Deploy Multicloud Inbound and Outbound Private Network Connectivity
Connecting services and applications running on private networks with on-premises enterprise applications using the public internet can pose a security risk for your organization. Instead, you can deploy an inbound and outbound private connection with applications on private networks such as Amazon Virtual Private Cloud, Microsoft Azure Virtual Network, Google Cloud Virtual Private Cloud, or another on-premises private network.
Using the Oracle Integration Cloud Service connectivity agent and OCI Oracle Integration Cloud Service private endpoint, the Oracle Integration Cloud Service directs inbound and outbound traffic from OCI to on-premises applications.
Architecture
This architecture provides the necessary connectivity between multicloud private networks and Oracle's cloud services and applications without directing traffic through the public internet as part of its outbound and inbound integration from Oracle Integration Cloud Service. Use this architecture when you have a requirement to consume and interact with an Oracle Integration Cloud Service private only connection.
Oracle Integration Cloud Service exposes REST API trigger integration services as publicly available, and all the REST trigger integrations are available to be accessed through a public network by default. Using the Oracle Integration Cloud Service allow list, you can restrict access to Oracle Integration Cloud Service to private consumers only. Private consumers will not access Oracle Integration Cloud Service directly, but through the OCI service virtualization layer represented by OCI API Gateway.
Inbound OCI interactions are enabled by OCI API Gateway, which enables you to publish APIs with private endpoints accessible from within your network. In this architecture you will publish Oracle Integration Cloud Service integration services as private APIs in combination with Oracle Integration Cloud Service. Additional OCI services are used to enable private connectivity for Oracle Integration Cloud Service inbound and outbound interactions.
There are 3 interaction types in this architecture:
- Oracle Integration Cloud
Service Connectivity Agent
Subscribe to business services, applications, and private platforms. This architecture uses the Oracle Integration Cloud Service connectivity agent to communicate with private business services or applications. The Oracle Integration Cloud Service connectivity agent is installed on an OCI compute instance in a private subnet within an OCI VCN. The connectivity agent communicates with Oracle Integration Cloud Service through a service gateway on one side, and with the service or application running on an private network on the other side through a dynamic routing gateway (DRG) and FastConnect private peering, or VPN. The connectivity agent implements Oracle Integration Cloud Service outbound scenarios, however it is capable of subscription and polling business services, platforms, and applications (for example java message service, messaging queue, or database).
- OCI Private Endpoint Connectivity
All outbound traffic from Oracle Integration Cloud Service goes through a connection based on an adapter. While you create a private endpoint for an instance, securing outbound traffic with the private endpoint is available on an adapter-by-adapter basis. For example, a Kafka adapter and FTP adapter support connectivity through a private endpoint, and no Oracle Integration Cloud Service connectivity agent is needed. The private endpoint connectivity adapter support grows with every Oracle Integration Cloud Service update.
- OCI API Gateway
Leverage OCI services without routing OCI inbound traffic through public networks. Extend the OCI API Gateway private pattern using a service gateway in the VCN where OCI API Gateway is provisioned to allow traffic to Oracle services. OCI API Gateway allows private platforms and applications to invoke services and functions running in OCI. In this architecture, OCI API Gateway provides access to REST API adapter trigger-based integrations and the Oracle Integration Cloud Service management API with private connectivity.
