7 Configuring an Identity Store with Multiple Directories
This chapter contains the following topics:
7.1 Overview of Configuring Multiple Directories as an Identity Store
This chapter describes how to configure Oracle Virtual Directory for two multiple directory scenarios. In both scenarios, you have some user data in a third-party directory, such as Active Directory, and other user data in Oracle Internet Directory.
In both scenarios, you use Oracle Virtual Directory to present all the identity data in a single consolidated view that Oracle Identity Management components can interpret.
The scenarios are as follows:
-
Split Profile: A split profile, or split directory configuration, is one where identity data is stored in multiple directories, possibly in different locations. You use a split profile when you must extend directory schema in order to support specific schema elements, but you cannot or do not want to extend the schema in the third-party Identity Store. In that case, deploy an Oracle Internet Directory as a shadow directory to store the extended attributes. For details, see Configuring Multiple Directories as an Identity Store: Distinct User and Group Populations in Multiple Directories. (If, on the other hand, you can extend the schema, use the approach described in Section 2.2.3, "Extending the Directory Schema for Access Manager.")
-
Distinct User and Group Populations: Another multidirectory scenario is one where you have distinct user and group populations, such as internal and external users. In this configuration, Oracle-specific entries and attributes are stored in Oracle Internet Directory. Enterprise-specific entries, for example, entries with Fusion Applications-specific attributes, are stored in Active Directory. For details, see Configuring Multiple Directories as an Identity Store: Distinct User and Group Populations in Multiple Directories.
In this chapter, Active Directory is chosen as the non-Oracle Internet Directory Enterprise Directory. The solution is applicable to all enterprises having one or more Active Directories as their enterprise Identity Store.
7.2 Configuring Multiple Directories as an Identity Store: Split Profile
This section describes how to configure multiple directories as an Identity Store. In cases where the Active Directory schema cannot be extended, you use Oracle Internet Directory as a shadow directory to store these attributes. Oracle Virtual Directory links them together to present a single consolidated DIT view to clients. This is called a split profile or split directory configuration. In this configuration, all the Oracle specific attributes and Oracle specific entities are created in Oracle Internet Directory.
This section contains the following topics:
7.2.1 Prerequisites to Configuring Multiple Directories as an Identity Store
The following assumptions and rules apply to this deployment topology:
-
Oracle Internet Directory houses the Fusion Identity Store. This means that Oracle Internet Directory is the store for all Fusion Application-specific artifacts. The artifacts include a set of enterprise roles used by Fusion Application and some user attributes required by Fusion Applications. All other stores are referred to as enterprise Identity Stores.
-
The enterprise contains more than one LDAP directory. Each directory contains a distinct set of users and roles.
-
The enterprise policy specifies that specific user attributes, such as Fusion Application-specific attributes, cannot be stored in the enterprise directory. All the extended attributes must be stored in a separate directory called the shadow directory. This shadow directory must be Oracle Internet Directory because Active Directory does not allow you to extend the schema.
-
User login IDs are unique across the directories. There is no overlap of the user login IDs between these directories.
-
Oracle Identity Management has no fine-grained authorization. If Oracle Identity Management's mapping rules allow it to use one specific subtree of a directory, then it can perform all CRUD (Create, Read, Update, Delete) operations in that subtree of the LDAP directory. There is no way to enable Oracle Identity Management to read user data in a subtree but not enable it to create a user or delete a user in subtree.
-
Referential integrity must be turned off in Oracle Internet Directory so that an Oracle Internet Directory group can have members that are in one of the Active Directory directories. The users group memberships are not maintained across the directories with referential integrity.
7.2.2 Repository Descriptions
This section describes the artifacts in the Identity store and how they can be distributed between Active Directory and Oracle Internet Directory, based on different enterprise deployment requirements.
The Artifacts that are stored in the Identity Store are:
-
Application IDs: These are the identities that are required to authenticate applications to communicate with each other.
-
Seeded Enterprise Roles: These are the enterprise roles or LDAP group entries that are required for default functionality.
-
Enterprise roles provisioned by Oracle Identity Management: These are runtime roles.
-
Enterprise Users: These are the actual users in the enterprise.
-
Enterprise Groups: These are the roles and groups that already exist in the enterprise.
In a split profile deployment, the Identity Store artifacts can be distributed among Active Directory and Oracle Internet Directory, as follows.
-
Oracle Internet Directory is a repository for enterprise roles. Specifically, Oracle Internet Directory contains the following:
-
Application IDs
-
Seeded enterprise roles
-
Enterprise roles provisioned by Oracle Identity Management
-
-
Active Directory is the repository for:
-
Enterprise users
-
Enterprise groups (not visible to Oracle Identity Management or Fusion Applications)
-
The following limitations apply:
-
The Active Directory users must be members of Oracle Internet Directory groups.
