7 Managing Permissions and Roles for Oracle SOA Suite Users
Support for SOA permissions and roles changed between 11g and 12c as follows:
-
In 11g, Oracle SOA Suite APIs and runtime were protected using Oracle SOA Suite application roles and Oracle Enterprise Manager Fusion Middleware Control protected user actions with the Oracle WebLogic Server role. Role mapping was required.
- In 12c, Oracle SOA Suite APIs and runtime and Oracle Enterprise Manager Fusion Middleware Control both protect user actions and the user interface using Oracle SOA Suite permissions. (Oracle SOA Suite application roles are defined by a set of permissions.) Therefore, mapping a user to one of the application roles gives them the required permissions.
Note:
By assigning a user to a particular role, the user gets the default permissions associated with that role. Subsequently, permissions associated with a particular role or user can be customized by managing application policies.Creating a WebLogic Server User
To create a user login to the WebLogic Server Administration Console:
- Log in to WebLogic Server Administration Control Console, and click Security Realms in the left pane.
- On the Summary of Security Realms page, select the name of the realm.
- On the Settings for Realm Name page select Users and Groups, then the Users tab, then click New.
- In the Name field of the Create New User page enter a unique name for the user.
- (Optional) In the Description field, enter a description. The description might be the user's full name.
- In the Provider drop-down list, select DefaultAuthenticator.
- In the Password field, enter a password for the new user, then reenter the password in the Confirm Password field.
- Click OK.
For more information about how to create roles, add users to groups, and secure resources with roles and policies in Oracle WebLogic Server, see Users, Groups, and Security Roles in Securing Resources Using Roles and Policies for Oracle WebLogic Server.
Assigning a WebLogic Server Role to a User
To assign a WebLogic Server role to a user:, add the user to a group:
- In the WebLogic Server Administration Control Console Users table, select the user you want to add to a group.
- On the Settings for User Name page, select Groups.
- Select a group from the Available list box.
Some of the default groups available in WebLogic Server are:
Group Name Membership AdministratorsBy default, this group contains the user information entered as part of the installation process (that is, the Configuration Wizard), and the systemuser if the WebLogic Server instance is running Compatibility security. Any user assigned to theAdministratorsgroup is granted theAdminsecurity role by default.DeployersBy default, this group is empty. Any user assigned to the Deployersgroup is granted theDeployersecurity role by default.OperatorsBy default, this group is empty. Any user assigned to the Operatorsgroup is granted theOperatorsecurity role by default.MonitorsBy default, this group is empty. Any user assigned to the Monitorsgroup is granted theMonitorsecurity role by default.AppTestersBy default, this group is empty. Any user assigned to the AppTestersgroup is granted theAppTestersecurity role by default.CrossDomainConnectorsBy default, this group is empty. Any user assigned to the CrossDomainConnectorsgroup is granted theCrossDomainConnectorsecurity role by default.AdminChannelUsersBy default, this group is empty. Any user assigned to the AdminChannelUsersgroup is granted theAdminChannelUsersecurity role by default - Click Save.
Assigning a SOA Role to a User
A user can be assigned an application-level role (such as SOAMonitor)
or a folder-specific role (for example, default_Monitor for the
default folder).
Note:
Roles can also be added to a group or another application role.To assign a SOA role to a user, use Oracle Enterprise Manager Fusion Middleware Control:
- Log in to Oracle Enterprise Manager Fusion Middleware Control as an Administrator.
- From the SOA Infrastructure menu, select
Security, then Application
Roles.
- In the list, select the role that you want to grant to the user and click
Edit.