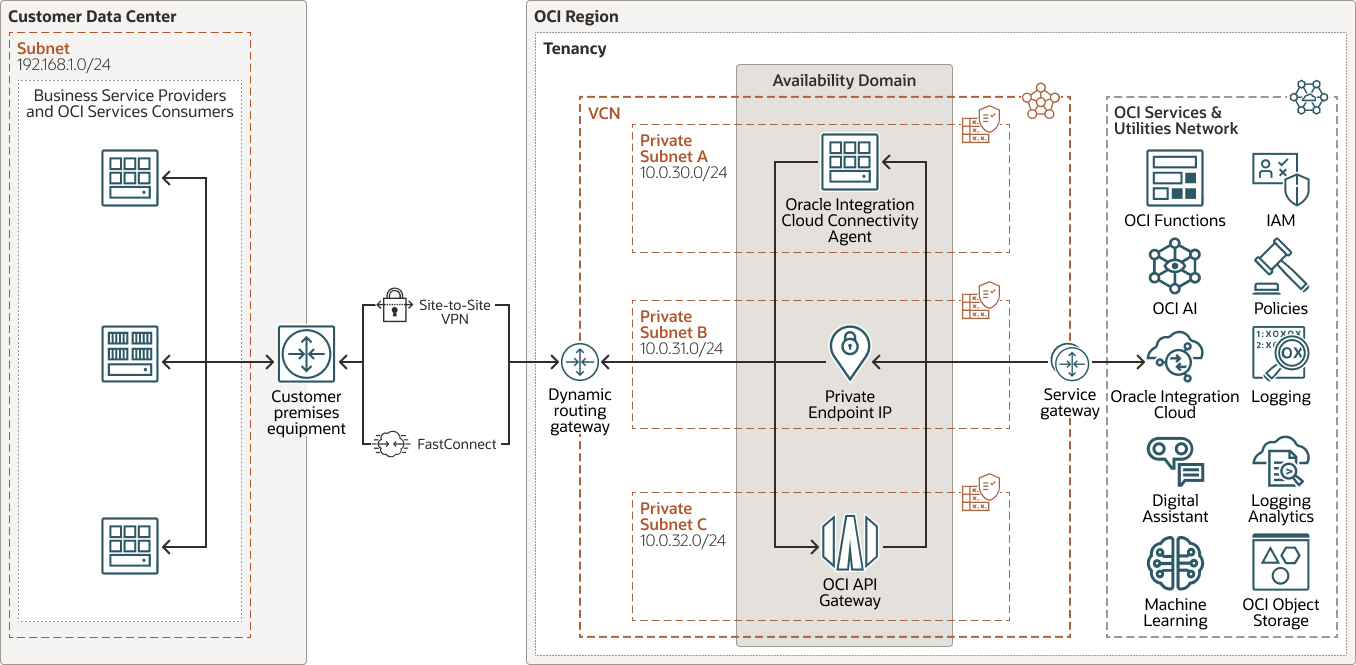
The following diagram illustrates this reference architecture.
integration-cloud-private-inbound-outbound.zip
The architecture has the following components:
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Availability domains
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain shouldn't affect the other availability domains in the region.
- Fault domains
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Route table
Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between VCNs in the same region, between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- Customer-premises equipment (CPE)
An object that represents the network asset that lives in the on-premises network and establishes the VPN connection. Most border firewalls act as the CPE, but a separate device (like an appliance or a server) can be a CPE.
- Site-to-Site VPN
Site-to-Site VPN provides IPSec VPN connectivity between your on-premises network and VCNs in Oracle Cloud Infrastructure. The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
- FastConnect
Oracle Cloud Infrastructure FastConnect provides an easy way to create a dedicated, private connection between your data center and Oracle Cloud Infrastructure. FastConnect provides higher-bandwidth options and a more reliable networking experience when compared with internet-based connections.
- OCI Private Endpoint
OCI Private endpoint is private OCI resource you can use to access nonpublic cloud resources in your tenancy from Oracle Cloud Infrastructure Resource Manager. Oracle Integration Cloud Service routes traffic and packages through the private endpoint. All traffic stays on your private network without going over the public internet.
- API Gateway
Oracle API Gateway enables you to publish APIs with private endpoints that are accessible from within your network, and which you can expose to the public internet if required. The endpoints support API validation, request and response transformation, CORS, authentication and authorization, and request limiting.
- Oracle Integration Cloud
Service
Oracle Integration Cloud Service is a fully managed service that allows you to integrate your applications, automate processes, exchange business documents B2B, and create visual applications.
- Functions
Oracle Cloud Infrastructure Functions is a fully managed, multitenant, highly scalable, on-demand, Functions-as-a-Service (FaaS) platform. It is powered by the Fn Project open source engine. Functions enable you to deploy your code, and either call it directly or trigger it in response to events. Oracle Functions uses Docker containers hosted in Oracle Cloud Infrastructure Registry.
