About Setting up the Federation Between Identity Cloud Service and Access Manager
By using Oracle Access Management (OAM) to provide single sign-on (SSO) for your on-premises applications, you can also incorporate any Oracle Identity Cloud Service protected application.
Your existing on-premises access management system provides your users with single sign-on to your on-premises enterprise applications. Adding cloud based applications to your enterprise introduces the challenges of managing another user directory with associated user passwords.
When you use Oracle Identity Cloud Service for your cloud based single sign-on solution, you also have the option of adding external identity providers. Configuring your OAM environment as an identity provider (IdP) for Oracle Identity Cloud Service provides your users with a single place to manage passwords.
By configuring OAM to act as an IdP, Oracle Identity Cloud Service is federated with OAM. The federation agreement is that when a user tries to access an application protected by Oracle Identity Cloud Service, the authentication is outsourced to OAM. The federation agreement designates OAM as a trusted relying partner.
Oracle Identity Cloud Service provides out-of-the-box integration with SAML 2.0 compliant IdPs.
The Oracle Identity Cloud Service SAML 2.0 IdP feature:
- Works with federated SSO solutions that are compatible with SAML 2.0, such as Oracle Access Management.
- Allows users to log into Oracle Identity Cloud Service using their credentials from the IdP.
- Can force the IdP authentication for all users or offer the IdP authentication as a Login Chooser option.
Establishing SSO between your on-premises OAM system and Oracle Identity Cloud Service is an important step in the migration to the cloud. Federating Oracle Identity Cloud Service with OAM makes the migration process transparent to your users because you don't need to change the login screen or the authentication flow for the users.
Architecture
Your on-premises Oracle Access Management implementation is the authoritative source of login credentials. Configuring a SAML 2.0 federation allows you to continue to leverage credentials from Oracle Access Management in Oracle Identity Cloud Service.
The second stage in the roadmap to migrate your environment from an on-premises access management system to Oracle Identity Cloud Service is to establish federated single sign-on.
The following diagram highlights the major architectural components of this stage:
Figure - Oracle Access Manager as IdP for Oracle Identity Cloud Service
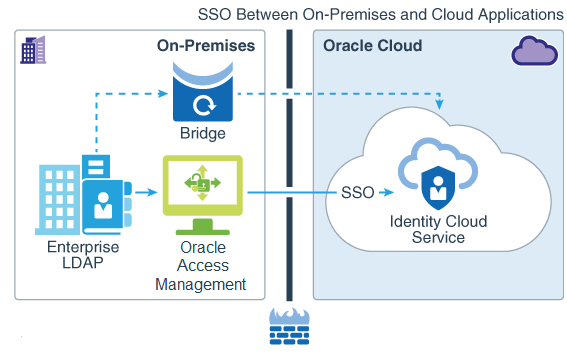
Description of "Figure - Oracle Access Manager as IdP for Oracle Identity Cloud Service"
In this architectural diagram, the on-premises access management system represents the legacy authentication mechanism, and Oracle Identity Cloud Service represents the cloud-based one. The corporate user trusted source is represented by an enterprise Lightweight Directory Access Protocol (LDAP) server. Users from the enterprise LDAP server are synchronized to Oracle Identity Cloud Service by the bridge.
Before You Begin
The following are considerations for federating Oracle Identity Cloud Service with Oracle Access Management (OAM).
If you plan to migrate your OAM environment to Oracle Identity Cloud Service you can follow a migration roadmap to integrate your on-premises applications with Oracle Identity Cloud Service so that these applications utilize the same Single Sign-On (SSO) as your cloud applications. To learn about this roadmap, see Learn about migrating from on-premises access management to Oracle Identity Cloud Service.
To federate Oracle Identity Cloud Service with Oracle Access Management, you need:
- Access to Oracle Identity Cloud Service with authorization to manage Identity Providers.
- An OAM environment with federation services enabled.
- Users synchronized between the OAM Identity Store and Oracle Identity Cloud Service. This can be accomplished with either the Microsoft Active Directory Bridge or a Provisioning Bridge.
- A shared unique attribute, such as email address, must be present and populated in both Oracle Identity Cloud Service and the directory for OAM.
- Synchronized server clocks where each service runs. The SAML assertion must be processed within it's valid time window.
- To maintain the existing process to manage user passwords in OAM, the authoritative source for login credentials.
About Required Services and Roles
This solution requires the following services:
- Oracle Identity Cloud Service
- Oracle Access Management
These are the roles needed for each service.
| Service Name: Role | Required to... |
|---|---|
Oracle Identity Cloud Service: Security Administrator |
Manage identity providers. |
Oracle Access Management: System
Administrator |
Access the Oracle Access Management console and change federation settings. |
See Oracle Products, Solutions, and Services to get what you need.