4 Executing the Transition
Topics:
4.1 Understanding Transition to OUD
You can upgrade Directory Server and Directory Proxy Server to Oracle Unified Directory. You must perform certain steps to transition to OUD.
Note:
If you are using the Direct Strategy, then skip to: Deploying Replication Gateway or DIP.
You must perform all steps in Executing the Transition regardless of which transition strategy you are using.
4.2 Creating a Complete Backup
Before you start the transition to Oracle Unified Directory, create a complete backup of Oracle Directory Server Enterprise Edition system-critical files, including the binary, database files, and LDIF.
Note:
Oracle recommends that you create a complete backup of your environment before you begin the the transition to Oracle Unified Directory. The transition cannot be reversed. In most cases, if an error occurs, you must stop the transition and restore the entire environment from backup and begin the transition process from the beginning.Ensure that you design a backup and restore strategy to suit your situation. For more information about the different backup options, considerations to take into account, and guidelines for planning a backup and restore strategy, see Designing Backup and Restore Policies in Deployment Planning Guide for Oracle Directory Server Enterprise Edition.
See:
- Binary Backup in Administrator's Guide for Oracle Directory Server Enterprise Edition.
- Backing Up to LDIF in Administrator's Guide for Oracle Directory Server Enterprise Edition.
4.3 Creating a Reference OUD Instance
The OUD reference instance is configured so that it can provide an LDAP service equivalent to ODSEE.
You must first install OUD 12c (12.2.1.4.0) and create a new instance. The new OUD instance is configured and initialized during the transition steps, and then used as a base to configure and deploy additional instances in a replicated topology.
For instructions on installing an OUD instance, see Installing Oracle Unified Directory in Installing Oracle Unified Directory.
You can set up a new OUD instance using one of the following methods:
-
Graphical User Interface (GUI)
-
Command Line Interface (CLI)
-
Batch mode
Note:
If you want to use Secure Socket Layers (SSL) with the Directory Server instance, then you must enable SSL with real certificates during the directory server instance creation.In order for the ds2oud command to work successfully, you must configure the new instance with no suffixes.
To set up your directory server by using the GUI or by using the CLI, the suffix/base dn must be left blank. See Setting Up the Directory Server Using the Graphical User Interface and Setting Up the Directory Server Using the Command-Line Interface in Installing Oracle Unified Directory.
When the directory server is set up in batch mode, the -b options must not be specified.
Note:
Theds2oud command is located
in <OUD_INSTANCE>/OUD/bin. OUD_INSTANCE is the
path of the base OUD instance.
4.4 Understanding (O)DSEE Directory Server, Configuration, Schema and Data using ds2oud
The existing (O)DSEE settings have certain features that do not have an identical counterpart on the OUD side and hence, cannot be transitioned automatically. These features require special attention during transition.
Ensure that you have the LDAP administrative password to access the (O)DSEE directory server. No changes will be performed on this server during the diagnostic cycle. For further information, see Understanding Root Users and the Privilege Subsystem in Administering Oracle Unified Directory.
Ensure that you have an LDIF file containing the user data exported from your (O)DSEE directory server. For information on exporting LDIF files, go to the following:
-
For information on exporting LDIF files for 5.2, see Exporting Databases in Sun ONE Directory Server 5.2 Reference Manual. You can access the Reference Manual on the Sun Java Enterprise System 2003Q4 website located at
http://docs.oracle.com/cd/E19199-01/. -
For information on exporting LDIF files for 6.x, see Exporting to LDIF in Sun Java System Directory Server Enterprise Edition 6.3 Administration Guide. You can access the Administration Guide in the Sun Java System Directory Server Enterprise Edition 6.3 website located at
http://docs.oracle.com/cd/E19261-01/. -
For information on exporting LDIF files for 7.0, see Exporting to LDIF in Sun Directory Server Enterprise Edition 7.0 Administration Guide. You can access the Administration Guide in the Sun Directory Server Enterprise Edition 7.0 website located at
http://docs.oracle.com/cd/E19424-01/. -
For information on exporting LDIF files for 11g, see Exporting to LDIF in Oracle Directory Server Enterprise Edition Administration Guide. You can access the Administration Guide in the Oracle Directory Server Enterprise Edition 11g Release 1 (11.1.1.7) library located at
https://docs.oracle.com/cd/E29127_01/index.htm.
Ensure that you have access to a copy of the user schema extensions (99user.ldif) holding the (O)DSEE server schema extension.
This diagnostic process is performed by running the ds2oud tool which is shipped with OUD. You can use the number of differences detected by ds2oud in diagnostic mode to estimate complexity and transition effort.
4.4.1 Diagnosing the (O)DSEE Directory Server Configuration and Schema
You can run the ds2oud command to diagnose the configuration and schema of the (O)DSEE Directory Server before transitioning to Oracle Unified Directory.
Run the following ds2oud command:
$ ds2oud --diagnose -h host1.example.com -p 1389 \ -D "cn=directory manager" -j pwdfile
In the command above, host1 is the (O)DSEE server, not the OUD server.
The --diagnose subcommand identifies the following elements of your directory server configuration:
-
Unsupported plug-ins
-
Extensions to the default schema
-
The type of password policy used which may have an impact if you use the Replication Gateway Strategy
-
Encrypted attributes
-
Index settings
-
Global configuration parameters
For each element above, ds2oud identifies what needs to transition and potential incompatibilities (if any). Below is an example of an output:
*** diagnose the deployment ... ******************************************************************************* Diagnose ODSEE Server : host1:1389 ******************************************************************************* ** Plugins : No user plugins are defined, nothing particular to migrate ** Plugins : No subtree counter plugins are enabled, nothing particular to migrate ** Schema The schema was extended regarding the original delivery. The following schema should be added to the new OUD server attributeTypes : ( 2.16.840.1.113730.9999 NAME 'customAttributeType' DESC 'Oracle defined attribute type' SYNTAX 1.3.6.1.4.1.1466.115.121.1.12 SINGLE-VALUE X-ORIGIN ( 'Custom' 'user defined' ) ) ** Password Policy A compatible password policy is defined, nothing particular to migrate ** Naming context(s) available on the ODSEE server : o=migration No incompatibility has been detected for naming context o=migration ** Indexes Only default indexes are defined, nothing particular to migrate ** Encrypted attributes No encrypted attributes are defined, no action is required
4.4.2 Diagnosing the Directory Server Data
You can run the ds2oud command to validate the directory server data against the Oracle Unified Directory schema.
To verify that your directory server data is compliant with OUD schema before importing the data:
4.4.3 Error Resolution During Diagnosis
Learn to resolve schema errors during diagnosis.
Schema errors may be reported for the following reasons:
-
Default schema is different.
-
OUD has a more recent version of standard schema.
-
Attribute value syntax validation and containment rules validations.
-
Unsupported directory metadata. This includes role-based ACIs, Roles or Class of Services definitions currently not supported by OUD password policies as LDAP sub-entries. These sub-entries contain (O)DSEE specific extensions account-based resource limits that differ between (O)DSEE and OUD.
In the above cases, OUD provides the commands below to make schema constraints flexible and resolve those schema errors.
Structural objectclass errors:
Structural objectclass errors occur when your directory server data is rejected during an import. A common reason for this error is the structural object-class for the user entry. The user entry must have exactly one structural object-class. If the entry has zero or more than one, the entry will be rejected. Also, because your (O)DSEE directory server does not differentiate between the two object-class types, this kind of schema inconsistency is common. Use the following command to avoid this error:
dsconfig set-global-configuration-prop --set \ single-structural-objectclass-behavior:accept -n
Invalid attribute value errors:
Attribute values must conform to the attribute syntax defined in the schema. By default, attribute syntax checking is enabled in OUD. For example, an attribute with Boolean syntax can hold TRUE or FALSE values only. In addition, zero-length attribute values are rejected by OUD during an import. However it is possible to make this constraints flexible for the DirectoryString syntax by using this command:
dsconfig set-attribute-syntax-prop --syntax-name Directory\ String \ --set allow-zero-length-values:true -n
4.5 Transitioning Directory Schema
The ds2oud tool in migration mode automatically adds (O)DSEE schema extensions to the OUD reference instance schema while transitioning the directory user schema.
