Deploy a Secure Landing Zone That Meets the CIS Foundations Benchmark for Oracle Cloud
Architecture
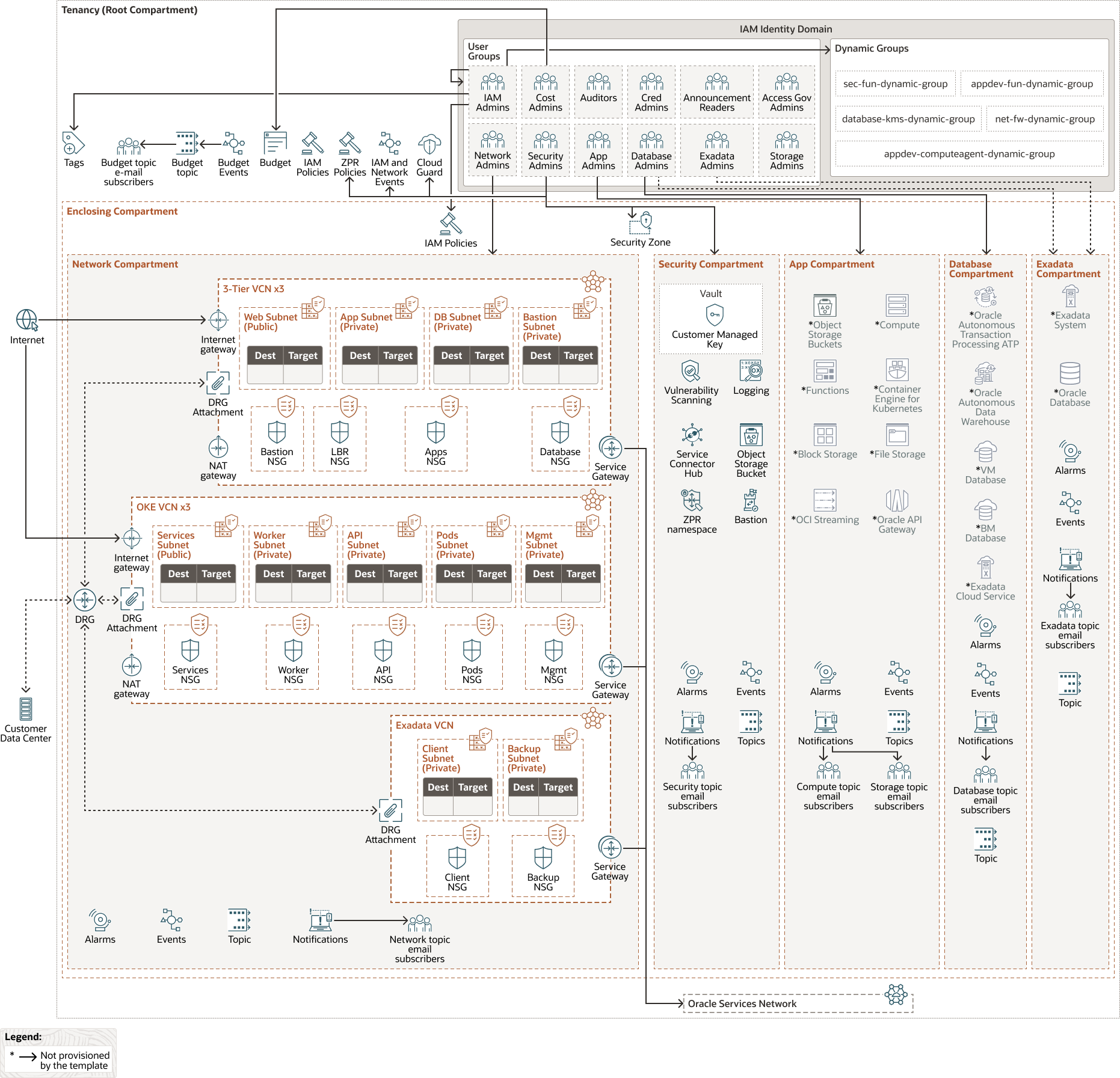
OCI Core Landing Zone has the ability to provision multiple VCNs, either in standalone mode or as constituent parts of a hub-and-spoke architecture, or connected through a DMZ VCN. The VCNs can either follow a general-purpose, three-tier network topology or be oriented toward specific topologies for supporting OCI Kubernetes Engine (OKE) or Oracle Exadata Database Service deployments. They are configured out-of-the-box with the necessary routing, with their inbound and outbound interfaces properly secured.
The landing zone includes various pre-configured security services that can be deployed in tandem with the overall architecture for a strong security posture. These services are Oracle Cloud Guard, VCN flow logs, OCI Connector Hub, OCI Vault with customer-managed keys, OCI Vulnerability Scanning Service, Security Zones, and Zero Trust Packet Routing (ZPR). Notifications are set using Topics and Events for alerting administrators about changes in the deployed resources.