-
The groups in Active Directory are not exposed at all. Oracle applications only manage the Oracle-created enterprise roles. The groups in Active Directory are not visible to either Oracle Identity Management or Fusion Applications.
7.2.3 Setting Up Oracle Internet Directory as a Shadow Directory
In cases where Oracle Internet Directory is used as the shadow directory to store certain attributes, such as all the Fusion Application-specific attributes, use a separate container in Oracle Internet Directory to store the shadow attributes.
-
The Shadow Entries container (
cn=shadowentries) must be in a separate DIT from the parent of the users and groups containerdc=mycompany,dc=com, as shown in Figure 7-1. -
The same ACL configured for
dc=mycompany,dc=comwithin Oracle Internet Directory must be configured forcn=shadowentries. To perform this configuration, use theldapmodifycommand. The syntax is as follows:ldapmodify -D cn=orcladmin -q -p portNum -h hostname -f ldifFile
The following is a sample LDIF file to use with
ldapmodify:dn: cn=shadowentries changetype: modify add: orclaci orclaci: access to entry by group="cn=RealmAdministrators,cn=groups,cn=OracleContext,dc=mycompany,dc=com" (browse,add,delete) orclaci: access to attr=(*) by group="cn=RealmAdministrators,cn=groups,cn=OracleContext,dc=mycompany,dc=com" (read, write, search, compare) orclaci: access to entry by group="cn=OIMAdministrators,cn=groups,dc=mycompany,dc=com" (browse,add,delete) orclaci: access to attr = (*) by group="cn=OIMAdministrators,cn=groups,dc=mycompany,dc=com" (search,read,compare,write) - changetype: modify add: orclentrylevelaci orclentrylevelaci: access to entry by * (browse,noadd,nodelete) orclentrylevelaci: access to attr=(*) by * (read,search,nowrite,nocompare)
-
If you have more than one directory for which Oracle Internet Directory is used as a Shadow directory, then you must create different shadow containers for each of the directories. The container name can be chosen to uniquely identify the specific directory for which this is a shadow entry.
7.2.4 Directory Structure Overview - Shadow Join
Figure 7-1 shows the directory structure in the primary and shadow directories. The containers cn=reservation, cn=appIDUsers, cn=FusionGroups, and cn=DataRoleGroups are speciric to Fusion Applications.
Figure 7-1 Directory Structure
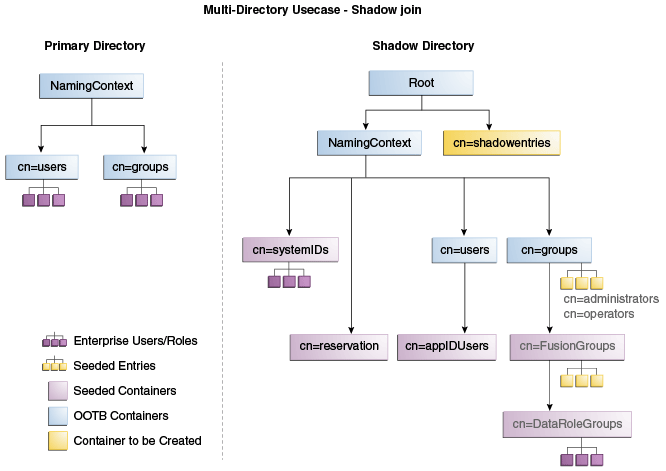
Figure 7-2 shows how the DIT appears to a user or client application. The containers cn=appIDUsers, cn=FusionGroups, and cn=DataRoleGroups are speciric to Fusion Applications.
Figure 7-2 Client View of the DIT
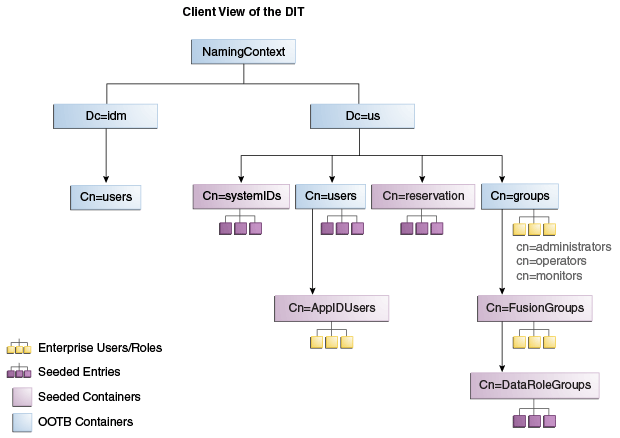
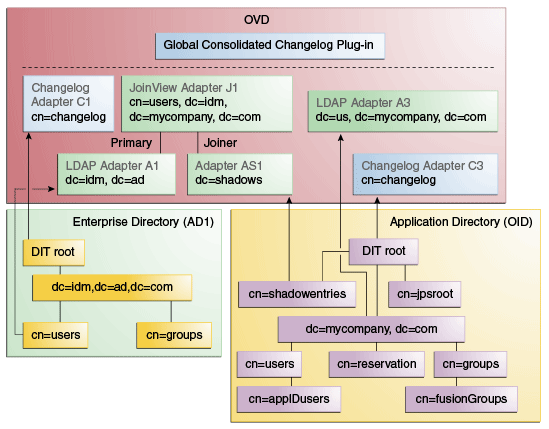
Figure 7-3 summarizes the adapters and plug-ins. The containers cn=appIDUsers, and cn=FusionGroups are speciric to Fusion Applications.