Schema is migrated automatically using the ds2oud tool. You must migrate the schema before you migrate the configuration or errors will be triggered during subsequent transition steps. The following command propagates the user schema from your (O)DSEE directory server to OUD and it can also be used to migrate the (O)DSEE schema to other OUD instances:
$ ds2oud --migrateUserSchema -h host1.example.com -p 1389 \ -D "cn=directory manager" -j pwdfile
To migrate the (O)DSEE schema to other OUD instances, you can also copy the content of the <OUD_INSTANCE>/OUD/config/schema directory to the corresponding directory of the new OUD instance, then restart the OUD instance.
Note:
Although the ds2oud --migrateUserSchema command handles any extensions made on the (O)DSEE user schema, schema violations still may occur when you import your user data into OUD. This happens because, unlike user-defined schema, standard schema varies slightly between (O)DSEE and OUD. If schema violations occur during the import process, then you must create additional schema extensions which are likely suggested as a result of the (O)DSEE diagnosis process.
4.6 Transitioning Directory Configuration
The OUD reference instance is configured so that it can provide an LDAP service equivalent to (O)DSEE.
Most of the (O)DSEE directory configuration is migrated automatically using the ds2oud tool in migration mode.
Configuration commands generated automatically are kept in a batch file so that they can be reused to initialize other instances quickly. Oracle recommends that additional commands created manually, should also be added to that batch file.
Additional configuration elements that cannot be migrated automatically have been identified in Understanding (O)DSEE Directory Server, Configuration, Schema and Data using ds2oud.
This chapter includes the following sections:
4.6.1 Migrating Configuration Settings Using the ds2oud Command
You can run the ds2oud command to migrate the configuration settings from your (O)DSEE directory server to Oracle Unified Directory.
-
Naming contexts
-
Global configuration settings that are relevant for OUD
-
Size-limit
-
Look-through-limit
-
Idle-time-limit
-
Max-psearches
-
Bind-with-dn-require-password
-
Allidthresholds
-
Database indexes
-
Global default access controls
-
Supported built-in plug-ins
-
7-bit check
-
UID uniqueness plug-in
-
Referential integrity plug-in
-
Strong password policy check
To apply each of the above configuration settings to each OUD instance, you must run the ds2oud command in batch mode. It will then generate a list of commands to be applied with dsconfig. This is recommended to be able to complement changes and replay them easily on every target system.
To produce the administrative command batch file to transition the configuration, run the following command:
ds2oud --migrateConfiguration
--odseeBindDN "cn=directory manager"
--odseePort <ODSEE_PORT>
--odseeBindPasswordFile <ODSEE_ADMIN_PASSWORD_FILE>
--oudBindDN "cn=directory manager"
--oudBindPasswordFile <OUD_ADMIN_PASSWORD_FILE1>
--oudPort <OUD_LDAP_PORT1>
--oudAdminPort <OUD_ADMIN_PORT1>
--no-prompt --batchFile <COMMAND_BATCH_FILE>
This section includes the following topics:
4.6.1.1 Migrating SSL Certificates
By default, self-signed certificates are automatically generated when OUD instances are created. In some cases you might want to reuse the (O)DSEE server certificate for the new OUD instance, so that the transition is transparent for SSL clients. This, however, might require installation of the OUD instance on the same box as the (O)DSEE server depending on SSL certificate options used.
To reuse the SSL server certificate, do the following:
4.6.1.2 Configuring the PKCS#12 Keystore
To configure the OUD PKCS12 keystore run the following command:
dsconfig set-key-manager-provider-prop \
-provider-name PKCS12 \
-set key-store-file:config/dsee.p12 \
-set key-store-pin-file:config/dsee.p12.pin \
-set enabled:true \
In this code sample, the dsconfig command connectivity-related arguments such as ports and credentials are omitted for simplicity.
4.6.1.3 Configuring the LDAPS Connection Handler to use the PKCS#12 keystore
To configure the LDAPS connection run the following command:
dsconfig set-connection-handler-prop \
--handler-name LDAPS\ Connection\ Handler \
--set key-manager-provider:PKCS12 \
4.6.1.4 Importing the Directory Server Certificate Key Pair
To import the certificate to the existing OUD JKS keystore, do the following:
4.6.1.5 Migrating Encrypted Attributes
Use --decrypt-attr option with dsconf export to decrypt attributes. You must ensure that attributes are decrypted when exported to the LDIF file. Corresponding attribute encryption must be configured in OUD so that values are re-encrypted during import.
See Configuring Attribute Encryption in Administering Oracle Unified Directory.
4.6.2 Understanding Password Storage Scheme for Coexistence
You must change the OUD password storage scheme configuration if you are using either coexistence strategy, that is, Replication Gateway or DIP. This will ensure that the password storage scheme configured on the OUD side corresponds to an algorithm supported by (O)DSEE. Otherwise, users will not be able to log in anymore on the (O)DSEE side when the password is modified on the OUD side.
In (O)DSEE, passwords are stored using some password encryption scheme, such as, SHA-1. In OUD, this is similar but passwords are stored by default in SSHA512.In OUD, password storage scheme is configured in password policies.
4.6.3 Applying Configuration Changes
You can apply configuration changes to the OUD directory server instance using the command provided in this topic.
Configuration changes generated in Migrating Configuration Settings Using the ds2oud Command, can be applied to the OUD directory server instance with the following command:
dsconfig -h <oud hostname> -p <oud admin port> -D cn="directory manager" -w <admin password> \ -F command_batch_file -X -n
The -F or --batchFilePath option of the dsconfig command enables you to specify several operations that are completed in a single command by consolidating those operations in a file. This can significantly improve performance and simplify configuration of other instances when several dsconfig commands are required.
Additional configuration changes identified in Migrating SSL Certificates, need to be applied also.
Note:
Schema changes must always be applied before configuration changes. These configuration changes will have to be applied on each OUD instance deployed later. See Understanding Replication Gateway Deployment.
4.7 Transitioning User Data and Directory Metadata
Once the OUD reference instance is configured, it is loaded with actual (O)DSEE user data and directory metadata.
Refer to the following sections for more information:
4.7.1 Exporting User Data from (O)DSEE to OUD
User data present in your directory server must first be exported to the LDIF format so that they can be reimported to OUD. The data to be exported depends on the chosen transition strategy.
Go to Understanding (O)DSEE Directory Server, Configuration, Schema and Data using ds2oud, for information on exporting to LDIF files.
For example, if you are using the Direct Transition Strategy or the Transition Strategy Using DIP, replication metadata that accounts for a large volume of the data on the disk should be filtered out at export time. But for the Transition Strategy using Replication Gateway, replication metadata is needed.
If you are using the Direct Transition Strategy or the Transition Strategy Using DIP, run the dsconf export command as shown in the following example to export the user data to LDIF:
$ dsconf export --no-repl --decrypt-attr \ -h host1.example.com -p 1389 \ dc=example,dc=com odsee-data.ldif
If you are using Transition Using Replication Gateway Strategy the replication metadata must be kept and adapted to OUD format. To export the user data to LDIF using this strategy, run the dsconf export command as shown in the following example:
$ dsconf export -f opends-export --decrypt-attr -h host1.example.com -p 1389 \ dc=example,dc=com odsee-data.ldif
Note:
The option -f opends-export in the preceding command is only applicable for ODSEE 11g Release 1 (11.1.1.5 or later) since the data must be exported from the ODSEE 11g master which is required if you are using the Replication Gateway. Also note that encrypted data on the disk must be decrypted during export.
