgrade readiness check. - Understanding the Readiness Report
After performing a readiness check for your domain, review the report to determine whether you need to take any action for a successful upgrade.
About Running a Pre-Upgrade Readiness Check
You can run the Upgrade Assistant in -readiness mode to detect issues before you perform the actual upgrade. You can run the readiness check in GUI mode using the Upgrade Assistant or in silent mode using a response file.
The Upgrade Assistant readiness check performs a read-only, pre-upgrade review of your Fusion Middleware schemas and WebLogic domain configurations that are at a supported starting point. The review is a read-only operation.
The readiness check generates a formatted, time-stamped readiness report so you can address potential issues before you attempt the actual upgrade. If no issues are detected, you can begin the upgrade process. Oracle recommends that you read this report thoroughly before performing an upgrade.
You can run the readiness check while your existing Oracle Fusion Middleware domain is online (while other users are actively using it) or offline.
You can run the readiness check any number of times before performing any actual upgrade. However, do not run the readiness check after an upgrade has been performed, as the report results may differ from the result of pre-upgrade readiness checks.
Note:
To prevent performance from being affected, Oracle recommends that you run the readiness check during off-peak hours.
Parent topic: Running a Pre-Upgrade Readiness Check
Starting the Upgrade Assistant in Readiness Mode
Use the -readiness parameter to start the Upgrade Assistant in readiness mode.
Upgrade Assistant Parameters
When you start the Upgrade Assistant from the command line, you can specify additional parameters.
Table 4-3 Upgrade Assistant Command-Line Parameters
| Parameter | Required or Optional | Description |
|---|---|---|
|
|
Required for readiness checks
Note: Readiness checks cannot be performed on standalone installations (those not managed by the WebLogic Server). |
Performs the upgrade readiness check without performing an actual upgrade. Schemas and configurations are checked. Do not use this parameter if you have specified the |
|
|
Optional |
Identifies the number of threads available for concurrent schema upgrades or readiness checks of the schemas. The value must be a positive integer in the range 1 to 8. The default is 4. |
|
|
Required for silent upgrades or silent readiness checks |
Runs the Upgrade Assistant using inputs saved to a response file generated from the data that is entered when the Upgrade Assistant is run in GUI mode. Using this parameter runs the Upgrade Assistant in silent mode (without displaying Upgrade Assistant screens). |
|
|
Optional |
Performs the examine phase but does not perform an actual upgrade. Do not specify this parameter if you have specified the |
|
|
Optional |
Sets the logging level, specifying one of the following attributes:
The default logging level is Consider setting the |
|
|
Optional |
Sets the default location of upgrade log files and temporary files. You must specify an existing, writable directory where the Upgrade Assistant creates log files and temporary files. The default locations are: (UNIX)
(Windows)
|
|
|
Optional |
Displays all of the command-line options. |
Parent topic: Starting the Upgrade Assistant in Readiness Mode
Performing a Readiness Check with the Upgrade Assistant
Navigate through the screens in the Upgrade Assistant to complete the pre-upgrade readiness check.
Parent topic: Running a Pre-Upgrade Readiness Check
Understanding the Readiness Report
After performing a readiness check for your domain, review the report to determine whether you need to take any action for a successful upgrade.
The format of the readiness report file is:
readiness_timestamp.txt
where timestamp indicates the date and time of when the readiness check was run.
A readiness report contains the following information:
Table 4-4 Readiness Report Elements
| Report Information | Description | Required Action |
|---|---|---|
| Overall Readiness Status: SUCCESS or FAILURE | The top of the report indicates whether the readiness check passed or completed with one or more errors. | If the report completed with one or more errors, search for FAIL and correct the failing issues before attempting to upgrade. You can re-run the readiness check as many times as necessary before an upgrade. |
|
Timestamp |
The date and time that the report was generated. |
No action required. |
|
Log file location
|
The directory location of the generated log file. |
No action required. |
|
Readiness report location
|
The directory location of the generated readiness report. |
No action required. |
|
Names of components that were checked |
The names and versions of the components included in the check and status. |
If your domain includes components that cannot be upgraded to this release, such as SOA Core Extension, do not attempt an upgrade. |
|
Names of schemas that were checked |
The names and current versions of the schemas included in the check and status. |
Review the version numbers of your schemas. If your domain includes schemas that cannot be upgraded to this release, do not attempt an upgrade. |
|
Individual Object Test Status: FAIL |
The readiness check test detected an issue with a specific object. |
Do not upgrade until all failed issues have been resolved. |
|
Individual Object Test Status: PASS |
The readiness check test detected no issues for the specific object. |
If your readiness check report shows only the PASS status, you can upgrade your environment. Note, however, that the Readiness Check cannot detect issues with externals such as hardware or connectivity during an upgrade. You should always monitor the progress of your upgrade. |
| Completed Readiness Check of <Object> Status: FAILURE | The readiness check detected one or more errors that must be resolved for a particular object such as a schema, an index, or datatype. | Do not upgrade until all failed issues have been resolved. |
| Completed Readiness Check of <Object> Status: SUCCESS | The readiness check test detected no issues. | No action required. |
Here is a sample Readiness Report file. Your report may not include all of these checks.
Note:
If the following warning occurs, install Patch 27830741 and re-run the readiness check to ensure that this warning is eliminated before continuing.[oracle] [WARNING] [] [com.oracle.cie.domain.template.catalog.impl.LocalTemplateCat] [tid: 13] [ecid: 7b6f129a-3761-461b-a64a-fb41fa79c822-00000002,0] Couldn't load [/u01/oracle/products/12c/identity/soa/common/templates/wls/oracle.bpm.jms.reconfig_template_12.2.1.3.0.jar].[[
java.util.MissingResourceException: Not managing namespace: (config).
at com.oracle.cie.common.util.ResourceBundleManager.getPublishedMessage(ResourceBundleManager.java:249Upgrade readiness check completed with one or more errors.
This readiness check report was created on Tue May 30 11:15:52 EDT 2016
Log file is located at: ORACLE_HOME/oracle_common/upgrade/logs/ua2016-05-30-11-14-06AM.log
Readiness Check Report File: ORACLE_HOME/oracle_common/upgrade/logs/readiness2016-05-30-11-15-52AM.txt
Starting readiness check of components.
Oracle Metadata Services
Starting readiness check of Oracle Metadata Services.
Schema User Name: DEV11_MDS
Database Type: Oracle Database
Database Connect String: machinename@yourcompany.com
VERSION Schema DEV11_MDS is currently at version 12.1.1.1.0. Readiness checks will now be performed.
