Deploy Oracle Banking Digital Experience on Oracle Cloud Infrastructure
Oracle Banking Digital Experience is a full-spectrum, full-stack solution offering ready-for-business retail, SME, corporate, and Islamic banking functionality through Omni channel touch-points in a modular environment. It offers a personalized user experience across all contemporary digital banking channels on mobile phones, tablets, desktops, and wearables through mobile applications and web interfaces.
Customers can deploy Oracle Banking Digital Experience in a matter of weeks and employ exclusive Oracle Cloud products, such as Exadata Cloud, Oracle Real Application Clusters (RAC), and Autonomous Database, designed for unmatched performance, reliability, and autonomous operations. Oracle Cloud’s global footprint and validated reference architectures ensure data sovereignty, disaster recovery, and enhanced availability, so banks can improve user experience tremendously.
Architecture
This reference architecture shows a highly available topology for deploying Oracle Banking Digital Experience on Oracle Cloud Infrastructure.
The applications and databases are in separate private subnets, which can be accessed through a bastion host. External access to the applications is through a flexible load balancer. Each tier has redundant resources in different fault domains to provide a highly available application environment.
The following diagram illustrates this reference architecture.
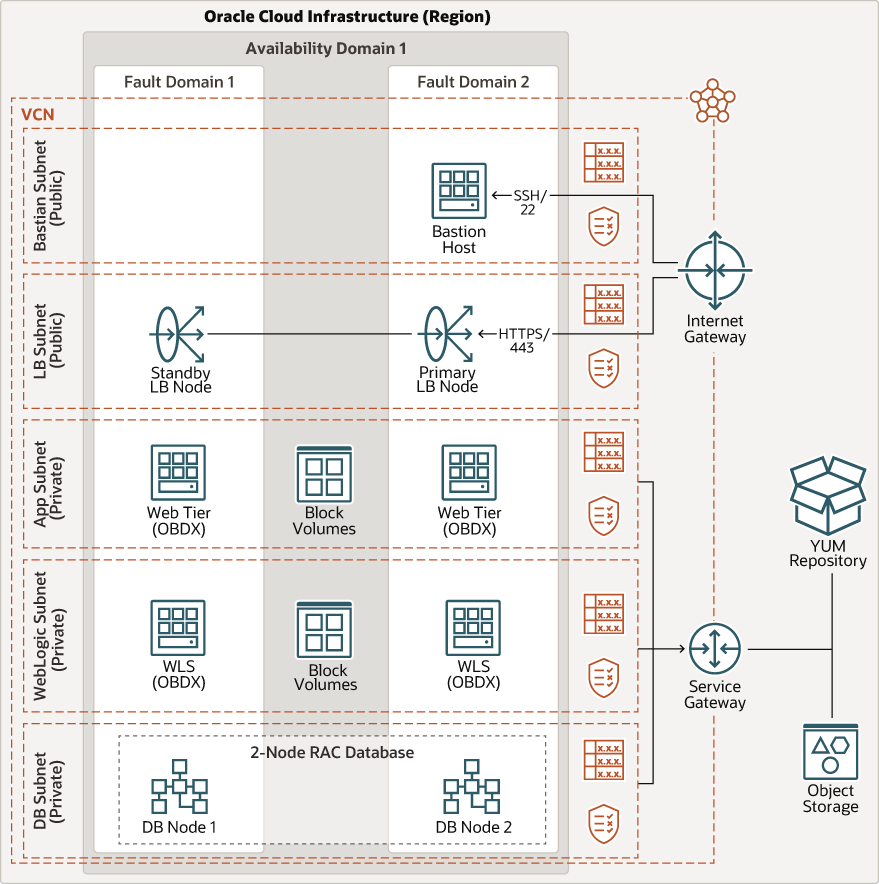
Description of the illustration obdx-arch.png
The architecture has the following components:
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Availability domains
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domains
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Bastion host
The bastion host is a compute instance that serves as a secure, controlled entry point to the topology from outside the cloud. The bastion host is provisioned typically in a demilitarized zone (DMZ). It enables you to protect sensitive resources by placing them in private networks that can't be accessed directly from outside the cloud. The topology has a single, known entry point that you can monitor and audit regularly. So, you can avoid exposing the more sensitive components of the topology without compromising access to them.
- Application servers The middle tier consists of compute instances to deploy the following components on Oracle WebLogic Server:
- Oracle Banking Digital Experience (OBDX)
- Web tier OBDX
- Database systems
This architecture uses a database system with Oracle Database Enterprise Edition Extreme Performance, using Oracle Real Application Clusters (RAC). It also uses Oracle Automatic Storage Management (Oracle ASM) with a minimum of 256 GB.
- Block volume
With block storage volumes, you can create, attach, connect, and move storage volumes, and change volume performance to meet your storage, performance, and application requirements. After you attach and connect a volume to an instance, you can use the volume like a regular hard drive. You can also disconnect a volume and attach it to another instance without losing data.
