Connect Oracle Data Safe to Exadata and Autonomous Databases
This reference architecture highlights the different ways you can connect Exadata and Autonomous databases to Oracle Data Safe. It also describes the security measurements you need take to provide a safe deployment of a connection to a specific target database.
Oracle Data Safe is a fully-integrated, regional Cloud service focused on data security. It provides a complete and integrated set of features of the Oracle Cloud Infrastructure (OCI) for protecting sensitive and regulated data in Oracle databases.
Oracle Data Safe delivers essential security services for Oracle Autonomous Database and databases running in OCI. Data Safe also supports on-premises databases, Oracle Exadata Cloud@Customer, and multicloud deployments. All Oracle Database customers can reduce the risk of a data breach and simplify compliance by using Data Safe to assess configuration and user risk, monitor and audit user activity, and discover, classify, and mask sensitive data.
Compliance laws, such as the European Union (EU) General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), require companies to safeguard the privacy of their customers. Running a variety of hosted databases in a safe and efficient requires way to manage the security of this data. Oracle Data Safe helps you understand data sensitivity, evaluate risks to data, mask sensitive data, implement and monitor security controls, assess user security, monitor user activity, and address data security compliance requirements.
- Security parameters
- Security controls in use
- User roles and privileges
- Center for Internet Security (CIS) Configuration - available for Oracle Database 12.2 and later.
- Security Technical Implementation Guidelines (STIG) - available for Oracle Database 21c and later.
- EU GDPR - European Union General Data Protection Regulation
- PCI-DSS - The Payment Card Industry Data Security Standard, and
- HIPPA- Health Insurance Portability and Accountability Act
Data masking, also known as static data masking, is the process of permanently replacing sensitive data with fictitious realistic looking data.
Data Safe can discover and classify sensitive data based on a library of more than 150 predefined sensitive data types. This can also be extended with custom data types.
Architecture
- Exadata Database Service or Exadata Cloud@Customer / Regional Cloud@Customer / Dedicated Region
- Autonomous Databases
This reference architecture only discusses databases with private IP addresses. To configure a database with a public IP address is from a security perspective not advised.
- Well-architected framework for Oracle Cloud Infrastructure
- Deploy a secure landing zone that meets the CIS Foundations Benchmark for Oracle Cloud
- CIS Compliant OCI Landing Zones (GitHub repository)
Note:
Please refer to the Explore More topic below for access to these resources.Exadata Database Service or Exadata Cloud@Customer
Oracle Exadata Database Service provides the Oracle Exadata Database Machine as a service in an Oracle Cloud Infrastructure (OCI) data center.
Exadata Cloud@Customer, a managed service, provides an Exadata Database Service that is hosted in the on-premises data center.
Exadata Database Service
The Exadata Database Service does not need to connect to the on-premises network because it is deployed on OCI and can therefor use the Private end-point directly. After setting up the necessary connectivity, the databases can be configured as targets in Data Safe using the wizard.
Exadata Cloud@Customer
- On-premises connector
- Private end-point
In the following diagram, the connections are shown between the Oracle Cloud and the on-premises data center. The diagram shows the options to choose from. If there is a site-to-site VPN or OCI FastConnect connection you can use a private endpoint to connect to your Exadata Cloud@Customer target Data Safe databases. If there is no VPN or OCI FastConnect, then you can deploy an on-premises connector to connect to your Exadata Cloud@Customer target Data Safe databases. This on-premises connector will then connect to Data Safe via a TLS tunnel.