Figure 7-3 Adapter and Plug-in Configuration
7.2.5 Configuring Oracle Virtual Directory Adapters for Split Profile
In order to produce the client side view of the data shown in Figure 7-2, you must configure multiple adapters in Oracle Virtual Directory following the steps in this section.
You can use idmConfigTool to create the adapters to facilitate this configuration.
See Also:
Section A.1, "Verifying Oracle Virtual Directory Adapters for Split Profile by Using ODSM" for instructions on viewing the adapters using Oracle Directory Services Manager.
To create the adapters using idmConfigTool, perform the following tasks on IDMHOST1:
7.2.6 Configuring a Global Consolidated Changelog Plug-in
Deploy a global level consolidated changelog plug-in to handle changelog entries from all the Changelog Adapters.
- In a web browser, go to Oracle Directory Services Manager (ODSM).
- Connect to an Oracle Virtual Directory instance.
- On the Home page, click the Advanced tab. The Advanced navigation tree appears.
- Expand Global Plugins
- Click the Create Plug-In button. The Plug-In dialog box appears.
- Enter a name for the Plug-in in the Name field.
- Select the plug-in class ConsolidatedChglogPlugin from the list.
- Click OK.
- Click Apply.
7.2.7 Validating the Oracle Virtual Directory Changelog
Run the following command to validate that the changelog adapter is working:
$IDM_ORACLE_HOME/bin/ldapsearch -p 6501 -D cn=orcladmin -q -b 'cn=changelog' -s base 'objectclass=*' lastchangenumber
The command should return a changelog result, such as:
Please enter bind password: cn=Changelog lastChangeNumber=changelog_OID:190048;changelog_AD1:363878
If ldapsearch does not return a changelog result, double check the changelog adapter configuration.
7.3 Configuring Multiple Directories as an Identity Store: Distinct User and Group Populations in Multiple Directories
In this configuration, you store Oracle-specific entries in Oracle Internet Directory and enterprise-specific entries in Active Directory. If necessary, extend the Active Directory schema. See Configuring Active Directory for Use with Oracle Access Manager and Oracle Identity Governance in Oracle® Fusion Middleware Enterprise Deployment Guide for Oracle Identity and Access Management.
Note:
The Oracle Internet Directory that is to be used is not necessarily the PolicyStore Oracle Internet Directory. Conceptually, a non-Active Directory directory can be used as the second directory. For convenience, this section refers to the Policy Store Oracle Internet Directory.
The following conditions are assumed:
-
Enterprise Directory Identity data is in one or more directories. Application-specific attributes of users and groups are stored in the Enterprise Directory.
-
Application-specific entries are in the Application Directory. AppIDs and Enterprise Roles are stored in the Application Directory,
This section contains the following topics:
7.3.1 Directory Structure Overview for Distinct User and Group Populations in Multiple Directories
Figure 7-4 shows the directory structure in the two directories, listed here as internal and external. The containers cn=appIDUsers, cn=FusionGroups, and cn=RGX_FusionGroups are Fusion Applications-specific.
Figure 7-4 Directory Structure
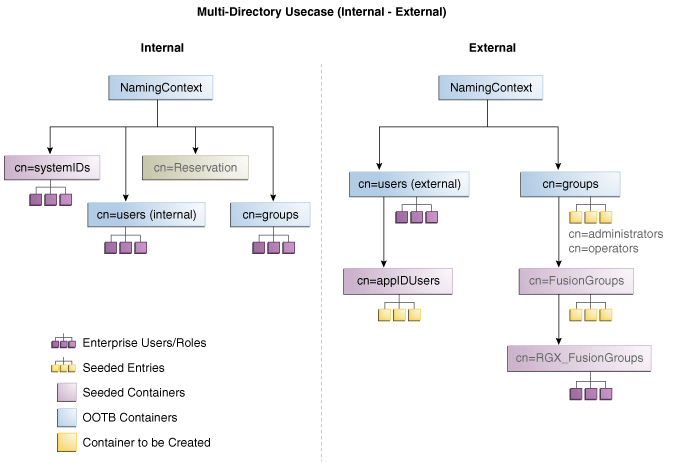
Oracle Virtual Directory makes multiple directories look like a single DIT to a user or client application, as shown in Figure 7-5. The containers cn=appIDUsers, cn=FusionGroups, and cn=RGX_FusionGroups are Fusion Applications-specific.