The following diagram illustrates this reference architecture.
oci-core-landingzone-oracle.zip
The architecture has the following components:
- Tenancy
A tenancy is a secure and isolated partition that Oracle sets up within Oracle Cloud when you sign up for Oracle Cloud Infrastructure. You can create, organize, and administer your resources in Oracle Cloud within your tenancy. A tenancy is synonymous with a company or organization. Usually, a company will have a single tenancy and reflect its organizational structure within that tenancy. A single tenancy is usually associated with a single subscription, and a single subscription usually only has one tenancy.
- Identity domain
An identity domain is a container for managing users and roles, federating and provisioning users, securing application integration through single sign-on (SSO) configuration, and SAML/OAuth-based identity provider administration. It represents a user population in Oracle Cloud Infrastructure and its associated configurations and security settings (such as MFA).
- Policies
An Oracle Cloud Infrastructure Identity and Access Management policy specifies who can access which resources, and how. Access is granted at the group and compartment level, which means you can write a policy that gives a group a specific type of access within a specific compartment, or to the tenancy.
- Compartments
Compartments are cross-regional logical partitions within an Oracle Cloud Infrastructure tenancy. Use compartments to organize, control access, and set usage quotas for your Oracle Cloud resources. In a given compartment, you define policies that control access and set privileges for resources.
The resources in this landing zone template are provisioned in the following compartments:- A recommended enclosing compartment containing all compartments listed below.
- A Network compartment for all the networking resources, including the required network gateways.
- A Security compartment for the logging, key management, and notifications resources.
- An App compartment for the application-related services, including compute, storage, functions, streams, Kubernetes nodes, API gateway, and so on.
- A Database compartment for all database resources.
- An optional compartment for Oracle Exadata Database Service infrastructure.
The grayed out icons in the diagram indicate services that are not provisioned by the template.
This compartment design reflects a basic functional structure observed across different organizations, where IT responsibilities are typically separated among networking, security, application development, and database administrators.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
The template can deploy VCNs for different workload types, including three-tier VCNs for typical three-tier web-based applications, OCI Kubernetes Engine applications and Oracle Exadata Database Service.
- Internet gateway
An internet gateway allows traffic between the public subnets in a VCN and the public internet.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between on-premises networks and VCNs and can also be used to route traffic between VCNs in the same region or across regions.
- NAT gateway
A NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Service gateway
The service gateway provides access from a VCN to other services, such as Oracle Cloud Infrastructure Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and does not traverse the internet.
- Oracle services network
The Oracle Services Network (OSN) is a conceptual network in Oracle Cloud Infrastructure that is reserved for Oracle services. These services have public IP addresses that you can reach over the internet. Hosts outside Oracle Cloud can access the OSN privately by using Oracle Cloud Infrastructure FastConnect or VPN Connect. Hosts in your VCNs can access the OSN privately through a service gateway.
- Network security groups (NSGs)
NSGs act as virtual firewalls for your cloud resources. With the zero-trust security model of Oracle Cloud Infrastructure you control the network traffic inside a VCN. An NSG consists of a set of ingress and egress security rules that apply to only a specified set of VNICs in a single VCN.
- Events
Oracle Cloud Infrastructure services emit events, which are structured messages that describe the changes in resources. Events are emitted for create, read, update, or delete (CRUD) operations, resource lifecycle state changes, and system events that affect cloud resources.
- Notifications
OCI Notifications broadcasts messages to distributed components by using a low latency publish-subscribe pattern, delivering secure, highly reliable, durable messages for applications hosted on Oracle Cloud Infrastructure.
- Vault
Oracle Cloud Infrastructure Vault enables you to centrally manage the encryption keys that protect your data and the secret credentials that you use to secure access to your resources in the cloud. You can use the Vault service to create and manage vaults, keys, and secrets.
- LogsOracle Cloud Infrastructure Logging is a highly-scalable and fully-managed service that provides access to the following types of logs from your resources in the cloud:
- Audit logs: Logs related to events produced by OCI Audit.
- Service logs: Logs published by individual services such as OCI API Gateway, OCI Events, OCI Functions, OCI Load Balancing, OCI Object Storage, and VCN flow logs.
- Custom logs: Logs that contain diagnostic information from custom applications, other cloud providers, or an on-premises environment.
- Service connectors
Oracle Cloud Infrastructure Connector Hub is a cloud message bus platform that orchestrates data movement between services in OCI. You can use service connectors to move data from a source service to a target service. Service connectors also enable you to optionally specify a task (such as a function) to perform on the data before it is delivered to the target service.
You can use Oracle Cloud Infrastructure Service Connector Hub to quickly build a logging aggregation framework for SIEM systems.
- Cloud Guard
Oracle Cloud Guard helps you achieve and maintain a strong security posture in Oracle Cloud by monitoring the tenancy for configuration settings and actions on resources that could pose a security problem.
You can use Oracle Cloud Guard to monitor and maintain the security of your resources in Oracle Cloud Infrastructure. Cloud Guard uses detector recipes that you can define to examine your resources for security weaknesses and to monitor operators and users for certain risky activities. When any misconfiguration or insecure activity is detected, Cloud Guard recommends corrective actions and assists with taking those actions, based on responder recipes that you can define.