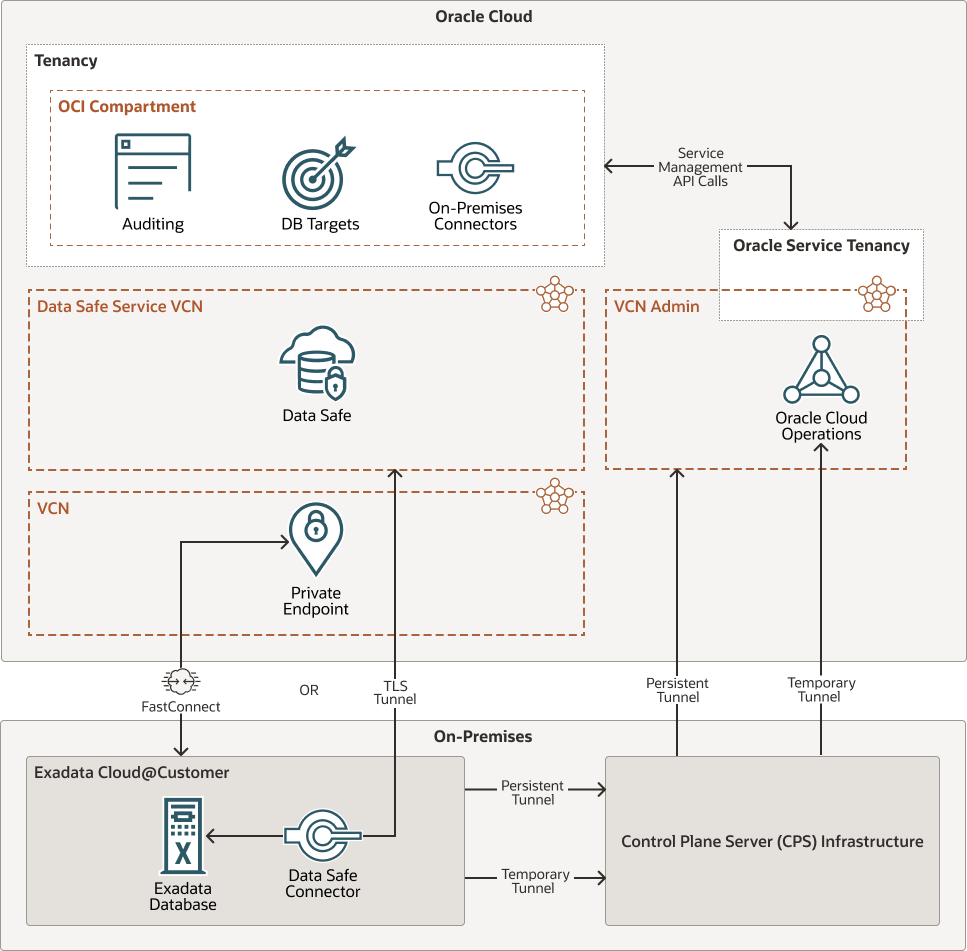
Description of the illustration data-safe-exa-adb.png
Be aware that as shown in the diagram, an outgoing, persistent, secure automation tunnel connects the CPS infrastructure in the on-premises data center to the Oracle-managed admin VCN in the OCI region for delivering cloud automation commands to the VM clusters. This is a outgoing tunnel for the CPS infrastructure and can not be used for Data Safe connections. For more information see the link below on 'Architecture Exadata Cloud@Customer'.
- Architecture Exadata Cloud@Customer
- Architecture Exadata Database Service
- Setup Cloud@Customer database using private endpoint
- Setup Cloud@Customer database using the wizard
- Simplify Security for your on-premises Oracle Databases with Oracle Data Safe
- Exadata Database Service Security Controls
Note:
Please refer to the Explore More topic below for access to these resources.Autonomous Databases
Autonomous database on shared infrastructure is available with Data Safe. Autonomous databases can be registered through the wizard or by a single click from the Autonomous database details page. The steps to connect the autonomous database for the Dedicated Region Cloud@Customer are discussed in this part of the Data Safe documentation.
Architecture Components
- Tenancy
Oracle Autonomous Transaction Processing is a self-driving, self-securing, self-repairing database service that is optimized for transaction processing workloads. You do not need to configure or manage any hardware, or install any software. Oracle Cloud Infrastructure handles creating the database, as well as backing up, patching, upgrading, and tuning the database.
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Compartment
Compartments are cross-region logical partitions within an Oracle Cloud Infrastructure tenancy. Use compartments to organize your resources in Oracle Cloud, control access to the resources, and set usage quotas. To control access to the resources in a given compartment, you define policies that specify who can access the resources and what actions they can perform.
- Availability domains
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domains
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end. The load balancer provides access to different applications.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- NAT gateway
The NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Service gateway
The service gateway provides access from a VCN to other services, such as Oracle Cloud Infrastructure Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and never traverses the internet.
- Cloud Guard
You can use Oracle Cloud Guard to monitor and maintain the security of your resources in Oracle Cloud Infrastructure. Cloud Guard uses detector recipes that you can define to examine your resources for security weaknesses and to monitor operators and users for risky activities. When any misconfiguration or insecure activity is detected, Cloud Guard recommends corrective actions and assists with taking those actions, based on responder recipes that you can configure.
- Security zone
Security zones ensure Oracle's security best practices from the start by enforcing policies such as encrypting data and preventing public access to networks for an entire compartment. A security zone is associated with a compartment of the same name and includes security zone policies or a "recipe" that applies to the compartment and its sub-compartments. You can't add or move a standard compartment to a security zone compartment.
- Object storage
Object storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. You can safely and securely store and then retrieve data directly from the internet or from within the cloud platform. You can seamlessly scale storage without experiencing any degradation in performance or service reliability. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
- FastConnect
Oracle Cloud Infrastructure FastConnect provides an easy way to create a dedicated, private connection between your data center and Oracle Cloud Infrastructure. FastConnect provides higher-bandwidth options and a more reliable networking experience when compared with internet-based connections.