To produce an LDIF file for DSEE 6.3 (DSEE 6.3 does not provide the -f option):
-
Export the LDIF from DSEE 6.3 using
dsconfcommand (do not include -f) -
Run
ds2oud --adaptDseeData<path to LDIF file> (This generates a new LDIF file <path to LDIF file>_result.ldif) -
Import the generated file into OUD by using the command:
import-ldif -b <your user data suffix> -n <db name e.g userRoot> --excludeAttribute "nsds5replconflict" -l <path to LDIF file_result.ldif>
4.7.2 Importing Data to OUD
You can use the import-ldif command to populate the Oracle Unified Directory server backend with data read from the LDIF file.
The following is an import-ldif example:
import-ldif -b <your user data suffix> -n userRoot --excludeAttribute "nsds5replconflict" -l <path to LDIF file>
When you use the opends-export option during transition, (O)DSEE-specific attributes might exist in some entries which will prevent these entries from being imported. For instance, nds5replconflict might exist in the (O)DSEE data so it is imperative to filter this attribute during import to OUD using the following import option:
--excludeAttribute "nsds5replconflict"
4.7.3 Strategy for Directory Metadata Transition
Directory metadata transition depends on the transition strategy you have chosen to use. This may include access control information (ACI), collective attributes and LDAP sub entries.
The different strategies for directory metadata transition:
-
For the Direct Transition Strategy: the directory metadata only must be adapted once.
-
For the Replication Gateway Strategy: directory metadata are replicated between the directory server and OUD. The directory metadata must be kept compatible on both sides. However, some metadata are different between the two environments, so additional schema extensions will be required to avoid errors or loss of data.
-
For the DIP Strategy: DIP should be configured to synchronize user data. The directory metadata is generally added manually on OUD. In some cases, you can configure DIP to synchronize the metadata.
Access to data is managed with access control instructions (ACIs) that specify the access rights of entries. ACIs can be stored as part of the user data or in the OUD configuration.
-
Global ACIs versus ACIs in the data
Global ACIs apply to all entries in the directory. They are stored in the configuration. (O)DSEE and OUD global ACIs can differ without causing errors as they are not replicated.
The
ds2oudtool migrates the global ACIs to OUD global ACIs automatically.ACIs that are stored as part of the data, are replicated.
-
Differences with Syntax
The
rolednkeyword is currently not supported in OUD 12c. ACIs with therolednkeyword cannot be imported into OUD because ACI syntax checking fails. Roles can be replaced by groups and therolednkeyword can be replaced bygroupdn(See Roles and ACIs).A new value for the
targetscopekeyword,subordinate, is introduced in OUD. This value is not supported by (O)DSEE so it must not be used in a two-way replication topology between (O)DSEE and OUD. -
Behavioral Differences
In a few cases, evaluation of the same ACI differs between (O)DSEE and OUD. Since OUD grants less access by default than (O)DSEE, you will need to grant additional write access during the transition so that OUD behaves like (O)DSEE. In such cases, OUD ACI evaluation would be more inflexible than on the (O)DSEE side.
By default, OUD ACIs do not allow users to reset another user's password. With OUD, a privilege must be added to achieve behavior that is equivalent to that of (O)DSEE. Alternatively, it is possible to disable the privilege subsystem. For example, the command below allows the admin to reset user passwords in (O)DSEE (this type of password reset is refused by default in OUD):
ldapmodify -p <dsee port> -D "cn=directory manager"-w <admin password dn: dc=example,dc=com changetype: modify replace: aci aci: (targetattr = "*") (version 3.0;acl "Custom LDAP Administrator";allow (all)(userdn = "ldap:///uid=admin,dc=example,dc=com");)
With OUD, the following privilege below must be added to achieve the equivalent behavior:
dn: uid=admin,dc=example,dc=com changetype: modify add: ds-privilege-name ds-privilege-name: password-reset
Alternatively, the privilege subsystem can be disabled using the following command:
dsconfig set-global-configuration-prop -add disabled-privilege:password-reset
4.7.4 ACIs in Replication Topologies
When (O)DSEE and OUD do not need to coexist in a replication topology, ACIs can be manually adapted, if needed, before importing them into OUD, as described previously.
When one-way replication is used, ACIs present in the data on (O)DSEE may have to be adapted manually before transition. Invalid ACIs will not be imported during replication initialization because of ACI syntax checking. ACIs updates on the (O)DSEE side might still be replicated to OUD but they will not be applied on the OUD side.
If you have incompatible ACIs, an alternate is to configure the Replication Gateway to filter out ACIs during replication. Each (O)DSEE ACI would be filtered out and the administrator would need to create the corresponding ACIs in OUD, either as part of the data or in the configuration.
For two-way replication between (O)DSEE and OUD, the same recommendations as for one-way replication applies. In addition, OUD-specific ACIs extensions must not be used in a mixed environment.
Note:
(O)DSEE and OUD ACIs are compatible except, in some cases, when (O)DSEE specific keywords as roleDN are used.
4.7.5 Understanding Class of Service (CoS)
Class of Services definitions are stored as LDAP sub entries along with the user data. Class of Services functionality is currently not supported in OUD. When replication is configured between (O)DSEE and OUD, CoS definitions are automatically filtered out by the Replication Gateway.
CoS can be replaced by the standard Collective Attributes mechanism or by Virtual Attributes. In a replicated topology, computed attributes are generated by CoS on the (O)DSEE side while the equivalent computation is achieved with Collective Attributes or Virtual attribute on the OUD side.
4.7.5.1 Collective Attributes Vs. Virtual Attributes
Collective attributes definitions are stored as LDAP sub entries along with the user data, which means that they are replicated. Collective attributes provide fine-grained scoping control through the generic sub-entry subtree specifications. Virtual attributes are stored in the OUD configuration and are not subject to replication. When two-way replication is enabled between (O)DSEE and OUD, you should use Virtual Attributes instead of Collective attributes because Collective Attributes definitions are replicated back to (O)DSEE.
If you specifically need to use Collective attributes (see Classic CoS and Indirect CoS), the (O)DSEE schema should be extended with the schema object that pertain to Collective Attributes. In this case, the LDAP sub entries will be present in (O)DSEE but they will be inactive. This means that they will not cause any attribute computation. The schema definition associated with the collectiveAttributeSubentry and subentry object classes (present in the OUD schema file 00-core.ldif) and the associated attributes can be added to the (O)DSEE schema.
Note:
In (O)DSEE, CoS is often used with roles and password policies. For example, you can use CoS to assign a custom password policy to a set of users. OUD provides new ways to assign password policies to user accounts. Therefore, usually, there are simple alternatives to CoS.
(O)DSEE Class Of Service type is covered in detail in the following sections.
4.7.5.2 Pointer CoS
You can use (O)DSEE Pointer CoS to share a common attribute among a set of entries.
The following (O)DSEE Pointer CoS below automatically assigns a facsimiletelephonenumber with a fixed value (+61245607890) to all entries located under ou=People,dc=example,dc=com.
dn: cn=ZipTemplate,ou=People,dc=example,dc=com objectclass: top objectclass: LDAPsubentry objectclass: extensibleobject objectclass: cosTemplate facsimiletelephonenumber: +61245607890 cosPriority: 0 dn: cn=pointerCoS,ou=People,dc=example,dc=com objectclass: top objectclass: LDAPsubentry objectclass: cosSuperDefinition objectclass: cosPointerDefinition cosTemplateDn: cn=ZipTemplate,ou=People,dc=example,dc=com cosAttribute: facsimiletelephonenumber
You can use the following OUD virtual attribute to compute an equivalent attribute value. This example creates and enables a virtual attribute rule that adds a virtual fax number of +61245607890 to any user entry matching the objectclass=person filter (unless there is already a fax number in the user entry):
dsconfig -h localhost -p 4444 -D "cn=directory manager" -j <password_file> -n \ create-virtual-attribute \ --type user-defined -name "Sydney Fax Number" \ --set attribute-type:facsimiletelephonenumber -set enabled:true \ --set value:+61245607890 -set filter:"(objectClass=person)"
Unlike virtual attributes, collective attributes are stored along with user data, so they are replicated across OUD instances.
