Isolate Multitier and Cross-Regional Development Environments by Using Compartments
Take advantage of compartments to create a template for secure multitier and cross-regional development and test environments that you can use to create enterprise solutions on Oracle Cloud Infrastructure.
To implement mission-critical projects, organizations typically maintain separate environments for developing and testing before releasing the project into a production environment. An environment lets you define and manage Oracle Cloud PaaS and Oracle Cloud Infrastructure services as a single entity. It’s important to have the right resources, structure, and design across environments to manage them efficiently.
Compartments are a powerful feature in Oracle Cloud Infrastructure (OCI) for security isolation and access control. Through policy enforcement, they deliver the right access level according to the parameters defined by the organization for resource management and delegated administration.
Architecture
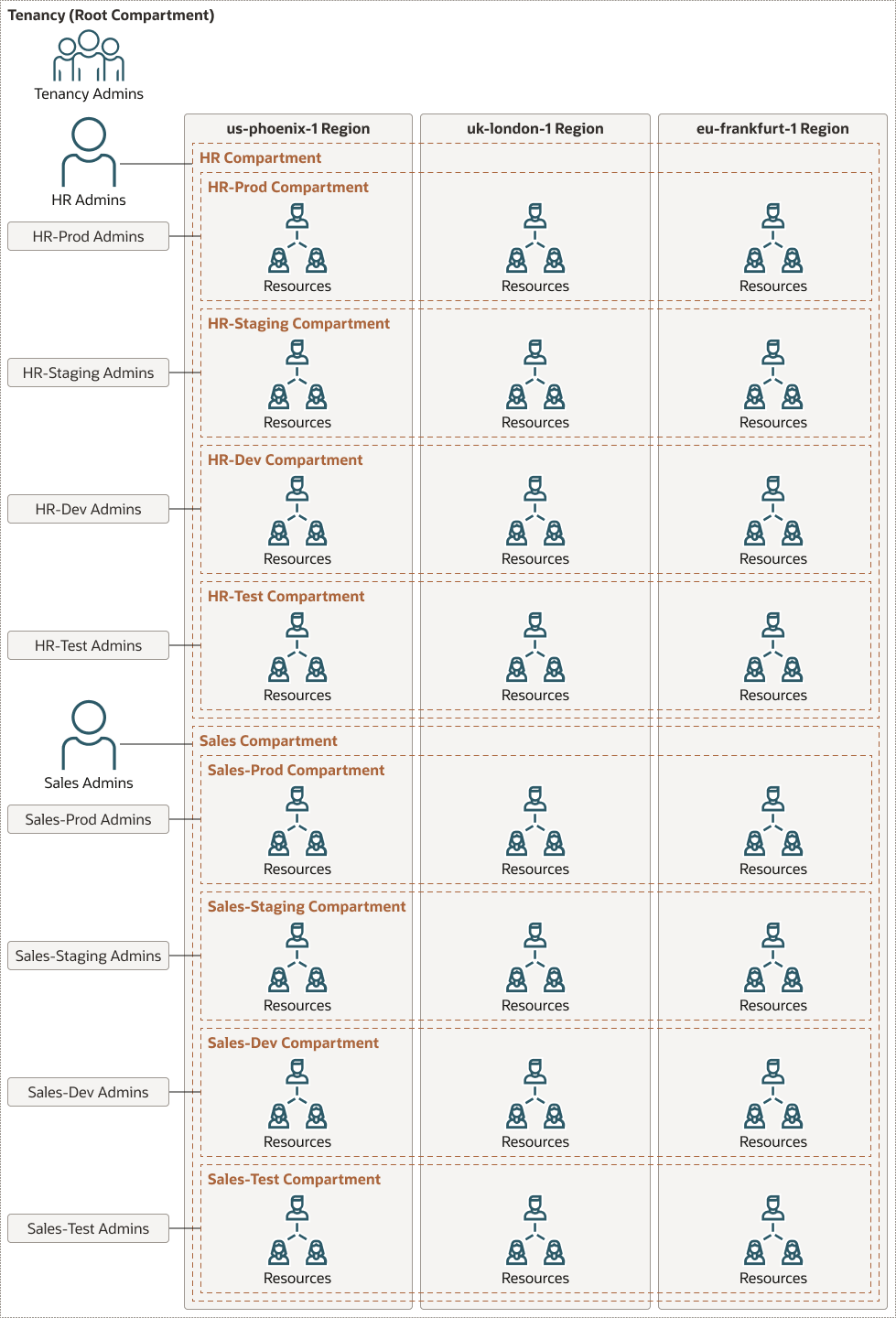
This reference architecture shows how to use compartments to design and configure different environments on Oracle Cloud Infrastructure and how to provision resources to support software development and the release life cycle. The architecture uses a multitier web application as a reference point while allocating resources across different organizations within an enterprise to illustrate the implementation.
The following diagram illustrates this architecture.
oci-dev-env-architecture-oracle.zip
This architecture has the following components:
- Tenancy
A tenancy is a secure and isolated partition that Oracle sets up within Oracle Cloud when you sign up for Oracle Cloud Infrastructure. You can create, organize, and administer your resources in Oracle Cloud within your tenancy. A tenancy is synonymous with a company or organization. Usually, a company will have a single tenancy and reflect its organizational structure within that tenancy. A single tenancy is usually associated with a single subscription, and a single subscription usually only has one tenancy.
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Compartment
Compartments are cross-region logical partitions within an Oracle Cloud Infrastructure tenancy. Use compartments to organize your resources in Oracle Cloud, control access to the resources, and set usage quotas. To control access to the resources in a given compartment, you define policies that specify who can access the resources and what actions they can perform.