Starting schema test: TEST_REQUIRED_TABLES Test that the schema contains all the required tables
Completed schema test: TEST_REQUIRED_TABLES --> Test that the schema contains all the required tables +++ PASS
Starting schema test: TEST_REQUIRED_PROCEDURES Test that the schema contains all the required stored procedures
EXCEPTION Schema is missing a required procedure: GETREPOSITORYFEATURES
Completed schema test: TEST_REQUIRED_PROCEDURES --> Test that the schema contains all the required stored procedures +++ FAIL
Starting schema test: TEST_REQUIRED_VIEWS Test that the schema contains all the required database views
Completed schema test: TEST_REQUIRED_VIEWS --> Test that the schema contains all the required database views +++ PASS
Starting index test for table MDS_ATTRIBUTES: TEST_REQUIRED_INDEXES --> Test that the table contains all the required indexes
Completed index test for table MDS_ATTRIBUTES: TEST_REQUIRED_INDEXES --> Test that the table contains all the required indexes +++ PASS
Starting index test for table MDS_COMPONENTS: TEST_REQUIRED_INDEXES --> Test that the table contains all the required indexes
Completed index test for table MDS_TXN_LOCKS: TEST_REQUIRED_INDEXES --> Test that the table contains all the required indexes +++ PASS
Starting schema test: TEST_REQUIRED_TRIGGERS Test that the schema has all the required triggers
Completed schema test: TEST_REQUIRED_TRIGGERS --> Test that the schema has all the required triggers +++ PASS
Starting schema test: TEST_MISSING_COLUMNS Test that tables and views are not missing any required columns
Completed schema test: TEST_MISSING_COLUMNS --> Test that tables and views are not missing any required columns +++ PASS
Starting schema test: TEST_UNEXPECTED_TABLES Test that the schema does not contain any unexpected tables
Completed schema test: TEST_UNEXPECTED_TABLES --> Test that the schema does not contain any unexpected tables +++ PASS
Starting schema test: TEST_UNEXPECTED_PROCEDURES Test that the schema does not contain any unexpected stored procedures
Completed schema test: TEST_UNEXPECTED_PROCEDURES --> Test that the schema does not contain any unexpected stored procedures +++ PASS
Starting schema test: TEST_UNEXPECTED_VIEWS Test that the schema does not contain any unexpected views
Completed schema test: TEST_UNEXPECTED_VIEWS --> Test that the schema does not contain any unexpected views +++ PASS
Starting index test for table MDS_ATTRIBUTES: TEST_UNEXPECTED_INDEXES --> Test that the table does not contain any unexpected indexes
Completed index test for table MDS_ATTRIBUTES: TEST_UNEXPECTED_INDEXES --> Test that the table does not contain any unexpected indexes +++ PASS
Completed index test for table MDS_LABELS: TEST_UNEXPECTED_INDEXES --> Test that the table does not contain any unexpected indexes +++ PASS
Starting index test for table MDS_LARGE_ATTRIBUTES: TEST_UNEXPECTED_INDEXES --> Test that the table does not contain any unexpected indexes
Starting schema test: TEST_UNEXPECTED_TRIGGERS Test that the schema does not contain any unexpected triggers
Completed schema test: TEST_UNEXPECTED_TRIGGERS --> Test that the schema does not contain any unexpected triggers +++ PASS
Starting schema test: TEST_UNEXPECTED_COLUMNS Test that tables and views do not contain any unexpected columns
Completed schema test: TEST_UNEXPECTED_COLUMNS --> Test that tables and views do not contain any unexpected columns +++ PASS
Starting datatype test for table MDS_ATTRIBUTES: TEST_COLUMN_DATATYPES_V2 --> Test that all table columns have the proper datatypes
Completed datatype test for table MDS_ATTRIBUTES: TEST_COLUMN_DATATYPES_V2 --> Test that all table columns have the proper datatypes +++ PASS
Starting datatype test for table MDS_COMPONENTS: TEST_COLUMN_DATATYPES_V2 --> Test that all table columns have the proper datatypes
Starting permissions test: TEST_DBA_TABLE_GRANTS Test that DBA user has privilege to view all user tables
Completed permissions test: TEST_DBA_TABLE_GRANTS --> Test that DBA user has privilege to view all user tables +++ PASS
Starting schema test: TEST_ENOUGH_TABLESPACE Test that the schema tablespaces automatically extend if full
Completed schema test: TEST_ENOUGH_TABLESPACE --> Test that the schema tablespaces automatically extend if full +++ PASS
Starting schema test: TEST_USER_TABLESPACE_QUOTA Test that tablespace quota for this user is sufficient to perform the upgrade
Completed schema test: TEST_USER_TABLESPACE_QUOTA --> Test that tablespace quota for this user is sufficient to perform the upgrade +++ PASS
Starting schema test: TEST_ONLINE_TABLESPACE Test that schema tablespaces are online
Completed schema test: TEST_ONLINE_TABLESPACE --> Test that schema tablespaces are online +++ PASS
Starting schema test: TEST_DATABASE_VERSION Test that the database server version number is supported for upgrade
INFO Database product version: Oracle Database 11g Enterprise Edition Release 11.2.0.3.0 - 64bit Production
With the Partitioning, OLAP, Data Mining and Real Application Testing options
Completed schema test: TEST_DATABASE_VERSION --> Test that the database server version number is supported for upgrade +++ PASS
Finished readiness check of Oracle Metadata Services with status: FAILURE.
Some errors may be related to the Oracle Fusion Middleware Infrastructure product components rather than Identity and Access Management product components. If errors occur, see Troubleshooting the Infrastructure Upgrade in the Upgrading to the Oracle Fusion Middleware Infrastructure Guide for potential workarounds.
If you are running the 12.1.3.0 version of Oracle Fusion Middleware IAU Schemas, and those schemas were upgraded from 11g (11.1.1.7 and later) or 12c (12.1.2.0), your readiness check may fail with the following error:
Note:
This is not applicable for Oracle Identity Manager.Starting index test for table IAU_COMMON: TEST_REQUIRED_INDEXES --> Test
that the table contains all the required indexes
INFO Audit schema index DYN_EVENT_CATEGORY_INDEX in table IAU_COMMON is
missing the required columns or index itself is missing. This maybe caused by
a known issue, anyway, this missing index will be added in 12.2.2 upgrade.
INFO Audit schema index DYN_EVENT_TYPE_INDEX in table IAU_COMMON is
missing the required columns or index itself is missing. This maybe caused by
a known issue, anyway, this missing index will be added in 12.2.2 upgrade.
INFO Audit schema index DYN_TENANT_INDEX in table IAU_COMMON is missing
the required columns or index itself is missing. This maybe caused by a known
issue, anyway, this missing index will be added in 12.2.2 upgrade.
INFO Audit schema index DYN_USER_INDEX in table IAU_COMMON is missing
the required columns or index itself is missing. This maybe caused by a known
issue, anyway, this missing index will be added in 12.2.2 upgrade.
