Understand the Integration
After you finish the integration, the authentication flow for on-premises applications using Oracle Access Management (OAM) remains the same. For cloud applications, the authentication flow changes from an Oracle Identity Cloud Service only flow to one using a SAML assertion from OAM.
Configuring OAM to act as an identity provider (IdP) for your Oracle Identity Cloud Service does not affect how users access your on-premises applications. Users that access an OAM protected on-premises application are challenged with the appropriate authentication scheme, such as a form login. OAM validates the user credentials, generates the user session and allows access to the on-premises application.
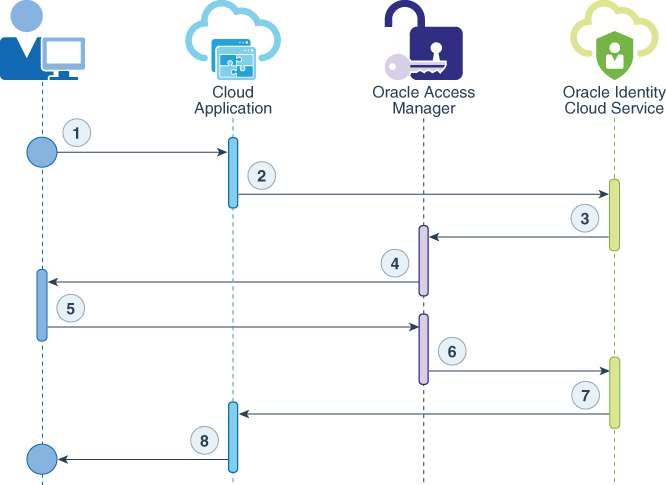
The following diagram explains the SAML 2.0 authentication flow for your cloud applications when using OAM as an IdP for Oracle Identity Cloud Service.
- The user requests access to a cloud application.
- The cloud application redirects the user browser to Oracle Identity Cloud Service for authentication.
- Oracle Identity Cloud Service redirects the user browser to OAM as the identity provider (IdP) for authentication.
- OAM presents its sign in page to the user.
- User submits credentials to OAM.
- After the user successfully authenticates in OAM, the browser is redirected to Oracle Identity Cloud Service with a valid SAML Token.
- Oracle Identity Cloud Service consumes the SAML token, creates a user session, and then redirects the browser back to the cloud application.
- The cloud application creates its own user session and then presents the home page to the user.
Validate the Prerequisites
Validate the following prerequisites before integrating Oracle Access Management (OAM) and Oracle Identity Cloud Service.
- Confirm that users are synchronized between OAM's identity store and Oracle Identity Cloud Service.
The IdP integration requires that user entries with the same unique attribute exist in both the OAM identity store and Oracle Identity Cloud Service. A commonly used unique attribute is email address. Oracle Identity Cloud Service offers mechanisms that continuously and automatically synchronize users.
You have the following options available to synchronize users between your existing OAM identity store and Oracle Identity Cloud Service:- REST APIs
- CSV files
- OIM connector
- Identity Bridge
As an example, using Oracle Unified Directory (OUD) for the OAM Identity Store, you can very simply check user entries. To check an individual user's email address in OUD, you can use ldapsearch. To retrieve a user in OUD, launch a terminal and run the ldapsearch command as follows, replacing the attributes and values according to your environment:
ldapsearch -h oudhost -p 1389 -D "cn=Directory Manager" -s sub -b "dc=example,dc=com" "uid=csaladna" dn mailThe command output will return the user DN and email as follows:
dn: uid=csaladna,ou=People,dc=example,dc=com mail: csaladna@example.comRecord the email returned from OUD (for example: csaladna@example.com):
- Access the Oracle Identity Cloud Service console,expand the Navigation Drawer , and click Users.
- Search and confirm that a user with the OUD email exists.
- If users are not both in OAM's user directory and Oracle Identity Cloud Service with matching unique attributes, you cannot continue.
You must first ensure that all users that will use the OAM IdP service have matching unique attributes in both directories.
- Verify that the OAM Identity Federation is enabled.
- Login to the OAM console and navigate to Configuration > Available Services.
- Confirm that Identity Federation is enabled. (Enable it if it's disabled).