The following collective attribute generates a facsimiletelephonenumber for entries in the sub-tree ou=people,dc=example,dc=com
dn: cn=People Preferred Language,dc=example,dc=com
changetype: add
objectClass: top
objectClass: subentry
objectClass: collectiveAttributeSubentry
objectClass: extensibleObject
cn: People fac simile number
facsimiletelephonenumber;collective: +61245607890
subtreeSpecification: {base "ou=people", minimum 1}
collectiveConflictBehavior: virtual-overrides-real
4.7.5.3 Indirect CoS
(O)DSEE Indirect CoS names an attribute in the cosIndirectSpecifier attribute to locate the template specific to each target. The template entry for indirect CoS can be any entry in the directory, including other user entries. The following indirect CoS example uses the manager attribute of the target entry to identify the CoS template entry. The template entry is the manager's user entry. The manager's user entry contains the value of the attribute to generate. In this case, the value is that of the departmentNumber attribute.
dn: cn=generateDeptNum,ou=People,dc=example,dc=com objectclass: top objectclass: LDAPsubentry objectclass: cosSuperDefinition objectclass: cosIndirectDefinition cosIndirectSpecifier: manager cosAttribute: departmentNumber dn: cn=Carla Fuentes,ou=People,dc=example,dc=com objectclass: cosTemplate objectclass: person departmentNumber: 318842 cn: Carla Fuentes
You can use inherited collective attributes to replace Indirect CoS. Like regular collective attributes, inherited collective attributes are defined using LDAP sub-entries within the directory tree where they are applicable. Inherited collective attributes are replicated across OUD instances. If two-way replication is used between (O)DSEE and OUD, the (O)DSEE schema should be extended with the Collective Attribute schema element as described in Collective Attributes Vs. Virtual Attributes. The following inherited collective attribute is equivalent to the Indirect CoS definition described previously.
dn: cn=indirectCOS,dc=example,dc=com
objectClass: top
objectClass: subentry
objectClass: inheritedCollectiveAttributeSubentry
objectClass: inheritedFromDNCollectiveAttributeSubentry
cn: indirectCOS
subtreeSpecification: {base "ou=people"}
inheritFromDNAttribute: manager
inheritAttribute: departmentNumber
4.7.5.4 Classic CoS
This example shows how to generate a postal address value with a classic CoS definition. The generated value is specified in a template entry that is located by a combination of the cosTemplateDN in the CoS definition and the value of the cosSpecifier attribute in the target entry. The following example creates the definition entry by using the cosClassicDefinition object class:
dn: cn=classicCoS,dc=example,dc=com objectclass: top objectclass: LDAPsubentry objectclass: cosSuperDefinition objectclass: cosClassicDefinition cosTemplateDn: ou=templates,ou=People,dc=example,dc=com cosSpecifier: building cosAttribute: postalAddress dn: cn=B07,ou=templates, ou=People,dc=example,dc=com objectclass: top objectclass: LDAPsubentry objectclass: extensibleobject objectclass: cosTemplate postalAddres: 7 Old Oak Street, Anytown, CA 95054
With this CoS definition, target entries (the entries under ou=People,dc=example,dc=com) that contain the building attribute will automatically have the corresponding postal address. The CoS mechanism searches for a template entry that has the specifier attribute value in its RDN. In this example, if Babs Jensen is assigned to building B07, her postal address is generated.
Equivalent behavior can be achieved in OUD with inherited collective attributes as follow:
dn: cn=classicCOS,dc=example,dc=com
objectClass: top
objectClass: subentry
objectClass: inheritedCollectiveAttributeSubentry
objectClass: inheritedFromRDNCollectiveAttributeSubentry
cn: classicCOS
subtreeSpecification: {base "ou=people"}
inheritFromBaseRDN: ou=templates
inheritFromRDNAttribute: building
inheritFromRDNType: cn
inheritAttribute: postalAddress
This inherited collective attribute sub-entry applies to user entries under ou=people,dc=example,dc=com. The subentry adds the postalAddress attribute inherited from the user entry whose DN is constructed from ou=templates, the Inherited collective attribute sub-entry root DN dc=example,dc=com and the RDN cn value taken from applicable entry building attribute, if any.
Like regular collective attributes, inherited collective attributes are defined using LDAP sub-entries within the directory tree where they are applicable. They are replicated across OUD instances. If two-way replication is used between (O)DSEE and OUD, the (O)DSEE schema should be extended with the collective attribute schema element as described in the Collective Attributes Vs. Virtual Attributes.
4.7.6 Overview of Roles Transition to OUD
Currently, Oracle Unified Directory does not support non-standard (O)DSEE roles and are usually replaced by standard OUD groups. The Replication Gateway filters out role definitions. The steps required to transition (O)DSEE roles to OUD depend on the way in which the roles are exposed to external client applications.
In many deployments, roles are not exposed to client applications, that is, applications do not use the nsRole or nsRoleDN attributes. Such roles can be replaced by either static or dynamic groups for ACIs and password policies.
This section includes the following topics:
4.7.6.1 Roles and ACIs
You can use the roledn ACI keyword to grant/deny access to data based on user role. For example, the following (O)DSEE ACI grants access to the user password attribute to users with Password Manager role.
dn: ou=data,o=example.com aci: (targetattr="userPassword")(version 3.0; acl "PasswordManager";allow (read,search,compare,write) roledn = "ldap:///cn=Password_Manager_Role,ou=roles,dc=example,dc=com";
The roledn keyword is not supported in OUD 12c (12.2.1.4.0). This has the following implications:
-
ACIs with the
rolednkeyword cannot be imported into OUD 12c (12.2.1.4.0). -
ACIs present in the (O)DSEE data will not be applied to OUD. These ACIs will be replicated to OUD but changes will not be applied because the ACI syntax does not work for OUD
Roles used in ACIs should be replaced by groups using the groupdn keyword before transition. For OUD, the preceding ACI above can be rewritten as:
dn: ou=data,o=example.com aci: (targetattr="userPassword")(version 3.0; acl "PasswordManager";allow (read,search,compare,write) groupdn = "ldap:///cn=Password_Manager_Group,ou=group,dc=example,dc=com";
The group pointed to by the ACI can be either a static group or a dynamic group.
To migrate role-based ACIs to group-based ACIs before you transition to OUD, you must:
-
Define groups that correspond to the roles (using the same DN)
-
Rewrite ACIs on the (O)DSEE side before transitioning to OUD
Note:
Role-based ACIs present in the (O)DSEE configuration are not replicated, so they do not need to be rewritten.
4.7.6.2 Roles and Password Policies
In many deployments, roles are used to assign custom password policies based on role membership. For example, users with the Admin role are subject to the Administrator password policy. In this use case, roles are used with CoS to create the virtual attribute pwdPolicySubEntry in every user entry pointing to the password policy that is necessary.
In OUD, a password policy can be associated directly with members of a group by using a virtual attribute. The following example associates the adminPasswordPolicy password policy with members of the administrator group.
dsconfig create-virtual-attribute -name "PWPolicy for Admins" --type user-defined --set attribute-type:ds-pwp-password-policy-dn --set group-dn:cn=administrators,ou=groups,dc=example,dc=com --set conflict-behavior:real-overrides-virtual --set value:"cn=adminPasswordPolicy,ou=policies,ddc=example,dc=com"
Note:
Unlike CoS, the virtual attribute above that associates password policies with roles is not replicated across OUD instances.