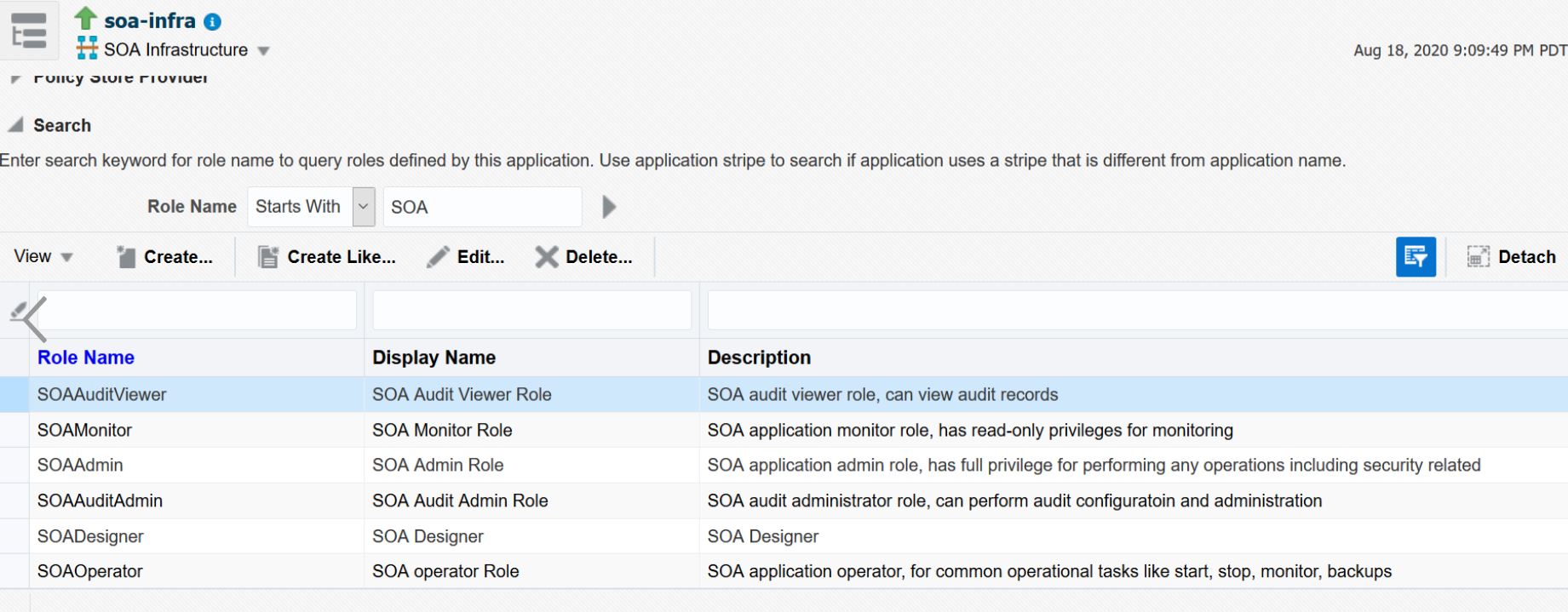
The following screenshot shows the available SOA roles. By assigning a user to one of these roles, the user has the associated permissions for all of the folders and partitions in the SOA application.
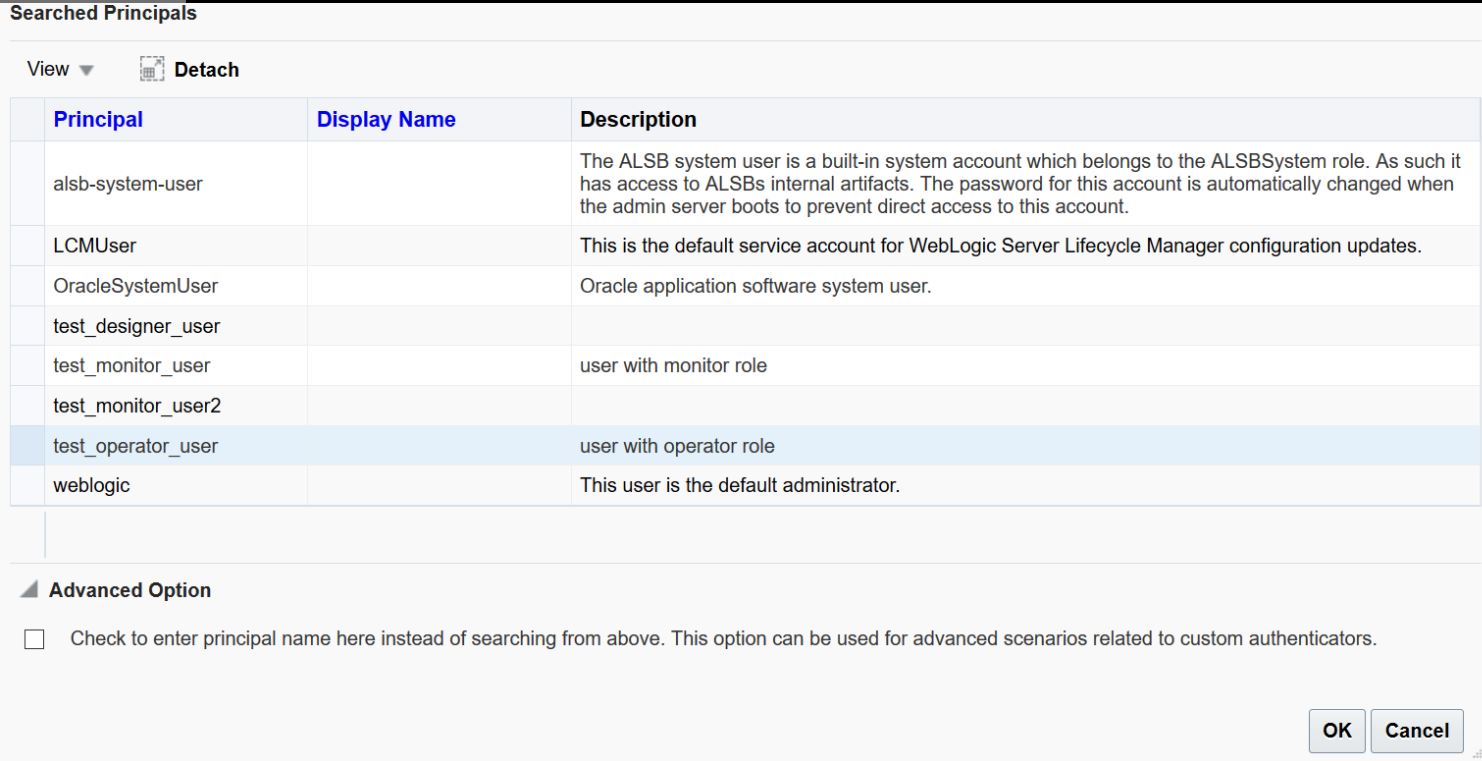
- In the Edit Application Role page, click Add.
