Learn About Deploying Agile PLM
Before You Begin
Before you begin to run Agile PLM 9.3.6 or upcoming versions in Oracle Cloud:
- Understand the Agile PLM deployment architecture and other considerations. See Learn about deploying Agile PLM on Oracle Cloud.
- Have access to an Oracle Cloud Infrastructure tenancy.
- Understand Terraform, at a minimum, read Terraform introduction.
- Before setting up Oracle Cloud
Infrastructure components using Terraform, ensure that you’re using a
Windows, Linux, or UNIX-like local host with access to the
internet. The steps to set up and use Terraform are
different on different operating systems.
On a Linux or UNIX-like system, you’ll need the following tools and utilities:
Gitto clone the Terraform provider package and the Terraform modules from the repository. This is optional. You could use a web browser instead, to download the packages.ssh-keygento generate an SSH key pair.OpenSSLto generate an API signing key pair.- A web browser to access the Oracle Cloud Infrastructure Console.
On a Windows system, you’ll need:- Git Bash to clone the Terraform
provider package and the Terraform modules from
the repository. You could use a web browser
instead, to download the packages. However, you’ll
need Git Bash to generate an API signing key pair
as well as an SSH key for the application
instances, using OpenSSL or
ssh-keygen. - PuTTY to generate an SSH key pair and to connect to your bastion hosts using that SSH key.
- A web browser to access the Oracle Cloud Infrastructure Console.
Architecture
You can design your Agile PLM deployment on Oracle Cloud Infrastructure in a single availability domain, across multiple availability domains, or in multiple regions.
-
Single availability domain: You can deploy Agile PLM in a single availability domain and still ensure high availability by setting up multiple application instances. Use this architecture when you want to ensure that your application is available even when an application instance goes down. The other available application instances in the availability domain continue to process the requests.
-
Multiple availability domains: Use this architecture when you want to ensure that your application is available even when one availability domain goes down. You can still access the application instances in another availability domain.
-
Multiple regions: Use this architecture when you want to set up a disaster recovery site for your application in a different region. This architecture is essentially the same as the multiple availability domain architecture, but instead of creating resources in a second availability domain in the same region, you create resources in another region.
Templates to Build Your Infrastructure
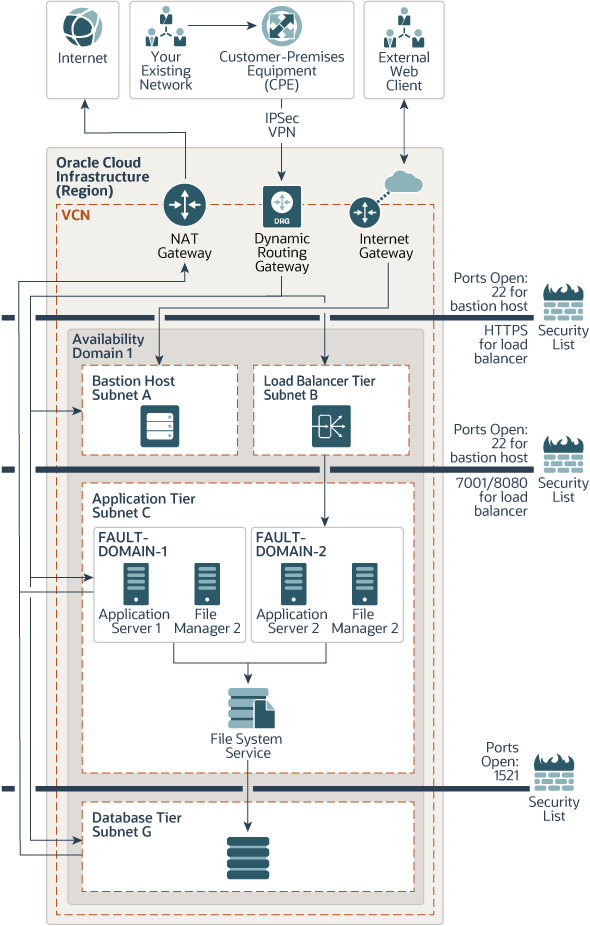
When you apply Terraform plan and install Agile PLM, all application instances in the availability domain are active. The load balancer instances receive requests and send it to the application servers. The application servers process these requests and forwards them to the database instances. You can access the instances in private subnets through the bastion host.
