Set up a WordPress CMS Connected to a MySQL Database in the Cloud
Create and manage modern websites in the cloud without needing a degree in programming or database administration. Take advantage of WordPress platform's user-friendly features and the elasticity and cost benefits of hosting your web pages and blogs in Oracle Cloud Infrastructure.
Architecture
This architecture deploys a WordPress CMS and Oracle MySQL Database Service in Oracle Cloud Infrastructure (OCI).
You can deploy WordPress in a single node, or as part of a multinode HA configuration. This reference architecture includes Terraform automation which is compatible with both configurations.
For a complex multinode high availability environment, deploy WordPress nodes in multiple fault domains with primary and standby load balancers and shared Oracle Cloud Infrastructure File Storage service (managed NFS service) for all WordPress nodes.
The following diagram illustrates this multinode architecture.
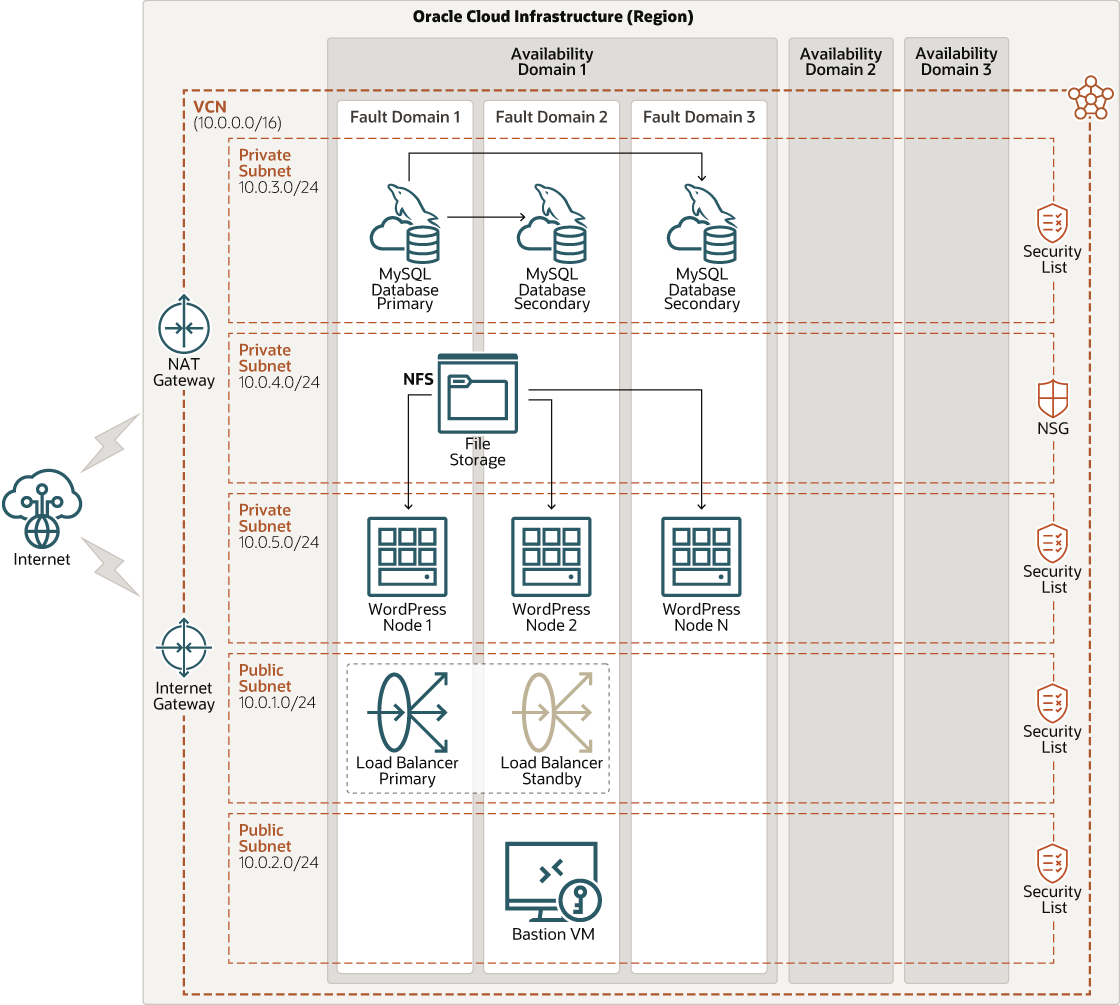
Description of the illustration oci-arch-wordpress-mds.png
oci-arch-wordpress-mds-oracle.zip
You can do the following when configuring a multinode environment:
- Define the number of WordPress layer nodes.