- In the Add Principal dialog, from the Type list, and select User.
- In the Principal Name list, select the user and click
OK.
The selected user is given the selected role.
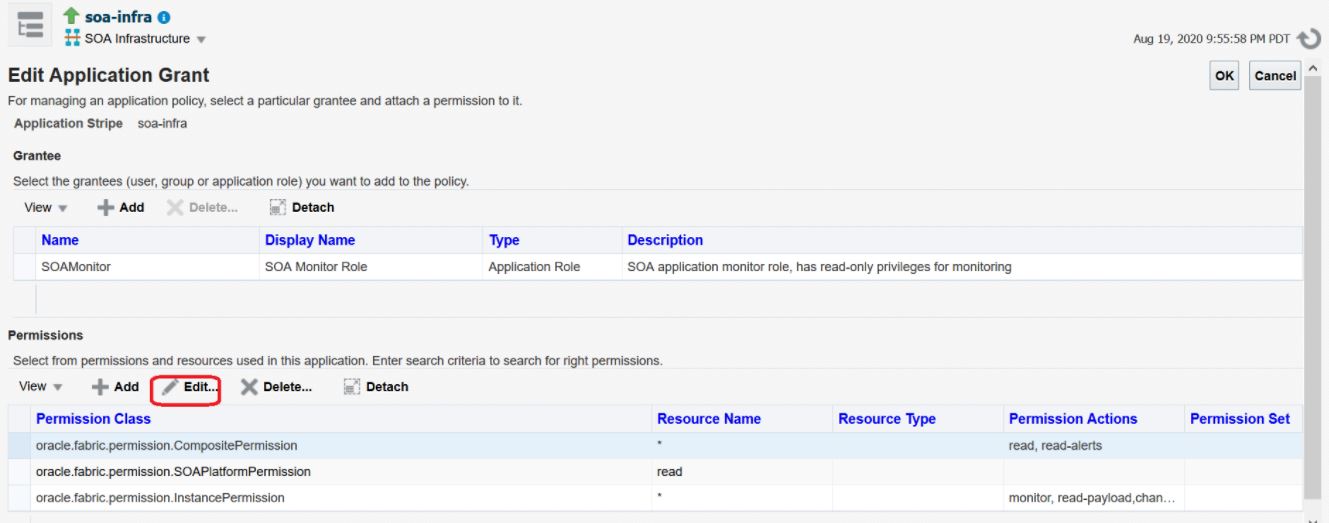
Customize Role Permissions
You can customize permissions associated with a particular role or user by managing application policies.