4.7.6.3 Exposing Roles to Client Applications
If you are using the Direct Transition Strategy or Transition Using DIP Strategy (the following is not compatible with the Transition Using Replication Gateway Strategy), use the nsRole attribute in the target user's entry to determine whether the DN of the appropriate role is present when you need to determine whether a user is a member of a given role in an application. In this case, role functionality can be simulated by following steps:
If the application alters membership by placing the name of the corresponding role in the nsRoleDN virtual attribute in a user's entry, create a dynamic group for each role (you must reuse the role DN), and extend the group memberURL filter so that it takes into account the nsRoleDN for group membership. In the following example, any user entry that contains a nsRoleDN value of "cn=Test Role,ou=Roles,dc=example,dc=com" also has that DN present in the nsRole operational attribute.
dn: cn=Test Role,ou=Roles,dc=example,dc=com objectClass: top objectClass: groupOfURLs cn: Test Role memberURL: ldap:///dc=example,dc=com??sub?(nsRoleDN=\ cn=Test Role,ou=Roles,dc=example,dc=com)
If your application needs to create, modify or delete role entries (for example, an entry containing one of the subordinates of the nsRoleDefinition object class), that functionality is currently not available in OUD.
4.7.6.4 Understanding Securely Transitioning Roles
In OUD, groups replace roles. To use the corresponding groups securely, you must set access control instructions (ACIs) to protect appropriate attributes. With dynamic groups, you must protect the part of the filter that would prevent the user from being able to relinquish the filtered group by modifying an attribute. Users should not be allowed to add, delete, or modify the attribute used by the filtered groups. In the same way, if the value of the filter attribute is computed, all the attributes that can modify the value of the filter attribute must be protected.
4.7.7 Understanding Password Policies Transition to OUD
Password policies are treated differently in DSEE and OUD, and thus there are different ways to manage the policy transition to OUD.
This section contains the following topics:
4.7.7.1 Guidelines for Transitioning Password Policies
The ds2oud tool, provided with OUD, migrates the standard attributes of the default password policy only. See Table 4-1 for password policy mapping from (O)DSEE to OUD.
Custom password policies can be stored either in the data or in the OUD configuration and can be assigned to target users by an attribute in the user entry or based on the position of the sub entry in the DIT. Selecting the best options is key for a successful password policy transition. Ease of use and impact on the OUD administration should be considered (for example, password policies as sub-entries are replicated across OUD instances, password policies in the configuration are not). In addition, not all combinations are possible in OUD 12c (12.2.1.4.0).
The following options must be selected based on your deployment constraints:
-
Store custom password policies as sub entries or in the OUD configuration
-
Use attributes in user entries or use the sub entry sub tree specification to assign password policies
-
If an attribute in user entry is used to assign the password policy, use an explicit setting, virtual attributes or collective attributes to populate the attribute
-
Reuse or filter out (O)DSEE password policies during replication
The main decision criteria to be considered are:
-
Does the (O)DSEE custom password policy rely on specific extensions?
-
Is replication used with (O)DSEE one-way only?
-
Is the (O)DSEE custom password policy sub-entry position compatible with OUD?
-
Is password policy assignment based on group memberships?
The following is a summary of the differences between OUD and (O)DSEE password policies:
-
The (O)DSEE password policy definition consists of standard attributes (defined in the
pwdPolicyobject class) and specific extensions (defined in thesunPwdPolicyobject class). -
OUD password policies also rely on standard attributes (defined in the
pwdPolicyobject class). However, (O)DSEE-specific extensions are currently not supported in OUD 12c (12.2.1.4.0). Such extensions are automatically filtered out during replication and must be replaced by OUD-specific extensions defined in theds-cfg-password-policyobject class.
Manual Adaptations required to migrate these extensions are summarized in the table below:
Table 4-1 Password Extensions for (O)DSEE and OUD
| (O)DSEE Extensions | OUD Extensions |
|---|---|
|
PasswordStorageScheme |
default-password-storage-scheme |
|
PwdKeepLastAuthTime |
last-login-time-attribute, last-login-time-format |
|
PasswordRootDnMayByPassModsChecks |
skip-validation-for-administrators |
|
pwdIsLockoutPrioritized |
N/A |
|
PwdCheckQuality |
password-validator |
In addition to the global password policy, you can create custom password policies. In (O)DSEE, custom password policies are stored as part of the data, as LDAP sub entries.
In OUD, custom password policies can be stored as part of the data, as LDAP sub entries, or directly in the OUD configuration.
In OUD, password policies defined as LDAP sub entries must rely on standard attributes only (see above) and cannot contain any extensions. This restriction does not apply to password policies stored in the OUD configuration.
4.7.7.2 Password Policy Assignments
In (O)DSEE, a password policy is assigned to a user account based on the value of the pwdPolicySubEntry attribute. The attribute value can be either stored physically in the user entry or dynamically populated with CoS based on criteria matched by the entry. The location of the password policy LDAP sub entry is not used to assign the policy to target users. The default password policy applies when the pwdPolicySubEntry attribute is not present in a user entry.
In OUD, you can assign a password policy to a user account in two ways:
-
By setting the attribute
ds-pwp-password-policy-dn, either explicitly or through a virtual or collective attribute, as in (O)DSEE. -
By creating the password policy sub-entry in the DIT so that all user entries are below the password policy entry and target user entries match the LDAP filter/subtree specification present in the sub-entry. Sub-entry sub-tree specification is defined in RFC 3672.
The following example corresponds to the first case: the password policy ServiceAccount is assigned to members of the group group_FirstLoginPolicy by creating a virtual attribute that populates the attribute ds-pwp-password-policy-dn based on group membership:
dn: cn=group_FirstLoginPolicy,dc=example,dc=com objectClass: groupOfURLs MemberURL: ldap://ou=people,dc=example,dc=com??sub? (pwdReset=TRUE) cn:group_FirstLoginPolicy dsconfig create-virtual-attribute --name "PWPolicy to Admins" \ --type user-defined --set attribute-type:ds-pwp-password-policy-dn \ --set group-dn:cn=group_FirstLoginPolicy,dc=example,dc=com \ --set conflict-behavior:real-overrides-virtual \ --set value:"cn=ServiceAccount,ou=passwordPolicies,ou=config,dc=example,dc=com"
The following example corresponds to the second case: the policy FirstLoginPolicy applies to users who are members of the group newbees in the subtree ou=people,dc=example,dc=com.
dn: cn=FirstLoginPolicy,dc=example,dc=com
objectClass: subentry
Objectclass: pwdpolicy
SubtreeSpecification: { specificationFilter "ismemberOf=cn=group_FirstLoginPolicy,dc=example,dc=com"}
PwdMaxFailure: 2
PwdAttribute: userPassword
cn:FirstLoginPolicyNote:
The subtree specification as implemented in OUD is a super-set of the standard: OUD considers any well-formed LDAP filter as a valid value for the specificationFilter attribute. This is a very convenient way to assign password policies based on group membership as shown in the preceding example.
4.7.7.3 Password Policy Inheritance
Evaluation of custom password policies differs between (O)DSEE and OUD. In (O)DSEE, a custom password policy overrides the default password policy settings. With OUD, a custom password policy inherits from the default password policy: Properties not defined at the custom policy level are taken from the default password policy at the functional level (even if the attribute names do not correspond). These differences must be taken into account during transition.
4.7.7.4 Password Policy and Replication Gateway
When OUD and (O)DSEE coexist in a replicated topology, password policies should be kept as consistent as possible between the two environments, even when they are not replicated through the replication protocol. For example, if password validators differ, a password could be valid on one side and considered invalid on the other side, leading to inconsistencies.
If account lockout is enabled for a given set of entries on (O)DSEE and disabled on OUD (or the reverse), a password reset will not unlock the account on the other side.
4.7.7.5 Replication Gateway and Upgrading (O)DSEE Password Policy
In a replicated topology with global password policy and account lockout across the entire topology, the (O)DSEE servers that communicate directly with the Replication Gateway must run with the password policy in DS6mode and the user entries must not contain data related to previous password policy mode. This is not a must have if you do not need global password policy and when OUD and (O)DSEE can have its own password policy management. Other (O)DSEE servers can run in compatibility mode, but such deployment is not the preferred one.
