Configure File Storage for Microsoft Windows Active Directory Users
You can integrate Oracle Cloud Infrastructure (OCI) File Storage with Microsoft Windows Active Directory to authenticate and authorize Windows users.
Applications running on Windows servers often need to access shared storage concurrently to support high availability and distributed processing architecture. Windows users also need shared storage to collaborate with other users. In some cases, it is necessary to share data between Linux and Windows systems.
- Re-export the OCI File Storage file system using SAMBA on another compute instance
- Build a separate infrastructure for Windows file sharing
Windows operating systems starting with Windows 7 and Windows server 2008 have Network File System (NFS) support with NFS client enabled by default in later versions.
Before You Begin
This solution playbook assumes that you have an Active Directory environment and you have access to a domain controller with Remote Desktop Protocol (RDP). You can configure authentication alone (Kerberos), LDAP alone (authorization alone), or both together.
Architecture
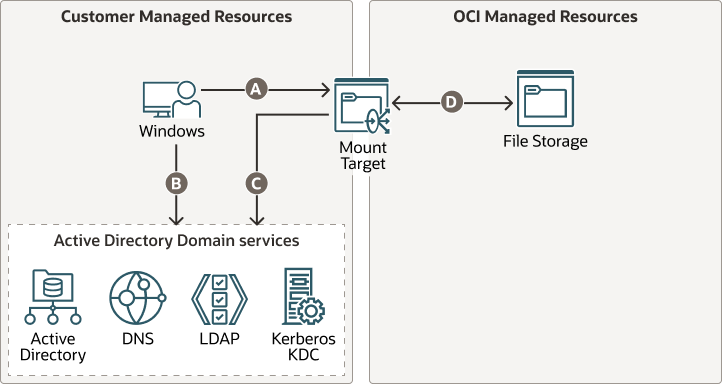
This architecture shows Microsoft Windows and services on a customer-managed data center and how they interact with the mount target and Oracle Cloud Infrastructure File Storage located on Oracle Cloud Infrastructure (OCI).
An OCI File Storage service file sharing environment requires network connectivity to LDAP server and integration with your Kerberos, LDAP, and DNS infrastructure.
Description of the illustration file-storage-windows-ad.png
file-storage-windows-ad-oracle.zip
- A: NFS client communication with mount target through TCP port 2048, 2049, and 2050.
- B: NFS Client talks to DNS through TCP and UDP port 53, LDAP over port 389 or LDAPS over port 636. Kerberos over TCP and UDP port 88.
- C: Mount target communication to DNS through TCP and UDP port 53, and LDAP over TCP port 636. Mount target requires LDAP server to have a proper certificate by a proper certificate authority. Self signed certificates are not accepted
- D: Internal communication between mount target and file system within OCI File Storage service (Oracle Managed infrastructure).
This architecture supports the following components on a customer-managed data center:
- DNS server
Enables the mount target and other systems to look up host names, including the LDAP server. DNS server is a customer-managed entity that sits outside of OCI File Storage service. The DNS server can be located in the same VCN as the mount target, a different VCN in the same region or another region, or on-premise. DNS service requires TCP and UDP port 53 open on firewall.
- LDAP
LDAP is the directory service where mount targets and other systems get attributes for the users and groups. Similar to DNS server, this is a customer managed entity and can be located anywhere with connectivity to port 636 (LDAPS). Active Directory uses LDAP for directory services and mount target uses this LDAP services for user authorization.
- Kerberos
Kerberos is an industry standard secure authentication protocol that facilitates authentication, data integrity, and in-transit encryption. Kerberos is part of Active Directory infrastructure and it is the standard authentication used by Windows users.
- Active Directory
Active Directory is a directory service for a Microsoft Windows domain. It enables centralized domain management and various directory based identity services. Domain controllers hosts Active Directory services to authenticate and authorizes all users and computers in Windows environment. It implements standard Kerberos protocol for authentication that mount target uses to authenticate and authorize Windows users. This is a customer managed entity similar to DNS that sits outside of OCI File Storage service.
This architecture supports the following components in OCI:
- Mount target
Mount target is a component of OCI File Storage. It sits in the customer VCN and provides an IP address for the clients to mount the file system.
- File storage
The Oracle Cloud Infrastructure File Storage service provides a durable, scalable, secure, enterprise-grade network file system. You can connect to a File Storage service file system from any bare metal, virtual machine, or container instance in a VCN. You can also access a file system from outside the VCN by using Oracle Cloud Infrastructure FastConnect and IPSec VPN.