INFO Audit schema index DYN_COMPONENT_TYPE_INDEX in table IAU_COMMON is
missing the required columns or index itself is missing. This maybe caused by
a known issue, anyway, this missing index will be added in 12.2.2 upgrade.
INFO Audit schema index DYN_USER_TENANT_INDEX in table IAU_COMMON is
missing the required columns or index itself is missing. This maybe caused by
a known issue, anyway, this missing index will be added in 12.2.2 upgrade.
Completed index test for table IAU_COMMON: TEST_REQUIRED_INDEXES --> Test
that the table contains all the required indexes +++ FAILNote:
You can ignore the missing index error in the readiness report. This is a known issue. The corresponding missing index is added during the schema upgrade operation. This error does not occur if the schema to be upgraded was created in 12c using the RCU.Parent topic: Running a Pre-Upgrade Readiness Check
Creating the Required 12c Schemas Using RCU
When upgrading from 11g, you must create the required 12c schemas. If your setup is not SSL enabled, you can use the Upgrade Assistant to create schemas by using the default schema settings. In case of SSL enabled setup, you can use the Repository Creation Utility (RCU) to create customized schemas. This procedure describes how to create schemas using the RCU. Information about using the Upgrade Assistant to create schemas is covered in the upgrade procedures.
Note:
This step is not required for non-SSL setup, as the Upgrade Assistant creates the necessary 12c schemas during the upgrade process.
For SSL enabled setup, you must run the RCU to create the necessary 12c schemas.
Note:
If you are upgrading from a previous 12c release of Oracle Fusion Middleware, you do not need to re-create these schemas if they already exist. Refer to the steps below to identify the existing schemas in your domain.The following schemas must exist before you upgrade to 12c. If you are upgrading from 11g, and you are not sure which schemas you currently have, refer to the steps below to identify the existing schemas in your domain. You do not need to re-create these schemas if they already exist.
-
Service Table schema (
prefix_STB). This schema is new in 12c and is required for domain-based upgrades. It stores basic schema configuration information (for example, schema prefixes and passwords) that can be accessed and used by other Oracle Fusion Middleware components during the domain creation. This schema is automatically created when you run the Repository Creation Utility (RCU), where you specify the existing schema owner prefix that you used for your other 11g schemas.Note:
If the Service Table schema does not exist, you may encounter the error message
UPGAST-00328 : The schema version registry table does not exist on this database. If that happens it is necessary to create the service table schema in order to run Upgrade Assistant -
Oracle Platform Security Services (OPSS) schema (
prefix_OPSS). This schema is required if you are using an OID-based security store in 11g. This schema is automatically created when you run the Repository Creation Utility (RCU). The only supported LDAP-based OPSS security store is Oracle Internet Directory (OID). An LDAP-based policy store is typically used in production environments. You do not need to reassociate an OID-based security store before upgrade. While the Upgrade Assistant is running, you can select the OPSS schema. The Upgrade Assistant upgrades the OID-based security store automatically.Note:
The 12c OPSS database schema is required so that you can reference the 12c schema during the reconfiguration of the domain. Your domain continues to use the OID-based security store after the upgrade is complete.
Stopping Servers and Processes
Before you run the Upgrade Assistant to upgrade your schemas and configurations, you must shut down all of the pre-upgrade processes and servers, including the Administration Server, Node manager, and any managed servers.
An Oracle Fusion Middleware environment can consist of an Oracle WebLogic Server domain, an Administration Server, multiple managed servers, Java components, system components such as Identity Management components, and a database used as a repository for metadata. The components may be dependent on each other, so they must be stopped in the correct order.
Note:
The procedures in this section describe how to stop the existing, pre-upgrade servers and processes using the WLST command-line utility or a script. You can also use the Oracle Fusion Middleware Control and the Oracle WebLogic Server Administration Console. See Starting and Stopping Administration and Managed Servers and Node Manager.Note:
Stop all of the servers in your deployment, except for the Database. The Database must be up during the upgrade process.To stop your pre-upgrade Fusion Middleware environment, navigate to the pre-upgrade domain and follow the steps below.
Step 1: Stop System Components
To stop 11g system components, such as Oracle HTTP Server, use the opmnctl script:
Note:
If the Oracle HTTP server is shared with other services, then you can choose not to stop the Oracle HTTP server.-
(UNIX)
OHS_INSTANCE_HOME/bin/opmnctl stopall -
(Windows)
OHS_INSTANCE_HOME\bin\opmnctl stopall
You can stop system components in any order.
Step 2: Stop the Managed Servers
Depending on the method you followed to start the managed servers, follow one of the following methods to stop the WebLogic Managed Server:
When prompted, enter your user name and password.
- Log into Weblogic console as a
weblogicAdmin. - Go to Servers > Control tab.
- Select the required managed server.
- Click Shutdown.
wls:/offline>nmConnect('nodemanager_username','nodemanager_password',
'AdminServerHostName','5556','domain_name',
'DOMAIN_HOME')
wls:/offline>nmKill('ManagedServerName')Step 3: Stop the Administration Server
When you stop the Administration Server, you also stop the processes running in the Administration Server, including the WebLogic Server Administration Console and Fusion Middleware Control.
Follow one of the following methods to stop the Administration Server:
When prompted, enter your user name, password, and the URL of the Administration Server.
- Log into Weblogic console as a
weblogicAdmin. - Go to Servers > Control tab.
- Select the required admin server.
- Click Shutdown.
wls:/offline>nmConnect('nodemanager_username','nodemanager_password',
'AdminServerHostName','5556','domain_name',
'DOMAIN_HOME')
wls:/offline>nmKill('AdminServer')Step 4: Stop Node Manager
To stop Node Manager, run the following command:
kill $(ps -ef | grep nodemanager | | awk '{print $2}')
Upgrading Schemas on OIMHOST1
Upgrade all of the necessary schemas for Oracle Identity Manager, on OIMHOST1 by using the Upgrade Assistant.
Note:
For SSL enabled setup, it is mandatory to run the Repository Creation Utility (RCU) to create the necessary 12c schemas. See Creating the Required 12c Schemas Using RCU (Optional) For a non-SSL enabled setup, running the RCU to create the 12c schemas is optional.- Upgrading Product Schemas
After stopping servers and processes, use the Upgrade Assistant to upgrade supported product schemas to the current release of Oracle Fusion Middleware.
Upgrading Product Schemas
After stopping servers and processes, use the Upgrade Assistant to upgrade supported product schemas to the current release of Oracle Fusion Middleware.
The Upgrade Assistant allows you to upgrade individually selected schemas or all schemas associated with a domain. The option you select determines which Upgrade Assistant screens you will use.
