Connect Your On-Premises Network Using VPN
An Oracle Cloud Infrastructure virtual cloud network (VCN) is a virtualized Layer 3 version of a traditional network that gives you control of the private IP addresses, subnets, routers, and firewalls. A single tenancy can have multiple VCNs, segregated or combined.
You can make a VCN an extension of your on-premises network by using a virtual private network (VPN) connection. For this purpose, Oracle Cloud Infrastructure provides VPN Connect, which is an IPSec VPN.
-
You can use public internet lines when leased lines are not required.
-
The IP addresses spaces involved are private and not exposed to the external world.
-
The communication between networks is encrypted.
-
A site-to-site VPN allows multiple users to access the cloud resources through a single connection instead of multiple connections, reducing the management overhead.
Architecture
This reference architecture shows how to set up VPC Connect to connect your on-premises network and VCN.
The following diagram illustrates this architecture.
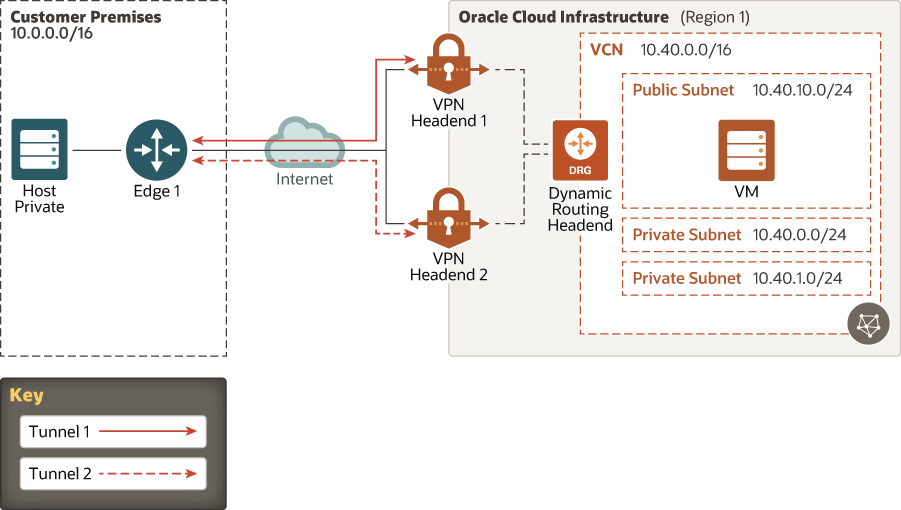
Description of the illustration vpn-redundancy.eps
- On-premises network
The local network used by your organization.
- VCN
A virtual, private network that you set up in Oracle data centers.
- Subnets
Subdivisions that you define within a VCN. A subnet has a contiguous range of IP addresses that don’t overlap with other subnets in the VCN.
- Security lists
Security rules that specify the source, destination, and type of traffic that are allowed in and out of a subnet.
- Route tables
Routing rules that provide mapping for traffic out of the VCN.
- Dynamic routing gateway (DRG)
A virtual router that you can add to your VCN to provide a path for private network traffic between your VCN and on-premises network (transit routing).
- VPN Connect
Function that manages IPSec VPN connections to your tenancy.
- Customer-premises equipment (CPE)
An object that represents the network asset that lives in the on-premises network and establishes the VPN connection. Most border firewalls act as the CPE, but a separate device (like an appliance or a server) can be a CPE.
- IPv4 and IPv6
Address schemes used for the networks. IPv6 is supported only in US Government Cloud.
- Internet Protocol Security (IPSec)
A protocol suite that encrypts IP traffic before packets are transferred from the source to the destination.
- Tunnel
Each connection between the CPE and Oracle Cloud Infrastructure.
- Border Gateway Protocol (BGP) routing
Allows routes to be learned dynamically. The DRG dynamically learns the routes from your on-premises network. On the Oracle side, the DRG advertises the VCN's subnets.
- Static routing
When you create the VPN connection, you inform the existing networks on each side. Changes are not learned dynamically.
Recommendations
Your requirements might differ from the architecture described here. Use the following recommendations as a starting point.
- VCN
When you create the VCN, determine how many IP addresses your cloud resources in each subnet require. Using Classless Inter-Domain Routing (CIDR) notation, specify a subnet mask and a network address range large enough for the required IP addresses. Use an address space that falls within the standard private IP address blocks.
Choose an address range that doesn't overlap with your on-premises network, in case you need to set up a connection between the VCN and your on-premises network later.
After you create the VCN, you can't change the address range.
When you design the subnets, consider functionality and security requirements. All compute instances within the same tier or role should go into the same subnet, which can be a security boundary.
- Security lists
Use security lists to define ingress and egress rules that apply to the entire subnet.
In the CPE, define the right set of access permissions. Permissions might have a different name in the CPE, such as access list.
- CPE
Some CPEs have specific requirements for some features to work, like policy-based routing (on CheckPoint and Cisco ASA firewalls). Ensure that the CPE’s software version fulfills those requirements.
Considerations
- Cost
VCNs, subnets, DRGs, security lists, and route tables have no additional cost. The test virtual machine (VM) in the deployment is set to use the Free Tier shape. If you use the Free Tier instances, set the test VM as a regular shape instances.
- Security
The default security list has the SSH port open to 0.0.0.0/0. Adjust the security list to match only the hosts and networks that should have SSH access to your infrastructure.
This deployment places all components in the same compartment.
The deployed subnet is public to allow access to the test instance from the internet until the VPN is working. If the VMs don’t provide any public service, consider removing resources or even the whole public subnet.
- Scalability
Each tenancy has a limit of five DRGs.
Each region can have four VPN connections.
- Performance
Each connection can reach 250 Mbps.
The DRG maximum throughput is 10 Gbps.
Because VPN connections use public internet lines, external actors can affect the performance on those lines.
- Availability and redundancy
DRGs are redundant and fail over automatically.
Each connection can have multiple tunnels.
Consider using multiple internet links from different providers on production environments.
- Usability
This deployment gives you all the components shown in the diagram. You must inform the public IP address of the CPE.
The included VM demonstrates and tests basic connectivity.