For more information about changing password policy modes, see Managing Password Policies in Administering Oracle Unified Directory.
You can use the dsconf get-server-prop pwd-compat-mode command to retrieve the current password policy mode. By default, ODSEE 11g Release 2 uses the DS5-compatible mode. You must switch to DS6-mode before exporting data from (O)DSEE. To switch to DS6-mode, you will need to first switch to the intermediate DS6-migration mode.
For more information on the process to switch to DS6-mode and
regenerate user entries, see Password Policy Compatibility in
Administrator's Guide for Oracle Directory Server Enterprise Edition.
4.7.7.6 Configuring Account Lockout policies
Both (O)DSEE and OUD allow you to configure password policies to force the lockout of accounts after a specified number of failed bind attempts. In addition, it is possible to lock an account manually. The locked account remains locked until the account is activated.
Transition of account state (locked/unlocked) between (O)DSEE and OUD require specific settings. In (O)DSEE, manual account lock relies on Roles: Locked entries are assigned nsRoleDN=cn=nsManagedDisabledRole,dc=com role. On OUD, manual account lock relies on the boolean attribute ds-pwp-account-disabled. To automatically import a manually locked account from (O)DSEE to OUD, use the following steps:
4.7.7.7 Custom Resource Limits
In (O)DSEE, the following limits can be associated with a password policy:
-
The look-through limit specifies the maximum number of entries examined for a search operation.
-
The size limit specifies the maximum number of entries returned in response to a search operation.
-
The time limit specifies the maximum time spent processing a search operation.
-
The idle time-out specifies the maximum time a client connection can remain idle before the connection is dropped.
For more information on setting account limits, see Setting Resource Limits For Each Client Account in Oracle Fusion Middleware Administration Guide for Oracle Directory Server Enterprise Edition. You can find that document in the Oracle Directory Server Enterprise Edition 11g Release 1 index page located at http://docs.oracle.com/cd/E19656-01/.
In addition to that, these limits can be set for specific account/user entries: Some (O)DSEE entries may contain the following resource limit attributes: nsSizeLimit, nsTimeLimit, nsLookThroughLimit, nsIdleTimeout.
Corresponding attributes on OUD are: ds-rlim-size-limit, ds-rlim-time-limit, ds-rlim-lookthrough-limit,ds-rlim-idle-time-limit.
Account-based resource limits are not taken into account by ds2oud and must be migrated manually.
When the Replication Gateway is used, the OUD schema (02-config.ldif) must be modified so that each (O)DSEE attribute name related to resource limits is declared as an alias name for each corresponding OUD attribute.
In (O)DSEE, -1 is used to disable a resource limit. In OUD, 0 is used. One way to address this difference is to create a virtual attribute on OUD to override the content of the OUD attribute when the value of the (O)DSEE attribute is equal to -1. A virtual attribute must be created for the four attributes. Below are descriptions:
attributeTypes: ( 1.3.6.1.4.1.26027.1.1.166 NAME ( 'ds-pwp-account-disabled' 'nsAccountLock' ) SYNTAX 1.3.6.1.4.1.1466.115.121.1.7 SINGLE-VALUE USAGE directoryOperation X-ORIGIN 'OpenDS Directory Server' )
dsconfig create-virtual-attribute --name "mapping nsTimeLimit " \ --type user-defined --set attribute-type:ds-rlim-time-limit \ --set filter:"(nsTimeLimit=-1)" \ --set conflict-behavior:virtual-overrides-real \ --set value:"0" \ --set enabled:true
dsconfig create-virtual-attribute --name "mapping nsLookthroughLimit " \ --type user-defined --set attribute-type:ds-rlim-lookthrough-limit \ --set filter:"(nsLookthroughLimit=-1)" \ --set conflict-behavior:virtual-overrides-real \ --set value:"0" \ --set enabled:true
dsconfig create-virtual-attribute --name "mapping nsIdleTimeout " \ --type user-defined --set attribute-type:ds-rlim-idle-time-limit \ --set filter:"(nsIdleTimeout=-1)" \ --set conflict-behavior:virtual-overrides-real \ --set value:"0" \ --set enabled:true
For the sake of performance, it is recommended to index the four attributes above for 'presence'.
Note:
With the settings above, (O)DSEE resource limit attribute names must always be used even on the OUD side. Use of the OUD attribute name cannot be used when (O)DSEE and OUD cohabit in the same replication topology.
4.8 Deploying Replication Gateway or DIP
Selected applications are validated against the OUD servers.
After completing Transitioning User Data and Directory Metadata, selected applications can be validated against the OUD servers. If you have chosen:
Table 4-2 Validating selected applications
| Deployment strategy | Refer to |
|---|---|
|
Coexistence Using the Replication Gateway |
|
|
Coexistence Using Oracle Directory Integration Platform (DIP) |
|
|
Direct Transition Strategy |
4.8.1 Understanding Replication Gateway Deployment
Understand how replication gateway is deployed. Below are additional components to configure the replication between (O)DSEE and OUD using the Replication Gateway.
Install and configure the Replication Gateway, as described in Setting Up the Replication Gateway in Installing Oracle Unified Directory.
At this point you must configure a global administrator for replication. If you intend to connect this server to an existing replicated OUD topology at a later stage, use the same global administrator credentials that you have defined on the other OUD servers.
For example, assuming an existing OUD topology, your server layout before transition would be as follows:
Figure 4-1 Replication Server Topologies for (O)DSEE and OUD Prior to Transition

Description of "Figure 4-1 Replication Server Topologies for (O)DSEE and OUD Prior to Transition"
After transition, your server layout would be as follows:
Figure 4-2 Replication Server Topologies for (O)DSEE and OUD After Transition
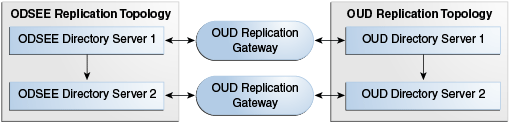
Description of "Figure 4-2 Replication Server Topologies for (O)DSEE and OUD After Transition"
4.8.2 Deploying DIP
Below are additional components to link between (O)DSEE and OUD using DIP. The procedures below configure the (O)DSEE server as the DIP backend directory so that your DIP-related metadata is no longer stored in OUD after you have deprovisioned your old directory server and DIP has been removed.
To deploy DIP:
-
Choose the (O)DSEE master instance and the OUD directory server instance that will be synchronized. The OUD directory server must have an embedded replication server because the external changelog services is provided by replication servers.
-
Synchronize password storage schemes.
Password storage schemes must be identical and compatible between (O)DSEE and OUD. To configure password storage schemes to enable synchronization, see Managing Password Policies in Administering Oracle Unified Directory.
-
Create a directory suffix holding DIP metadata in (O)DSEE.
Use the following command on DSEE 6.x (or higher) to create the suffix
cn=products,cn=oraclecontextto hold DIP metadata:dsconf create-suffix -i -c -p $PORT -D "$ADMIN" -w "$PW_FILE" cn=products,cn=oraclecontext
For instructions on how to create the directory suffix for DSEE 5.2, see Creating Suffixes in Sun ONE Directory Server Administration Guide.
-
Enable changelog.
Changelog must be enabled on the directory that will contain changes. Enable changelog on (O)DSEE with the following command:
dsconf set-server-prop -p $PORT -w "$PW_FILE" retro-cl-enabled:on
For two-way synchronization, external changelog must be enabled on OUD. By default, the external changelog is automatically enabled when the OUD instance is part of a replication topology. For testing purposes, set up a standalone OUD directory server instance and enable external changelog with the following command:
dsreplication enable-changelog --no-prompt --baseDN "dc=example,dc=com" --hostname "$HOST" --port $APORT --bindDN "$ADMIN" --adminPasswordFile "$PW_FILE" --trustAll
-
Install and configure DIP.