Note:
High waits and performance degradation may be seen due to 'library cache lock' (cycle)<='library cache lock' for DataPump Worker (DW) processes in the 12.2 RAC environment. To resolve this issue, you should disable S-Optimization by using the following command:ALTER SYSTEM SET "_lm_share_lock_opt"=FALSE SCOPE=SPFILE SID='*';alter system reset "_lm_share_lock_opt" scope=spfile sid='*';- Identifying Existing Schemas Available for Upgrade
This optional task enables you to review the list of available schemas before you begin the upgrade by querying the schema version registry. The registry contains schema information such as version number, component name and ID, date of creation and modification, and custom prefix. - Starting the Upgrade Assistant
Run the Upgrade Assistant to upgrade product schemas, domain component configurations, or standalone system components to 12c (12.2.1.3.0). Oracle recommends that you run the Upgrade Assistant as a non-SYSDBA user, completing the upgrade for one domain at a time. - Upgrading Oracle Identity Manager Schemas Using the Upgrade Assistant
Navigate through the screens in the Upgrade Assistant to upgrade the product schemas. - Verifying the Schema Upgrade
After completing all the upgrade steps, verify that the upgrade was successful by checking that the schema version inschema_version_registryhas been properly updated.
Parent topic: Upgrading Schemas on OIMHOST1
Identifying Existing Schemas Available for Upgrade
This optional task enables you to review the list of available schemas before you begin the upgrade by querying the schema version registry. The registry contains schema information such as version number, component name and ID, date of creation and modification, and custom prefix.
You can let the Upgrade Assistant upgrade all of the schemas in the domain, or you can select individual schemas to upgrade. To help decide, follow these steps to view a list of all the schemas that are available for an upgrade:
-
If you are using an Oracle database, connect to the database by using an acount that has Oracle DBA privileges, and run the following from SQL*Plus:
SET LINE 120 SET PAGESIZE 20 COLUMN MRC_NAME FORMAT A14 COLUMN COMP_ID FORMAT A20 COLUMN VERSION FORMAT A12 COLUMN STATUS FORMAT A9 COLUMN UPGRADED FORMAT A8 SELECT MRC_NAME, COMP_ID, OWNER, VERSION, STATUS, UPGRADED FROM SCHEMA_VERSION_REGISTRY ORDER BY VERSION, MRC_NAME, COMP_ID; -
Examine the report that is generated.
If an upgrade is not needed for a schema, the
schema_version_registrytable retains the schema at its pre-upgrade version. -
Note the schema prefix name that was used for your existing schemas. If you are using RCU for creating new 12c schemas, use the same prefix.
Notes:
-
If you used an OID-based policy store in 11g, make sure to create a new OPSS schema before you perform the upgrade. After the upgrade, the OPSS schema remains an LDAP-based store.
-
You can only upgrade schemas for products that are available for upgrade in Oracle Fusion Middleware release 12c (12.2.1.3.0). Do not attempt to upgrade a domain that includes components that are not yet available for upgrade to 12c (12.2.1.3.0).
Parent topic: Upgrading Product Schemas
Starting the Upgrade Assistant
Run the Upgrade Assistant to upgrade product schemas, domain component configurations, or standalone system components to 12c (12.2.1.3.0). Oracle recommends that you run the Upgrade Assistant as a non-SYSDBA user, completing the upgrade for one domain at a time.
Note:
Before you start the Upgrade Assistant, make sure that the JVM character encoding is set to UTF-8 for the platform on which the Upgrade Assistant is running. If the character encoding is not set to UTF-8, then you will not be able to download files containing Unicode characters in their names. This can cause the upgrade to fail.
To ensure that UTF-8 is used by the JVM, use the JVM option -Dfile.encoding=UTF-8.
- Go to the
oracle_common/upgrade/bindirectory:- (UNIX)
ORACLE_HOME/oracle_common/upgrade/bin - (Windows)
ORACLE_HOME\oracle_common\upgrade\bin
- (UNIX)
- Set a parameter for the Upgrade Assistant to include the JVM encoding
requirement:
- (UNIX)
export UA_PROPERTIES="-Dfile.encoding=UTF-8" - (Windows)
set UA_PROPERTIES="-Dfile.encoding=UTF-8"
- (UNIX)
- Start the Upgrade Assistant:
- (UNIX) ./ua
- (Windows) ua.bat
Note:
In the above command,ORACLE_HOME refers to the 12c (12.2.1.3.0) Oracle Home.
For information about other parameters that you can specify on the command line, such as logging parameters, see:
Parent topic: Upgrading Product Schemas
Upgrading Oracle Identity Manager Schemas Using the Upgrade Assistant
Navigate through the screens in the Upgrade Assistant to upgrade the product schemas.
Note:
-
If the pre-upgrade environment has 11g Audit schema (IAU), you must first upgrade Audit schema only, using the Individually Selected Schema option on the Selected Schemas screen, and selecting Oracle Audit Services schema. Ensure that you select the appropriate IAU schema from the list of available IAU schemas. The upgrade assistant will not detect the corresponding IAU schema from the provided domain directory automatically. Hence, you must select it manually. Once the IAU schema is upgraded, run the Upgrade Assistant again to upgrade the remaining schemas using the All Schema Used by a domain option on the Selected Schemas screen.
-
If there is no Audit schema (IAU) in your pre-upgrade environment, use the All Schema Used by a Domain option on the Selected Schemas screen and proceed.
-
To check whether the pre-upgrade environment has the IAU schema and its version, run the following SQL command using a user with sysdba privileges:
SET LINE 120 COLUMN MRC_NAME FORMAT A14 COLUMN COMP_ID FORMAT A20 COLUMN VERSION FORMAT A12 COLUMN STATUS FORMAT A9 COLUMN UPGRADED FORMAT A8 SELECT MRC_NAME, COMP_ID, OWNER, VERSION, STATUS, UPGRADED FROM SCHEMA_VERSION_REGISTRY WHERE COMP_ID LIKE '%IAU%' ORDER BY VERSION, MRC_NAME, COMP_ID ;This command lists the IAU schemas available in your configured database, and their version.
Note:
For SSL enabled setup, it is mandatory to run the Repository Creation Utility (RCU) to upgrade the existing schemas. For more information, see Creating the Required 12c Schemas Using RCU (Optional). For non-SSL enabled setup, running RCU to upgrade schemas is optional.
Parent topic: Upgrading Product Schemas
Verifying the Schema Upgrade
After completing all the upgrade steps, verify that the upgrade was successful by checking that the schema version in schema_version_registry has been properly updated.