- Oracle Cloud Infrastructure
AI Services
Oracle Cloud Infrastructure AI Services is a collection of services with prebuilt machine learning models that make it easier for developers to apply AI to applications and business operations. The models can be custom-trained for more accurate business results. For more information, see Oracle Cloud Infrastructure Generative AI, Oracle Cloud Infrastructure Language, Oracle Cloud Infrastructure Speech, Oracle Cloud Infrastructure Vision, and Oracle Cloud Infrastructure Document Understanding.
- Machine Learning Services (ML)
Machine learning services from Oracle make it easier to build, train, deploy, and manage custom learning models. These services deliver data science capabilities with support from favorite open source libraries and tools, or through in-database machine learning and direct access to cleansed data. See Oracle Cloud Infrastructure Data Science, Machine Learning in Oracle Database, Oracle Cloud Infrastructure Data Labeling, OCI Virtual Machines for Data Science.
- Oracle Digital Assistant
Digital assistants are virtual devices that help users accomplish tasks through natural language conversations, without having to manage various apps and web sites.
- Identity and Access Management (IAM)
Oracle Cloud Infrastructure Identity and Access Management (IAM) is the access control plane for Oracle Cloud Infrastructure (OCI) and Oracle Cloud Applications. The IAM API and the user interface enable you to manage identity domains and the resources within the identity domain. Each OCI IAM identity domain represents a standalone identity and access management solution or a different user population.
- Policy
An Oracle Cloud Infrastructure Identity and Access Management policy specifies who can access which resources, and how. Access is granted at the group and compartment level, which means you can write a policy that gives a group a specific type of access within a specific compartment, or to the tenancy.
- Audit
The Oracle Cloud Infrastructure Audit service automatically records calls to all supported Oracle Cloud Infrastructure public application programming interface (API) endpoints as log events. Currently, all services support logging by Oracle Cloud Infrastructure Audit.
- LoggingLogging is a highly scalable and fully managed service that provides access to the following types of logs from your resources in the cloud:
- Audit logs: Logs related to events emitted by the Audit service.
- Service logs: Logs emitted by individual services such as API Gateway, Events, Functions, Load Balancing, Object Storage, and VCN flow logs.
- Custom logs: Logs that contain diagnostic information from custom applications, other cloud providers, or an on-premises environment.
- Oracle Cloud Infrastructure Logging Analytics
Oracle Cloud Infrastructure Logging Analytics is a machine learning-based cloud service that monitors, aggregates, indexes, and analyzes all log data from on-premises and multi-cloud environments. Enabling users to search, explore, and correlate this data to troubleshoot and resolve problems faster and derive insights to make better operational decisions.
- Object storage
Object storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. You can safely and securely store and then retrieve data directly from the internet or from within the cloud platform. You can seamlessly scale storage without experiencing any degradation in performance or service reliability. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
Recommendations
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
- Connectivity
When you deploy resources to Oracle Cloud Infrastructure, you might start small, with a single connection to your on-premises network. This single connection could be through FastConnect or through IPSec VPN. To plan for redundancy, consider all the components (hardware devices, facilities, circuits, and power) between your on-premises network and Oracle Cloud Infrastructure. Also consider diversity, to ensure that facilities are not shared between the paths.
- Restrict Access to an Oracle Integration Cloud
Service Instance
Restrict the networks that have access to your Oracle Integration Cloud Service instance by configuring an allow-list (formerly a whitelist). Only users from the specific IP addresses, Classless Inter-Domain Routing (CIDR) blocks, and virtual cloud networks that you specify can access the Oracle Integration Cloud Service instance.
- Private Endpoint Network
The VCN must be in the same region as your Oracle Integration Cloud Service instance. The VCN and subnet can be in any compartment and can be in either the same or different compartments. The subnet can be public or private, but it must be private for private only access.
Considerations
Consider the following points when deploying this reference architecture.
- Scalability
When creating Oracle Integration Cloud Service instances, administrators specify the number of message packs they plan to use per instance.