-
Install DIP in a Weblogic container.
For more information on installing DIP in a WebLogic container, see Configuring the Oracle WebLogic Server Domain for Oracle Directory Integration Platform with Oracle Unified Directory in Administrator's Guide for Oracle Directory Integration Platform.
-
Configure DIP with the command below:
$ORACLE_HOME/bin/dipConfigurator setup -wlshost <hostname> -wlsport <admin_server_domain_Port> -wlsuser weblogic -ldaphost <dsee_host> -ldapport <dsee_port> -ldapuser "dsee_administrator" -metadatasuffix cn=products,cn=oraclecontext -isldapssl false
The
<dsee_administrator>, for example,cn=directorymanager must be granted read and write access to the DIP metadata suffix (cn=products,cn=oraclecontext).In the default password policy, the
allow-pre-encodedoption must be 'true.' This will allow the<dsee_administrator>to have access to write pre-encoded password.For LDAP users, the following command will change the default password policy:
dsconfig set-password-policy-prop --policy-name Default\ Password\ Policy --set allow-pre-encoded-passwords: true
SSL users refer to the DIP Administrator's Guide to manage certificates.
-
-
Create synchronization profiles.
Ensure that the
oud_ldap_administrator(for example,cn=directory manager) has read and write access to the suffix to be synchronized. Also, when two-way synchronization is used, it must have read access on the OUD external changelog.There are two ways to synchronize profiles: the command line and DIP graphical user interface (EM). The following is an example to synchronize profiles using the command line:
$ORACLE_HOME/bin/expressSyncSetup -h <dip_hostname> -p <dip_domain_port> -D weblogic -conDirType IPLANET -conDirUrl <OUD_host>:<oud_port> -conDirBindDN <oud_ldap_administrator> -conDirContainer <target_suffix> -backendDirContainer cn=products,cn=oraclecontext -pf <profile_name>
The command above creates one import file and one export file with the following naming convention:
-
If the profile name (
-pf argument) is profile1,expresSyncSetupcreates the two following profilesprofile1Exportandprofile1Import.
To create synchronization profile using EM, see Creating Synchronization Profiles in Administrator's Guide for Oracle Directory Integration Platform. Use the DIP graphical user interface to update the list of attributes to be synchronized.
Oracle recommends that you create 1-1 exact attribute mappings (for example,
cn<->cn) and one extra mapping for each attribute alias (for example,commonName->commonName). -
-
Configure ACIs.
Additional directory ACIs must be created on the backend directory server for DIP to operate correctly.
The following command is an example of ACIs created on the backend directory on the suffix to be synchronized (
dc=example,dc=com):ldapmodify -h <dsee_host> -p <dsee_port> -D "cn=Directory Manager" -w <password> <<EOF dn: dc=example,dc=com changetype: modify add: aci aci: (target="ldap:///dc=example,dc=com")(version 3.0; acl "Entry-level DIP permissions"; allow (all,proxy) groupdn="ldap:///cn=dipadmingrp,cn=DIPadmins,cn=Directory Integration Platform,cn=products,cn=oraclecontext"; allow (all,proxy) groupdn="ldap:///cn=odipigroup,cn=DIPadmins,cn=Directory Integration Platform,cn=products,cn=oraclecontext"; ) - add: aci aci: (targetattr="*")(version 3.0; acl "Attribute-level DIP permissions"; allow (all,proxy) groupdn="ldap:///cn=dipadmingrp,cn=DIPadmins,cn=Directory Integration Platform,cn=products,cn=oraclecontext"; allow (all,proxy) groupdn="ldap:///cn=odipigroup,cn=DIPadmins,cn=Directory Integration Platform,cn=products,cn=oraclecontext";) EOF
Export profile's entry must be added to the Export group:
ldapmodify -h <dsee_host> -p <dsee_port> -D "cn=Directory Manager" -w <password> <<EOF dn: cn=odipegroup,cn=DIPadmins,cn=Directory Integration Platform,cn=products,cn=oraclecontext changetype: modify add: uniqueMember uniqueMember: orclodipagentname=profile1Export,cn=subscriber profile,cn=changelog subscriber,cn=directory integration platform,cn=products,cn=oraclecontext EOF
Note that the profile name (
profile1Exportin the example) is part of the DN of the new memberWhen two-ways synchronization is used, the Import profile's entry must be added to the Import group:
ldapmodify -h <dsee_host> -p <dsee_port> -D "cn=Directory Manager" -w <password> <<EOF dn: cn=odipigroup,cn=DIPadmins,cn=Directory Integration Platform,cn=products,cn=oraclecontext changetype: modify add: uniqueMember uniqueMember: orclodipagentname=profile1Import,cn=subscriber profile,cn=changelog subscriber,cn=directory integration platform,cn=products,cn=oraclecontext EOF
In the example above, notice that the profile name (
profile1Exportin the example) is part of the DN of the new member. -
Managing Directory Bootstrapping.
Bootstrapping refers to the initial transition of data between the (O)DSEE back-end directory and OUD. Because the synchronization process can handle the transition of data between an (O)DSEE and OUD, you are not required to perform directory bootstrapping. However, relying on the synchronization process to perform the initial transition will be a time-consuming process. For this reason, you should perform directory bootstrapping when you first deploy DIP.
There are two possibilities to initialize the two directory topologies:
-
Enable the synchronization so that DIP creates every (O)DSEE entry to OUD.
-
Export the content of the (O)DSEE directory to an LDIF file, then import the content to OUD and configure DIP to use the (O)DSEE changelog.
The first solution is simpler but it is much slower than with the Direct Transition Strategy which uses this procedure.
To use the first solution you must:
-
Enable the synchronization profiles.
-
Run the following commands:
$ORACLE_HOME/bin/syncProfileBootstrap -h <dip_host> -p <dip_domain_port> -D weblogic -pf profile1Import $ORACLE_HOME/bin/syncProfileBootstrap -h <dip_host> -p <dip_domain_port> -D weblogic -pf profile1Export
Directory Boostrapping is described in Bootstrapping a Directory in Oracle Directory Integration Platform in Administering Oracle Directory Integration Platform.
To use the LDIF bootstrapping:
-
Use the following command to export entries from DSEE to
data.ldiffile without the replication metadata and with the backend server in off-line mode:$ dsconf export --no-repl -h host -p port suffix-DN LDIF-file
-
Retrieve the change number of the last update applied before the export began. To do so, start the export procedure then write down the time and convert it in Generalized Time in YYYYMMDDHHMMSSZ format: An example of a time stamp in a generalized time format is 20130508200557Z, which specifies a time (in the UTC time zone) of 8:05:57 PM on May 28, 2013.
-
Restart the (O)DSEE server (if needed) after the export has completed.
-
Run the following search command:
ldapsearch -p <dsee_port> -D <dsee_admin> -w <password> -b "cn=changelog" "changetime>= <timeStamp>" changeNumber
-
Note the value of the smallest
changeNumbervalue returned by doing the following:ldapsearch -p PORT -h DSEE HOSTNAME -D "cn=directory manager" -w PASSWORD -b "cn=changelog" "changetime>=20130508200557Z" changeNumber dn: changenumber=16747773,cn=changelog changeNumber: 16747773 dn: changenumber=167477734,cn=changelog changeNumber: 167477734 dn: changenumber=1674777345,cn=changelog changeNumber: 1674777345
-
Use the DIP management console (EM) as described in Managing Synchronization Profiles Using Fusion Middleware Control in Administrator's Guide for Oracle Directory Integration Platform.
Or you can use the
manageSyncProfilesupdatechgnumcommand to start synchronization to update the last change number parameters of the DIP synchronization export profile with the above value. ThemanageSyncProfilesupdatechgnumcommand is described in manageSyncProfiles utility in Administrator's Guide for Oracle Directory Integration Platform. -
Enable the DIP synchronization profiles using GUI or CLI as described in Enabling and Disabling Synchronization Profiles in Administrator's Guide for Oracle Directory Integration Platform.