- Policy
An Oracle Cloud Infrastructure Identity and Access Management policy specifies who can access which resources, and how. Access is granted at the group and compartment level, which means you can write a policy that gives a group a specific type of access within a specific compartment, or to the tenancy.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end.
- Compute
The Oracle Cloud Infrastructure Compute service enables you to provision and manage compute hosts in the cloud. You can launch compute instances with shapes that meet your resource requirements for CPU, memory, network bandwidth, and storage. After creating a compute instance, you can access it securely, restart it, attach and detach volumes, and terminate it when you no longer need it.
- Autonomous Transaction
Processing
Oracle Autonomous Transaction Processing is a self-driving, self-securing, self-repairing database service that is optimized for transaction processing workloads. You do not need to configure or manage any hardware, or install any software. Oracle Cloud Infrastructure handles creating the database, as well as backing up, patching, upgrading, and tuning the database.
Recommendations
Use the following recommendations as a starting point. Your requirements might differ.
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
Use regional subnets.
- Compartment
By default, any Oracle Cloud tenancy has a default root compartment named after the tenancy itself. The tenancy administrator (default root compartment administrator) is any user who is a member of the default Administrators group.
For this architecture, we create two top-level compartments, HR and Sales, for two different organizations in the root compartment. Two groups manage those compartments: HR-Admins and Sales-Admins. Under the HR top-level compartment, we create the subcompartments HR-Prod, HR-Dev, HR-Staging, and HR-Test. These compartments are managed by groups HR-Prod-Admins, HR-Dev-Admins, HR-Staging-Admins and HR-Test-Admins, respectively. Under the Sales top-level compartment, we create the subcompartments Sales-Prod, Sales-Dev, Sales-Staging, and Sales-Test. These compartments are managed by groups Sales-Prod-Admins, Sales-Dev-Admins, Sales-Staging-Admins, and Sales-Test-Admins, respectively.
- Policy
Compartment access control is governed by policies. Policies are made up of statements that associate a subject (always a group of users) to actions on selected resources (or family of resources) within a tenancy or compartment. You can further qualify policy statement by adding conditions that further refine access control.
In this implementation, we delegate the administration of Oracle Cloud Infrastructure Compute resources through policies and compartments for top-level-compartments and subcompartments. The goal is to have each compartment work independently and in complete isolation from each other.
Considerations
Consider the following points when deploying this reference architecture.
- Scalability
Oracle Cloud Infrastructure supports a compartment hierarchy of up to a six-levels. The administrator of a compartment has full powers over its nested compartments. In this implementation, we use three levels.
Oracle Cloud Infrastructure resources, such as Oracle Cloud Infrastructure Compute, Load Balancing service, and Autonomous Transaction Processing are provisioned in each of the compartments across regions and across environments. In this example, resources are allocated for a simple web application as a reference point for the life cycle of a software development and release.
Oracle Cloud Infrastructure Compute offers the autoscaling feature, which helps you provide consistent performance for your end users during periods of high demand and helps you reduce your costs during periods of low demand. You can also use the auto scaling feature for Oracle Autonomous Transaction Processing. When autoscaling is enabled, if your application the database automatically uses more CPU and IO resources as necessary without any manual intervention. The load balancer offers support for dynamically changing the bandwidth of a shape.
- Availability
Generally, you deploy an application in the region where it's most heavily used because using nearby resources is faster than using distant resources. The availability domains within the same region connect to each other using a low-latency, high-bandwidth network. This network provides high-availability connectivity to the internet and to on-premises equipment so you can build replicated systems in multiple availability domains for both high-availability and disaster recovery.
Oracle Autonomous Transaction Processing eliminates site downtime by maintaining a real-time remote copy of a production database and automatically switching from the primary database to the remote copy using Oracle Data Guard.
- ManageabilityBecause compartments segregate resource management, you can share resources across compartments. For example, to share a compute instance from HR-Dev to Sales-Dev, you have two options:
- Create a custom image of the HR-Dev-Admins group, export the image to Oracle Cloud Infrastructure Object Storage, and make it available to the Sales-Dev-Admins group.
- You can also export the instance boot volume in HR-Dev to the Sales-Dev compartment.
As an administrator, plan in advance how to partition available CIDR ranges across different organization areas. Ensure that VCNs don't have overlapping CIDR ranges. This planning prevents inadvertent peering between any two VCNs across different compartments.
Finally, manage the architecture by automating the infrastructure and resource allocation using Terraform.
-
Security
Configure security lists, which act as virtual firewalls, so that resources in different compartments can communicate. For example, a database instance in the HR compartment can connect to a database instance in the Sales compartment as long as the applicable security lists are properly configured.
Expose a private endpoint for the Oracle Autonomous Transaction Processing database by attaching the database to a private subnet.
When you design the subnets, consider traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary. Add route tables and gateways (virtual routers) to the VCN to manage traffic, depending on the type of access you need. For example, you might need to connect through the public internet, a private internet, an on-premises network, another Oracle service, or a different VCN network in the tenancy.
Consider using Oracle Cloud Infrastructure Compute Web Application Firewall (WAF) to protect the application against malicious traffic from the public internet. This architecture relies on policies that restrict who can access which Oracle Cloud Infrastructure Compute resources within a specific compartment.
Deploy
The Terraform code for creating multitier compartment environments for enterprise solution development is available in GitHub.
- Go to GitHub.
- Clone or download the repository to your local computer.
- Follow the instructions in the
READMEdocument.