If you are using an Oracle database, connect to the database as a user having Oracle DBA privileges, and run the following from SQL*Plus to get the current version numbers:
SET LINE 120 COLUMN MRC_NAME FORMAT A14 COLUMN COMP_ID FORMAT A20 COLUMN VERSION FORMAT A12 COLUMN STATUS FORMAT A9 COLUMN UPGRADED FORMAT A8 SELECT MRC_NAME, COMP_ID, OWNER, VERSION, STATUS, UPGRADED FROM SCHEMA_VERSION_REGISTRY ORDER BY MRC_NAME, COMP_ID ;
In the query result:
-
Check that the number in the
VERSIONcolumn matches the latest version number for that schema. For example, verify that the schema version number is 12.2.1.3.0.Here is a sample output:MRC_NAME COMP_ID OWNER VERSION STATUS UPGRADED -------- ----------- ------------------ ----------- -------- --–------ PREFIX BIPLATFORM PREFIX_BIPLATFORM 11.1.1.9.0 VALID N PREFIX OPSS PREFIX_OPSS 12.2.1.0.0 VALID Y PREFIX UCSUMS PREFIX_ORASDPM 12.2.1.0.0 VALID Y PREFIX WLS PREFIX_WLS 12.2.1.0.0 VALID N PREFIX IAU PREFIX_IAU 12.2.1.2.0 VALID N PREFIX IAU_APPEND PREFIX_IAU_APPEND 12.2.1.2.0 VALID N PREFIX IAU_VIEWER PREFIX_IAU_VIEWER 12.2.1.2.0 VALID N PREFIX MDS PREFIX_MDS 12.2.1.3.0 VALID Y PREFIX OIM PREFIX_OIM 12.2.1.3.0 VALID Y PREFIX SOAINFRA PREFIX_SOAINFRA 12.2.1.3.0 VALID Y PREFIX STB PREFIX_STB 12.2.1.3.0 VALID N 11 rows selected.
Note:
Some schema versions may remain at the pre-upgrade version number and others may have various 12.2.1.x.y version numbers listed.
BIPLATFORM - is not upgraded and remains 11.1.1.9.0 Audit schemas (IAU*) may not upgrade if pre-exist in 11g, otherwise will be created at version 12.2.1.2.0. WLS schema will be created new at version 12.2.1.0.0 STB schema will be created new at 12.2.1.3.0 -
The
STATUSfield will be eitherUPGRADINGorUPGRADEDduring the schema patching operation, and will becomeVALIDwhen the operation is completed. -
If the status appears as
INVALID, the schema update failed. You should examine the logs files to determine the reason for the failure. -
Synonym objects owned by
IAU_APPENDandIAU_VIEWERmay appear asINVALID, but that does not indicate a failure. In the case where the IAU schemas are created rather than upgraded, they will show up asVALID.They become invalid because the target object changes after the creation of the synonym. The synonyms objects will become valid when they are accessed. You can safely ignore these
INVALIDobjects.
Parent topic: Upgrading Product Schemas
Reconfiguring the Domain on OIMHOST1
Run the Reconfiguration Wizard on OIMHOST1 to reconfigure your domain component configurations to 12c (12.2.1.3.0).
- About Reconfiguring the Domain
Run the Reconfiguration Wizard to reconfigure your domain component configurations to 12c (12.2.1.3.0).
About Reconfiguring the Domain
Run the Reconfiguration Wizard to reconfigure your domain component configurations to 12c (12.2.1.3.0).
Note:
- If custom applications are deployed in OIM 11g, the Reconfiguration Wizard will display a warning message along with the list of custom applications and libraries (if present). These applications/libraries will continue pointing to the 11g location even after upgrade to OIM 12c (12.2.1.3). You have to update them manually after the upgrade.
- After reconfiguration, the domain continues to remain in the same location (that is, the
11g DOMAIN_HOME). It will not be moved or copied to 12c
$ORACLE_HOME/user_projects/domains/.
When you reconfigure a WebLogic Server domain, the following items are automatically updated, depending on the applications in the domain:
-
WebLogic Server core infrastructure
-
Domain version
Note:
Before you begin the domain reconfiguration, note the following limitations:
-
The Reconfiguration Wizard does not update any of your own applications that are included in the domain.
-
Transforming a non-dynamic cluster domain to a dynamic cluster domain during the upgrade process is not supported.
The dynamic cluster feature is available when running the Reconfiguration Wizard, but Oracle only supports upgrading a non-dynamic cluster upgrade and then adding dynamic clusters. You cannot add dynamic cluster during the upgrade process.
-
If the installation that you’re upgrading does not use Oracle Access Manager (OAM), then you must edit two files to prevent the Reconfiguration Wizard from attempting to update the nonexistent OAM Infrastructure schema, which causes the upgrade to fail.
Comment out the lines in your
$DOMAIN_HOME/init-info/domain-info.xmlthat are similar to this example:Where,
DOMAIN_HOMEis the Administrator server domain home.<!--extention-template-ref name="Oracle Identity Navigator" version="11.1.1.3.0" location="/u01/app/oracle/product/fmw/iam111130/common/templates/applications/oracle.oinav_11.1.1.3.0_template.jar" symbol=""/--> <!--install-comp-ref name="oracle.idm.oinav" version="11.1.1.3.0" symbol="oracle.idm.oinav_11.1.1.3.0_iam111130_ORACLE_HOME" product_home="/u01/app/oracle/product/fmw/iam111130"/-->and similarly comment out the lines in
$DOMAIN_NAME/config/config.xmlthat are similar to this example:<!--app-deployment> <name>oinav#11.1.1.3.0</name> <target>AdminServer</target> <module-type>ear</module-type> <source-path>/u01/app/oracle/product/fmw/iam111130/oinav/modules/oinav.ear_11.1.1.3.0/oinav.ear</source-path> <deployment-order>500</deployment-order> <security-dd-model>DDOnly</security-dd-model> <staging-mode>nostage</staging-mode> </app-deployment-->
-
The domain version number in the
config.xmlfile for the domain is updated to the Administration Server's installed WebLogic Server version. -
Reconfiguration templates for all installed Oracle products are automatically selected and applied to the domain. These templates define any reconfiguration tasks that are required to make the WebLogic domain compatible with the current WebLogic Server version.
-
Start scripts are updated.
If you want to preserve your modified start scripts, be sure to back them up before starting the Reconfiguration Wizard.
Note:
When the domain reconfiguration process starts, you can’t undo the changes that it makes. Before running the Reconfiguration Wizard, ensure that you have backed up the domain as covered in the pre-upgrade checklist. If an error or other interruption occurs while running the Reconfiguration Wizard, you must restore the domain by copying the files and directories from the backup location to the original domain directory. This is the only way to ensure that the domain has been returned to its original state before reconfiguration.- Backing Up the Domain
- Starting the Reconfiguration Wizard
- Reconfiguring the Oracle Identity Manager Domain
Navigate through the screens in the Reconfiguration Wizard to reconfigure your existing domain.