- Deploy public load balancers and hide the WordPress nodes in a private subnet.
- Deploy Bastion Host or Bastion Services to access private resources.
- Use Oracle Cloud Infrastructure File Storage services with shared NFS storage for WordPress content (share uploads, plugins, and themes between nodes).
The following diagram illustrates a simple single-node architecture. It consists of a lightweight deployment, which could be suitable for learning purposes or serve as a proof-of-concept.
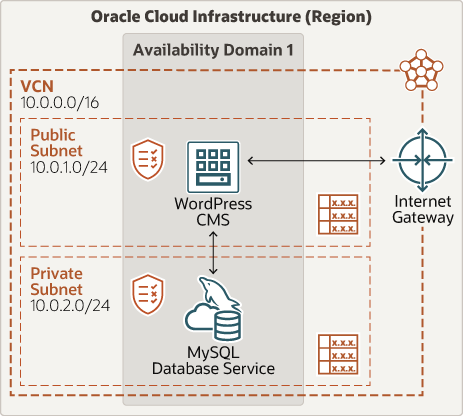
Description of the illustration deploy-wordpress-cms-mysql-dbs.png
deploy-wordpress-cms-mysql-dbs-oracle.zip
The architectures have some or all of the following components:
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Availability domains
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domain
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Internet gateway
The internet gateway allows traffic between the public subnets in a VCN and the public internet.
- Network address translation (NAT) gateway
A NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Network security group (NSG)
NSGs act as virtual firewalls for your cloud resources. With the zero-trust security model of Oracle Cloud Infrastructure, all traffic is denied, and you can control the network traffic inside a VCN. An NSG consists of a set of ingress and egress security rules that apply to only a specified set of VNICs in a single VCN.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Oracle MySQL Database Service
Oracle MySQL Database Service is a fully managed Oracle Cloud Infrastructure (OCI) database service that lets developers quickly develop and deploy secure, cloud native applications. Optimized for and exclusively available in OCI, MySQL Database Service is 100% built, managed, and supported by the OCI and MySQL engineering teams.
In this reference architecture, Oracle MySQL Database Service is deployed on a virtual machine and is used to host the content information for WordPress. The deployment is not in a cluster.
- File storage
The Oracle Cloud Infrastructure File Storage service provides a durable, scalable, secure, enterprise-grade network file system. You can connect to a File Storage service file system from any bare metal, virtual machine, or container instance in a VCN. You can also access a file system from outside the VCN by using Oracle Cloud Infrastructure FastConnect and IPSec VPN.
- WordPress content management system (CMS)
WordPress CMS enables you to build a full-blown blog site or a general-purpose website. This architecture uses a regular Compute instance to deploy the WordPress CMS engine.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end.
- Bastion service
Oracle Cloud Infrastructure Bastion provides restricted and time-limited secure access to resources that don't have public endpoints and that require strict resource access controls, such as bare metal and virtual machines, Oracle MySQL Database Service, Autonomous Transaction Processing (ATP), Oracle Container Engine for Kubernetes (OKE), and any other resource that allows Secure Shell Protocol (SSH) access. With Oracle Cloud Infrastructure Bastion service, you can enable access to private hosts without deploying and maintaining a jump host. In addition, you gain improved security posture with identity-based permissions and a centralized, audited, and time-bound SSH session. Oracle Cloud Infrastructure Bastion removes the need for a public IP for bastion access, eliminating the hassle and potential attack surface when providing remote access.
- Compute
The Oracle Cloud Infrastructure Compute service enables you to provision and manage compute hosts in the cloud. You can launch compute instances with shapes that meet your resource requirements for CPU, memory, network bandwidth, and storage. After creating a compute instance, you can access it securely, restart it, attach and detach volumes, and terminate it when you no longer need it.