Modes of Operation
With Kerberos and LDAP integration with File Storage Service, you can configure Windows file sharing in one of the following ways:
- Simple NFS access from Windows instances without authentication.
Mount File Storage from Windows instances without additional configuration on the mount target.
Windows users and application can access File Storage with a configured user ID and group ID in the Windows registry, no LDAP or Kerberos configuration is required for this mode of operation. For more information, see Mounting File Systems From Windows Instances.
- Authenticate users without authorization.
Configure Kerberos to authenticate users using Active Directory. All the authenticated users are then mapped to a single user id and group id using user squashing of the File Storage export. This user id and group id are used to authorize access to files and folder in File Storage. This mode of operation can simplify the configuration if only in-transit encryption is required. See "Configure the Mount Target for Kerberos" and "Configure Users and Groups with NFS Export".
- Authorize users without authentication.
Integrate Windows NFS client with Active Directory and use uidNumber and gidNumber configured in Active Directory.
LDAP configuration on the mount target is not mandatory for this mode of operation. However, if additional group membership for the user should be considered for authorization, LDAP configuration is required on the mount target. See "Integrate Windows NFS client with Active Directory" and "LDAP configuration".
- Authenticate and authorize users with Active Directory.
Configure both Kerberos and LDAP on mount target to achieve both authentication and authorization. As with other modes, the permission checks (authorization) are done based on Unix permissions (
uid,gid, and others). See "Configure the Mount Target for Kerberos", "LDAP configuration", and "Unix Permission in Windows".
About Kerberos, LDAP, and Windows Active Directory
You can integrate Kerberos and Lightweight Directory Access Protocol (LDAP) with Oracle Cloud Infrastructure File Storage for secure centralized authentication and authorization. Active Directory authentication for Windows users relies on File Storage Kerberos and LDAP feature.
The following are some of the benefits of integrating Kerberos and LDAP:
- Centralized Management: Organize users and enable tailored access rights with your Windows Active Directory Kerberos and LDAP identity management system.
- Security Compliance: Address security compliance requirements with the following
modes of operations:
- krb5: Kerberos authentication and authorization.
- krb5i: Integrity to protect against man-in-the-middle attacks and unauthorized modification.
- krb5p: Privacy or confidentiality to prevent eavesdropping (in-transit encryption).
- Scale Users with more groups: Increase the maximum number of secondary Unix groups OCI File Storage supports for authorization to 256 (from 16).
- Integrate with Microsoft Windows Active Directory: Access OCI File Storage NFS shares from Active Directory joined Microsoft Windows workstations and have Unix permissions for Active Directory Users (based on user, group, and others).
Summary of benefits using Active Directory integration in a Microsoft Windows environment:
- File Storage access from Microsoft Windows, universal access across Linux and Windows, and permissions based on Unix (user id, group id and others).
- User authentication with Active Directory.
- Avoid using Samba on a compute instance to re-export OCI File Storage with Server Message Block (SMB) protocol for Microsoft Windows access.
- Use Active Directory and LDAP for centralized user management.
- Enable in-transit encryption with Kerberos.
Limitations of NFS Access from Windows
Consider the following limitations of accessing NFS from Microsoft Windows:
- NFS protocol is not the default and native file sharing protocol in Windows. Performance observed from individual instances may be slower compared to SMB. If there is a difference in performance, then it is from an NFS client perspective with no effect on performance offered from the Oracle Cloud Infrastructure File Storage service.
- Restricted to Unix permissions with no access control list (ACL) support.
- Limited international characters support (no Unicode). See mount command for limited international character set support.
About Required Products, Services, and Roles
This solution requires the following products and services:
- Oracle Cloud Infrastructure (OCI)
- OCI File Storage
- Active Directory
- LDAP
These are the roles needed for each product and service.
| Product or Service Name: Permissions | Required to... |
|---|---|
| Oracle Cloud Infrastructure: Permissions in the compartment. If permissions are segregated into different roles, then contact the appropriate administrators to perform the task. |
|
| Active Directory: Write permissions to the Active Directory | Create users, add user attributes, and create computer accounts. |
| LDAP: Active Directory user with LDAP DN and password |
Configure LDAP on mount targets. The mount target requires a user with minimum read-only permissions to read users, group, and related attributes using LDAP. |
See Oracle Products, Solutions, and Services to get what you need.