Parent topic: Reconfiguring the Domain on OIMHOST1
Backing Up the Domain
Before running the Reconfiguration Wizard, create a backup copy of the domain directory.
To create a backup of the Administration server domain directory:
Parent topic: About Reconfiguring the Domain
Starting the Reconfiguration Wizard
Note:
- Shut down the administration server and all managed servers before starting the reconfiguration process. See Stopping Servers and Processes.
- If the source is a clustered environment, run the Reconfiguration Wizard on
the primary node only, where, primary node is the Administration Server.
Use the
Pack/Unpackutility to apply the changes to other cluster members in the domain.
To start the Reconfiguration Wizard in graphical mode:
Parent topic: About Reconfiguring the Domain
Reconfiguring the Oracle Identity Manager Domain
Navigate through the screens in the Reconfiguration Wizard to reconfigure your existing domain.
Parent topic: About Reconfiguring the Domain
Upgrading Domain Component Configurations on OIMHOST1
Use the Upgrade Assistant to upgrade the domain component’s configurations inside the domain to match the updated domain configuration.
Note:
Perform this procedure OIMHOST1 only.- Upgrading Domain Component Configurations
After reconfiguring the domain, use the Upgrade Assistant to upgrade the domain component configurations inside the domain to match the updated domain configuration.
Upgrading Domain Component Configurations
After reconfiguring the domain, use the Upgrade Assistant to upgrade the domain component configurations inside the domain to match the updated domain configuration.
- Starting the Upgrade Assistant
Run the Upgrade Assistant to upgrade product schemas, domain component configurations, or standalone system components to 12c (12.2.1.3.0). Oracle recommends that you run the Upgrade Assistant as a non-SYSDBA user, completing the upgrade for one domain at a time. - Upgrading Oracle Identity Manager Domain Component Configurations
Navigate through the screens in the Upgrade Assistant to upgrade component configurations in the WebLogic domain.
Parent topic: Upgrading Domain Component Configurations on OIMHOST1
Starting the Upgrade Assistant
Run the Upgrade Assistant to upgrade product schemas, domain component configurations, or standalone system components to 12c (12.2.1.3.0). Oracle recommends that you run the Upgrade Assistant as a non-SYSDBA user, completing the upgrade for one domain at a time.
Note:
Before you start the Upgrade Assistant, make sure that the JVM character encoding is set to UTF-8 for the platform on which the Upgrade Assistant is running. If the character encoding is not set to UTF-8, then you will not be able to download files containing Unicode characters in their names. This can cause the upgrade to fail.
To ensure that UTF-8 is used by the JVM, use the JVM option -Dfile.encoding=UTF-8.
- Go to the
oracle_common/upgrade/bindirectory:- (UNIX)
ORACLE_HOME/oracle_common/upgrade/bin - (Windows)
ORACLE_HOME\oracle_common\upgrade\bin
- (UNIX)
- Set a parameter for the Upgrade Assistant to include the JVM encoding
requirement:
- (UNIX)
export UA_PROPERTIES="-Dfile.encoding=UTF-8" - (Windows)
set UA_PROPERTIES="-Dfile.encoding=UTF-8"
- (UNIX)
- Start the Upgrade Assistant:
- (UNIX) ./ua
- (Windows) ua.bat
Note:
In the above command,ORACLE_HOME refers to the 12c (12.2.1.3.0) Oracle Home.
For information about other parameters that you can specify on the command line, such as logging parameters, see:
Upgrade Assistant Parameters
When you start the Upgrade Assistant from the command line, you can specify additional parameters.
Table 4-6 Upgrade Assistant Command-Line Parameters
| Parameter | Required or Optional | Description |
|---|---|---|
|
|
Required for readiness checks
Note: Readiness checks cannot be performed on standalone installations (those not managed by the WebLogic Server). |
Performs the upgrade readiness check without performing an actual upgrade. Schemas and configurations are checked. Do not use this parameter if you have specified the |
|
|
Optional |
Identifies the number of threads available for concurrent schema upgrades or readiness checks of the schemas. The value must be a positive integer in the range 1 to 8. The default is 4. |
|
|
Required for silent upgrades or silent readiness checks |
Runs the Upgrade Assistant using inputs saved to a response file generated from the data that is entered when the Upgrade Assistant is run in GUI mode. Using this parameter runs the Upgrade Assistant in silent mode (without displaying Upgrade Assistant screens). |
|
|
Optional |
Performs the examine phase but does not perform an actual upgrade. Do not specify this parameter if you have specified the |
|
|
Optional |
Sets the logging level, specifying one of the following attributes:
The default logging level is Consider setting the |
|
|
Optional |
Sets the default location of upgrade log files and temporary files. You must specify an existing, writable directory where the Upgrade Assistant creates log files and temporary files. The default locations are: (UNIX)
(Windows)
|
|
|
Optional |
Displays all of the command-line options. |
Parent topic: Starting the Upgrade Assistant
Upgrading Oracle Identity Manager Domain Component Configurations
Navigate through the screens in the Upgrade Assistant to upgrade component configurations in the WebLogic domain.
After running the Reconfiguration Wizard to reconfigure the WebLogic domain to 12c (12.2.1.3.0), you must run the Upgrade Assistant to upgrade the domain component configurations to match the updated domain configuration.
Parent topic: Upgrading Domain Component Configurations
Replicating the Domain Configurations on each OIMHOST
Replicate the domain configurations on OIMHOST2. This involves packing the upgraded domain on OIMHOST1 and unpacking it on OIMHOST2.
Note:
If you are following the EDG methodology you also need to pack and unpack the domain in the OIM managed server location on OIMHOST1.Starting the Servers for Initial Post-Upgrade Bootstrap Processing
After you upgrade Oracle Identity Manager, start the servers to bootstrap the domain configuration.
pack/unpack operations
to replicate the domain configuration from ASERVER_HOME to
MSERVER_HOME on OIMHOST1 so that the SOA and OIM Managed
Server can be bootstrapped properly with the upgraded domain configuration.
Note:
Thepack/unpack operations will be
repeated in the next step after the bootstrap process is complete, to replicate
the final domain configuration to all OIMHOSTn hosts.
Fully Deploy the
oracle.iam.ui.custom-dev-starter-pack.war
Validate that the Upgrade Assistant has automatically copied the
oracle.iam.ui.custom-dev-starter-pack.war file from the
11g MW_HOME to the 12c ORACLE_HOME on the
AdminServer host.
If you have an Enterprise Reference topology or use multiple shared volumes for your ORACLE_HOME binaries, then also replicate this file manually to each OIMHOSTn where a distinct separate binary volume is mounted.