Recommendations
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
- Security lists
Use security lists to define ingress and egress rules that apply to the entire subnet.
- Compute shapes
This architecture uses an Oracle Linux 7.8 OS image with a VM.Standard2.1 shape for WordPress CMS. If your application’s resource needs are different, you can choose a different shape.
- Oracle MySQL Database Service
In this architecture, WordPress CMS stores the relational data in Oracle MySQL Database Service. We recommend using the latest version.
Considerations
When deploying WordPress in Oracle Cloud, consider the following for scalability, availability, and backup:
- WordPress CMS scalability
You can scale your WordPress CMS by using the instance pool and autoscaling features.
Instance pools let you provision and create multiple Compute instances based on the same configuration within the same region.
Autoscaling lets you automatically adjust the number of Compute instances in an instance pool based on performance metrics, such as CPU utilization. Autoscaling helps you provide consistent performance for users during periods of high demand and helps you reduce your costs during periods of low demand.
- Oracle MySQL Database Service scalability
Choose the shape of the machine for your Oracle MySQL Database Service based on the planned workload.
- Application availability
Fault domains provide the best resilience within an availability domain. If you need higher availability, consider using multiple availability domains or multiple regions.
- Oracle MySQL Database Service backups
MySQL Database Service supports two types of backup: full backup of all data contained in the database system and incremental backup of only the data that has been added or changed since the last full backup. Backups run in the following ways:
-
Manual: An action in the Console or request made through the API initiates the backup. Manual backups can be retained for a minimum of one day and a maximum of 365 days.
-
Automatic: Automatically scheduled backups run without any required interaction at a time of the user's choosing. Automatic backups are retained for between one and 35 days. The default retention value is seven days. When defined, you can’t edit the retention period of an automatic backup
The Oracle Cloud Infrastructure Block Volumes service lets you make point-in-time backups of data on a block volume. You can then restore these backups to new volumes immediately or later.
You can also use the service to make a point-in-time, crash-consistent backup of a boot volume without application interruption or downtime. Boot volume backup capabilities are the same as block volume backup capabilities.
-
- Security policies
Use policies to restrict who can access what Oracle Cloud Infrastructure (OCI) resources that your company has and how.
- Network security
The Networking service offers two virtual firewall features that use security rules to control traffic at the packet level: security lists and network security groups (NSGs). An NSG consists of a set of ingress and egress security rules that apply only to a set of VNICs of your choice in a single VCN. For example, you can choose all the Compute instances that act as web servers in the web tier of a multitier application in your VCN.
NSG security rules function the same as security list rules. However, for an NSG security rule's source or destination, you can specify an NSG instead of a CIDR block. So, you can easily write security rules to control traffic between two NSGs in the same VCN or traffic within a single NSG. When you create a database system, you can specify one or more NSGs. You can also update an existing database system to use one or more NSGs.
Deploy
The Terraform code for this reference architecture is available on GitHub. You can pull the code into Oracle Cloud Infrastructure Resource Manager with a single click, create the stack, and deploy it. Alternatively, you can download the code from GitHub to your computer, customize the code, and deploy the architecture by using the Terraform CLI.
- Deploy using the sample stack in Oracle Cloud Infrastructure Resource
Manager:
- Click

If you aren't already signed in, enter the tenancy and user credentials.
- Review and accept the terms and conditions.
- Select the region where you want to deploy the stack.
- Follow the on-screen prompts and instructions to create the stack.
- After creating the stack, click Terraform Actions, and select Plan.
- Wait for the job to be completed, and review the plan.
To make any changes, return to the Stack Details page, click Edit Stack, and make the required changes. Then, run the Plan action again.
- If no further changes are necessary, return to the Stack Details page, click Terraform Actions, and select Apply.
- Click
- Deploy using the Terraform code in GitHub:
- Go to GitHub.
- Clone or download the repository to your local computer.
- Follow the instructions in the
READMEdocument.
- Deploy using the tutorial, Install WordPress CMS on Oracle Linux with MySQL database.
Explore More
Learn more about Oracle Cloud Infrastructure best practices and Oracle MySQL Database Service.
Review these additional resources:
Change Log
This log lists significant changes:
| June 8, 2022 |
|
| September 14, 2021 |
|