To customize role permissions:
- Log in to Oracle Enterprise Manager Fusion Middleware Control as an Administrator.
- From the SOA Infrastructure menu, select
Security, then Application
Policies.

- In the list, select the row showing the user and role for which you want to
customize permissions and click Edit.
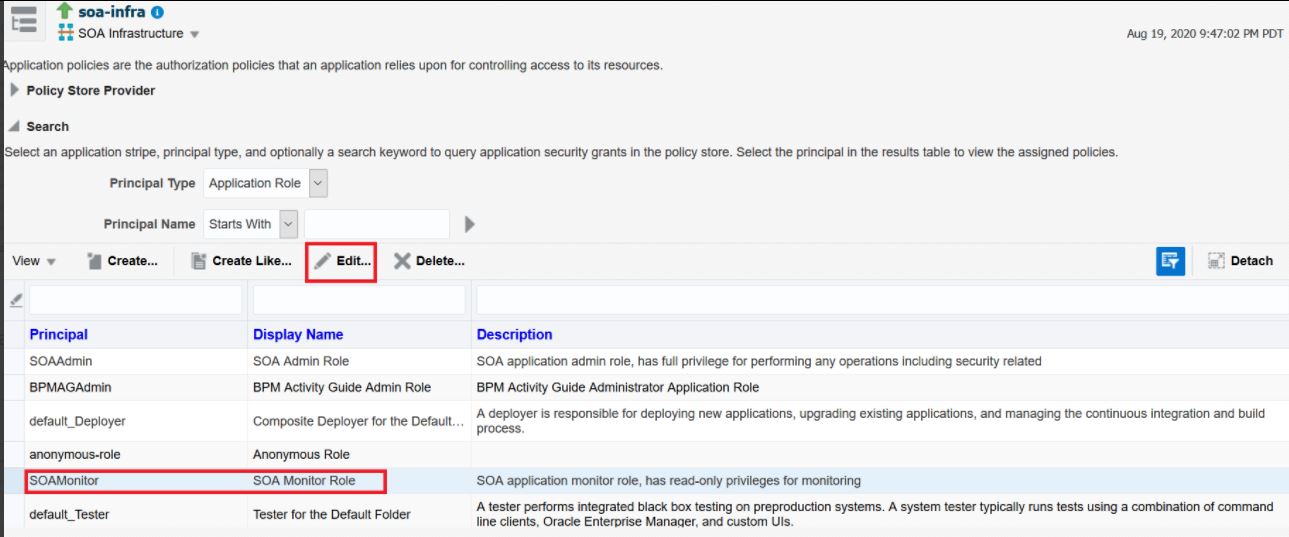
- In the Edit Application Grant page, click Edit
and edit the permissions as required.
The following table lists the permissions for the default roles in Oracle Enterprise Manager. Note that these roles can be altered or new roles can be created with required permissions.
Role CompositePermission SOAPlatformPermission InstancePermission SOAMonitorread, read-alerts on all folders/partitions read monitor, read-payload SOAOperatorread, write, provision, lifecycle, read-alerts, manage-alerts read, write-shared-data, read-shared-data change-state, monitor, manage-fault, read-payload, test SOADesignerread, write, provision read, write-shared-data, read-shared-data N/A SOAAdminAll All All where
- CompositePermission represents permissions to invoke an
operation on composites. Permissions include:
- read - read-only actions, including:
- view composite configuration
- get default version
- get composite metadata (export_composite, export_updates, and so on)
- list deployed composites for a partition
-
write - actions resulting in modifications of composites,
including:
- import updates
- provision - actions resulting in composite
provisions, including:
- deploy
- undeploy
- delete a SOA partition, removing all composites for that partition as a result
- lifecycle - actions resulting in composite
lifecycle state changes, including:
- start
- stop
- activate
- retire
- assign default version
- read-alerts - read all forms of alerts/notifications on configuration actions
- manage-alerts - manage all forms of alerts/notifications on configuration actions
- read - read-only actions, including:
- SOAPlatformPermission represents access to configuration
operations on SOA server, including viewing and updating the server URL,
logging, auditing, and so on. Permissions include:
- read - view SOA server configuration.