The automatic and on-demand database backups to Oracle Cloud Infrastructure Object Storage can be configured using the Oracle Cloud Infrastructure console. The backup of application can be configured by using the policy-based backup feature of Oracle Cloud Infrastructure Block Volumes. Oracle Cloud Infrastructure Block Volumes provides you with the capability to perform volume backups automatically based on a schedule and retain them based on the selected backup policy. This allows you to adhere to your data compliance and regulatory requirements. There are three predefined backup policies: Bronze, Silver, and Gold. Each backup policy has a predefined backup frequency and retention period. You can set the variables for these policies in your Terraform plans.
Terraform Plan for Single Instance: The architecture consists of a virtual cloud network with the bastion, load balancer, application, file manager, and database hosts that are required to run Agile PLM. The Terraform configuration will install the application server, file manager and database hosts on a single virtual machine. You can use this configuration for training or testing purposes. The bastion host is deployed in a public subnet, and all the other instances are deployed in private subnets.
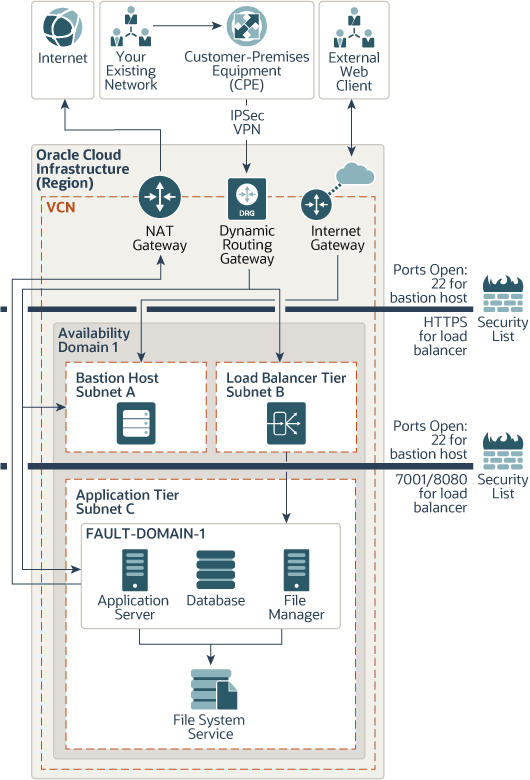
Description of the illustration simple_topology_plan.png
Terraform Plan for Multiple Instances: The architecture consists of a virtual cloud network (VCN) with the bastion, load balancer, application, file manager, and database hosts placed in separate virtual machines. In this architecture, multiple application instances are deployed in an availability domain to ensure high availability. This ensures that your application is available even when an application instance goes down. Fault domains enable you to distribute your instances so that they are not on the same physical hardware within a single availability domain.
Instances in the private subnet may optionally require outbound connection to the Internet to download application patches and for external integrations. For this purpose, use a Network Address Translation (NAT) gateway in your VCN. With a NAT gateway, the hosts in the private subnet can initiate connections to the Internet and receive responses, but won’t receive inbound connections initiated from the Internet.
About Required Services and Policies
This solution requires the following services and access-management policies:
| Service | Policies Required To... |
|---|---|
| Oracle Cloud Infrastructure Identity and Access Management | Create and manage compartments. |
| Oracle Cloud Infrastructure Networking | Create and manage VCNs, subnets, internet gateways, route tables, security lists, LPGs, and DRGs |
| Oracle Cloud Infrastructure Compute | Create and manage compute instances. |
See Learn how to get Oracle Cloud services for Oracle Solutions to get the cloud services you need.