CountryPlace Mortgage: Lending and Leasing Platform Deployment on Oracle Cloud
CountryPlace Mortgage migrated its chattel mortgage platform to Oracle Cloud Infrastructure (OCI) to help ensure availability, scalability, disaster recovery, regulatory compliance, and contractual reliability.
CountryPlace Mortgage is an American mortgage provider founded in 1995. CountryPlace differentiates itself in the marketplace by not only supporting mortgages for conventional property purchases but also by specializing in mortgages for modular-built homes. Modular homes are factory-built based on a chosen template and then assembled on the plot of prepared land, reducing construction time and cost. CountryPlace has a number of different mortgage options including one where the mortgage finances the modular home purchase but excludes the land on which it is built. This kind of loan is known as a chattel loan or mortgage. The COVID pandemic has changed people's attitudes to mortgages and property, and chattel loans now represent the largest part of the new loan business.
CountryPlace's chattel mortgage back-office operations use Oracle Financial Services Lending and Leasing (OFSLL). OFSLL is built on Oracle Database, Oracle WebLogic Server, and Oracle BI Publisher servers. CountryPlace faced several challenges that have become ever more critical as the business has grown:
- Hosting on-premises or through a managed data center limited the physical resilience options
- Lack of high availability meant that any downtime would stop the activities of 65 users
- Capacity was constrained so that running reporting functions made the system unusable
- Lack of disaster recovery increased business risk
- Software versions needed updating
- Regulatory compliance and business operations constrained the ability to make significant changes, and switch-over approaches required additional infrastructure
CountryPlace adopted OCI for several reasons including:
- The need for a cloud-based solution that supports the latest Oracle products and versions
- The ability to meet reliability SLAs for the mission-critical OFSLL application
- To achieve business continuity with the disaster-recovery environment
- To scale quickly and reduce the lead time to acquire new infrastructure and deploy more resources from weeks to hours or days
- The ability to satisfy these goals while meeting the business use case
Once the migration strategy, redesign, and plan were agreed upon, it took two people four months to perform the migration which included the following initiatives:
- Create the environments (both production and non-production)
- Build the legacy conversion scripts
- Migrate the application data
- Test the new configuration (set up Oracle Cloud Infrastructure Identity and Access Management and verify application configuration and failover processes)
- Train the users on the new products and environment
- Switch over to the OCI solution
This experience showed CountryPlace that Oracle Cloud is easy to work with and, as a result, CountryPlace has plans to bring additional workloads into their OCI environment.
Architecture
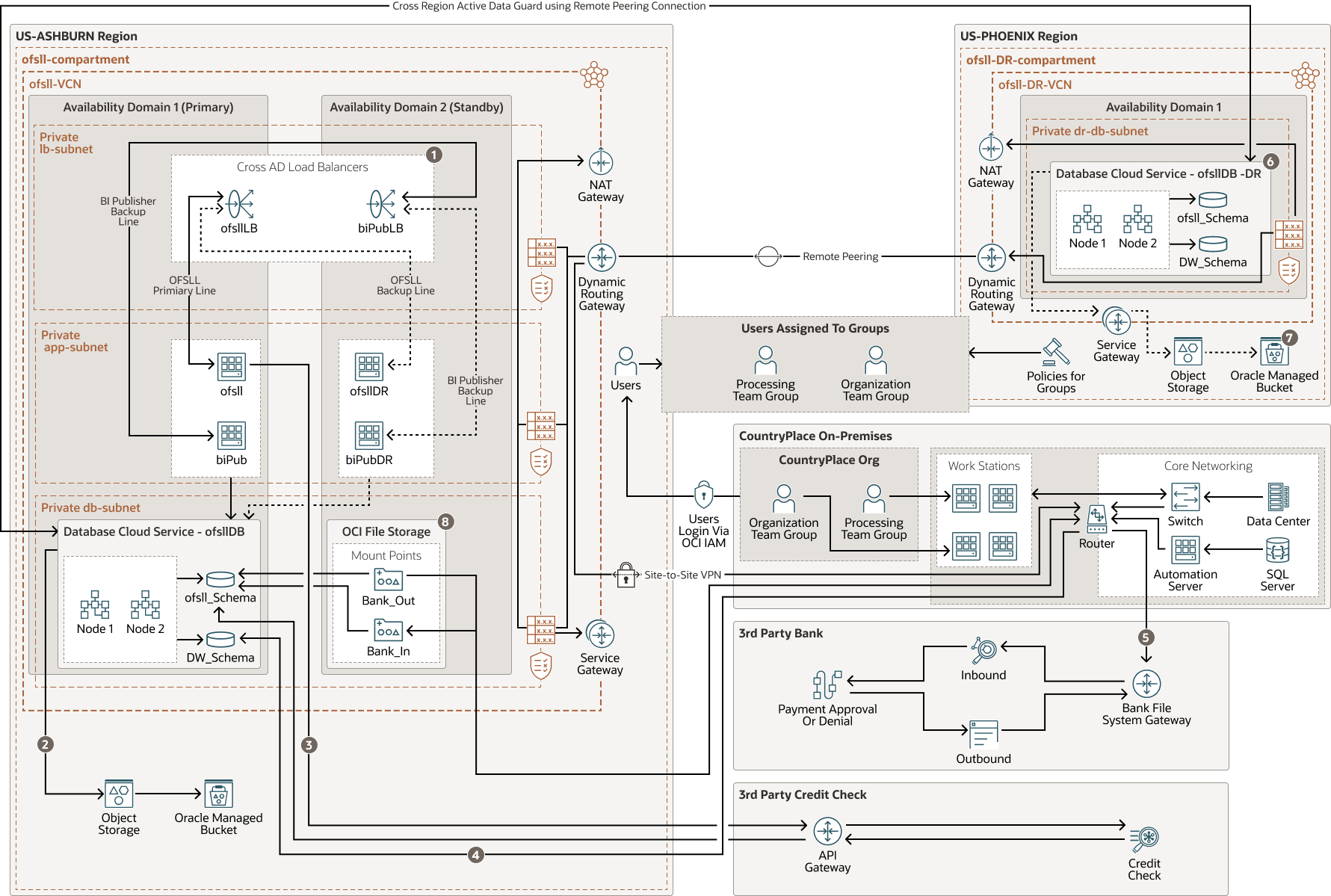
CountryPlace's new architecture not only hosts the latest versions of the products, but also addresses the need for resilience and reliable user access to the Oracle Financial Services Lending and Leasing (OFSLL) service.
On-premises environments connect to Oracle Cloud Infrastructure by using a site-to-site VPN tunnel. OFSLL user access is routed through the tunnel to load balancers which route traffic to the appropriate servers so that users interact solely with the load balancer.