- write - modify SOA server configuration.
- write-shared-data - deploy/remove shared composite resources.
- read-shared-data - export shared composite resources.
- InstancePermission represents permissions to invoke SOA
runt ime operations such as audit trails and fault recovery. Permissions
include:
-
monitor - read access to composite instances, including
actions such as
getNumberOfFaults,getNumberOfCompositeInstances,getNumberOfFaultInstances,getCompositeInstances,getComponentSnapshot,getAuditFlow,getSensorData, and so on. - read-payload - along with monitor permission, provides additional ability to view the payload of the run time instances.
-
change-state - access to instance state change actions
including:
- suspend a flow
- resume a flow
-
manage-fault - access to fault management actions
including:
- recover a fault
- abort instances
- delete - ability to delete or purge composite instances and delete rejected messages.
- modify-payload - along with change-state, provides additional ability to modify payload.
- migrate - access to composite migration actions.
- test - access to composite test methods.
-
monitor - read access to composite instances, including
actions such as
- CompositePermission represents permissions to invoke an
operation on composites. Permissions include:
- Click OK.
The following examples show permissions required to access certain functionality in Oracle Enterprise Manager Fusion Middleware Control.
| Functionality | Permissions Required |
|---|---|
| Access Flow Instance tab |
|
| Start/stop/activate/retire a composite |
|
| Deploy/undeploy/redeploy composite |
|
| Terminate/recover an instance |
|
| Delete a flow instance | oracle.fabric.permission.InstancePermission with
delete and monitor permissions
|
Assigning SOA Folder Roles to a User
For information about managing SOA folders, see Managing SOA Folders.
Note:
All folders are automatically secured with application roles and folder roles.To assign a SOA folder role to a user:
- Log in to Oracle Enterprise Manager Fusion Middleware Control as an Administrator.
- From the SOA Infrastructure menu, select
Security, then Application
Roles.

- In the list, select the required role that you want to assign to the
user and click Edit.
Folder-based roles are named using the convention
folder-name_folder-role. For example, some of the roles available for foldertestmay be as shown here: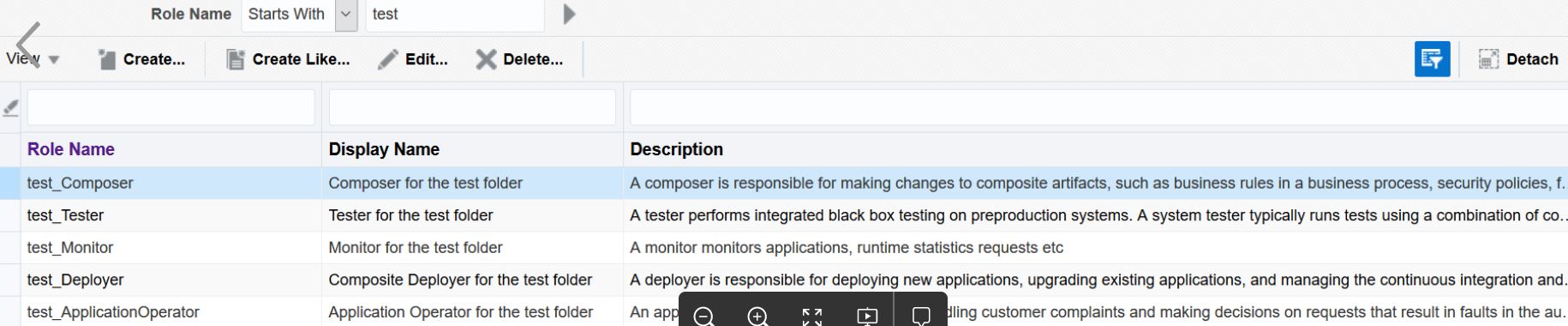
- In the Edit Application Role page, click Add.
- In the Add Principal dialog, from the Type list, select User.
- In the Principal Name list, select the user and click
OK.
The selected user is granted the permissions associated with the selected folder role.