Synchronization will now begin based on the changelog.
-
4.9 Deploying Replicated Topology
You can set up additional instances in the replicated environment once the OUD reference instance is initialized and most of the transition work is completed.
Additional instances are created and initialized with the batch procedure identified in Transitioning Directory Configuration. Replication is then enabled between OUD instances.
Once a reference OUD server has been configured and loaded with data from (O)DSEE as indicated in: Creating a Reference OUD Instance, Understanding (O)DSEE Directory Server, Configuration, Schema and Data using ds2oud, Transitioning Directory Schema, Transitioning Directory Configuration, additional instances can be set up in the replicated environment. This step covers:
-
Configuring an OUD Replica
-
Deploying Topology
-
Initializing Data
These steps are required for every strategy.
4.9.1 Types of Replicas
Understand about the three types of replicas: Master Replica, Consumer Replica and Hub Replica.
As a reminder, (O)DSEE makes the distinction between three types of replicas:
-
A master replica is a read-write database that contains a master copy of the directory data.
-
A consumer replica is a read-only database that contains a copy of the information held in a master replica.
-
A hub replica is a read-only database, like a consumer replica, but stored on a directory server that supplies one or more consumer replicas.
For more information on (O)DSEE replicas, see Introduction to Replication in Reference for Oracle Directory Server Enterprise Edition.
The OUD replication model is a multi-master model. In other words, all directory server replicas in a replicated topology can process both read and write operations.
Since the release of DSEE 6.x, Oracle have recommended multi-master replica with typical deployments, which eliminated the need for consumer and hub replicas.
In most deployments, using read-only replica is not needed for performance reason and should only be done if the applications require it. In this case it is achieved by configuring the writability mode of the back end. However, you can configure an OUD directory server to be read-only, in which case add, modify, and delete operations from LDAP clients are rejected on this server and a referral is returned containing pointers to others (read-write) servers within the replicated topology.
4.9.2 About OUD Read-Write Replica
The replication concepts and deployments in Oracle Unified Directory are different to those in (O)DSEE. You can learn more about OUD read-write replica and the differences between cascaded and centralized replication.
In (O)DSEE, hub replicas are introduced with cascaded replication to make the replication protocol operate better. Cascading replication is useful in the following scenarios:
-
When there are a lot of consumers.
-
Because the masters in a replication topology handle all update traffic, it could put them under a heavy load to support replication traffic to the consumers. You can off-load replication traffic to several hubs that can each service replication updates to a subset of the consumers.
-
To reduce connection costs by using a local hub in geographically distributed environments.
In OUD, hub replicas do not exist. Replication is built around a centralized publish-subscribe architecture. Each directory server communicates with a central service, and uses the central service to publish its own changes and to receive notification about changes on other directory servers. This central service is called the replication service. OUD read-write masters are the default so in most cases they are deployed.
The replication service can be made highly available by using multiple server instances running on multiple hosts. Within the replication architecture, a server instance that provides the replication service is called a replication server. A server instance that provides the directory service is called a directory server.
In a small topology (up to four directory servers) it makes sense to configure each server to function as both a directory server and a replication server. In a large topology (more than twenty directory servers) it is advisable to separate the directory server and replication server instances into separate JVMs, and to limit the number of replication servers.
Between these two extremes, you can decide on the configuration that works best for your requirements. Having all servers functioning as both directory servers and replication servers is generally a simpler topology and easier to administer. Separating the directory servers and replication servers lowers the disk requirements of the directory server instances because they do not need to store a replication change log.
In large topologies with several directory servers and several replication servers, it is more efficient to spread the directory servers out across the replication servers in a predefined manner. This is particularly important if the replication servers run on different types of machines with different capabilities. If the estimated performance of the machines differs significantly from one replication server to another, it is useful to balance the load on the replication servers according to their power.
You must understand the replication concepts of OUD because they are different than those of (O)DSEE. For more information about configuring Replication Servers and Load-balancing, see Undestanding Replication Server Load Balancing in Administering Oracle Unified Directory.
4.9.3 About OUD Read-Only Replica
The read-only replica in Oracle Unified Directory does not allow the LDAP client applications to perform replication operations directly on the server. Use the dsconfig command to configure Oracle Unified Directory as a read-only replica.
This example assumes a replication configuration with replication servers on two hosts: host1 and host2. The example makes the directory server on host2 a read-only replica and uses the dsconfig command which accesses the server configuration using the administration connector.
For more information on configuring an OUD read-only replica, see Understanding Replication Server Load Balancing in Administering Oracle Unified Directory.
You can configure OUD as a read-only replica using the dsconfig command to set the writability-mode of host2:
$ dsconfig -h host2 -p 4444 -D "cn=Directory Manager" -j <password_file> -X -n \
set-global-configuration-prop --set writability-mode:internal-onlyA writability mode of internal-only means that replication operations are processed on the server, but the server is not writable directly by LDAP client applications.
4.9.4 Deploying Servers in a Replicated Topology
The deployment of Oracle Unified Directory Servers in a replicated topology starts with the creation of OUD instances and the configuration of replication among them.
To create new OUD instances:
- Create an OUD instance. For instructions to set up a directory server, see Setting Up Oracle Unified Directory as a Directory Server in Installing Oracle Unified Directory.
- Configure each OUD instance by applying the configuration changes identified in Transitioning Directory Configuration. For the additional configuration changes that might have been identified while importing the data, see Transitioning User Data and Directory Metadata.
- Run the
dsreplicationcommand to enable replication between OUD instances. For more information on thedsreplicationcommand, see Enabling Replication Between Two Servers With dsreplication in Administering Oracle Unified Directory.
For deploying servers in a replicated topology, see Configuring Data Replication with dsreplication in Administering Oracle Unified Directory.
Once an OUD server is loaded with (O)DSEE data, you can either import the same file on every other OUD instance or use binary copy or initialize a replicated server with the data from another replicated server as described in Administering Oracle Unified Directory.
4.9.5 Initializing OUD with (O)DSEE Data
Once you have set up the replication topology, you will need to initialize it with fresh data. There are four different options for every strategy to initialize the OUD instance with the (O)DSEE data already contained in the reference instance.
If you are using the Replication Gateway Strategy, you must ensure that the OUD reference instance is loaded with (O)DSEE data that was exported before the (O)DSEE replication purge delay configured on (O)DSEE.
The four options are:
-
Run the
dsreplicationcommand to initialize each empty OUD instance. See Initializing a Replicated Server With dsreplication in Administering Oracle Unified Directory. -
Initialize each OUD instance at the same time. See Initializing an Entire Topology With dsreplication in Administering Oracle Unified Directory.
-
Perform a binary copy of the database files from the reference OUD to each OUD instance. See Adding a Directory Server to an Existing Replicated Topology in Administering Oracle Unified Directory.
-
Export entries from the reference OUD and reimported them into each empty OUD instance.
4.10 Redirecting Traffic to the OUD Topology
(O)DSEE and OUD deployments coexist and are synchronized in a production environment while client applications are redirected progressively to OUD. Coexistence between the two environments is kept until the application testing is complete.
This procedure depends on the architecture. Redirection may involve the reconfiguration of the software or hardware load-balancers, LDAP proxy servers, modification of the Domain Name Systems (DNS), or use of IP impersonation.
4.11 Stopping Coexistence
Deprovisioning of Replication Gateway(s) and companion (O)DSEE starts when all the applications have been redirected to Oracle Unified Directory and validated.
Once the Replication Gateway is no longer in use, it can be stopped and then uninstalled and the same is true for the (O)DSEE side.
Note:
After performing Stopping Coexistence, your transition to OUD is complete. If you encounter problems during your transition, contact your Oracle support representative. For more information, go to the My Oracle Support website located at https://support.oracle.com.