The new OFSLL deployment is made up of one Oracle WebLogic Server for OCI server hosting the application layer in each availability domain and with two Oracle BI Publisher servers split across the availability domains. The servers within each availability domain are also split across fault domains for greater reliability. These components reside within their own subnet with networking rules to control access. The load balancers separate the Oracle WebLogic Server and Oracle BI Publisher traffic so that the resource-intensive tasks such as report generation don't impact the users' experience of the rest of the application.
The Oracle WebLogic Server and Oracle BI Publisher servers are connected to the database servers by using Real Application Cluster (RAC) nodes in a separate subnet within the same availability domain. Using RAC servers maximizes the availability of the database. Each availability domain has its own database servers that are synchronized by using Active Data Guard.
The load balancer is configured to keep the traffic within one availability domain and only reroutes the traffic in the event of an availability domain failure. This ensures that Active Data Guard traffic flows in a single direction at any one time, and that user traffic can't be directed to a recovering availability domain before data between the availability domains is again synchronized.
The Oracle database infrastructure is also used to provide data warehouse capabilities not only for data from OFSLL but also for data transferred in from external systems, such as SQL Server databases, using the IPsec tunnel connection. Report content is then generated from the data warehouse and made available by using Oracle BI Publisher.
In addition to the synchronization between the database instances, the data is regularly backed up to archive storage. These business critical backups are copied to a separate cloud region for increased redundancy. The Phoenix region also hosts an additional disaster recovery deployment of the system in a single availability domain. To allow the regions to remain aligned, the regions are connected through remote peering which allows Active Data Guard to send the data to the database in the Phoenix region along with a replication of the server VM images.
The OFSLL application must communicate with a third-party bank for payments and also with third-party credit check services. These application flows are routed through the on-premises infrastructure with secure file transfer technologies or with API calls initiated by OFSLL as is the case with credit services. A Samba file share handles the OFSLL reports and documents that need to be printed and sent to customers.
The following diagram illustrates this architecture.
countryplace-oci-arch-oracle.zip
The process flow includes the following steps:
- The load balancer will only failover to a disaster recovery app in availability domain 2 if apps in availability domain 1 are not responsive.
- Backups are performed by using the OCI console and are sent to an Oracle-managed bucket by using the service gateway.
- Credit checks are initiated from OFSLL and sent to the third-party credit service over the credit service's native API gateway, and results are stored in the database.
- After an SSIS ETL job is initiated from SQL server, the job loads data into the data warehouse schema.
- Transactions from the database are extracted by using SQL to the Bank_Out OCI file system mount point. The file is then pushed to the bank's file system gateway inbound folder. The bank processes the data and places the results in their outbound folder. CountryPlace retrieves the file and places it in the Bank_In internal mount point. The file results are then loaded into the database.
- The disaster recovery deployment of OFSLL apps communicates with the disaster recovery database if communication with the primary database is lost.
- Backups are taken from ofsllDB-DR if the primary database or backup mechanism fails.