- Object storage
Object storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
- NAT gateway
The NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Service gateway
The service gateway provides access from a VCN to other services, such as Oracle Cloud Infrastructure Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and never traverses the internet.
- Internet gateway
The internet gateway allows traffic between the public subnets in a VCN and the public internet.
Recommendations
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
Use regional subnets.
- Network connectivity
You can manage the environment by connecting to your existing on-premises infrastructure by using a site-to-site VPN or a dedicated connection with FastConnect. If the environment needs to be segregated from the existing infrastructure, a bastion host can secure the management connections.
- Compute
The servers in this architecture use an Oracle Linux 7.7 image or opt for a Flexible virtual machine (VM) shape. For applications that are deployed on VMs, you can take the advantage of flexible VM instances. You can increase or decrease capacity of the VMs in minutes by adding CPUs and memory to their existing footprint, 1–64 cores and 1–64 GB per core, up to 1,024 GB per instance.
If your application requires more memory, cores, or network bandwidth, choose a larger shape.
- Load balancer
The OCI Load Balancing service provides automated traffic distribution from one entry point to multiple servers reachable from your VCN. When you provision the load balancer in a single availability domain, redundant load balancer nodes are distributed across two fault domains. When you create the application layer in cluster mode, you can configure the load balancer to distribute traffic across the servers in your Oracle WebLogic Server domain. While creating the load balancer, you can either select a predefined shape that provides a fixed bandwidth, or specify a custom (flexible) shape where you set a bandwidth range and let the service scale the bandwidth automatically based on traffic patterns. With either approach, you can change the shape at any time after creating the load balancer. You can specify a minimum bandwidth of 10 Mbps to a maximum bandwidth of 8,000 Mbps. The minimum bandwidth is always available and provides instant readiness for your workloads.
We provide choice of load balancers, and you can find more information in OCI's release notes on flexible load balancing.
- Virtual Machine (VM) CPU and GPU Shapes and options
Virtual machines allow you to run an operating system in an app window on your desktop that behaves like a full, separate computer. You can use it to play around with different operating systems, run software your main operating system can't, and try out apps in a safe, sandboxed environment. For applications that are deployed on virtual machines (VM), you can take the advantage of flexible VM instances. You can increase or decrease capacity of the VMs in minutes by adding CPUs and memory to their existing footprint, 1–64 cores and 1–64 GB per core, up to 1,024 GB per instance.
For further details on VM shapes and size, refer to the document Compute Shapes, listed in the Explore More topic, below.
- High availability and disaster recovery
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
All the resources in this architecture are deployed in a single availability domain. For disaster recovery considerations, customers can choose to distribute their VM across multiple availability domains if the region allows it or customers can use a cross-region disaster recovery approach.
- Bring your own license (BYOL)
Oracle BYOL allows customers to apply licenses that they currently own for on-premises software for equivalent, highly automated Oracle platform-as-a-service (PaaS). With this program, customers can use their existing on-premises licenses with 100-percent workload compatibility and license mobility, helping you reach business value faster.
- Security
Oracle Cloud Guard to monitor and maintain the security of your resources in OCI proactively. Cloud Guard uses detector recipes that you can define to examine your resources for security weaknesses and to monitor operators and users for risky activities. When any misconfiguration or insecure activity is detected, Cloud Guard recommends corrective actions and assists with taking those actions, based on responder recipes that you can define.
For resources that require maximum security, Oracle recommends that you use security zones. A security zone is a compartment associated with an Oracle-defined recipe of security policies that are based on best practices. For example, the resources in a security zone must not be accessible from the public internet and they must be encrypted using customer-managed keys. When you create and update resources in a security zone, Oracle Cloud Infrastructure validates the operations against the policies in the security-zone recipe, and denies operations that violate any of the policies.
- Block Volume
The Oracle Cloud Infrastructure Block Volume service provides the capability to attach a block volume to multiple Compute instances. With this feature, you can share block volumes across instances in read/write or read-only mode. Attaching block volumes as read/write and shareable enables you to deploy and manage your cluster-aware solutions. For more details about this process, see Attaching a Volume to Multiple Instances, listed in the Explore More topic, below.
Considerations
When implementing Oracle Banking Digital Experience, consider these options.
- Performance
The performance of banking applications depends on the workload characteristics and requirements of the specific applications. A synthetic test can't predict performance reliably. For sizing assistance, work with your Oracle Sales consultant to characterize the workload requirements and provision the resources required to support the environment.
- Availability
Consider using a high-availability option based on your deployment requirements and your region. The options include distributing resources across multiple availability domains in a region, and distributing resources across the fault domains within an availability domain.
Explore More
Learn more about deploying Oracle Banking Digital Experience by reviewing these additional resources:
- Oracle Banking Digital Experience documentation
- Best practices framework for Oracle Cloud Infrastructure
- Learn about protecting your cloud topology against disasters
- Learn about architecting a highly available cloud topology
- Flexible Load Balancing Release Notes
- VM Shapes in the Oracle Cloud Infrastructure Computes Shapes documentation
- Configuring Multiple Instance Volume Attachments with Read/Write Access