Figure 7-5 Client View of the DIT
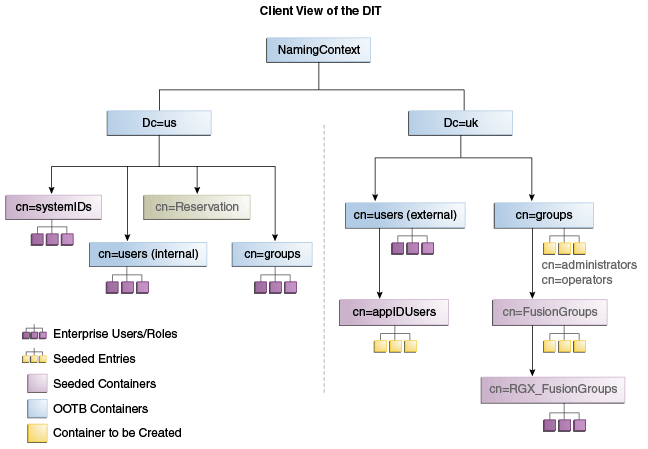
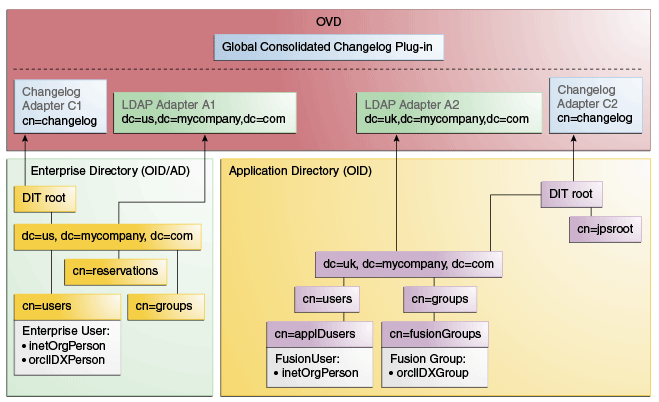
Figure 7-6 provides an overview of the adapter configuration. The classes inetOrgPerson, orclIDXPerson, and orclIDXGroup and the containers cn=appIDusers and cn=fusionGroups are required only for Fusion Applications.
Figure 7-6 Configuration Overview
7.3.2 Configuring Oracle Virtual Directory Adapters for Distinct User and Group Populations in Multiple Directories
Create the user adapter on the Oracle Virtual Directory instances running on LDAPHOST1 and LDAPHOST2 individually, as described in the following sections:
7.3.2.1 Creating Enterprise Directory Adapters
Create Oracle Virtual Directory adapters for the Enterprise Directory. The type of adapter that is created will be dependent on whether or not the back end directory resides in Oracle Internet Directory or Active Directory.
You can use idmconfgTool to create the Oracle Virtual Directory User and Changelog adapters for Oracle Internet Directory and Active Directory.
See Also:
Section A.1 for instructions on viewing the adapters using Oracle Directory Services Manager.
Oracle Identity Management requires adapters. It is highly recommended, though not mandatory, that you use Oracle Virtual Directory to connect to Oracle Internet Directory.
To create the adapters using idmconfgTool, perform the following tasks on IDMHOST1:
Run this command on each Oracle Virtual Directory host in your topology, with the appropriate value for ovd.host in the property file.
7.3.2.2 Creating Application Directory Adapters
Create Oracle Virtual Directory adapters for the Application Directory. The back end directory for the application directory is always Oracle Internet Directory.
You can use idmconfgTool to create the Oracle Virtual Directory User and Changelog adapters for Oracle Internet Directory and Active Directory. Oracle Identity Management requires adapters. It is highly recommended, though not mandatory, that you use Oracle Virtual Directory to connect to Oracle Internet Directory.
To do this, perform the following tasks on IDMHOST1:
Run this command on each Oracle Virtual Directory host in your topology, with the appropriate value for ovd.host in the property file.
7.4 Additional Configuration Tasks When Reintegrating Oracle Identity Governance With Multiple Directories
If you have previously integrated Oracle Identity Management with a single directory and you are now reintegrating it with multiple directories, you must reset the changelog number for each of the incremental jobs to zero. The changelog numbers are repopulated on the next run.