- File storage is provided across the availability domains and is mounted to instances as required.
In addition to the production environment shown in the architecture diagram, there are several other environments that are smaller, but simpler in configuration. These include non-production development and test environments to validate any development or changes. CountryPlace has also adopted the practice of revalidating the architecture by rebuilding an environment from the ground up every month and then tearing it down.
Based on their experience of delivering a highly resilient solution, CountryPlace has identified a number of other areas within their IT infrastructure that need to be enhanced. They are working on proofs of concept (PoCs) for OCI to replace existing solutions such as the one for ingesting scanned documents that represent the contractual agreements with customers into OFSLL by using a third-party file imaging tool called Virpack.
The architecture has the following components:
- Tenancy
A tenancy is a secure and isolated partition that Oracle sets up within Oracle Cloud when you sign up for Oracle Cloud Infrastructure. You can create, organize, and administer your resources in Oracle Cloud within your tenancy. A tenancy is synonymous with a company or organization. Usually, a company will have a single tenancy and reflect its organizational structure within that tenancy. A single tenancy is usually associated with a single subscription, and a single subscription usually only has one tenancy.
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Identity and Access Management (IAM)
Oracle Cloud Infrastructure Identity and Access Management (IAM) is the access control plane for Oracle Cloud Infrastructure (OCI) and Oracle Cloud Applications. The IAM API and the user interface enable you to manage identity domains and the resources within the identity domain. Each OCI IAM identity domain represents a standalone identity and access management solution or a different user population.
- Audit
The Oracle Cloud Infrastructure Audit service automatically records calls to all supported Oracle Cloud Infrastructure public application programming interface (API) endpoints as log events. Currently, all services support logging by Oracle Cloud Infrastructure Audit.
- Compartment
Compartments are cross-region logical partitions within an Oracle Cloud Infrastructure tenancy. Use compartments to organize your resources in Oracle Cloud, control access to the resources, and set usage quotas. To control access to the resources in a given compartment, you define policies that specify who can access the resources and what actions they can perform.
- Availability domain
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domain
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Route table
Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways.
- Site-to-Site VPN
Site-to-Site VPN provides IPSec VPN connectivity between your on-premises network and VCNs in Oracle Cloud Infrastructure. The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
- Network address translation (NAT) gateway
A NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Service gateway
The service gateway provides access from a VCN to other services, such as Oracle Cloud Infrastructure Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and never traverses the internet.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between VCNs in the same region, between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- Remote peering
Remote peering allows the VCNs' resources to communicate using private IP addresses without routing the traffic over the internet or through your on-premises network. Remote peering eliminates the need for an internet gateway and public IP addresses for the instances that need to communicate with another VCN in a different region.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end.
- Compute
The Oracle Cloud Infrastructure Compute service enables you to provision and manage compute hosts in the cloud. You can launch compute instances with shapes that meet your resource requirements for CPU, memory, network bandwidth, and storage. After creating a compute instance, you can access it securely, restart it, attach and detach volumes, and terminate it when you no longer need it.
- Object storage
Object storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. You can safely and securely store and then retrieve data directly from the internet or from within the cloud platform. You can seamlessly scale storage without experiencing any degradation in performance or service reliability. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
- VM DB System
Oracle VM Database System is an Oracle Cloud Infrastructure (OCI) database service that enables you to build, scale, and manage full-featured Oracle databases on virtual machines. A VM database system uses OCI Block Volumes storage instead of local storage and can run Oracle Real Application Clusters (Oracle RAC) to improve availability.
- Data Guard
Oracle Data Guard provides a comprehensive set of services that create, maintain, manage, and monitor one or more standby databases to enable production Oracle databases to remain available without interruption. Oracle Data Guard maintains these standby databases as copies of the production database. Then, if the production database becomes unavailable because of a planned or an unplanned outage, Oracle Data Guard can switch any standby database to the production role, minimizing the downtime associated with the outage.
Get Featured in Built and Deployed
Want to show off what you built on Oracle Cloud Infrastructure? Care to share your lessons learned, best practices, and reference architectures with our global community of cloud architects? Let us help you get started.
- Download the template (PPTX)
Illustrate your own reference architecture by dragging and dropping the icons into the sample wireframe.
- Watch the architecture tutorial
Get step by step instructions on how to create a reference architecture.
- Submit your diagram
Send us an email with your diagram. Our cloud architects will review your diagram and contact you to discuss your architecture.
Explore More
Learn more about the features of this architecture.
- Best practices framework for Oracle Cloud Infrastructure
- Deploy Oracle WebLogic Server on compute instances
- Oracle Cloud Infrastructure documentation
- Data and Application Security Comparison
- Oracle Database Security
- Oracle Financial Services Lending and Leasing Platform on Oracle Cloud Infrastructure
- Oracle Cloud Cost Estimator