- Check the 11g MW_HOME for the war file,
validate it is no longer
present.
ls /u01/oracle/products/identity/iam/server/apps/oracle.iam.ui.custom-dev-starter-pack.war - Check the 12c ORACLE_HOME for the war file,
validate it has been placed in the correct
location.
ls /u01/oracle/products/12c/identity/idm/server/apps/oracle.iam.ui.custom-dev-starter-pack.war - Copy the war file from the binary volume on OIMHOST1 to any
other hosts with a separate binaries volume.
For example:
cd /u01/oracle/products/12c/identity/idm/server/apps/ scp oracle.iam.ui.custom-dev-starter-pack.war \ iamoracle@OIMHOST2:/u01/oracle/products/12c/identity/idm/server/apps/.
Starting the Servers on OIMHOST1 and OIMHOST2
After you upgrade Oracle Identity Manager on both OIMHOST1 and OIMHOST2, start the servers.
- Start the Node Manager on both OIMHOST1 and OIMHOST2.
- Start the Administration Server on OIMHOST1.
- Start the Oracle SOA Suite Managed Server (without BPM property) and Oracle Identity Manager Managed Servers on OIMHOST1.
- Start the Oracle SOA Suite Managed Server (without BPM property) and Oracle Identity Manager Managed Servers on OIMHOST2.
- Starting Servers and Processes
After a successful upgrade, start all processes and servers, including the Administration Server and any Managed Servers. - Verifying the Domain-Specific-Component Configurations Upgrade
To verify that the domain-specific-component configurations upgrade was successful, sign in to the Administration console and the Oracle Enterprise Manager Fusion Middleware Control and verify that the version numbers for each component is 12.2.1.3.0. - Configuring Oracle HTTP Servers to Front End OIM, and SOA Managed Servers
Starting Servers and Processes
After a successful upgrade, start all processes and servers, including the Administration Server and any Managed Servers.
The components may be dependent on each other so they must be started in the correct order.
Note:
The procedures in this section describe how to start servers and process using the WLST command line or a script. You can also use the Oracle Fusion Middleware Control and the Oracle WebLogic Server Administration Console. See Starting and Stopping Administration and Managed Servers and Node Manager in Administering Oracle Fusion Middleware.To start your Fusion Middleware environment, follow the steps below.
Step 1: Start Node Manager
Start the Node Manager in the Administration Server
<DOMAIN_HOME>/bin location by
running the following command.
-
(UNIX)
nohup ./startNodeManager.sh > <DOMAIN_HOME>/nodemanager/nodemanager.out 2>&1 & -
(Windows)
nohup .\startNodeManager.sh > <DOMAIN_HOME>\nodemanager\nodemanager.out 2>&1 &
Where, <DOMAIN_HOME> is the Administration server domain home.
Step 2: Start the Administration Server
Note:
Typically, the name of the Administration Server is always
'AdminServer'. If the name of your Administration Server is different from
the default name 'AdminServer', you should modify the name in the
<domainname>/config/config.xml file,
accordingly, prior to starting the server.
- Open the
<domainname>/config/config.xmlfile and locate the following library entry:<library> <name>oracle.idm.ipf</name> <target>AdminServer</target> <module-type>jar</module-type> ..... ..... </library> - Note the name of the Administration Server. If the name
is other than 'AdminServer', change the following entry
accordingly:
<target><name_of_your_admin_server></target>
nohup DOMAIN_HOME/bin/startWeblogic.sh &cd ORACLE_COMMON_HOME/common/bin
./wlst.sh
wls:/offline> nmConnect('nodemanager_username','nodemanager_password',
'ADMINVHN','5556','domain_name',
'DOMAIN_HOME')
nmStart('AdminServer')Step 3 (Option 1): Start the Managed Servers
Note:
In an HA environment, it is preferred to use the console or node manager to start servers.- Log into Weblogic console as a
weblogicAdmin. - Go to Servers > Control tab.
- Select the required managed server.
- Click Start.
Step 3 (Option 2): Start the SOA and OIM Clusters
<code block>
connect('weblogic','weblogic_passsword','t3://ADMINVHN:7001')
start('cluster_soa', 'Cluster', block='true')
start('cluster_oim', 'Cluster', block='true')
state('cluster_soa', 'Cluster')
state('cluster_oim', 'Cluster')
exit()
</code block>Parent topic: Starting the Servers on OIMHOST1 and OIMHOST2
Verifying the Domain-Specific-Component Configurations Upgrade
To verify that the domain-specific-component configurations upgrade was successful, sign in to the Administration console and the Oracle Enterprise Manager Fusion Middleware Control and verify that the version numbers for each component is 12.2.1.3.0.
To sign in to the Administration Console, go to: http://administration_server_host:administration_server_port/console
To sign in to the Administration Console in an EDG deployment, see Validating the Virtual Server Configuration and Access to the Consoles.
To sign in to Oracle Enterprise Manager
Fusion Middleware Control Console, go to: http://administration_server_host:administration_server_port/em
Note:
- After upgrade, ensure you run the administration tools from the new 12c Oracle home directory and not from the previous Oracle home directory.
- During the upgrade process, some OWSM documents, including policy sets and predefined documents such as policies and assertion templates, may need to be upgraded. If a policy set or a predefined document is upgraded, its version number is incremented by 1.
- In the site-specific configuration, the WebLogic and EM consoles must be accessible with the URLs either directly or through proxy URLs.
Parent topic: Starting the Servers on OIMHOST1 and OIMHOST2
Configuring Oracle HTTP Servers to Front End OIM, and SOA Managed Servers
If your installation is fronted by Oracle HTTP Server, you need to ensure that your OHS
directives are as given below. Note that you may have one configuration file or several of
these files will have the extention .conf and reside in:
OHS_DOMAIN_HOME/config/fmwconfig/components/OHS/instances/OHS_INSTANCE_NAME/modultconf
To configure the Oracle HTTP Server instances in the Web tier so they route
requests correctly to the Oracle SOA Suite cluster, use the following procedure to create an
additional Oracle HTTP Server configuration file that creates and defines the parameters of
the https://igdinternal.example.com:7777 virtual server.
To validate the virtual host configuration file so requests are routed properly to the Oracle Identity Governance clusters:
Note:
If internal invocations are going to be used in the system, add the appropriate locations to the soainternal virtual host.
Parent topic: Starting the Servers on OIMHOST1 and OIMHOST2
Upgrading Oracle Identity Manager Design Console
Upgrade the Oracle Identity Manager Design Console after you upgrade the Oracle Identity Manager (OIM) domain component configurations.
To upgrade the Oracle Identity Manager Design Console, replace the 12c (12.2.1.3.0)
ORACLE_HOME/idm/designconsole/config/xlconfig.xml file with
the 11.1.2.3.0
ORACLE_HOME/Oracle_IDM1/designconsole/config/xlconfig.xml
file.