- Security zone
A security zone is associated with one or more compartments and a security zone recipe. When you create and update resources in a security zone, Oracle Cloud Infrastructure (OCI) validates these operations against the list of policies that are defined in the security zone recipe. If any security zone policy is violated, then the operation is denied.
Security zones ensure that your OCI resources comply with your security policies, including Oracle Cloud Infrastructure Compute, Oracle Cloud Infrastructure Networking, Oracle Cloud Infrastructure Object Storage, Oracle Cloud Infrastructure Block Volumes, and Database resources.
- Vulnerability Scanning Service
Oracle Cloud Infrastructure Vulnerability Scanning Service helps improve the security posture in Oracle Cloud by routinely checking ports and hosts for potential vulnerabilities. The service generates reports with metrics and details about these vulnerabilities.
- Zero Trust Packet Routing
Oracle Cloud Infrastructure Zero Trust Packet Routing (ZPR) prevents unauthorized data access by managing the network security policy separately from the network architecture. ZPR uses a user-friendly, intent-based policy language to define allowed access pathways for data. Any traffic patterns not explicitly defined by policy cannot traverse the network, which simplifies data protection and prevents data exfiltration.
- Bastion service
Oracle Cloud Infrastructure Bastion service provides restricted access from specific IP addresses to target OCI resources that do not have public endpoints using Identity-based, audited and time-bound Secure Shell (SSH) sessions.
- Object Storage
OCI Object Storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. You can safely and securely store data directly from the internet or from within the cloud platform. You can scale storage without experiencing any degradation in performance or service reliability.
Recommendations
Use the following recommendations as a starting point to design and configure security for your cloud environment. Your requirements might differ from the architecture described here.
- Network configuration
For the VCNs, select CIDR blocks that do not overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
- Monitoring security
Use Oracle Cloud Guard to monitor and maintain the security of your resources in Oracle Cloud Infrastructure. Cloud Guard uses detector recipes that you can define to examine your resources for security weaknesses and to monitor operators and users for risky activities. When any misconfiguration or insecure activity is detected, Cloud Guard recommends corrective actions and assists with taking those actions, based on responder recipes that you can define.
- Secure resource provisioning
For resources that require maximum security, use security zones. A security zone is a compartment associated with an Oracle-defined recipe of security policies that are based on best practices. For example, the resources in a security zone must not be accessible from the public internet and they must be encrypted using customer-managed keys. When you create and update resources in a security zone, Oracle Cloud Infrastructure validates the operations against the policies in the security-zone recipe, and denies operations that violate any of the policies.
Considerations
When implementing this reference architecture, consider the following factors:
- Access permissions
The landing zone template provisioning requires a user with tenancy-wide permissions (any user that is a member of the Administrators group).
The landing zone template provisions resources as the tenancy administrator (any user that is a member of the Administrators group), and it includes policies to allow separate administrator groups to manage each compartment after the initial provisioning. The pre-configured policies do not cover all possible resources available in OCI (for example, if you add resources to the Terraform template, you may have to add the required additional policy statements).
- Network Configuration
The landing zone network can be deployed in different ways: with one or multiple standalone VCNs in a hub-and-spoke architecture with Oracle Cloud Infrastructure DRG V2 service, or with a DMZ VCN architecture with Oracle Cloud Infrastructure DRG V2. It is also possible to configure the network with no internet connectivity. Although the landing zone allows for switching back and forth between standalone and hub-and-spoke, it is important to plan for a specific design, as manual actions might be needed when switching.
- Deployment Guide
The OCI Core Landing Zone Deployment Guide in GitHub provides detailed guidance on how to configure the Core landing zone, including some key deployment scenarios.
Deploy
The Terraform code for this solution is available in GitHub. You can pull the code into Oracle Cloud Infrastructure Resource Manager with a single click, create the stack, and deploy it. Alternatively, download the code from GitHub to your computer, customize the code, and deploy the architecture by using the Terraform CLI.
- Deploy using the sample stack in Oracle Cloud Infrastructure Resource
Manager:
- Go to

If you aren't already signed in, enter the tenancy and user credentials.
- Select the region where you want to deploy the stack.
- Follow the on-screen prompts and instructions to create the stack.
- After creating the stack, click Terraform Actions, and select Plan.
- Wait for the job to be completed, and review the plan.
To make any changes, return to the Stack Details page, click Edit Stack, and make the required changes. Then, run the Plan action again.
- If no further changes are necessary, return to the Stack Details page, click Terraform Actions, and select Apply.
- Go to
- Deploy using the Terraform code in GitHub:
- Go to GitHub.
- Download or clone the code to your local computer.
- Follow the instructions in the README.
Change Log
This log lists significant changes:
| February 20, 2025 |
|
| May 16, 2024 |
|
| May 2, 2023 |
|
| October 19, 2021 |
|