- Resource Limits
Consider the best practices, limits by service, and compartment quotas for your tenancy.
- Security
Use Oracle Cloud Infrastructure Identity and Access Management policies to control who can access your cloud resources and what operations can be performed. OCI cloud services use Oracle Cloud Infrastructure Identity and Access Management policies such as allowing OCI API Gateway to invoke functions. OCI API Gateway can also control access using OAuth authentication and authorization. Oracle Cloud Infrastructure Identity and Access Management allows authentication and authorization that can be federated via Oracle Cloud Infrastructure Identity and Access Management - as a result, the OCI API Gateway has the power to authenticate against a wide array of services and authentication setups.
- Performance and Cost
OCI offers compute shapes that cater to a wide range of applications and use cases. Choose the shapes for your compute instances carefully. Select shapes that provide optimal performance for your load at the lowest cost. If you need more performance, memory, or network bandwidth, you can change to a larger shape.
OCI API Gateway supports response caching by integrating with an external cache server (such as a Redis or KeyDB server), to help avoid unnecessary load on backend services. When responses are cached, if similar requests are received they can be completed by retrieving data from a response cache, rather than sending the request to the backend service. This reduces the load on backend services and thereby helps in improving performance and reducing costs.
OCI API Gateway also caches authorization tokens (based on their time to leave), reducing the load on the identity provider and improving performance.
- Availability
Consider using a high-availability option based on your deployment requirements and region. The options include distributing resources across multiple availability domains in a region, and distributing resources across the fault domains within an availability domain. Fault domains provide the best resilience for workloads deployed within a single availability domain. For high availability in the application tier, deploy the application servers in different fault domains, and use a load balancer to distribute client traffic across the application servers.
- Monitoring and Alerts
Set up monitoring and alerts on CPU and memory usage for your nodes, so you can scale the shape up or down as needed.
Deploy
You can deploy this reference architecture on Oracle Cloud Infrastructure by following these steps:
- Sign in to the OCI console.
- Set up the required networking infrastructure as shown in the architecture diagram: VCN, subnet, dynamic routing gateway, security list, routing table, service gateway, FastConnect/VPN, CPE, and OCI private endpoint.
- Provision an Oracle Integration Cloud Service instance.
- Install the Oracle Integration Cloud
Service connectivity agent.
- Navigate to the Oracle Integration Cloud Service console and create an agent group.
- Follow the instructions for downloading and running and connectivity agent installer.
- Navigate to the OCI console and select compute shapes according to Oracle Integration Cloud Service system requirements.
- Configure the Oracle Integration Cloud Service private endpoint.
- Create an OCI API Gateway instance.
- Restrict the networks with access to your Oracle Integration Cloud Service instance by configuring an allowlist, if required.
Explore More
Review these resources for instructions and context to deploy multicloud private network connectivity through Oracle Integration Cloud Service.
Oracle Integration Cloud Service
- "Download and Run the Connectivity Agent Installer" in Provisioning and Administering Oracle Integration 3
- "System Requirements" in Provisioning and Administering Oracle Integration 3
- "Prerequisites for Configuring a Private Endpoint" in Provisioning and Administering Oracle Integration 3
- "About Connecting to Endpoints Using a Private Virtual Cloud Network (VCN)" in Provisioning and Administering Oracle Integration 3
- "Connect to Private Resources" in Provisioning and Administering Oracle Integration 3
Oracle Cloud Infrastructure API Gateway
- "API Gateway QuickStart Guide" in Oracle Cloud Infrastructure documentation
- Oracle API Gateway documentation
Oracle Cloud Infrastructure
- Best practices framework for Oracle Cloud Infrastructure
- Oracle Cloud Cost Estimator
- Oracle API Management
- "FastConnect Overview" in Oracle Cloud Infrastructure documentation
- "Networking Overview" in Oracle Cloud Infrastructure documentation
- "Security Overview" in Oracle Cloud Infrastructure documentation
- Establish a multi-cloud private network connectivity through Oracle Integration Cloud