After copying the file to the 12c ORACLE_HOME location on OIMHOST1, copy the file to any remote OIMHOSTn that use a different copy of the ORACLE_HOME binaries volume.
Performing the Post-Patch Install Steps
After completing the upgrade, you have to perform the post-patch installation steps.
The post-patch installation steps comprises the following:
Running the Poststart Command to Confirm Successful Binary Patching
poststart command for your product, as shown below:
$ ./spbat.sh -type oig -phase poststart -mw_home /<INSTALLATION_DIRECTORY>/IAM12c -spb_download_dir /<DOWNLOAD_LOCATION>/IDM_SPB_12.2.1.4.200714 -log_dir /<DOWNLOAD_LOCATION>/OIGlogsFor details, see Doc ID 2657920.1.
Parent topic: Performing the Post-Patch Install Steps
Filling in the patch_oim_wls.profile File
Using a text editor, edit the file patch_oim_wls.profile
located in the ORACLE_HOME/idm/server/bin/
directory and change the values in the file to match your environment. The
patch_oim_wls.profile file contains sample values.
Table 4-7 lists the information to be entered for the patch_oim_wls.profile
file. This file is used in the next stage of the bundle patch process.
Table 4-7 Parameters of the patch_oim_wls.profile File
| Parameter | Description | Sample Value |
|---|---|---|
|
|
Location of the ANT installation. It is usually under MW_HOME. |
For Linux:
For Windows:
|
|
|
Location of the JDK/JRE installation that is being used to run the Oracle Identity Governance domain. |
For Linux: <JAVA_HOME_PATH> consumed by $MW_HOME For Windows: <JAVA_HOME_PATH> consumed by %MW_HOME% |
|
|
Location of the middleware home location on which Oracle Identity Governance is installed. |
For Linux:
For Windows:
|
|
|
Location of the Oracle Identity Governance installation. |
For Linux: For Windows: |
|
|
Location of the SOA installation. |
For Linux: For Windows: |
|
|
Directory on which WebLogic server is installed. |
For Linux: For Windows: |
|
|
Location of the domain home on which Oracle Identity Governance is installed. |
|
|
|
Domain administrator user name. Normally it is weblogic, but could be different as well. |
weblogic |
|
weblogic_password |
Domain admin user's password. If this line is commented out, then password will be prompted. |
NA |
|
|
Listen address of the SOA Managed Server, or the hostname on which the SOA Managed Server is listening. Note: If the SOA Managed Server is configured to use a virtual IP address, then the virtual host name must be supplied. |
|
|
|
Listen port of the SOA Managed Server, or SOA Managed Server port number. |
8001 Only Non-SSL Listen port must be provided. |
|
|
Oracle Identity Governance database schema user. |
DEV_OIM |
|
|
Oracle Identity Governance database schema password. If this line is commented out, then the password will be prompted when the script is executed. |
NA |
|
|
Host name of the Oracle Identity Governance database. |
|
|
|
Database service name of the Oracle Identity Governance schema/database. This is not the hostname and it can be a different value as well. |
|
|
|
Database listener port number for the Oracle Identity Governance database. |
1521 |
|
|
MDS schema user |
DEV_MDS |
|
|
MDS schema password. If this line is commented out, then password will be prompted. |
NA |
|
|
MDS database host name |
|
|
|
MDS database/Listen port |
1521 |
|
|
MDS database service name |
|
|
|
Oracle Identity Governance username. |
System administrator username |
|
|
Oracle Identity Governance password. This is optional. If this is commented out, then you will be prompted for the password when the script is executed. |
NA |
|
|
URL to navigate to Oracle Identity Governance. |
|
|
|
URL to navigate to WLS Console |
|
|
|
Enables customizations related to authorization or custom task flow. Set this value to true to enable customization. |
true |
Note:
Update the parameter value as per the setup used, and then execute thepatch_oim_wls.sh file.
Parent topic: Performing the Post-Patch Install Steps
Patching the Oracle Identity Governance Managed Servers (patch_oim_wls Stage)
Patching the Oracle Identity Governance Managed Servers is the process
of copying the staged files to the correct locations, running SQL scripts, importing
event handlers, and deploying SOA composite. For making MBean calls, the script
automatically starts the Oracle Identity Governance Managed Server and SOA Managed
Server specified in the patch_oim_wls.profile file.
This step is performed by running patch_oim_wls.sh (on UNIX) and
patch_oim_wls.bat (on Microsoft Windows) script by using
the inputs provided in the patch_oim_wls.profile file. As
prerequisites, the WebLogic Admin Server, SOA Managed Servers, and Oracle Identity
Governance Managed Server must be running.
To patch Oracle Identity Governance Managed Servers on WebLogic:
Parent topic: Performing the Post-Patch Install Steps
Performing a Clean Restart of the Servers
Restart all the servers including the Administration Server and any Managed Servers. See Starting Servers and Processes.
Parent topic: Performing the Post-Patch Install Steps
Completing the Post-Upgrade Tasks for SSL Enabled Setup
If you are upgrading an Oracle Identity Manager SSL enabled setup, you must perform the required post-upgrade tasks to complete the upgrade process.
Increasing the Maximum Message Size for WebLogic Server Session Replication
Oracle recommends you to modify the Maximum Message Size from the default vale of 10 MB to 100 MB. This value is used to replicate the session data across the nodes. You should perform this step for all the Managed servers and the Administration server.
- Log in to the WebLogic Server Administration Console.
- Navigate to Servers, select Protocols, and then click General.
- Set the value of Maximum Message Size to 100 MB.
Changing the JMS and TLOG Persistence Store After the Upgrade
The JMS and TLOG persistent store remain the same after the upgrade to Oracle Identity Manager 12c (12.2.1.3.0). That is, if the persistence store is file-based prior to the upgrade, it will be file-based after the upgrade as well.
If you want to change the persistence stores from a file-based system to a database-based system, you have to perform the steps manually. See Using Persistent Stores for TLOGs and JMS in an Enterprise Deployment.
Installing Standalone Oracle BI Publisher
When you upgrade Oracle Identity Manager 11.1.2.3.0 to Oracle Identity Governance 12c (12.2.1.3.0), the embedded Oracle BI Publisher present in the 11.1.2.3.0 deployment, is removed. Therefore, you must install a new standalone Oracle BI Publisher 12c (12.2.1.3.0) post upgrade, for configuring the Oracle Identity Governance reports.
For information about installing and configuring Oracle BI Publisher 12c (12.2.1.3.0), see Installing and Configuring Oracle BI Publisher in Developing and Customizing Applications for Oracle Identity Governance.
For information about integrating standalone Oracle BI Publisher with Oracle Identity Governance 12c (12.2.1.3.0), see Integrating Standalone BI Publisher with Oracle Identity Governance in Developing and Customizing Applications for Oracle Identity Governance.