- Local peering gateway (LPG)
An LPG enables you to peer one VCN with another VCN in the same region. Peering means the VCNs communicate using private IP addresses, without the traffic traversing the internet or routing through your on-premises network.
- Autonomous Transaction Processing Autonomous Transaction Processing delivers a self-driving, self-securing, self-repairing database service that can instantly scale to meet demands of a variety of applications: mission-critical transaction processing, mixed transactions and analytics, IoT, JSON documents, and so on. When you create an Autonomous Database, you can deploy it to one of three kinds of Exadata infrastructure:
- Shared; a simple and elastic choice. Oracle autonomously operates all aspects of the database life cycle from database placement to backup and updates.
- Dedicated on Public Cloud; a private cloud in public cloud choice. A completely dedicated compute, storage, network and database service for only a single tenant, providing for the highest levels of security isolation and governance.
- Dedicated on Cloud@Customer; Autonomous Database on dedicated infrastructure running on on Exadata Database Machine system in your data center, together with the networking configuration that connects it to Oracle Cloud.
- Autonomous Data Warehouse
Oracle Autonomous Data Warehouse is a self-driving, self-securing, self-repairing database service that is optimized for data warehousing workloads. You do not need to configure or manage any hardware, or install any software. Oracle Cloud Infrastructure handles creating the database, as well as backing up, patching, upgrading, and tuning the database.
- Autonomous Transaction Processing
Oracle Autonomous Transaction Processing is a self-driving, self-securing, self-repairing database service that is optimized for transaction processing workloads. You do not need to configure or manage any hardware, or install any software. Oracle Cloud Infrastructure handles creating the database, as well as backing up, patching, upgrading, and tuning the database.
- Exadata DB system
Exadata Database Service enables you to leverage the power of Exadata in the cloud. You can provision flexible X8M systems that allow you to add database compute servers and storage servers to your system as your needs grow. X8M systems offer RoCE (RDMA over Converged Ethernet) networking for high bandwidth and low latency, persistent memory (PMEM) modules, and intelligent Exadata software. You can provision X8M or X9M systems by using a shape that's equivalent to a quarter-rack X8 system, and then add database and storage servers at any time after provisioning.
Recommendations
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
Use regional subnets.
- Security
Use Oracle Cloud Guard to monitor and maintain the security of your resources in Oracle Cloud Infrastructure proactively. Cloud Guard uses detector recipes that you can define to examine your resources for security weaknesses and to monitor operators and users for risky activities; for example, Cloud Guard provides a detector recipe that can alert you if a database is not registered with Data Safe.
For resources that require maximum security, Oracle recommends that you use security zones. A security zone is a compartment associated with an Oracle-defined recipe of security policies that are based on best practices. For example, the resources in a security zone must not be accessible from the public internet and they must be encrypted using customer-managed keys. When you create and update resources in a security zone, Oracle Cloud Infrastructure validates the operations against the policies in the security-zone recipe, and denies operations that violate any of the policies.
- Cloud Guard
Clone and customize the default recipes provided by Oracle to create custom detector and responder recipes. These recipes enable you to specify what type of security violations generate a warning and what actions are allowed to be performed on them. For example, you might want to detect Object Storage buckets that have visibility set to public.
Apply Cloud Guard at the tenancy level to cover the broadest scope and to reduce the administrative burden of maintaining multiple configurations.
You can also use the Managed List feature to apply certain configurations to detectors.
- Network security groups (NSGs)
You can use NSGs to define a set of ingress and egress rules that apply to specific VNICs. We recommend using NSGs rather than security lists, because NSGs enable you to separate the VCN's subnet architecture from the security requirements of your application.
- Load balancer bandwidth
While creating the load balancer, you can either select a predefined shape that provides a fixed bandwidth, or specify a custom (flexible) shape where you set a bandwidth range and let the service scale the bandwidth automatically based on traffic patterns. With either approach, you can change the shape at any time after creating the load balancer.
Explore More
Learn more about implementing Oracle Data Safe for Exadata and Autonomous Databases.
Review these additional resources:
- Well-architected framework for Oracle Cloud Infrastructure
- Deploy a secure landing zone that meets the CIS Foundations Benchmark for Oracle Cloud
- Exadata Cloud@Customer Technical Architecture
- Oracle Exadata Database Service on Dedicated Infrastructure Technical Architecture
- Register Exadata Cloud@Customer Databases by Using an Oracle Data Safe Private Endpoint
- Set up Cloud@Customer database using the wizard
- Simplify Security for your on-premises Oracle Databases with Oracle Data Safe
- Exadata Cloud Service Security Controls
- Oracle Operator Access Control for Exadata Cloud@Customer
- oci-landing-zones / terraform-oci-core-landingzone (OCI Core Landing Zone) on GitHub.
- oci-landing-zones / oci-landing-zone-operating-entities (Operating Entities Landing Zone) on GitHub